IPsec VPN with Active Directory RADIUS/NPS and 2FA
-
I've configured an IPSec VPN as documented here. After some help from the community, I was able to make the configuration work with a standard Windows 11 client.
I've now set down the path of trying to see if I can incorporate 2FA using the NPS extension. I've followed the directions at on how to integrate Network Policy Server (NPS) with Microsoft Entra multifactor authentication.
After installing the NPS extension, I can no longer successfully authenticate against NPS from the Diagnostics/Authentication page with RADIUS. Looking at the logs on the firewall I see:

I however never get the Authenticator prompt to approve my sign-on in the app. Looking at the logs on the NPS Server I see:
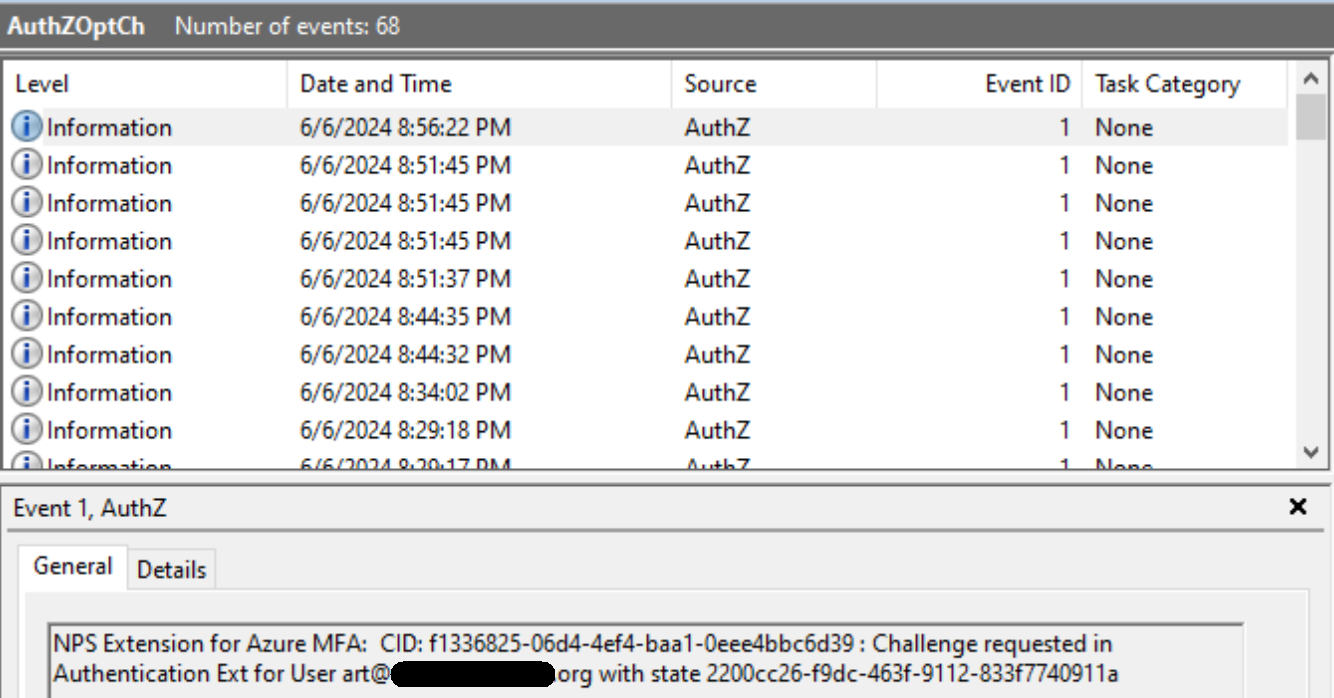
If I disable the NPS Extension, RADIUS sign in (and subsequent the VPN session) works fine. I can confirm that 2FA via the authenticator app is working without issue by attempting to sign into portal.azure.com as that account and going through the MFA process.
Any thoughts on wheret to look or what to look at?
-
@codechurn You need to configure the radius timeout in pfSense in two places actually:
1: Under SYSTEM -> USER MANAGER -> Authentication Servers: You need to fill out the empty “authentication timeout” to fx. 60sec to allow the pfsense system connection to wait for the user to approve the wto factor login.
2: You also need to configure the IPSec VPN component to wait for a radius answer. This is done under VPN -> IPSEC -> Mobile Client -> “Advanced Radius parameters” which you basically just need to tick and setup for fx a 60sec timeout and one retry (instead of 4)
You faillure happens because of the very quick default radius timeout (couple of secs) pfsense has if this is not configured.
-
I bumped up the Authentication Timeout for Radius
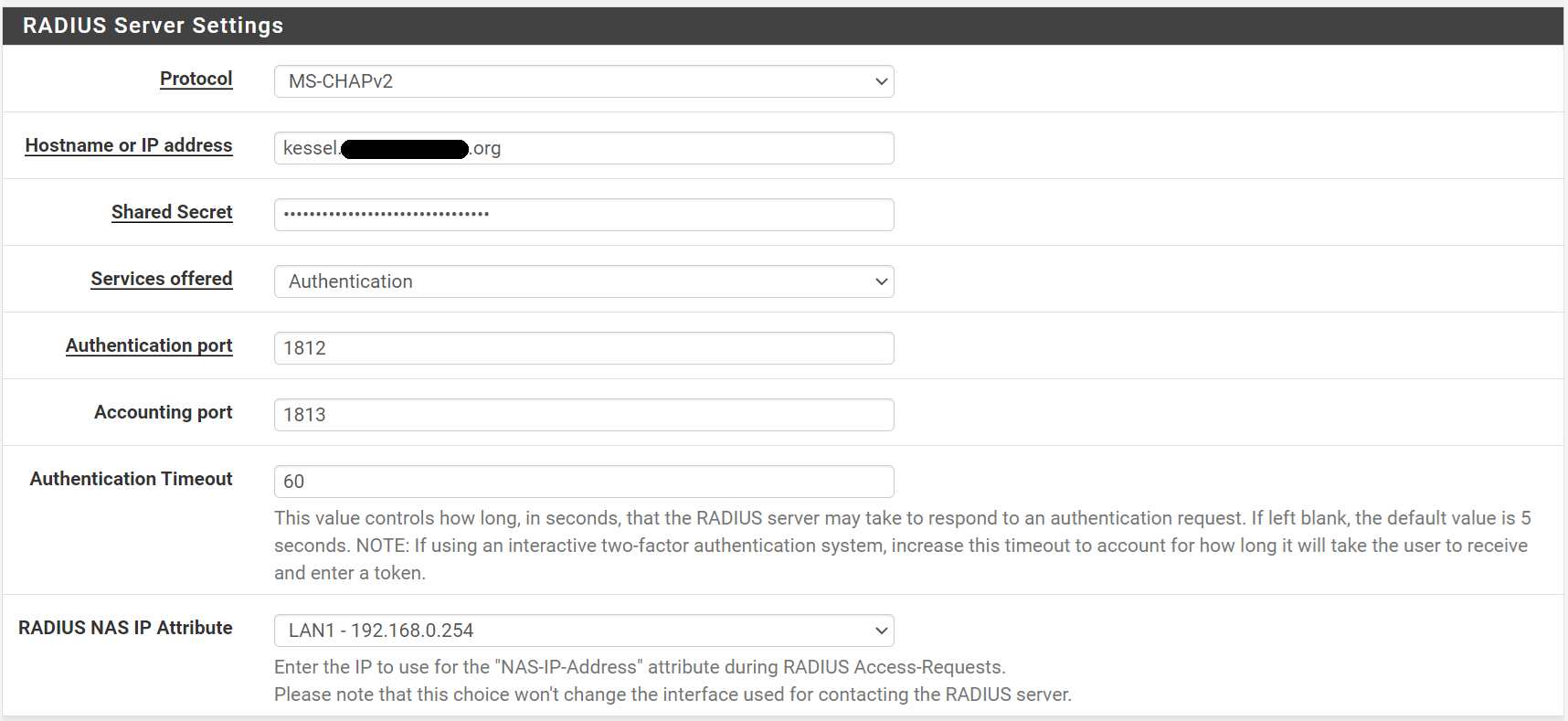
However, when I attempt to test RADIUS authentication via the Diagnostics | Authentication menu it still fails. I am assuming this should work and I should get a 2FA push notification on my Authenticator app.
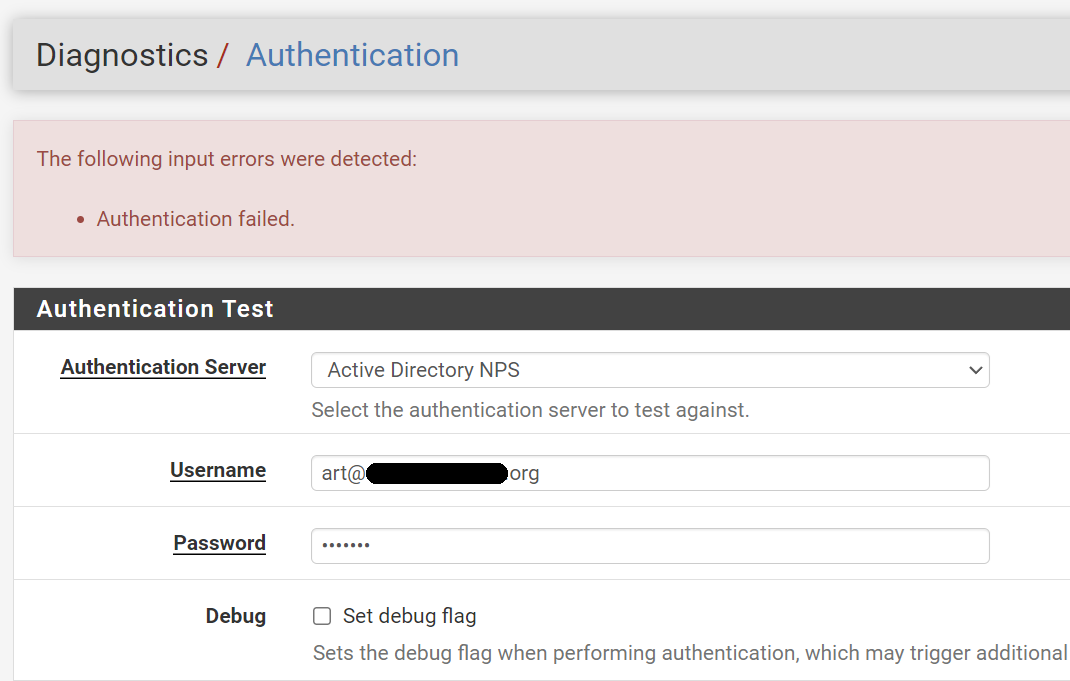
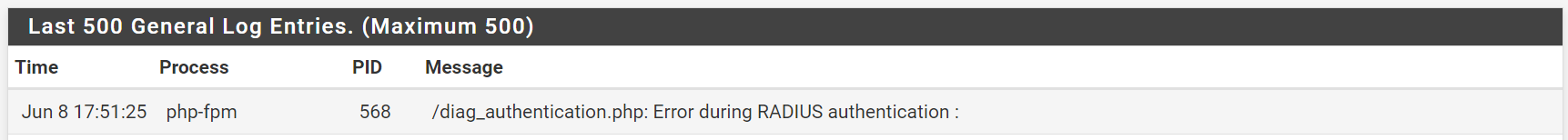
Why is there now error in the above message?
Looking at the logs on the NPS server I see:
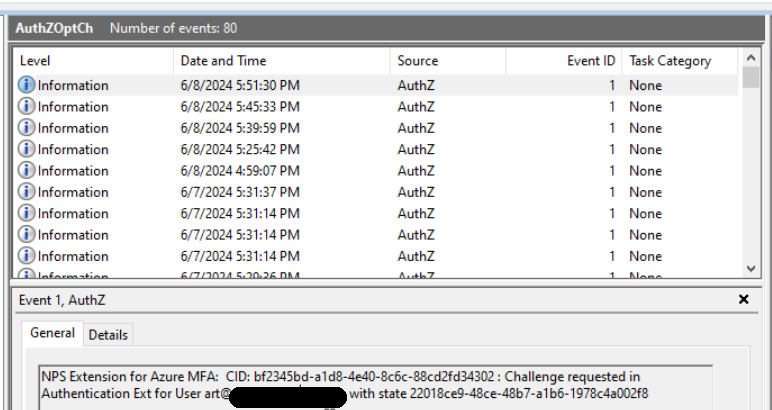
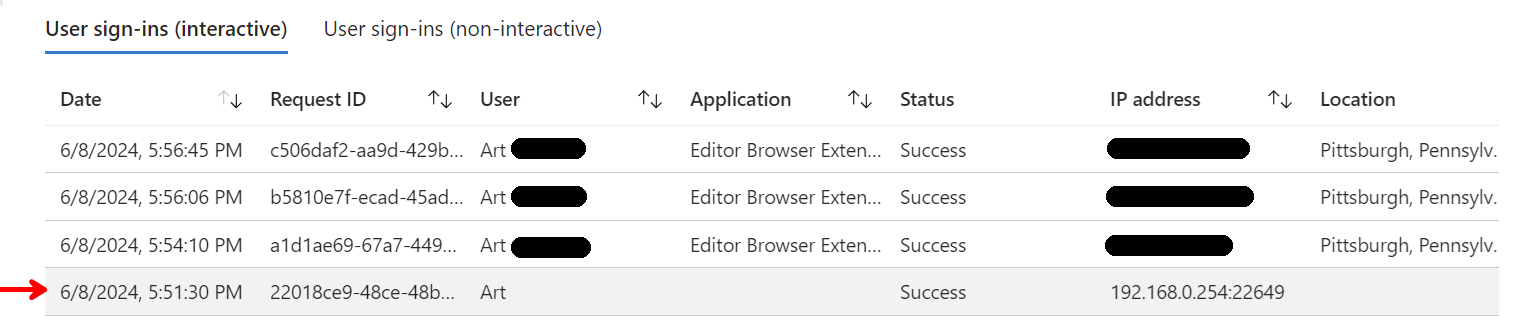
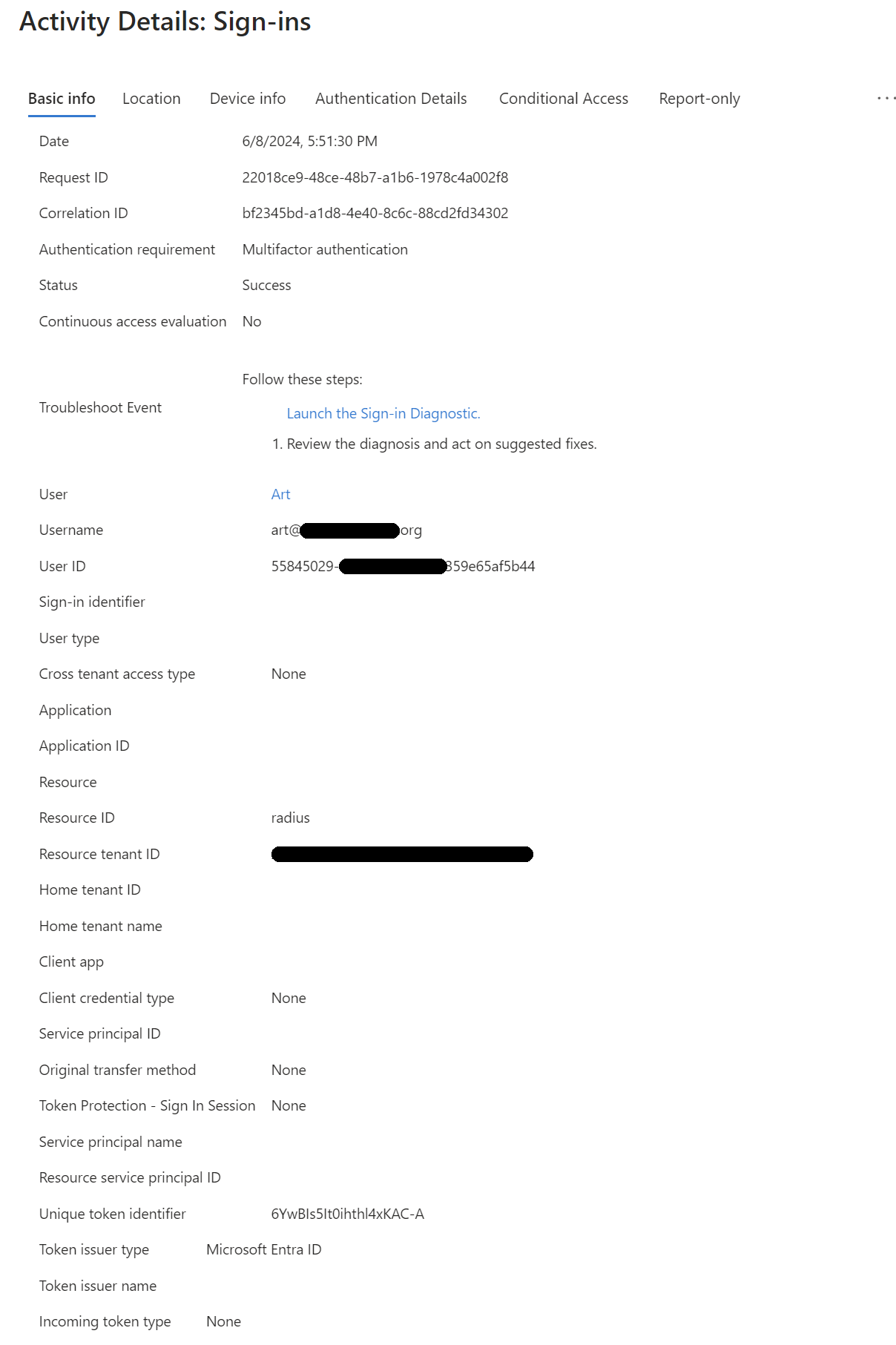
I feel like I am missing something here.
-
I found the missing link!
On the NPS server, I had to set the following registry entry:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\AzureMf Create the following String/Value pair: Name: OVERRIDE_NUMBER_MATCHING_WITH_OTP Value = FALSEThen I had to restart the Network Policy Service and BINGO! I got the approve sign-in notification on my phone when I tested the RADIUS logon. Because I had number matching turned on in my tenant, the extension was falling back to TOTP which obviously won't work with MSCHAPv2.
See this link:
https://learn.microsoft.com/en-us/entra/identity/authentication/how-to-mfa-number-match#nps-extension