NAT Wireguard Subnet to other Subnet
-
Hi,
I currently have a problem where I can't see the wood for the trees. I have a Wireguard VPN subnet (172.24.0.0/24) and a home subnet directly on the pfSense. Since the Wireguard subnet in my case is threatet the same as the users of the home network, the same rules apply there 1:1. However, this double rule setting is too tiring for me and I have often forgotten to copy a rule.
My idea was to simply NAT all known Wireguard IPs in the subnet to IPs from the home network so that I only have to maintain one rule set.
Unfortunately, I can't really get it to work. My approach was to create a virtual IP in the home network and then NAT everything from the wireguard subnet via an outbound rule. Is this the right way? Is there a better approach than NAT?Thanks
-
@merasil Very confusing post and I could ask questions to try and clear it up but it would be easier if you just post a diagram of the network and screenshots of all relevant config.
-
@Jarhead
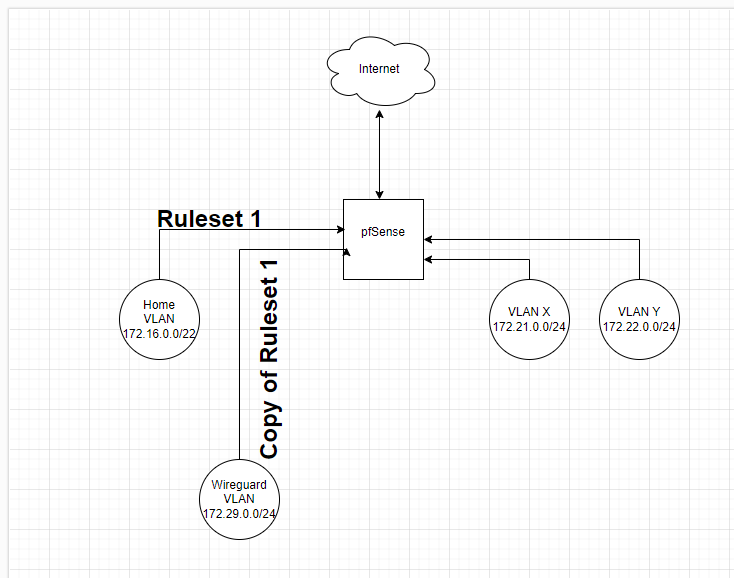
Thank you for your answer. I hope I can provide more clarity with the diagram and my further explanations.
I have created several Wireguard Roadwarrior VPN connections (notebook, iPhone, etc) in pfSense. When connecting, the Roadwarriors end up in the Wireguard VPN VLAN/subnet (172.29.0.0/24). However, since the devices are treated by me as if they were devices from the home VLAN, the rules that I create in pfSense for the subnet are virtually identical to those from the home VLAN. This means that I have to maintain the same ruleset twice, which is quite annoying in the long run.
My thought now was:- either the roadwarriors end up with their IP directly in the home subnet, which is apparently not intended with Wireguard and pfSense
- or I leave them in the 172.29.0.0/24 network and create rules/configs that route all traffic from this network via NAT through the 172.16.0.0/22 network.
Both would mean that I only have to maintain one rule set. However, I don't know exactly what the best approach would be and/or how I can implement point 2.
-
@merasil Still not getting this.
Post the rules from your Home Vlan.
Are you limiting outbound (meaning internet) access with these rules or are they to limit inter-vlan access?
Do you know about "aliases"? -
i limit both internet access and inter vlan communication.
I think the complete ruleset would be a bit much :)
In principle, there are rules that, for example, allow all devices in the home VLAN to access destinations on the Internet via HTTP/HTTPS, but there are also rules that allow all devices in the home VLAN to access services in the other VLANs. For example, all devices may contact the NTP server in VLAN X on UDP 123. However, I now have to maintain the same rules for the Wireguard VLAN, as these are virtually the same for me as if they were devices from the home VLAN. So now I also have to create a rule that allows all devices from the Wireguard VLAN to access destinations on the Internet via HTTP/HTTPS or the rule that they are allowed to access the NTP service in VLAN X.That's what I mean by ruleset copy. If I now create a new rule for the home VLAN, e.g. that they are allowed to access a DNS in VLAN Y, then I must also create this rule for the Wireguard VLAN. This is a bit tedious. It would be better if I only had to create a rule for the home VLAN and didn't have to worry about creating the same rule for the wireguard VLAN.
I don't see how aliases could help me in this case.
Maybe i have to mention that all subnets are on different physical interfaces. So basicly each subnet/vlan has its own physical network interface.