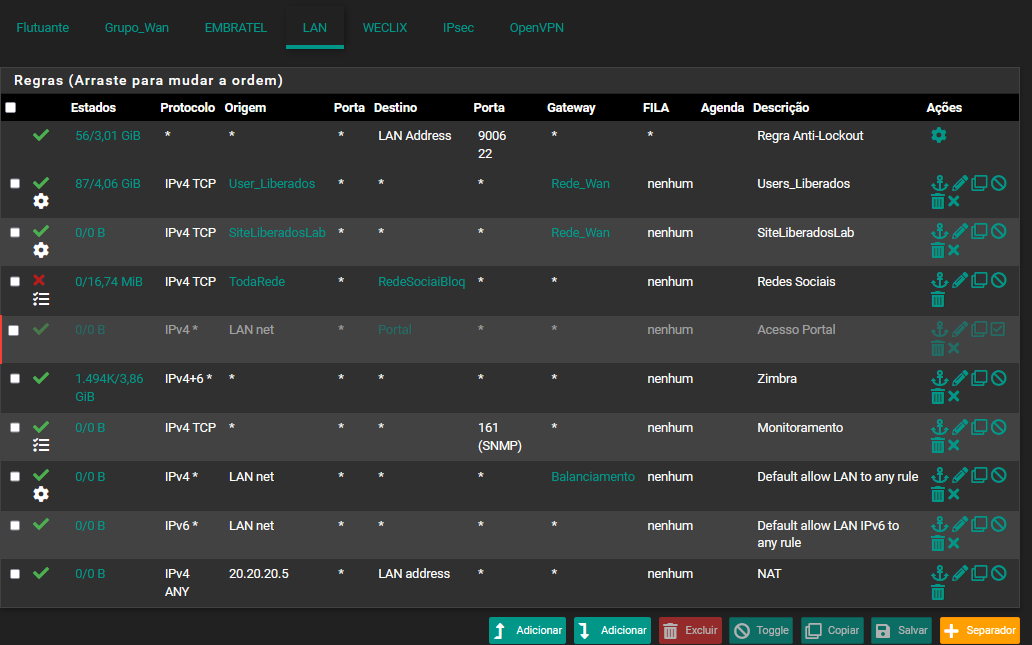
VPN -> LAN (OK) | LAN -> VPN (OFF) need both working
-
I need my Local Internet to talk to OPENVPN clients, I currently have an OPENVPN configured on a Gateway on another unit, the OpenVPN client normally talks to my pfsense and the local network, but the local network and pfsense don't even ping these clients.
Settings that may help below:
Config SERVER OpenVPN:
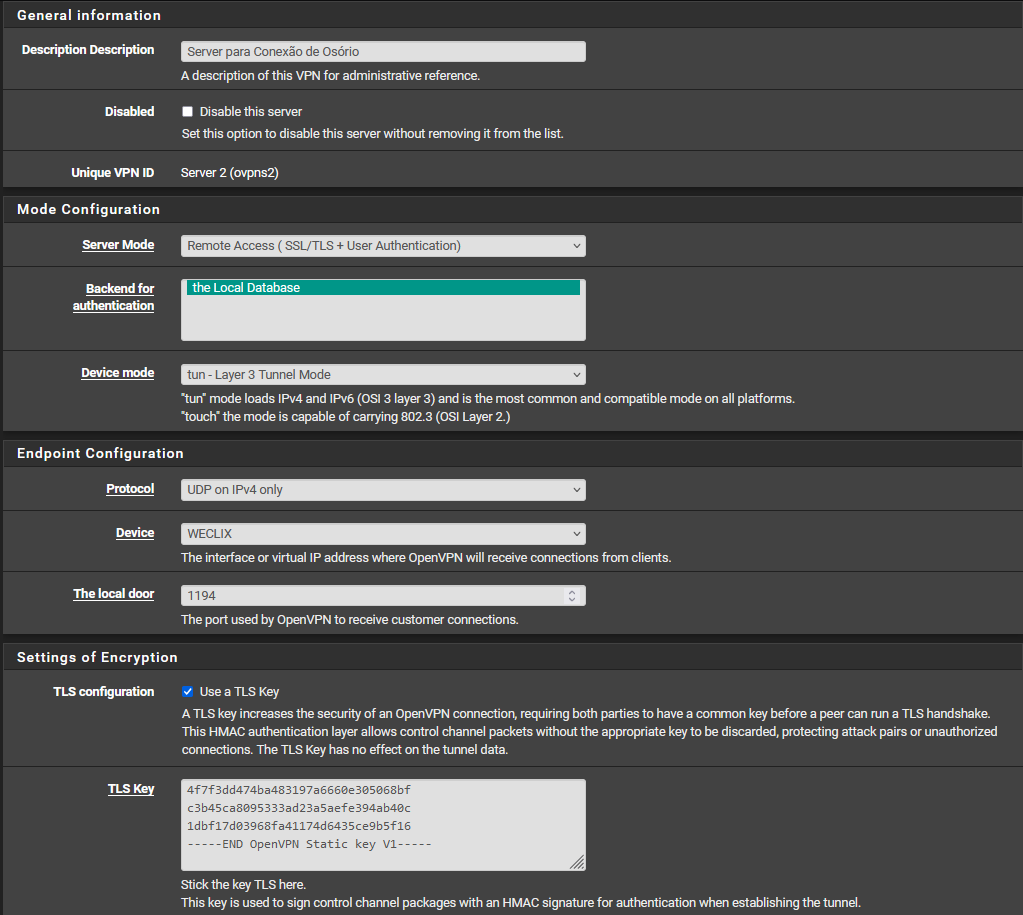
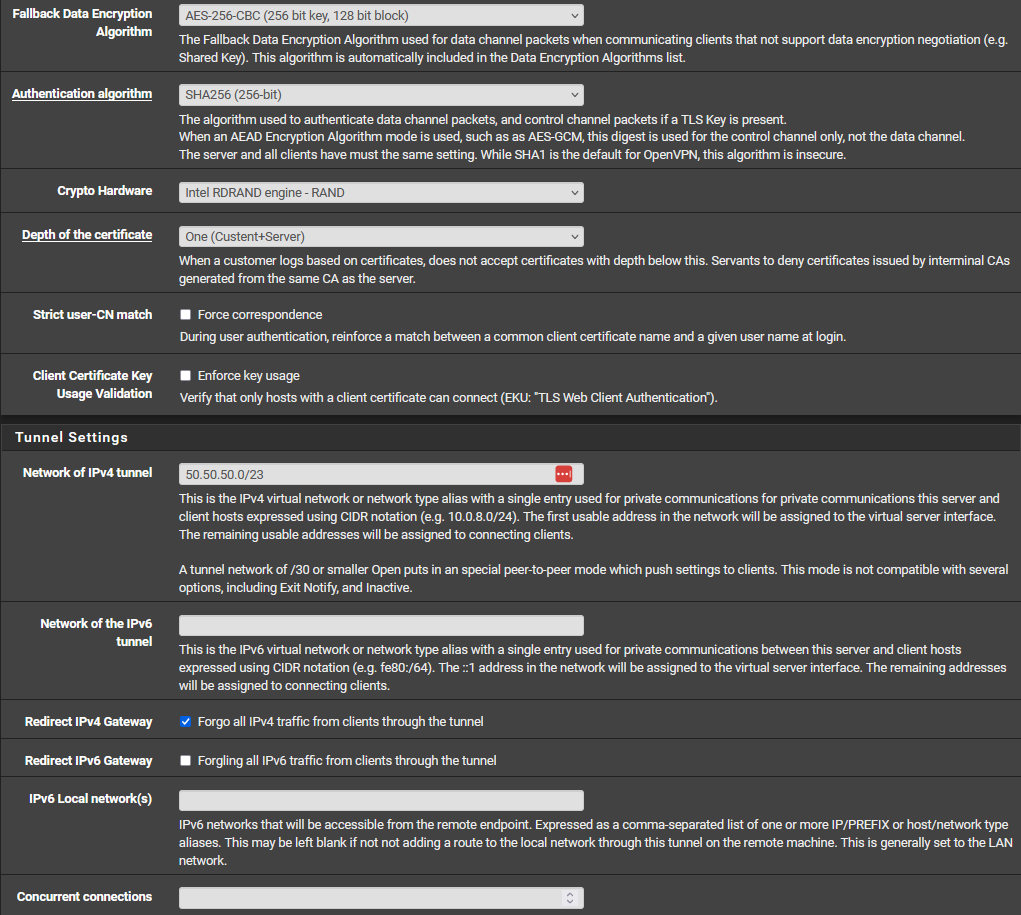
There is no static routing done, and no outbound NAT.
Rules made:
Firewall>Rules>OpenVPN:
Protocol: Any
Origin: Any
Destination: Any2.7.0-RELEASE (amd64)
-
So the OpenVPN server is in the same subnet as the local clients?
Those local clients are using some other router as their default gateway?
Are you sure there is no outbound NAT on the pfSense used as the OpenVPN server?
Because that would usually be required for the VPN clients to reach the local hosts and them to be able to respond.Steve
-
OpenVPN clients: 50.50.50.0/23
Local Lan: 192.168.140.0/23Local clients only use 192.168.140.1/23 as Gateway (My pfsense)
There is no static configuration in NAT, just automatic configurations that already come in place for the traffic to be carried out.
-
-
Oh so you only have one router and it's pfSense?
What are you firewall rules on the local interface then? Probably LAN.
-
-
@BRQ_michael I believe it is to pass, because there is a rule to allow everything (LAN)
-
Where are you testing this from? If it's inside one of those aliases you may be policy routing it via the Rede_Wan gateway.
-
@stephenw10 How do I do that?
-
@stephenw10 I do the tests as follows, access through the OpenVPN client and try to ping my Lan XDD
-
I mean when testing the other way, from LAN to OpenVPN, if the client you are testing from on LAN gets policy routed it will be forced via that gateway can cannot reach the VPN.
So that means whatever is inside the User_Liberados or SiteLiberadosLab aliases.
-
@stephenw10 Even if I am within these rules or not, I cannot ping either the IP that the Gateway got from the other side, nor the IP of its LAN.
-
What IPs specifically are you trying to ping? I assumed other clients inside the tunnel subnet but do you mean remote subnets behind other clients?
For that to work you need to add routes and iroutes so both pfSense and OpenVPN know where to send traffic.
-
@stephenw10 I'm trying to ping my machine, and even the firewall, the option within the firewall to ping, but if I don't have to add some static routing and some outbound NAT? If so, how do I do it?
-
What is 'your machine' in this context?
-
@stephenw10 My notebook on the LAN within PFSENSE, on the LAN where I couldn't talk to OPENVPN clients but the OPENVPN client accesses my machine, pings, etc...
192.168.140.57
-
And you are trying to ping that from Diag > Ping in pfSense? And it's failing?
Is 192.168.140.57 in either of those aliases?
What remote client IP are you trying to connect to from the notebook?
-
@stephenw10
Exactly, I'm trying to ping from my notebook (192.168.140.57) and PFSENSE (192.168.140.1) and the ping doesn't work, both for the IP that the client got from the VPN, and for the client's LAN.192.168.140.57 I was, but I removed it, and it didn't work the same way, whether or not it was in the aliases.
50.50.50.2/32(OPENVPN Client) or 192.168.100.1(Local LAN OpenVPN Client)
-
Ok. So you should be able to ping the VPN client IP in the tunnel subnet but the client itself would have to allow it. Is that also pfSense? If so you would need a firewall rule there.
To ping a subnet behind the client you need routes and iroutes. That means adding them as remote networks in the server setup and adding Client Specific Overrides for the client with that subnet defined:
https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-tls.html#create-client-specific-overridesSteve
-
@stephenw10 Okay, but I don't want clients to be visible on my network just to ping, I need them to talk to everything, from ping to remote access, everything in fact