Open up a vlan ip to the outside
-
@rashadmahmood do your AP support vlans? You can for sure segment out your wifi ssids to different networks if you desire. But your cameras are not over wifi are they? You really wouldn't need a wifi segment for your cameras if they are wired.
And again - your cameras are not going to be saturating the wire or anything, not with 4 of them.. But I would keep traffic between the cameras and the nvr on a completely different network than your normal network traffic. If your wanting to segment it out, might as well keep it from riding over the same wires as your normal network if possible.
For example - lets say your cameras are doing 40mbps per second.. If that rides over the same wire as your normal traffic to your router as all your other traffic for other networks, or even over the same wire to say your nvr machine. That is 40mbps that is used that your devices can't use.. Or if you saturate that link with other traffic, maybe your cameras have issues with recording..
It is best if possible to put this sort of traffic on its own wires so that it doesn't compete or interfere with your normal day to day network traffic.
its not the end of the world if you can't, and it might never be problem - but if your going to take the time to set it up on its own network anyway, might as well keep this traffic off your normal day to day connections.
-
yep the access points can do vlans.
@johnpoz said in Open up a vlan ip to the outside:
It is best if possible to put this sort of traffic on its own wires so that it doesn't compete or interfere with your normal day to day network traffic.
absolutely agree, I will do this, thanks so much for your help and advice!
-
@rashadmahmood said in Open up a vlan ip to the outside:
What is the best way to deal with this? My understanding is that you want to segment the CCTV LAN; otherwise, the whole network would be broadcasting all over the place. With a VLAN, I can confine this to the CCTV LAN.
Does your NVR have 2 ports? If so, you use one to access the NVR from elsewhere and one for an isolated LAN for your cameras.
-
thanks, yes I will separate the camera network from the NVR.
-
@rashadmahmood keep in mind if your going to multihome this box your using as your nvr. The interface you add to the cam network you create wouldn't have a gateway set, nor dns on this interface.
I would just have an IP with proper mask for the network your attaching it too.
-
You mean such as 192/168.0.1/24 (proper subnet mask?) and omit the gateway?
-
@rashadmahmood yeah your just going to use this interface to talk to cameras on this same network - you would not want your pc being used as nvr to use it for any other connections to other networks - so there would be no gateway set on it.
-
Many thanks
-
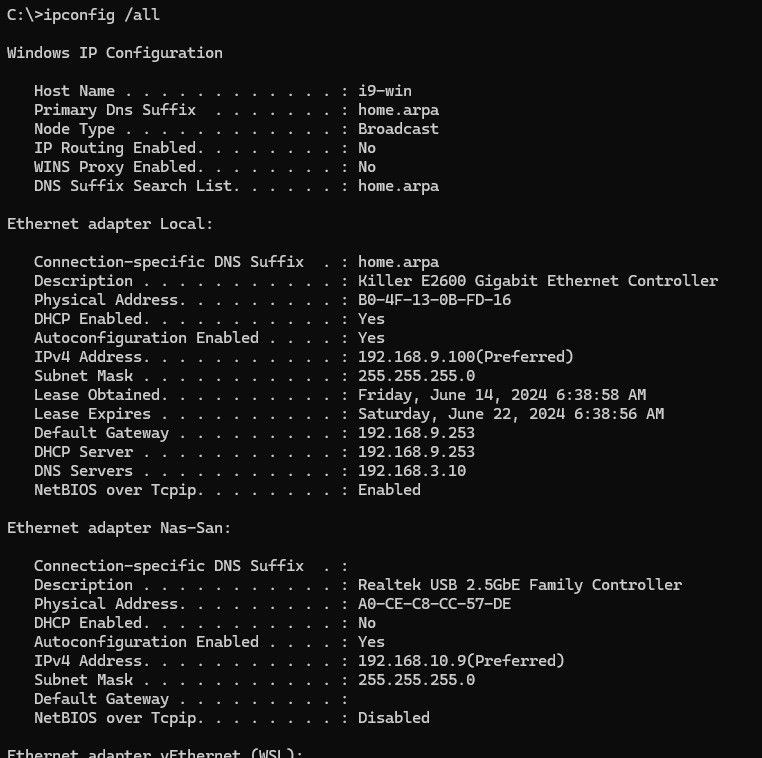
@rashadmahmood example - my main pc connection to my nas at 2.5ge.. That I use only to move files back and forth from my pc and nas.
This network 192.168.10/24 isn't use for anything else.. Kind of like the network your pc/nvr will user to talk to the cameras..
if I want to talk to the nas for say admin of the nas, then I talk to it on its 192.168.9 IP address.
-
@johnpoz perfect, thanks!
-
@johnpoz said in Open up a vlan ip to the outside:
so there would be no gateway set on it
Unless the device needs a gateway set. Then just use the NVR or a dummy address.
-
@JKnott said in Open up a vlan ip to the outside:
Unless the device needs a gateway set.
Why would the windows PC with a 2nd nic added it to it need a gateway on the interface?
This not the cameras - this is the PC he is using as his NVR.
"It's a PC running Windows 10 with AXIS Camera Station 5 software"
-
The 1st NIC connected to the network (for the purpose of viewing the server/software) would require a gateway - correct?
The 2nd NIC connected to the cameras via a POE switch does not require a gateway?Have I understood this correctly?
Also can I use the same POE switch for bother camera (different network) and other lan devices (again another network)?
-
So I'm thinking of implementing the following
Network 1:
Subnet: 192.168.0.0/24
Gateway: 192.168.0.1 (pfSense)
Windows machine for viewing cameras: Assign a unique IP within the range, e.g., 192.168.0.10/24
Other LAN devices: Assign unique IPs within the range.
VLAN 1:VLAN 1 Interface for Access Point 1: 192.168.0.2/24
VLAN 1 Interface for Access Point 2: 192.168.0.3/24Network 2 (CCTV):
Subnet: 10.0.0.0/25
NIC 2 of the Windows machine: Assign an IP within this range, e.g., 10.0.0.1 with no gateway
cameras 1 to 4 set with no gatewayExample Configuration:
pfSense Gateway: 192.168.0.1/24
Windows Machine NIC 1 (Network 1): 192.168.0.10/24
Windows Machine NIC 2 (Network 2): 10.0.0.1/25
Access Point 1: 192.168.0.2
Access Point 2: 192.168.0.3Also create a vpn to access the 192.168.0.0/24 network
Apologies, its been a while since I messed with network configs.
-
@johnpoz said in Open up a vlan ip to the outside:
Why would the windows PC with a 2nd nic added it to it need a gateway on the interface?
Over the years I have come across some devices that required all the setting to be configured, including gateway whether it was needed or not. I'm not saying that will happen here, but it's always possible.
-
Yes, that's correct and yes you can use the same PoE switch, provided it supports VLANs.
-
@JKnott - yep its a managed switch
-
@JKnott said in Open up a vlan ip to the outside:
, but it's always possible.
What part are you not getting that this is a Windows PC??
His cameras should point to pfsense as their gateway.. That is if he wants them to talk to the internet to say get firmware updates. Or if he wants to talk to them directly via his vpn connection without doing source natting. Or any other local networks.
-
refering to this:
@rashadmahmood said in Open up a vlan ip to the outside:
So I'm thinking of implementing the following
Network 1:
Subnet: 192.168.0.0/24
Gateway: 192.168.0.1 (pfSense)
Windows machine for viewing cameras: Assign a unique IP within the range, e.g., 192.168.0.10/24
Other LAN devices: Assign unique IPs within the range.
VLAN 1:VLAN 1 Interface for Access Point 1: 192.168.0.2/24
VLAN 1 Interface for Access Point 2: 192.168.0.3/24Network 2 (CCTV):
Subnet: 10.0.0.0/25
NIC 2 of the Windows machine: Assign an IP within this range, e.g., 10.0.0.1 with no gateway
cameras 1 to 4 set with no gatewayExample Configuration:
pfSense Gateway: 192.168.0.1/24
Windows Machine NIC 1 (Network 1): 192.168.0.10/24
Windows Machine NIC 2 (Network 2): 10.0.0.1/25
Access Point 1: 192.168.0.2
Access Point 2: 192.168.0.3Also create a vpn to access the 192.168.0.0/24 network
Apologies, its been a while since I messed with network configs.
So I need to add the gateway into the 2nd LAN, it does kind of make sense for updating firmwares etc..
-
@rashadmahmood I would set your cameras with pfsense as their gateway, they are not multihomed, etc.. If you want to talk to them directly from any other local network or via your vpn.. They need to be able to talk back..
The only device that you would not set a gateway on is your NVR box that you will have multihomed..