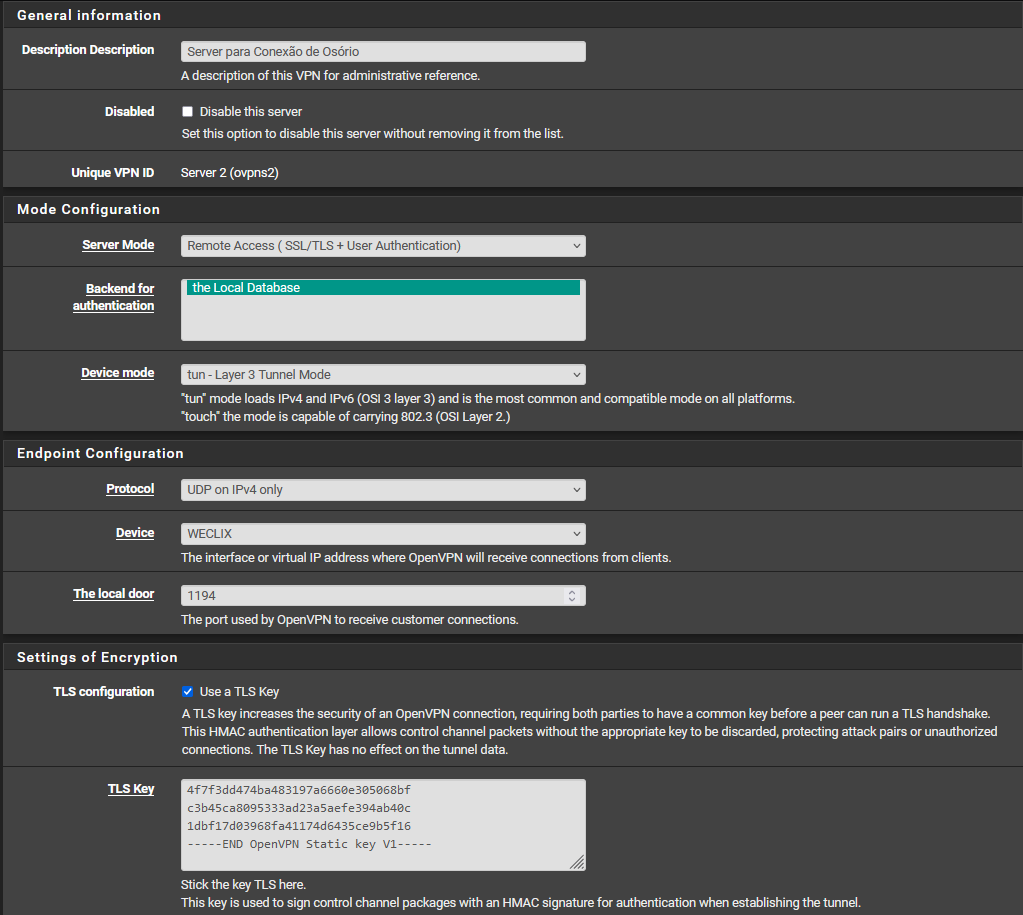
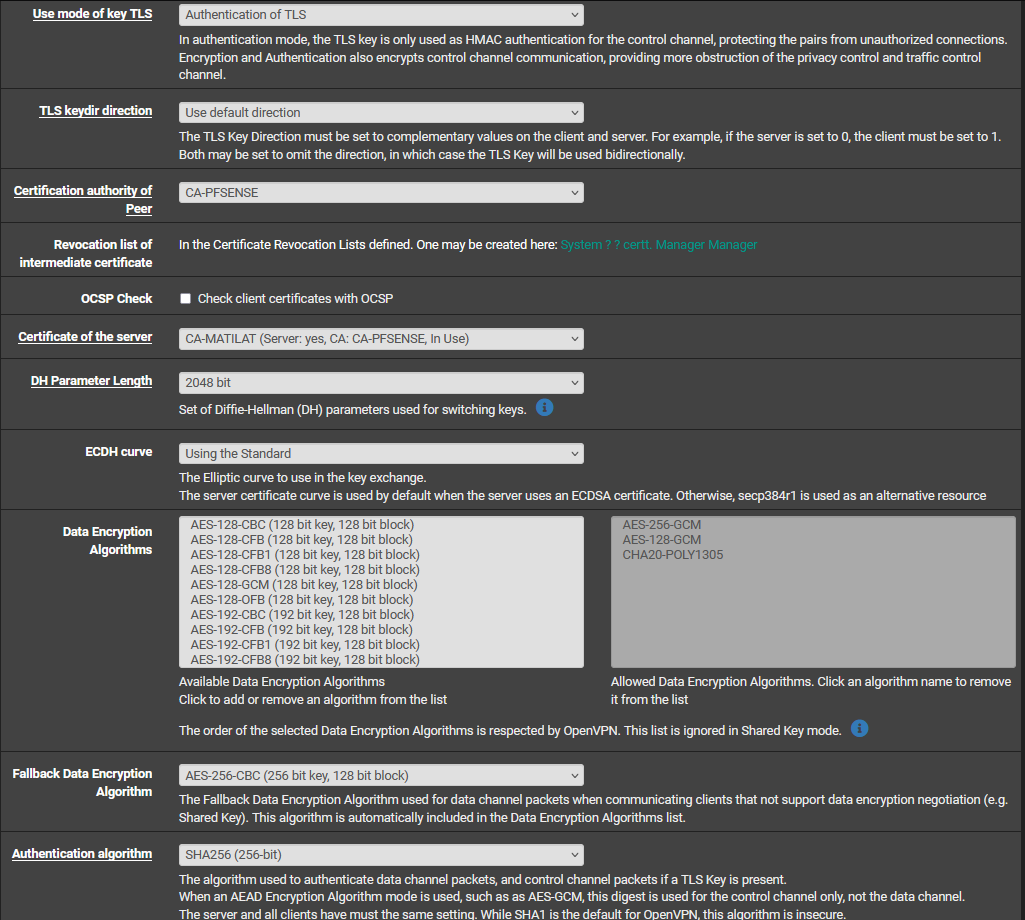
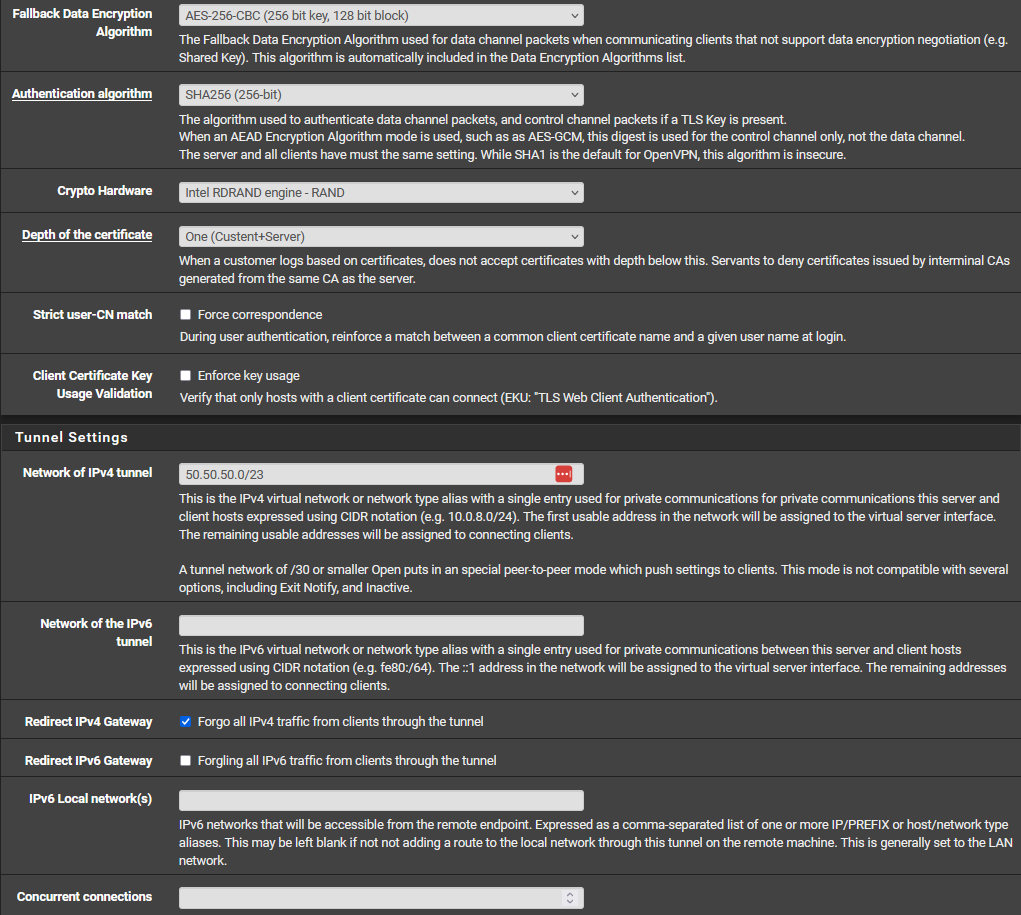
VPN -> LAN (OK) | LAN -> VPN (OFF) need both working
-
What is 'your machine' in this context?
-
@stephenw10 My notebook on the LAN within PFSENSE, on the LAN where I couldn't talk to OPENVPN clients but the OPENVPN client accesses my machine, pings, etc...
192.168.140.57
-
And you are trying to ping that from Diag > Ping in pfSense? And it's failing?
Is 192.168.140.57 in either of those aliases?
What remote client IP are you trying to connect to from the notebook?
-
@stephenw10
Exactly, I'm trying to ping from my notebook (192.168.140.57) and PFSENSE (192.168.140.1) and the ping doesn't work, both for the IP that the client got from the VPN, and for the client's LAN.192.168.140.57 I was, but I removed it, and it didn't work the same way, whether or not it was in the aliases.
50.50.50.2/32(OPENVPN Client) or 192.168.100.1(Local LAN OpenVPN Client)
-
Ok. So you should be able to ping the VPN client IP in the tunnel subnet but the client itself would have to allow it. Is that also pfSense? If so you would need a firewall rule there.
To ping a subnet behind the client you need routes and iroutes. That means adding them as remote networks in the server setup and adding Client Specific Overrides for the client with that subnet defined:
https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-tls.html#create-client-specific-overridesSteve
-
@stephenw10 Okay, but I don't want clients to be visible on my network just to ping, I need them to talk to everything, from ping to remote access, everything in fact
-
@BRQ_michael But this step by step is just to add in case PFSENSE was a client of another OpenVPN server, no?
-
No that's the server side for an SSL/TLS site to site which is what you have.
Is the client end here also pfSense?
-
@stephenw10 No, it's a computer
-
So how is it routing traffic from the subnet behind it? You enabled some software routing on the 'computer'?
-
@stephenw10 I don't understand the question sorry, I'm on a computer on the pfsense local network and that's why I can access it, to test I disconnect from the company's LAN network, connect from my cell phone data and do the tests connected to openvpn, if it is What you wanted to know from the question, I ended up not understanding.
-
You said you need to be able to access the VPN clients from LAN is that not true?
-
@stephenw10 exactly, this is what I need, I need my local LAN to talk to the Clients of my OPENVPN server
-
OK so you are testing by pinging from, for example, 192.168.140.57 to 50.50.50.5 ?
In that case the client at 50.50.50.5 must allow the ping traffic. For example Windows firewall will block that.
-
@stephenw10 Exactly, but for example, it's not just ping that doesn't allow it, I try to access my folders, and also transfer something, and my Windows firewall has been dead for ages, completely disabled.
-
Right but we just use ping as a test because it will usually be allowed.
So what error does it return?
-
@stephenw10 The order has timed out.
-
OK, run the ping from a host on LAN then check the state table. Filter by the target IP address and make sure you see the states present.
You should see one state on LAN and one on OpenVPN.
-
@stephenw10 Done, no ping
-
So no states created on any interface?
Was the ping running while you checked the states? The states will close quickly after the ping stops, like maybe 30s.