REGEX blocking
-
@gertjan Sometimes it works...sometime it doesnt.
Kind of annoying....
^ad([sxv]?[0-9]*|system)[_.-]([^.[:space:]]+\.){1,}|[_.-]ad([sxv]?[0-9]*|system)[_.-] ^(.+[_.-])?adse?rv(er?|ice)?s?[0-9]*[_.-] ^(.+[_.-])?telemetry[_.-] ^adim(age|g)s?[0-9]*[_.-] ^adtrack(er|ing)?[0-9]*[_.-] ^advert(s|is(ing|ements?))?[0-9]*[_.-] ^aff(iliat(es?|ion))?[_.-] ^analytics?[_.-] ^banners?[_.-] ^beacons?[0-9]*[_.-] ^count(ers?)?[0-9]*[_.-] ^mads\. ^pixels?[-.] ^stat(s|istics)?[0-9]*[_.-] # ^(.+[_.-])?(facebook|fb(cdn|sbx)?|tfbnw)\.[^.]+$Facebook block only works sometimes and it makes DNS horribly slow. (its intentional that I commented it out in the current config).
-
I'm not sure you can comment it out with a #. I advise you to remove it.
This is regex, not some script ;)Btw :
See line 1451 in /var/unbound/pfb_unbound.py
as long as there are items on the regex list, the pfb_regex_match(q_name) function is called.
The main advantage of regex is : is 'blindingly' fast (way faster as what PHP could have done, python is far superior). When I activated that rule, my browser instantaneously showed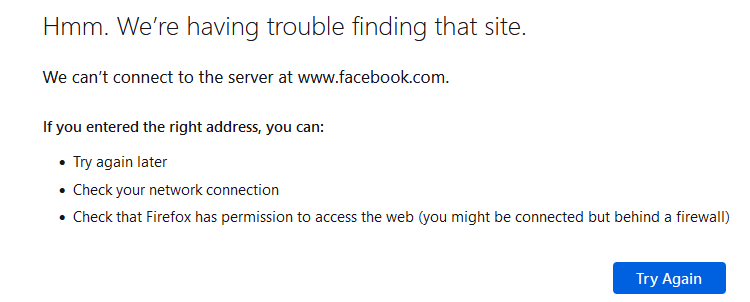
when I entered www.facebook.com in the URL bar.
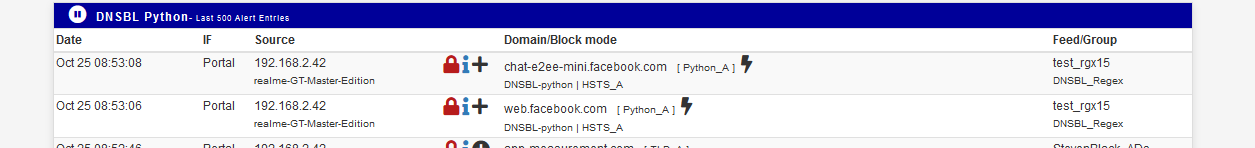
The DNSBL Python logs :
Regex blocking is as fast as it can gets, way faster as the parsing needed for all the main DNSBL list, compiled from all your DNBL feeds.
-
WTF ....
I added a 'facebook' regex above so I could collect some DNSBL log lines - see image above.
I also saw :
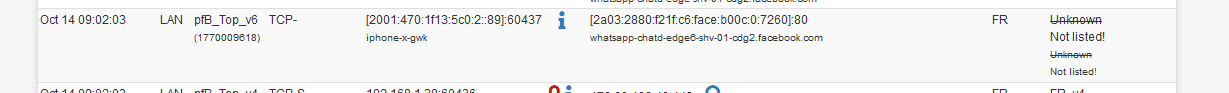
and, as 'facebook' is in the hostname, all looks fine.
I removed the facebook regex, and reloaded pfBlockerng.
Still, Whatsapp didn't work (on my phone).
And wtf, when I deactivated wifi on my phone, still Whatsapp "doesn't work".Facebook did it again : they have managed to shut themselves, whatsapp this time, out of the Internet. Probably on a planetary level

-
@gertjan Thats exactly my issue.... that other apps are affected because they are all mining on each others data og dns records.
Kind of annoying...
-
@gertjan https://www.independent.co.uk/tech/whatsapp-down-not-working-status-b2209835.html?utm_content=Echobox&utm_medium=Social&utm_campaign=Main&utm_source=Twitter#Echobox=1666682232
-
@cool_corona Twitter ?
Also on CNN, MSNBC, Foxnews, BBC, all major (local) french tv news, and soon many Youtube "facebook did it again" videos. -
@gertjan so i guess a really slick feature to pfblockerng-devel would be the ability to add regex lists from pihole, like how suricata can use snort lists.
-
At the bottom of Python Regex List section reads "Changes to this option will require a Force Update to take effect" but actually Reload is required.
-
This post is deleted! -
@Uglybrian Is it still working?
-
@Gertjan Hello, are you still using regex blocking in pfblockerng?
-
Yes Antibotic, its still working and I am still using the same list. so far so good.
-
yes :
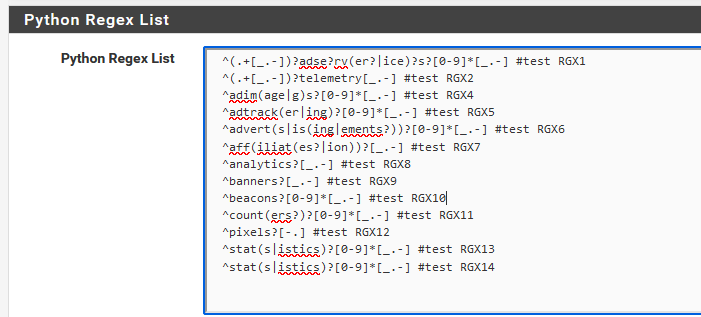
It's pretty powerful.
Be aware : regex !Read it like this : if any of the text in the lines (the requested host name) matches the regex list, the request gets blocked.
-
@Gertjan Can you please post your regex in text format? I will copy
-
^(.+[_.-])?adse?rv(er?|ice)?s?[0-9]*[_.-] #test RGX1 ^(.+[_.-])?telemetry[_.-] #test RGX2 ^adim(age|g)s?[0-9]*[_.-] #test RGX4 ^adtrack(er|ing)?[0-9]*[_.-] #test RGX5 ^advert(s|is(ing|ements?))?[0-9]*[_.-] #test RGX6 ^aff(iliat(es?|ion))?[_.-] #test RGX7 ^analytics?[_.-] #test RGX8 ^banners?[_.-] #test RGX9 ^beacons?[0-9]*[_.-] #test RGX10 ^count(ers?)?[0-9]*[_.-] #test RGX11 ^pixels?[-.] #test RGX12 ^stat(s|istics)?[0-9]*[_.-] #test RGX13 ^stat(s|istics)?[0-9]*[_.-] #test RGX14 -
@Gertjan Thank you
-
-
@Gertjan Are you block for incoming?
What the reason, firewall block itself all in? -
@Antibiotic said in REGEX blocking:
Are you block for incoming?
My LANs of course.
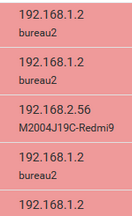
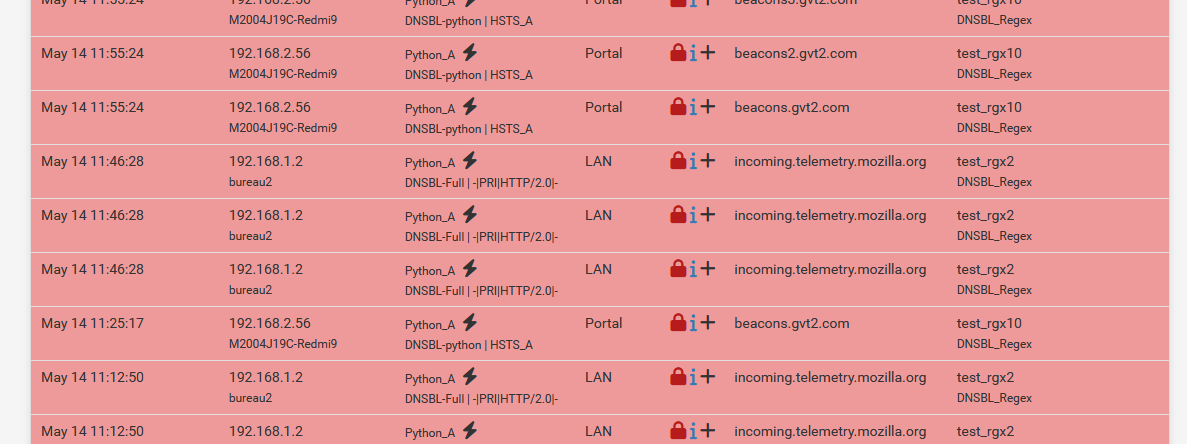
That's where the original DNS requests come from, and I want to 'disable' some of them like "incoming.telemetry.mozilla.org" (probably from my browser).
I don't know what beacons.gtv2.com is, the request came from my captive portal.@Antibiotic said in REGEX blocking:
What the reason, firewall block itself all in?
The regex has nothing to with the/a firewall.
A DNS request came in "what is the A of incoming.telemetry.mozilla.org ?"
The regex filter found it, so pfBlockerng told unbound to tell the LAN client : it's 0.0.0.0.
When the LAN clients receives 0.0.0.0 it can't connect to "incoming.telemetry.mozilla.org" because it has no valid IP to connect to.
This is how DNSBL works.I don't need (want) a firewall that blocks "Internet" IPs. My LAN firewall is wide open - the portal a bit less, though.
-
@Gertjan are you using firefox?