DNS error
-
Hi, dns log show this error
unbound 83870 [83870:2] error: SSL_write syscall: Permission denied
What it mean,before never see this error type on my pfsense. Unbound resolver working in forward mode to upstream dns in general settings
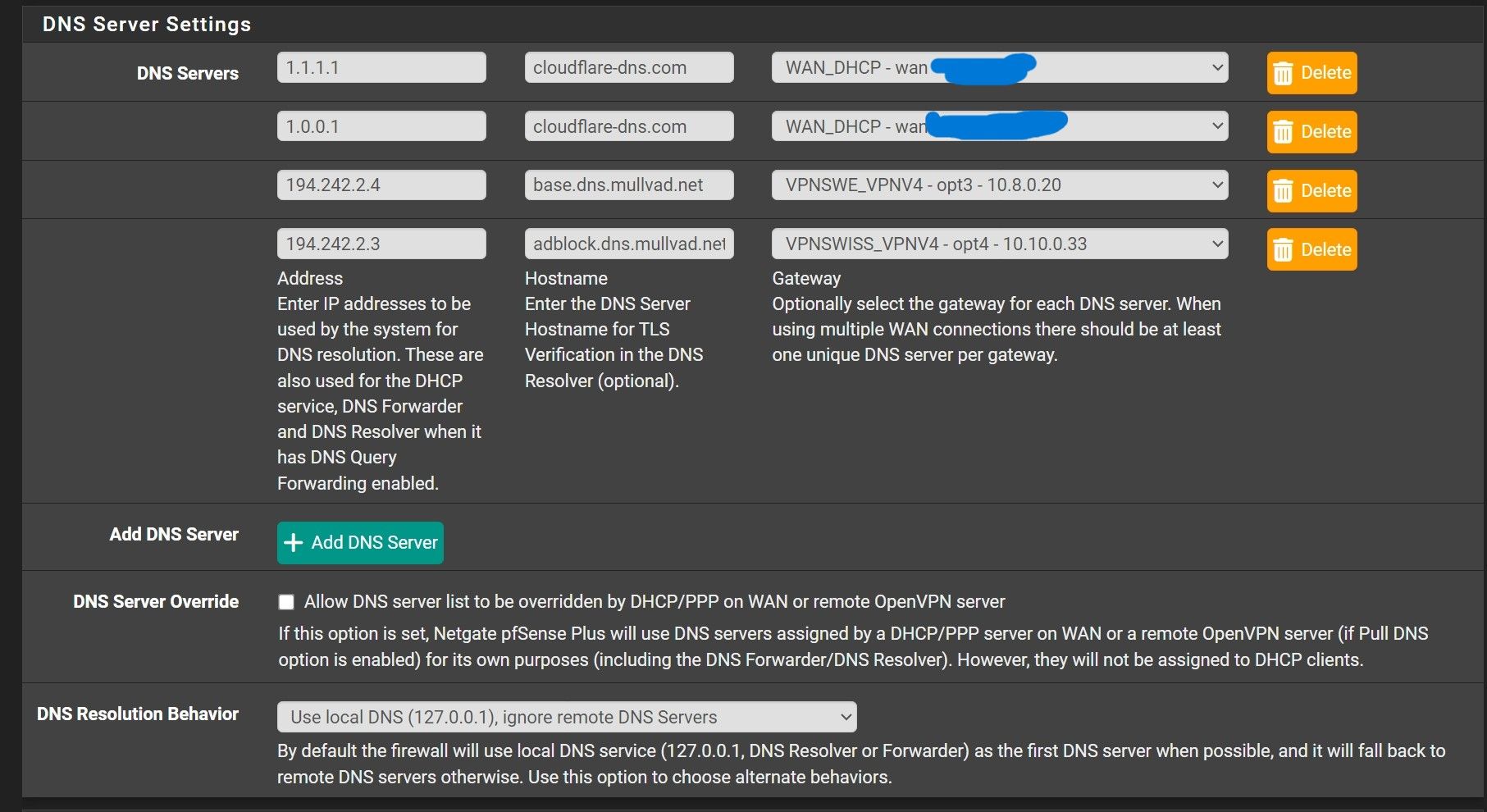
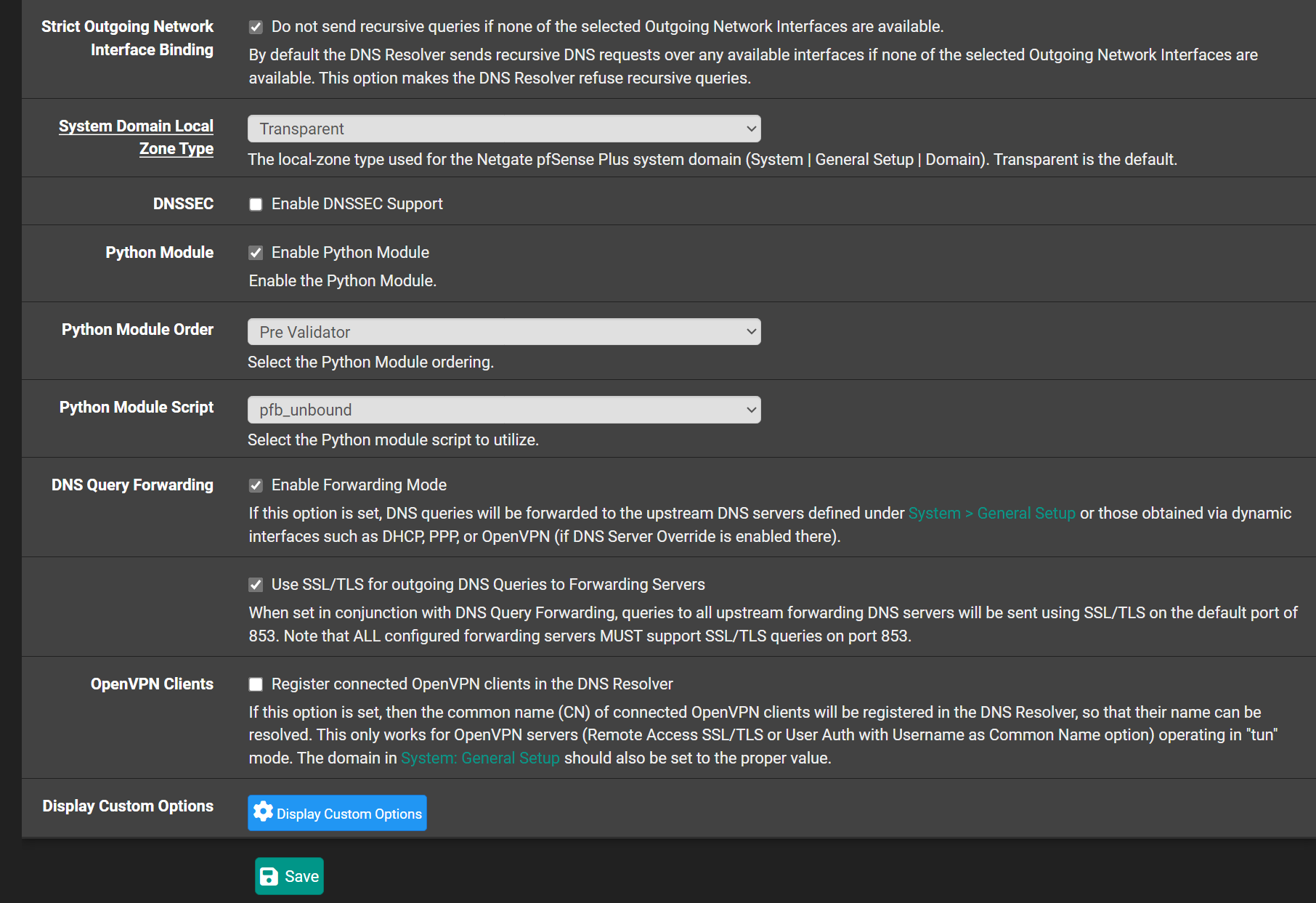
-
@Antibiotic said in DNS error:
unbound 83870 [83870:2] error: SSL_write syscall: Permission denied
It could be as simple as : "the TCP connection, SSL secured" broke, as Internet is a rough place and SSL (TLS) is highly sensible, and unbound complains.
Knowing that two of the possible outgoing connections go over a VPN, changes are bigger (as the path is way more complicated).Keep in mind : complex setup tend to break faster. Stay on KIS road, and you've more time left to do other things^^
Btw : both the reverse of 1.1.1.1 and 1.0.0.1 is not cloudflare-dns,com but "one.one.one.one".
-
@Gertjan Ok , did KIS
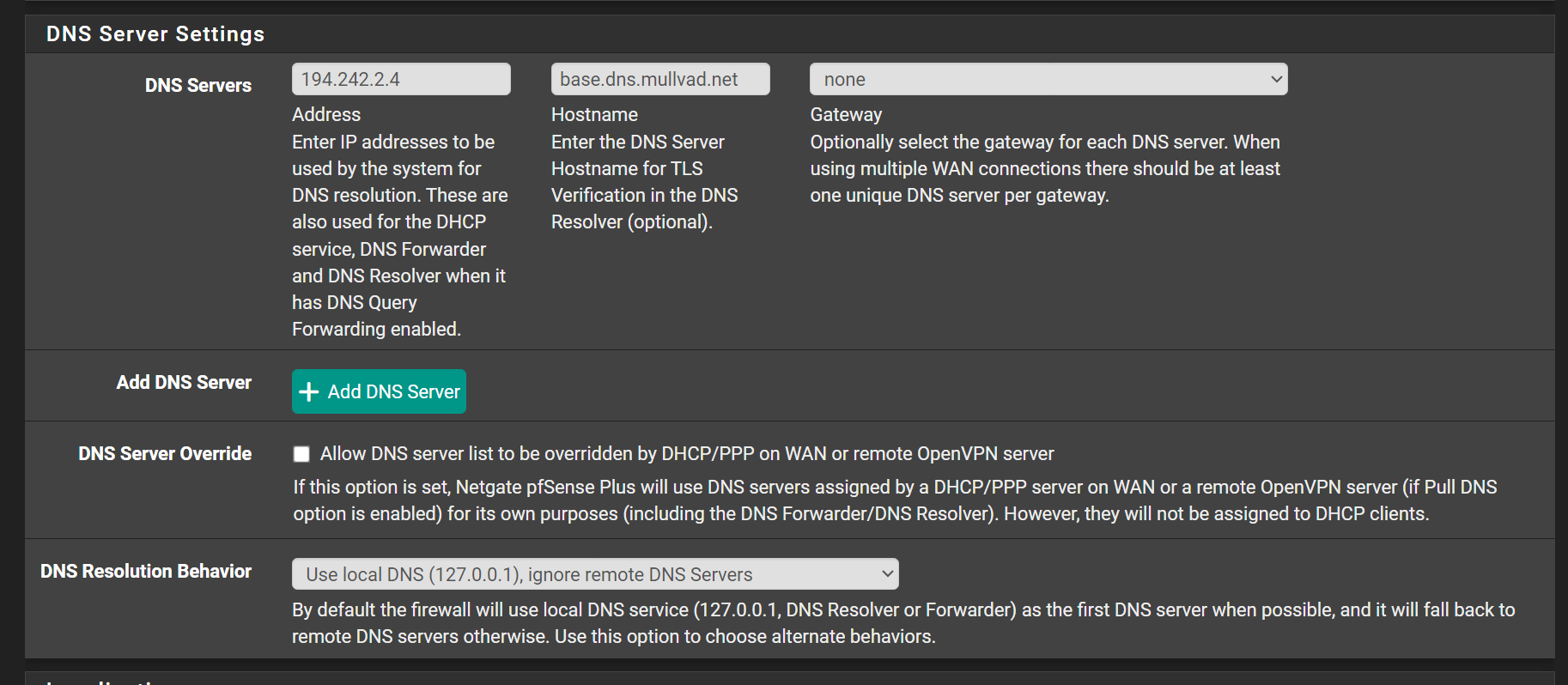
-
-
@Gertjan BTW is any benefits to increase in dns resolver settings "Number of Queries per Thread" default is 512. Lets say up to 1024? Home user not a server production
-
@Antibiotic said in DNS error:
Lol, always set cloudflare-dns.com fot tls over dns
It's just my brain that tells me : when you (unbound) uses TLS, it will get a cert from the other side.
The cert contains a 'host name' (one.one.one.one) and this one.one.one.one resolves to .... aha : 1.1.1.1 : so the connection is ok, unbound speaks to the one he wants to talk to (and the resverse of 1.1.1.1 is ... one.one.one.one. Great.Like https.
-
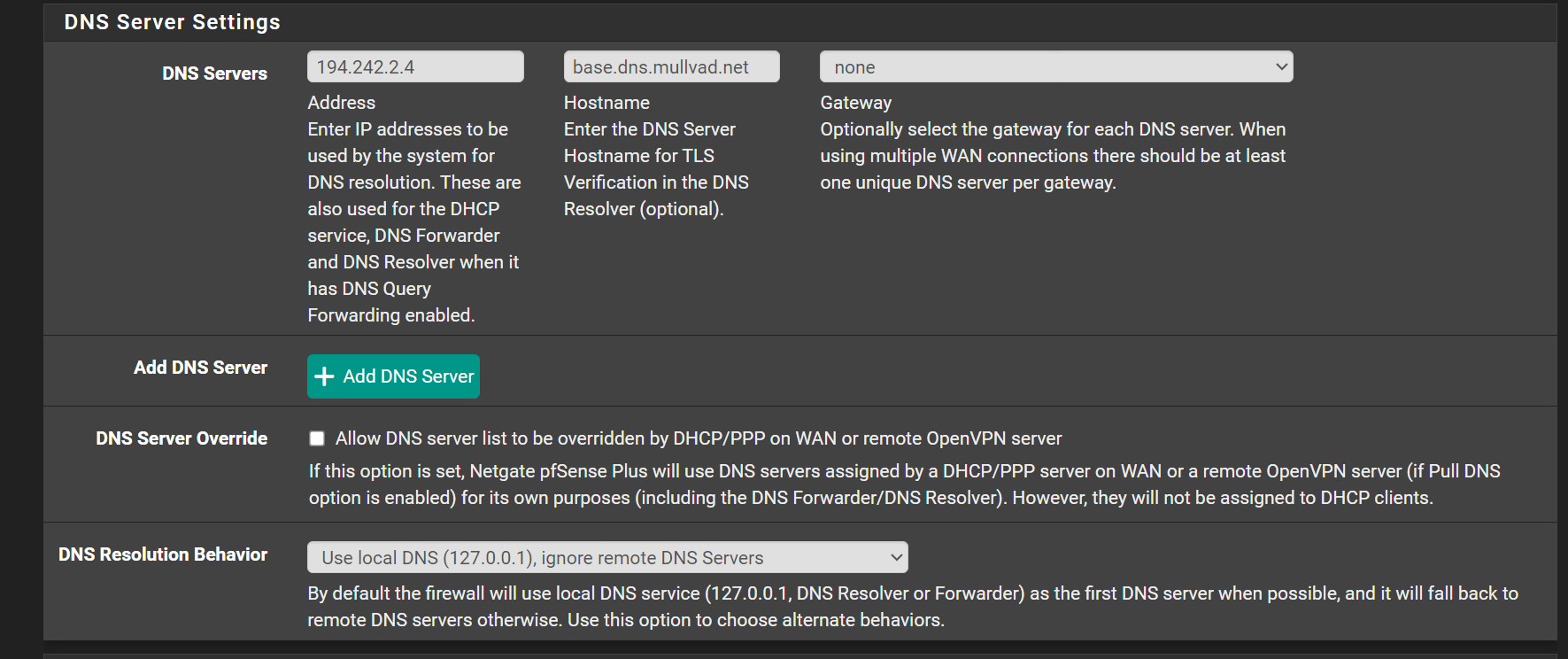
@Gertjan How to check with my new settings, that resolve correctly DOT now via DNS server hostname?
-
With this :
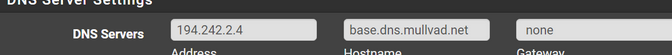
you set it up like this :
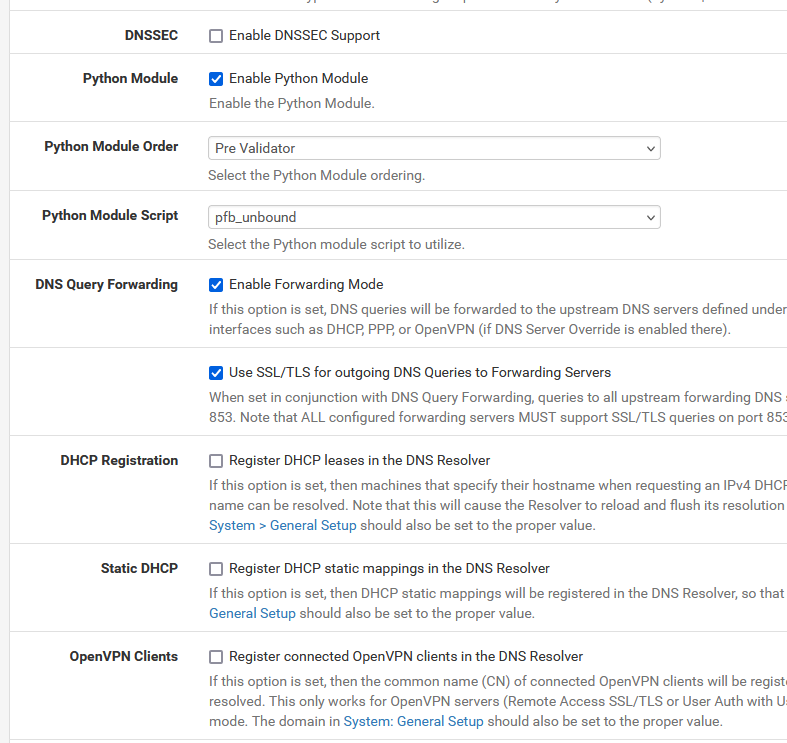
?
So, in short, forwarding to 194.242.2.4, using TLS.Here's one, execute it on pfSense :
dig @127.0.0.1 www.google.com +traceAlso : check every device connected to pfSense, and check every application (system, browser, everything) that it using the pfSense IP as a DNS.
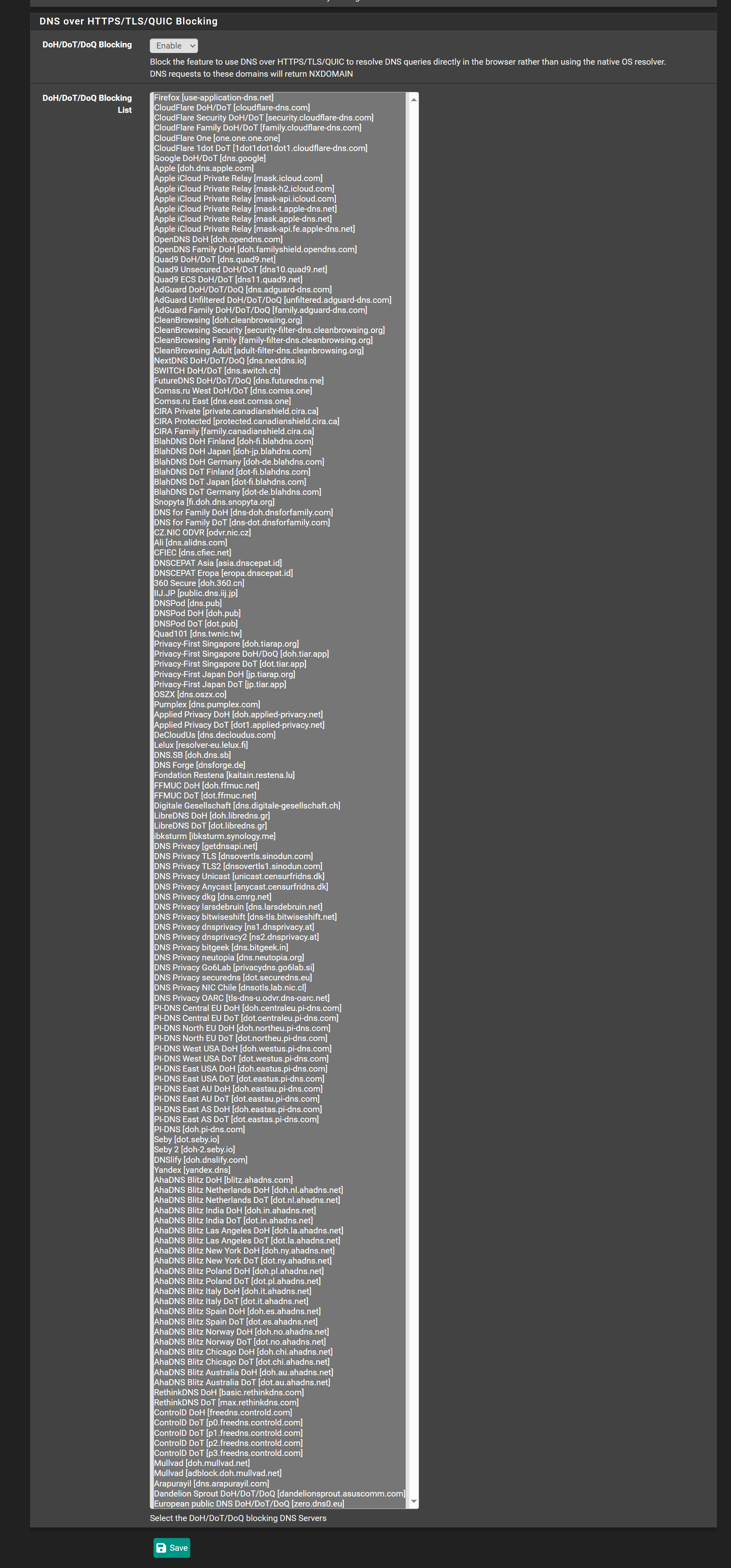
Be aware that browser, when you install them these days, can do (will do) DOT/DOH themselves, completely bypassing pfSense, bypassing unbound (and where unbound forwards to = your 194.242.2.4)
A way to check this : look it up :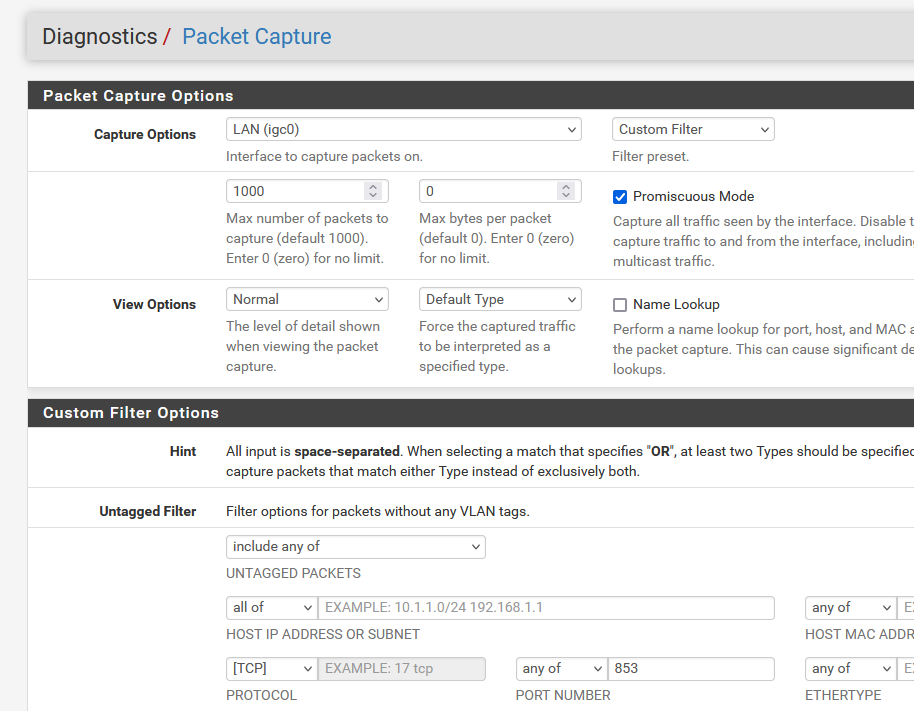
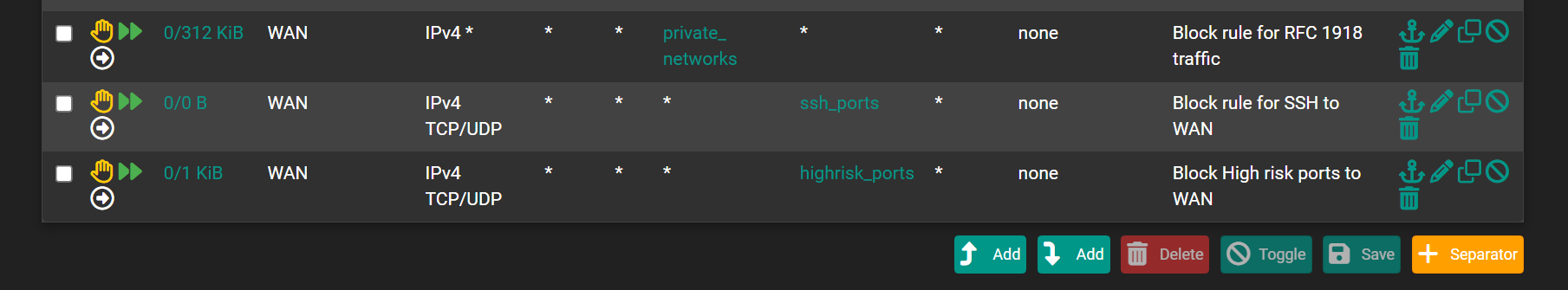
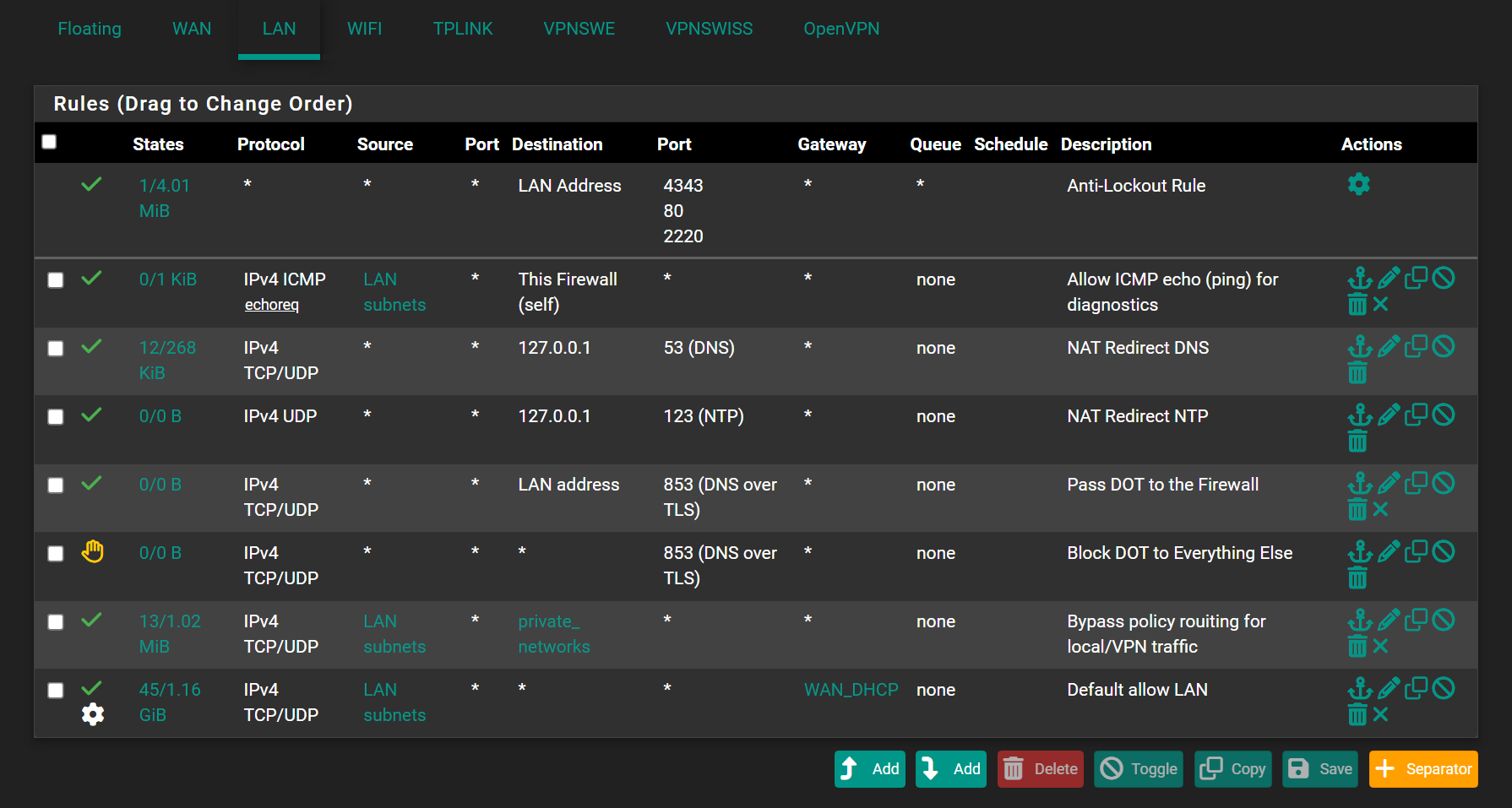
Packet capture traffic on LAN that has a destination, using port 853 (DOT), and let it run for a while.
If lines get logged; devices are doing DOT.
DOH is more difficult, as these could be classic https requests.
And you can't have access to the payload, as it is TLS ;)
I block on my LAns most DOT/DOH using pfBlockerng, forcing my LAN devices to uses classic "port 53", so unbound can do its thing.Btw : KIS isn't even forwarding. Its resolving (that's why unbound was used : its a resolver
 ).
). -
dig @127.0.0.1 www.google.com +trace
What have now:
; <<>> DiG 9.18.20 <<>> @127.0.0.1 www.google.com +trace
; (1 server found)
;; global options: +cmd
. 1213 IN NS e.root-servers.net.
. 1213 IN NS m.root-servers.net.
. 1213 IN NS i.root-servers.net.
. 1213 IN NS a.root-servers.net.
. 1213 IN NS c.root-servers.net.
. 1213 IN NS f.root-servers.net.
. 1213 IN NS k.root-servers.net.
. 1213 IN NS d.root-servers.net.
. 1213 IN NS g.root-servers.net.
. 1213 IN NS b.root-servers.net.
. 1213 IN NS j.root-servers.net.
. 1213 IN NS l.root-servers.net.
. 1213 IN NS h.root-servers.net.
. 1213 IN RRSIG NS 8 0 518400 20240526170000 202 40513160000 5613 . IiMf9tIbZ472c1VluFXMSiqPKqBsYj036EOMEhVb1GzkE+KOF3CE3XOd 6Uq3 jirWQYXzKumY2Zv9nICGSNpz7dBmoZfPcO0gEKhNaO4kvI5Sd9Xo L8vHmJLT/DXKNbj0N/Jb8Ugimn6 hzn+EgUgcWkzi3/UbfG3S3PatTsN5 Ao+bAUYlTnEYmVmSvLbXICRebu5pw5fKezh45+MtSSb7IVQrTg BEcdwP sXURDTv0V+6gKSj2eN0lyOwRzj1HTSMBEOah2ZiPsuVhncZqkU34ctQV 1fEuNqreLTTf2AHP iV3WEv1ZYENFM3DW6zkAXBWxNZwGFX81GoC91ZbL E27KjQ==
;; Received 1097 bytes from 127.0.0.1#53(127.0.0.1) in 60 ms;; communications error to 192.112.36.4#53: connection refused
;; communications error to 192.112.36.4#53: connection refused
;; communications error to 192.112.36.4#53: connection refused
;; communications error to 199.7.83.42#53: connection refused
;; communications error to 199.7.91.13#53: connection refused
Is it OK? -
Also : check every device connected to pfSense, and check every application (system, browser, everything) that it using the pfSense IP as a DNS.
Be aware that browser, when you install them these days, can do (will do) DOT/DOH themselves, completely bypassing pfSense, bypassing unbound (and where unbound forwards to = your 194.242.2.4)With my rules, I think impossible to bypass))