Firewall review
-
Hi, please can someone with more experience review my rules. I would like to restrict ports on LAN and WAN . Is it correct order , invert on WAN correct?
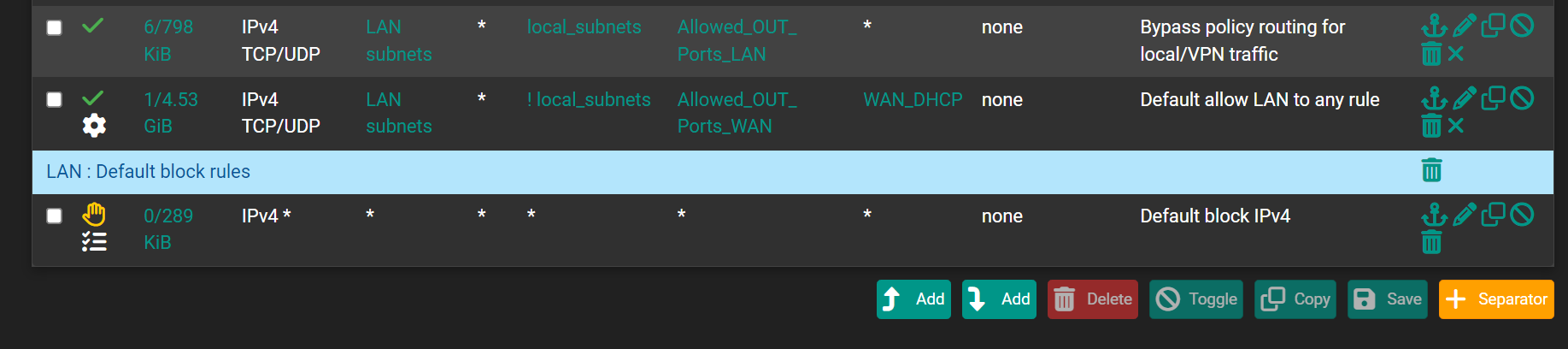
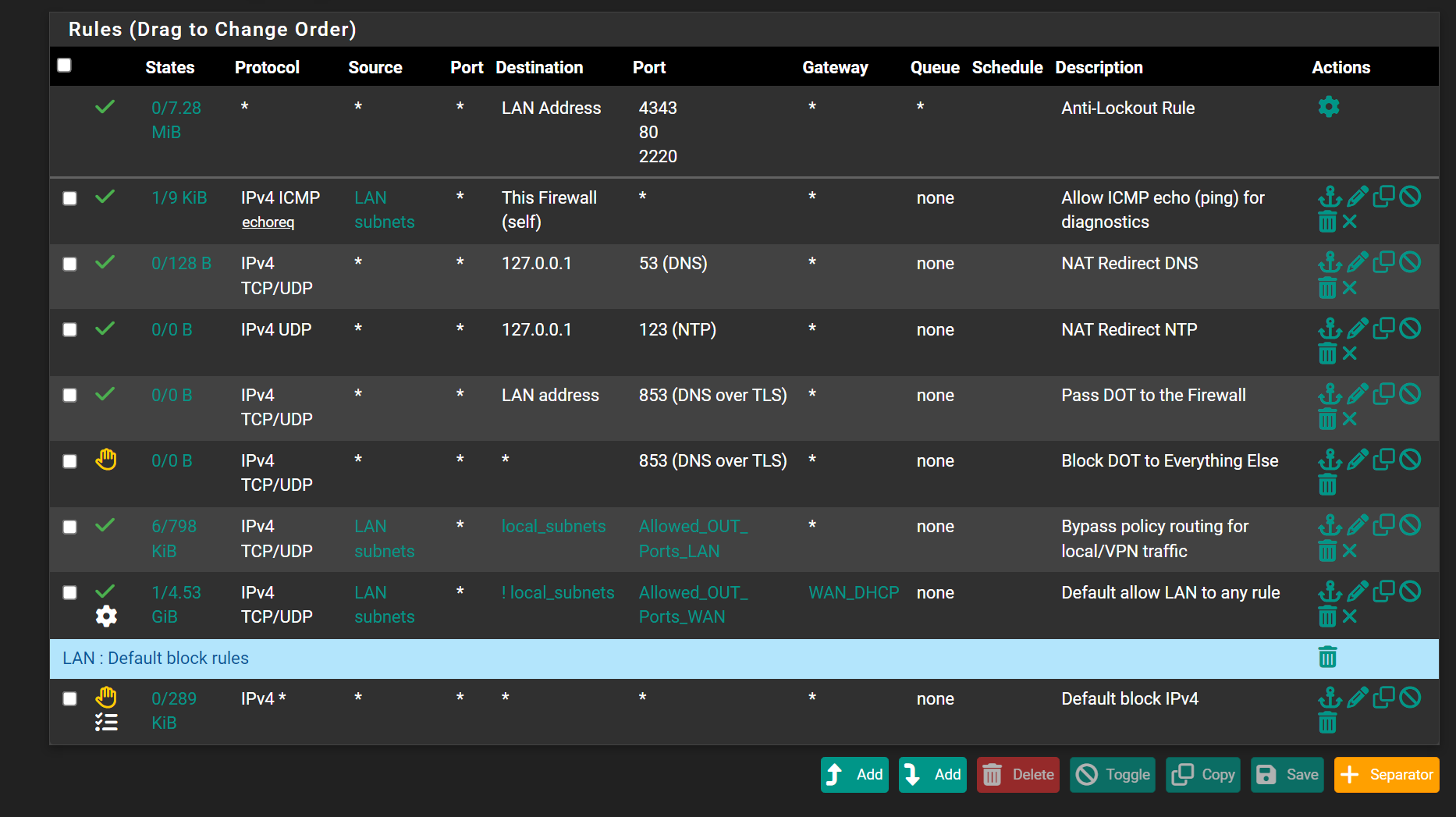
-
@Antibiotic LAN Subnets can't be a source on the WAN.
-
Is the first image the LAN, and the second image the WAN ?
The other way around ?edit : I get it : the second is LAN.
-
@Gertjan Should second rule set exactly on WAN interface or it's ok with invert?
-
@Jarhead Should be set on WAN interface?
-
-
@Gertjan First rule restrict ports to use in local subnets (between LAN OPT1 OPT2 and etc), second restrict ports use outside to world ( from local subnets to internet)
-
Rules apply on traffic that goes INTO the interface only.
A rule like this :
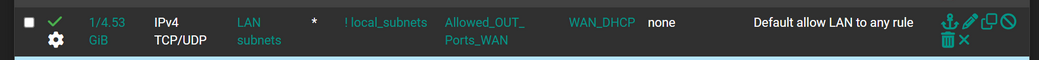
(I presume you already removed the "LAN subnets" from Source)
is placed on an interfact that can never have IP addresses you've placed in "local_subnets".
Golden rule : RFC1918 is not routed over the Internet. So traffic that comes into your WAN contains as a destination IP : your WAN IP and nothing else.
......
The first image is a copy of the bottom part of the second image .....

Can you redo the images svp ? -
-
@Gertjan said in Firewall review:
Golden rule : RFC1918 is not routed over the Internet. So traffic that comes into your WAN contains as a destination IP : your WAN IP and nothing else.
I want to restrict ports use not ip addresses
-
@Antibiotic The firewall applies rules to traffic coming into the interface from the attached network.
If you want to block a PC on the LAN from accessing anything else, the rule goes on the LAN interface.
If you want to block all traffic from the Internet, the rule goes on the WAN. Keep in mind there is a default Block All on all interfaces, but it's a hidden rule. So no rules on an interface means everything is blocked coming in to that interface. -
@Jarhead said in Firewall review:
default Block All on all interfaces
Block all to pfsense and allow all from pfsense? is it correct?
-
@Jarhead said in Firewall review:
coming in
I want to use ports which me allow coming out not come in
-
@Antibiotic said in Firewall review:
What this svp?
That's local language for S'il vous plait, or "Please".
-
@Gertjan Ok my friend, so suspect my rules were incorrect))))
I did default:
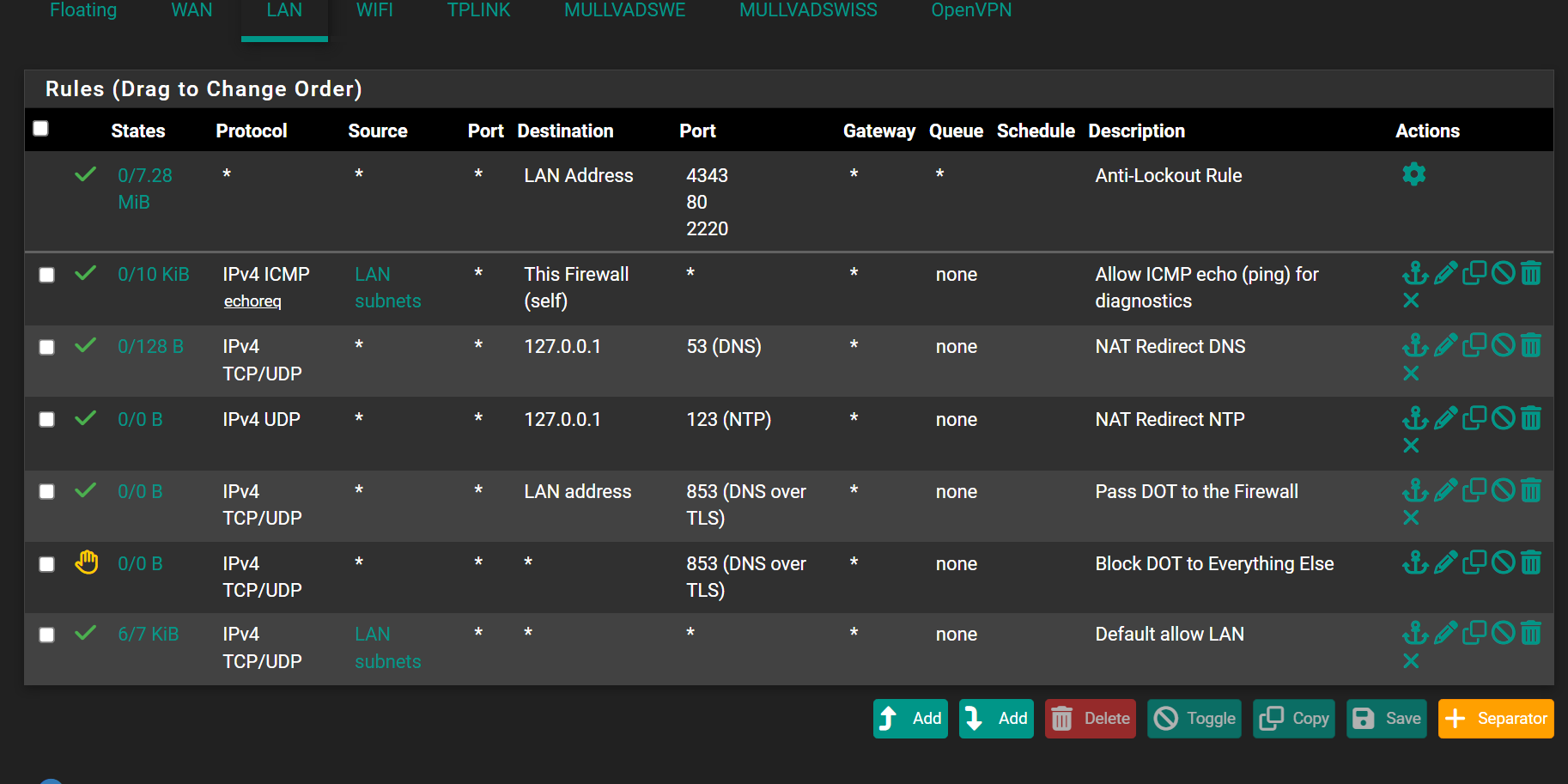
And will searching how to make in correct way, what I want.
Fisrt rule restrict ports using only, what me allow to use inside local subnets
Second rule restrict ports using, what me allow to use outside local subnets to internet. I do not know for this moment, how to make this correct, will search examples with a images by words difficult to imaging. -
@Antibiotic said in Firewall review:
@Jarhead said in Firewall review:
default Block All on all interfaces
Block all to pfsense and allow all from pfsense? is it correct?
You're not understanding still. All traffic is evaluated "entering" the interface that network is attached to.
So yes, block all to pfSense if you wanna say it that way, but not allow all from pfSense because it depends on where that traffic is coming from.
If it's from another interface on pfSense and blocked on that interface, it wouldn't be allowed from pfSense.@Antibiotic said in Firewall review:
@Jarhead said in Firewall review:
coming in
I want to use ports which me allow coming out not come in
So then you have to block or allow the traffic on the interface attached to pfSense.
If you have a pc on OPT1, and you want to block it's traffic to the LAN, you put the block rule on OPT1. That blocks that pc's out as you're calling it.
So you have to think about what each interface, or device, can access, and create rules to do that. -
@Jarhead said in Firewall review:
If it's from another interface on pfSense and blocked on that interface, it wouldn't be allowed from pfSense
When you install pfsense this one is default rule on LAN
Sorry protocol also any , it mean all allow out from interface LAN
-
@Jarhead said in Firewall review:
So then you have to block or allow the traffic on the interface attached to pfSense.
tHAT WJY , ME ASKING CORRECT EXAMPLE TO ALLOW ONLY PORTS WHAT ME WANT TO COMMUNICATE ON SUBNETS AND COMMUNICATE WITH INTERNET. DO NOT HAVE A BIG EXPIRIENCE ,THAT ALL WHAT I WANT
-
@Antibiotic It means allow all traffic from the LAN subnet to anywhere it wants to go.
Once traffic is allowed into the firewall, it can then go anywhere.Don't know how else to say this, traffic is either allowed or blocked as it enters the interface from the network directly attached to that interface.
If you're LAN is 192.168.1.0/24 and you have a pc at 192.168.1.2, and you want to block it from accessing the internet, you put the rule on the LAN interface, not the WAN. -
@Jarhead said in Firewall review:
from accessing the internet
i DO NOT WANT TO BLOCK INTERNET, JUST WANT TO RESTRICT TO PORTS NUMBERS WIHCH I WANT