DNS Resolver, DNSSEC, and Harden DNSSEC Data
-
@johnpoz The reason of asking, because use pfBlockerNG unbound python mode. If follow netgate docs, there explain that if dnssec unticked python modul will not working. So, actually DNSSEC support not important for me , but in doubt will Python Module Script for pfBlockerNG in DNS unbound resolver work in this case?
-
@johnpoz The link you provided for Quad9 have this:
Caching
It is imperative that your DNS forwarders are configured to cache response data in order to avoid excessive recursive queries to Quad9 and to provide significantly faster DNS resolution for devices on the network.Ensure that your DNS forwarders have enough memory or disk space allocated to the cache to avoid the cache filling up.
The amount of memory that should be dedicated to DNS caching varies greatly from megabytes to gigabytes based on the amount of DNS requests originating from your network endpoints.
How can be checked in pfSense the amount of memory dedicated to DNS caching?
-
@Antibiotic way to hone in what is a non-sequitur for sure...
But did you click the unbound tab in that section?
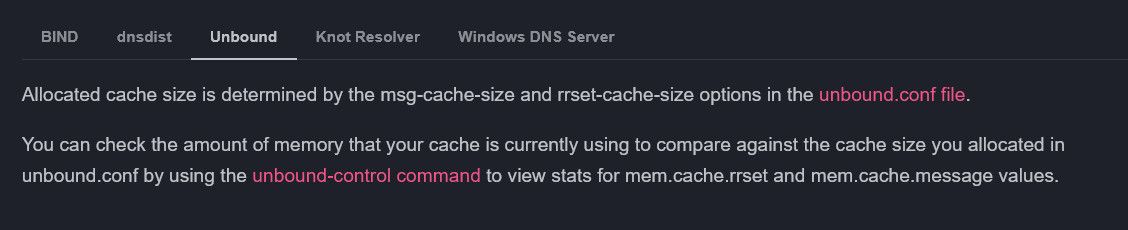
Unless your running pfsense in some enterprise with 1000s and 1000s of clients I doubt you would have to touch from the defaults.
Default in unbound is 10k hosts.. Are you anywhere close to that? This is how many host records it will cache... If you hit that limit it will start purging older records from the cache, maybe before their ttl has expired.. But I would find it surprising if you were anywhere close to that.. You can bump it up in the advanced section
-
@johnpoz Ok, thanks but what about than pfBlockerNg python script?
-
@Antibiotic what about it? Are not the stuff unbound loads local records? Those would not be cached items, ie something unbound looked up from say quad9 servers and then cached for the life of the ttl, etc.
-
@johnpoz I mean from docs;
Python Module Order
:
Controls the position of the Python module in the DNS resolution process. If DNSSEC is disabled, this option has no effect.If DNSSEC disabled will python SCRIPT module than work?
Do not asking about Pre Validator or Post Validator.
: -
@Antibiotic What part do you not understand if you forward to something that does dnssec, there is ZERO to do on your end.. Trying to do anything with dnssec if you forward is wheel spinning for zero benefit..
Yeah there is zero point to your local anything trying to do validation of dnssec, if where you forward is doing it already!!!
What part is unclear with " If DNSSEC is disabled, this option has no effect."
Well yeah what would any sort of local validation have do do anything... That is for when your actually resolving and doing your own validation of the dnssec info..
-
@johnpoz
Im trying to understand not regarding DNSSEC , will in this case to work pfBlockerNg unbound python script. If DNSSEC disabled, than pfBlockerng SHOULD set than in old Unboud mode ?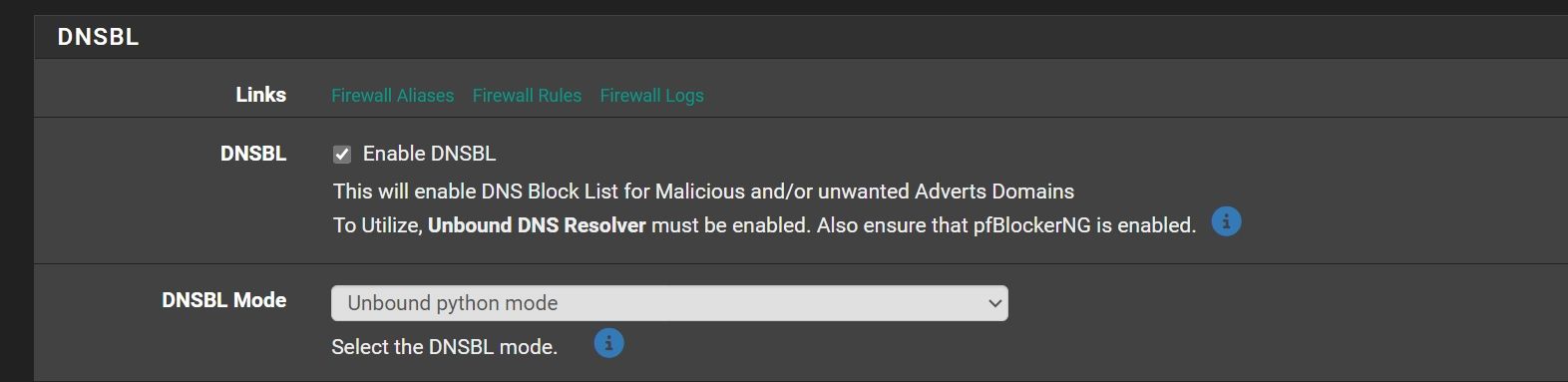
-
@Antibiotic that has zero to do with dnssec, zero.. You do not need dnssec at all for that to function. Be it your doing it local via your actually resolving in unbound, or where you forward does dnssec for you, or it doesn't
But yeah you need to be using unbound, either in resolver mode, forwarder mode, forwarder TLS mode, etc.
-
@johnpoz So, finally to be clear. At this case better to use pfBlockerNG DNSBL mode in Unbound mode not Unbound python mode ?
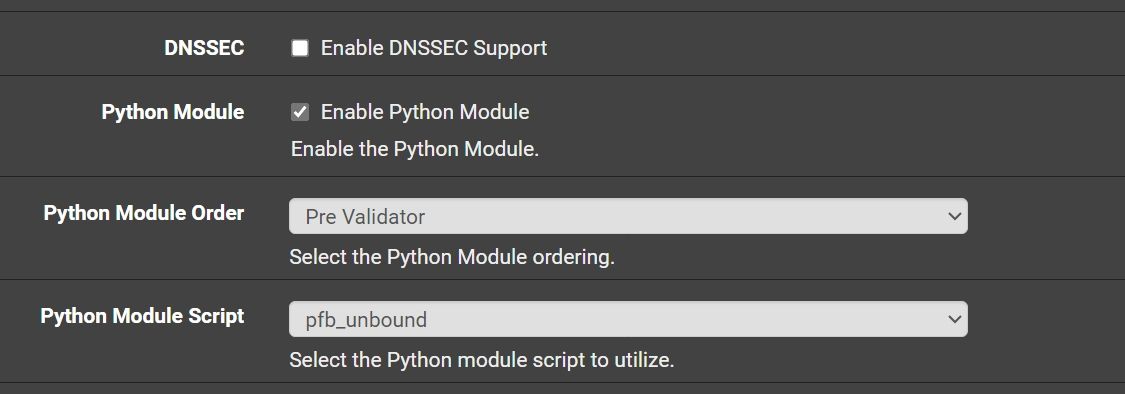
Python Module Order and Python Module Script , two different functions? They are not depend from each other?
-
@Antibiotic did you not click the little info i ?
Not sure what your not grasping??
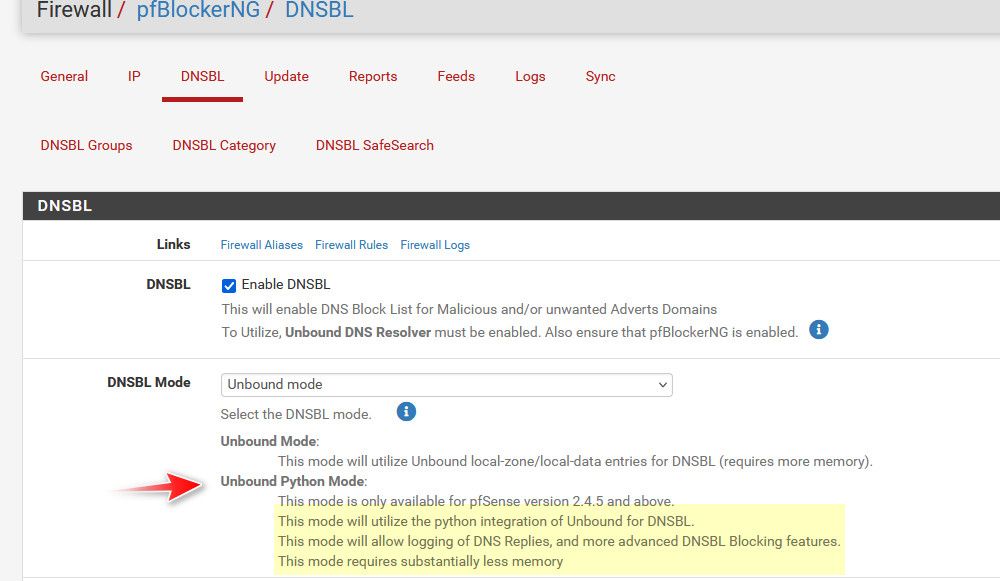
No the module order has to do if using dnssec, the script you use would have nothing to do with that.. If you want to use the pfblocker script, then yes you would need to have python modules enabled.
-
@johnpoz Ok, thanks. Are you using Unbound mode not Unbound python mode. Can me asking why? Why do you prefer first and not Unbound python mode?
-
@Antibiotic I am not using pfblocker for dnsbl - I only use it to create aliases that I use in my firewall rules myself. So I have no use for it.