LAN Clients cannot see OPT1 Client
-
Question: How do I allow my Desktop on network 192.168.1.0/24 talk to my laptop on a different physical port with network 192.168.2.0/24. Dunno if this is a NAT or Routing question.
I have a Protectli Vault running pfSense 2.7.2-RELEASE to protect my home network devices (and more).
It runs an OpenVPN Client that connects all devices to a VPN service. However, some of my streaming devices do not work connected to a VPN, therefore forcing me to connect my WiFi AP hardware to a port not protected by the VPN service.
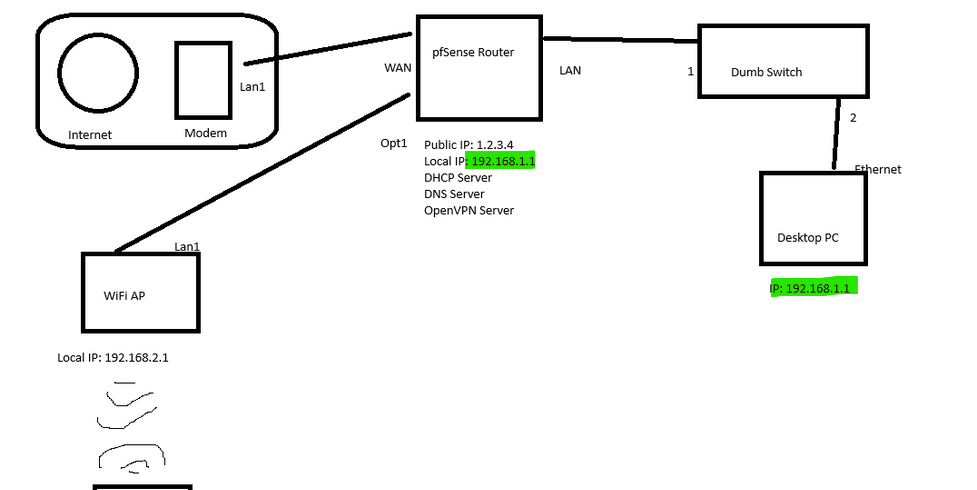
My network looks like this diagram:
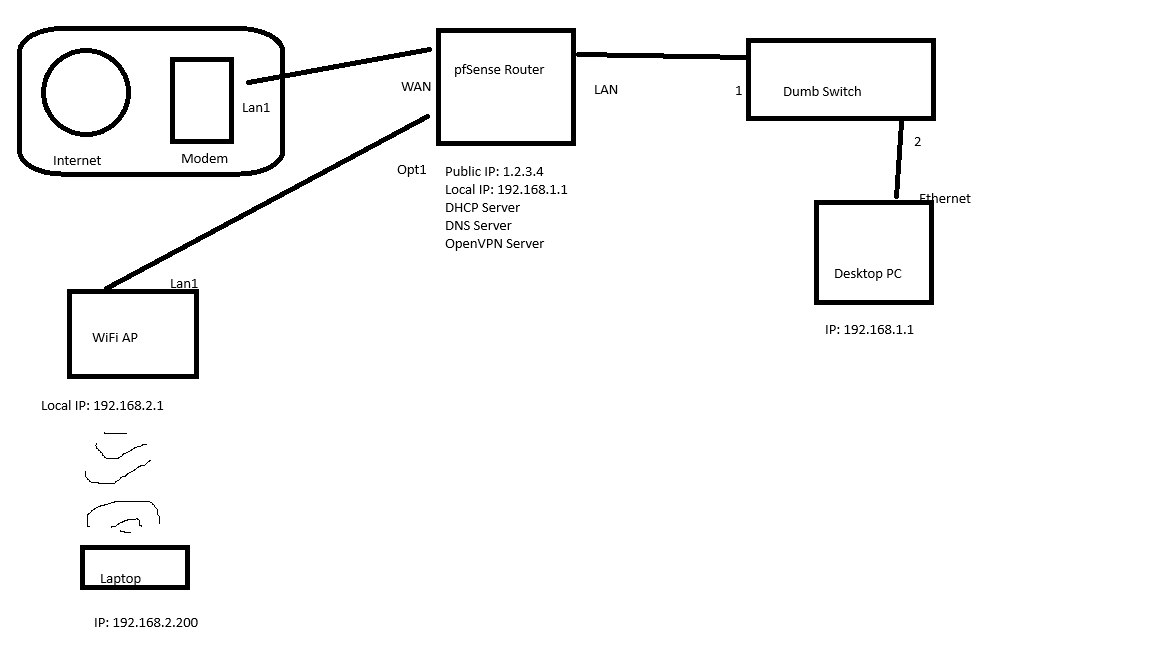
- I have one of those ISP-provided modem/routers with limited functionality. An "IP Passthrough" setting forwards my public IP address (1.2.3.4) and all traffic to the pfSense router, This effectively makes it the public facing device.
- The "pfSense router" has 4 ethernet ports on it: WAN, LAN, OPT1, and OPT2
- The WAN port connects to the modem, and with the passthrough settings, makes this the main router.
- The LAN port connects to a "dumb switch" and is connected to my Desktop + some other physically connected devices on the network. Everything connected here has an IP of 192.168.1.X
- I have an OpenWRT WiFi router connected to the OPT1 port of the device configured in "Access Point" mode. This Wifi device has DHCP disabled and that functionality is handled by the main pfSense device. Anything connected over WiFi gets assigned an address of 192.168.2.X and is NOT protected by the VPN service
- Yes, I would connect every single device to the pfSense LAN port with VPN protection if not for the streaming services throwing a fit. Also my laptop is a bit dated and does not handle ethernet connections well, hence the wifi necessity.
My laptop connects to my network via WiFi (192.168.2.200) and my desktop connects via ethernet cable (192.168.1.100). I want both devices to be able to talk to each other when I am at home. They are on two separate subnets due to my personal configuration, but I do not 100% know if this is fixable via a NAT setting or Routing setting (or both?).
For now I just want to all the devices on my local network to be able to communicate regardless or being on the hardline network or wifi network. Any guidance or pointers would be appreciated. I have a decent understanding of networking, but the concept of NAT and advanced routing is a bit outside of my knowledge sphere for the moment (will get there eventually)
-
@mrzander https://docs.netgate.com/pfsense/en/latest/multiwan/policy-route.html#figure-multiwan-bypass-policy-routing
-
@mrzander said in LAN Clients cannot see OPT1 Client:
Question: How do I allow my Desktop on network 192.168.1.0/24 talk to my laptop on a different physical port with network 192.168.2.0/24. Dunno if this is a NAT or Routing question.
I have a Protectli Vault running pfSense 2.7.2-RELEASE to protect my home network devices (and more).
It runs an OpenVPN Client that connects all devices to a VPN service. However, some of my streaming devices do not work connected to a VPN, therefore forcing me to connect my WiFi AP hardware to a port not protected by the VPN service.
My network looks like this diagram:

- I have one of those ISP-provided modem/routers with limited functionality. An "IP Passthrough" setting forwards my public IP address (1.2.3.4) and all traffic to the pfSense router, This effectively makes it the public facing device.
- The "pfSense router" has 4 ethernet ports on it: WAN, LAN, OPT1, and OPT2
- The WAN port connects to the modem, and with the passthrough settings, makes this the main router.
- The LAN port connects to a "dumb switch" and is connected to my Desktop + some other physically connected devices on the network. Everything connected here has an IP of 192.168.1.X
- I have an OpenWRT WiFi router connected to the OPT1 port of the device configured in "Access Point" mode. This Wifi device has DHCP disabled and that functionality is handled by the main pfSense device. Anything connected over WiFi gets assigned an address of 192.168.2.X and is NOT protected by the VPN service
- Yes, I would connect every single device to the pfSense LAN port with VPN protection if not for the streaming services throwing a fit. Also my laptop is a bit dated and does not handle ethernet connections well, hence the wifi necessity.
My laptop connects to my network via WiFi (192.168.2.200) and my desktop connects via ethernet cable (192.168.1.100). I want both devices to be able to talk to each other when I am at home. They are on two separate subnets due to my personal configuration, but I do not 100% know if this is fixable via a NAT setting or Routing setting (or both?).
For now I just want to all the devices on my local network to be able to communicate regardless or being on the hardline network or wifi network. Any guidance or pointers would be appreciated. I have a decent understanding of networking, but the concept of NAT and advanced routing is a bit outside of my knowledge sphere for the moment (will get there eventually)
This is done by firewall rules only.
By default, the LAN has access to anything, you would have to add a rule on the OPT to allow access to the LAN. For now just copy the LAN's ANY/ANY rule to the OPT. You can then adjust it as necessary.
If you already have the needed rules on both interfaces, then turn off the software firewall on the pc's since, by default, it will block other subnets. -
@Antibiotic It took a tiny bit of tweaking, but this link gave me the answer. Thanks for the pointer!
In case anyone wants to try something similar in the future, here's what I changed:
In Firewall > Rules > LAN Tab, I added this second row:
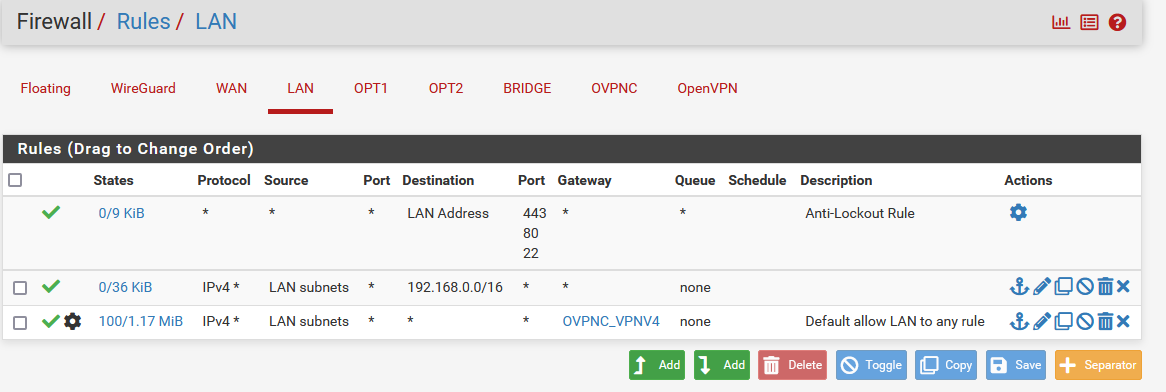
Then I tweaked the Bridge (which combines the OPT1 and OPT2 as a single interface; I mistakenly said OPT1 above but the same concept still should apply) to add a reverse of the rule:
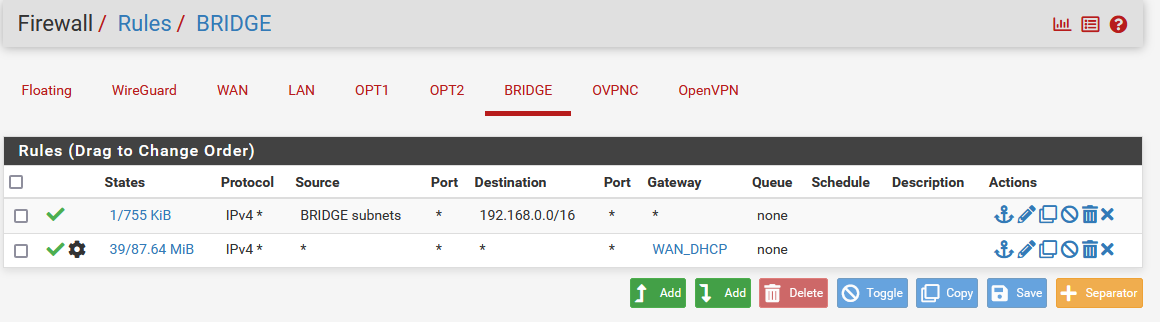
Now both machines are able to communicate with each other.
Note: as others have mentioned, some operating systems (such as Win 10/11) block ping requests by default, so be sure to add a rule to your machine's firewall.
Cheers!
-
If pfSense uses (the default) 192.168.1.1 then your desktop PC should not be using 192.168.1.1. if it does, yes, major issues ahead.
-
@Gertjan Oof, also a typo. The desktop actually ends with 100, not 1. I'll make an edit. That WOULD be a disaster.