Routing Firewall A over IPSec to Firewall B
-
Dear community,
i have the following Setup:
Firewall A:
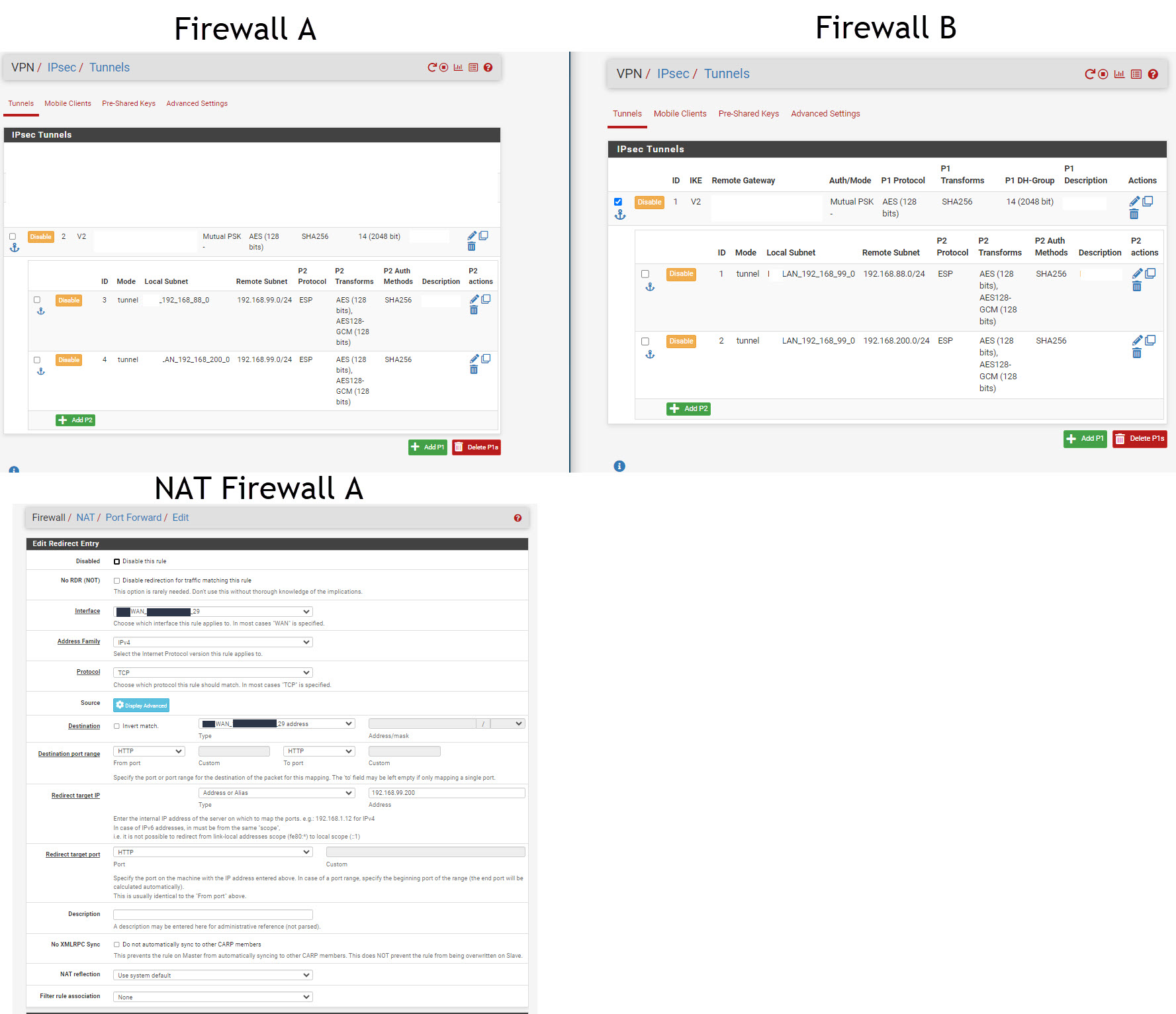
LAN IP: 192.168.88.0/24Firewall B:
LAN IP: 192.168.99.0/24Firewall A is connected with Firewall B through IPSec Tunnel .
On Firewall A and B on the LAN Interfaces i can ping each other.
but when i try now add a NAT rule on Firewall A (WAN-IP:8080) and want use the destination address 192.168.99.X:8080, then i get this not working.
now is the questions how i can solve that. i have in IPSec tunnels configured local and remote subnet. in the LAN interfaces of both i can ping each other. but direct in firewall when i try use the ping function, i cannot ping the remote subnet.
last time i has done this with openVPN. here all was working fine (because openVPN has created the own routes).
but how i can setup this via IPSec?
I want use WAN-IP-FIREWALL-A:PORT to connect to FIREWALL-B-LAN-IP:8080.
Thank you so much.
many greets markus
here are the configuration:
-
@mako said in Routing Firewall A over IPSec to Firewall B:
but when i try now add a NAT rule on Firewall A (WAN-IP:8080) and want use the destination address 192.168.99.X:8080, then i get this not working.
This does not work with policy-based IPSec. Response packets of the destination device will be routed out to the default gateway.
The only option to make it work would be to route the whole internet traffic of the concerned device to the remote site and go out on its WAN.You can do this with OpenVPN, Wireguard or maybe routed IPSec (VTI), however.
-
@viragomann
thank you for your reply!
This confirms my assumption. thanks for that.But I still have a question about openVPN (i also has before i has done the update to 2.7.2 openVPN site to site (PSK) in use. while this has not worked, i have changed my tunnels temporary to IPSec thats the reason:
Before I updated to the 2.7.2 version, I had realized Site to Site via openVPN and Preshared Key.After the update I set up Site 2 Site using TLS certificates as described here:
https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-tls.htmlUnfortunately I have the problem that the tunnel opens correctly, but I can't get any packets through. I have also added local and remote networks and tried to recreate the tunnel.
Unfortunately, this no longer works as before. What am I doing wrong? I am following the instructions 1:1 see open.
Tunnel opens (without error messages) but I can neither ping from the firewall itself nor from the LANs directly to each other. Is there any BUG here? I have tried for hours to test this. I also tested 2 virtual pfsense cloud machines, unfortunately all without success...
THANK YOU!
-
@mako said in Routing Firewall A over IPSec to Firewall B:
After the update I set up Site 2 Site using TLS certificates as described here:
https://docs.netgate.com/pfsense/en/latest/recipes/openvpn-s2s-tls.htmlDid you do all steps described there?
When you running OpenVPN in TLS mode, you have to configure a CSO for each connected client to route the packets properly, even if you have only a single client.
In the CSO you have to enter the client site network and as well in the server settings at "Remote Networks".
-
@viragomann
Thank you yes, that sovled my problem. i has not used client specific override. now it works perfectly.thank you so much!
-
@viragomann said in Routing Firewall A over IPSec to Firewall B:
@mako said in Routing Firewall A over IPSec to Firewall B:
but when i try now add a NAT rule on Firewall A (WAN-IP:8080) and want use the destination address 192.168.99.X:8080, then i get this not working.
This does not work with policy-based IPSec. Response packets of the destination device will be routed out to the default gateway.
The only option to make it work would be to route the whole internet traffic of the concerned device to the remote site and go out on its WAN.You can do this with OpenVPN, Wireguard or maybe routed IPSec (VTI), however.
That is not intirely true. There is a workaround that I’m using to allow my two firewalls to talk to each other using their LAN Static Ip address.
The trick is to create a gateway on both firewall with their own LAN ip address as the gateway address.
After that you create a static route to the remote LAN subnet using that gateway.
It will have no impact on policy routing of client traffic, but the firewalls own traffic towards the remote subnet, will now follow the static route and be egressed on its LAN interface (using the LAN IP) thus causing them to speak LAN IP to LAN IP :-) -
@keyser said in Routing Firewall A over IPSec to Firewall B:
There is a workaround that I’m using to allow my two firewalls to talk to each other using their LAN Static Ip address.
Agree, your workaround enables the IPSec endpoints to talk to each other. But the primary issue of this thread is to forward public requests over the VPN to a device at the remote site. And this cannot be done with policy-based IPSec, as long as you do not nat the packets to the LAN address on the remote, but this is mostly not wanted.