HA, gateway groups and firewall's default route.
-
I have a HA setup with two WANs, everything seems to be working correctly but one thing is not clear to me.
Gateway groups that I configured are using the CARP VIP IP and not the interface address.
Can I use this same gateway group as the default route for the firewall itself ?Or, should I create a new gateway group just to use it for the firewall itself, in which I use the interface address instead ?
Can't find this info in the documentation, thanks.
-
@mcury said in HA, gateway groups and firewall's default route.:
Gateway groups that I configured are using the CARP VIP IP and not the interface address.
A gateway group is not assumed to contain interface IPs of the node itself or HA pair. So not clear, what you're talking about here.
However, of course you can use the CARP VIP of another HA pair as upstream gateway, even for the firewall itself.
-
@viragomann said in HA, gateway groups and firewall's default route.:
@mcury said in HA, gateway groups and firewall's default route.:
Gateway groups that I configured are using the CARP VIP IP and not the interface address.
A gateway group is not assumed to contain interface IPs of the node itself or HA pair. So not clear, what you're talking about here.
However, of course you can use the CARP VIP of another HA pair as upstream gateway, even for the firewall itself.
Oh, sorry, let me try to be more clear.
Note: I'll be using my firewall as an example, the HA setup is currently unreachable right now.gateway group: (Where you see Interface address, it is actually a VIP CARP IP)
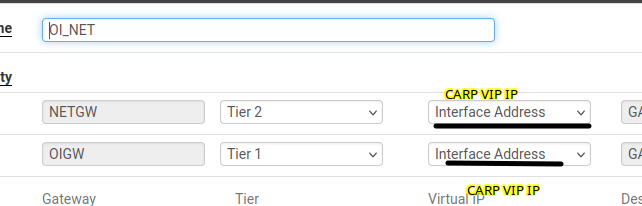
This same gateway group, is being used as the firewall's default gateway:
System > Routing > Gateways
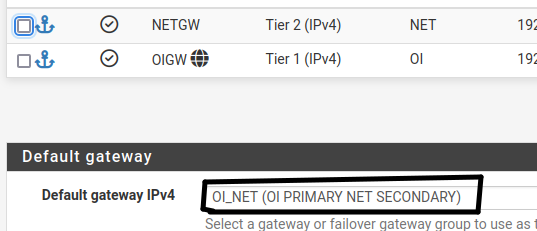
I wonder if it will cause problems or not, can't find anything about this in the Netgate's documentation for HA and multi-WAN.
-
@mcury
Ah yeah. To be honest, I never noticed that you can select the virtual IPs there. So no idea.But the docs say:
Virtual IP
When using a gateway group for failover in certain contexts which require binding a specific address, such as IPsec, this option controls which address on an interface is used for that purpose. For example, in an HA pair this could be a CARP VIP used as an endpoint for IPsec tunnels.
Leave it set to the default Interface Address when a specific address is not required by any use of the gateway group.
(https://docs.netgate.com/pfsense/en/latest/routing/gateway-groups.html)
-
@viragomann said in HA, gateway groups and firewall's default route.:
@mcury
Ah yeah. To be honest, I never noticed that you can select the virtual IPs there. So no idea.But the docs say:
Virtual IP
When using a gateway group for failover in certain contexts which require binding a specific address, such as IPsec, this option controls which address on an interface is used for that purpose. For example, in an HA pair this could be a CARP VIP used as an endpoint for IPsec tunnels.
Leave it set to the default Interface Address when a specific address is not required by any use of the gateway group.
(https://docs.netgate.com/pfsense/en/latest/routing/gateway-groups.html)
1- Localhost is what got me confused, 127.0.0.0/8 will use interface IP address, which according the documentation, is the correct thing to to.
2- Default route of the firewall itself, isn't that the same of 127.0.0.0/8 ?This is the question I can't find in the documentation.
Thinking here, I suppose that I should create a new gateway group, using interface IP address, and use that just for the firewall itself (default route).
Policy routes, ipsecs and everything else would use the gateway group with the CARP VIP.
-
@mcury said in HA, gateway groups and firewall's default route.:
1- Localhost is what got me confused, 127.0.0.0/8 will use interface IP address, which according the documentation, is the correct thing to to.
2- Default route of the firewall itself, isn't that the same of 127.0.0.0/8 ?Are you talking about outbound NAT?
Then yes, the firewall itself should use the interface address. Networks behind it should use the CARP VIPs.But this has nothing to do with gateway groups or the used default gateway.
-
@viragomann said in HA, gateway groups and firewall's default route.:
Are you talking about outbound NAT?
Then yes, the firewall itself should use the interface address. Networks behind it should use the CARP VIPs.Yes, talking about NAT, this part is OK.
@viragomann said in HA, gateway groups and firewall's default route.:
But this has nothing to do with gateway groups or the used default gateway.
hmm, that is what I don't understand...
So, you think I can use the gateway group translated to CARP VIP as the firewall's default gateway as shown in the screenshot above, and that won't cause any problems ?
-
@mcury
The gateway group setting doesn't translate anything. As described in the docs, there are certain use cases, where you should select a virtual IP there. But the default "interface address" is mostly the correct setting.E.g. if you want an OpenVPN server listening on the CARP VIP (or an other virtual IP hooking up on it) and want to use a gateway group for it, you can configure the gateway group with the desired virtual IPs, and in the OpenVPN server settings you can state the gateway group at Interface to listening on.
-
@viragomann said in HA, gateway groups and firewall's default route.:
@mcury
The gateway group setting doesn't translate anything. As described in the docs, there are certain use cases, where you should select a virtual IP there. But the default "interface address" is mostly the correct setting.hm, so it doesn't translate anything.. great.
E.g. if you want an OpenVPN server listening on the CARP VIP (or an other virtual IP hooking up on it) and want to use a gateway group for it, you can configure the gateway group with the desired virtual IPs, and in the OpenVPN server settings you can state the gateway group at Interface to listening on.
Yes, I'm using this gateway group with CARP IPs for IPsec, it works on both nodes, already tested.
For OpenVPN server, I'm listening on localhost, and I have a portforward on both WANs (destination is the CARP), that forwards UDP 1194 to localhost, it is also working perfectly.Everything is all right then, no problems using the gateway group with CARP VIPs as the default route for the firewall.
Thanks @viragomann , that phrase (it doesn't translate anything), fixed my understanding about it.
-
@mcury said in HA, gateway groups and firewall's default route.:
For OpenVPN server, I'm listening on localhost, and I have a portforward on both WANs (destination is the CARP), that forwards UDP 1194 to localhost, it is also working perfectly.
Is it this, why you were looking for localhost?
This does NAT from a virtual IP to localhost. Any respond from the server is translated back to the requested IP according to the state table.
So response packets get the correct IP in any case. -
@viragomann said in HA, gateway groups and firewall's default route.:
Is it this, why you were looking for localhost?
Not OpenVPN, but the outbound connections from the firewall itself.
In the documentation, localhost should be 'NATted' to interface IP address, which is OK, this part is clear to me.What wasn't clear to me is if I should have created a new gateway group, using Interface address, to use as the default route of the firewall.
However, since it doesn't translate anything and everything is working, including IPsec, I'll leave as it is right now, everything using the same gateway group, that has the CARP IP there.
Note that without those CARP IPs in the gateway group, IPsec tunnels won't go up.