Open up a vlan ip to the outside
-
Many thanks
-
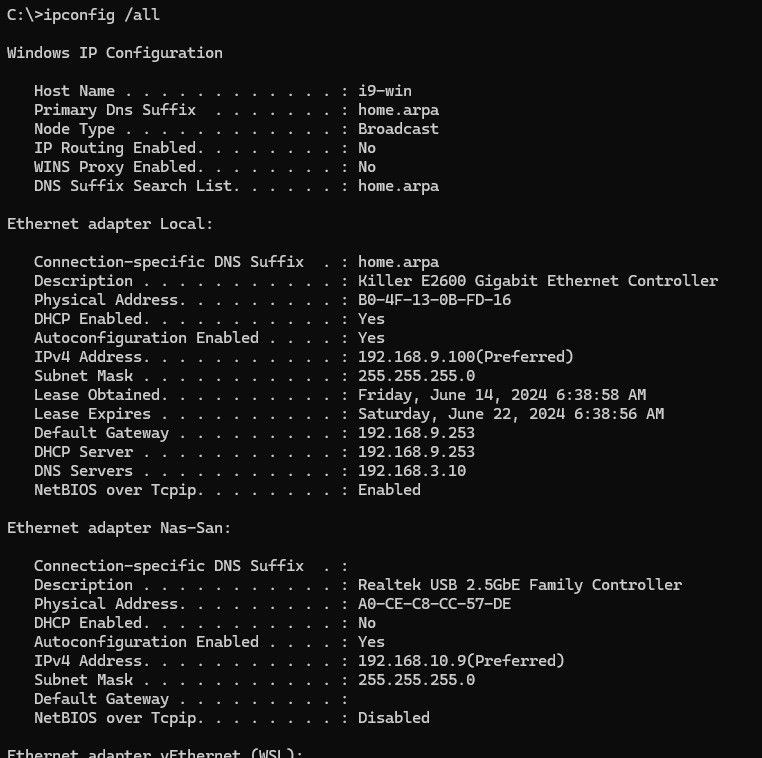
@rashadmahmood example - my main pc connection to my nas at 2.5ge.. That I use only to move files back and forth from my pc and nas.
This network 192.168.10/24 isn't use for anything else.. Kind of like the network your pc/nvr will user to talk to the cameras..
if I want to talk to the nas for say admin of the nas, then I talk to it on its 192.168.9 IP address.
-
@johnpoz perfect, thanks!
-
@johnpoz said in Open up a vlan ip to the outside:
so there would be no gateway set on it
Unless the device needs a gateway set. Then just use the NVR or a dummy address.
-
@JKnott said in Open up a vlan ip to the outside:
Unless the device needs a gateway set.
Why would the windows PC with a 2nd nic added it to it need a gateway on the interface?
This not the cameras - this is the PC he is using as his NVR.
"It's a PC running Windows 10 with AXIS Camera Station 5 software"
-
The 1st NIC connected to the network (for the purpose of viewing the server/software) would require a gateway - correct?
The 2nd NIC connected to the cameras via a POE switch does not require a gateway?Have I understood this correctly?
Also can I use the same POE switch for bother camera (different network) and other lan devices (again another network)?
-
So I'm thinking of implementing the following
Network 1:
Subnet: 192.168.0.0/24
Gateway: 192.168.0.1 (pfSense)
Windows machine for viewing cameras: Assign a unique IP within the range, e.g., 192.168.0.10/24
Other LAN devices: Assign unique IPs within the range.
VLAN 1:VLAN 1 Interface for Access Point 1: 192.168.0.2/24
VLAN 1 Interface for Access Point 2: 192.168.0.3/24Network 2 (CCTV):
Subnet: 10.0.0.0/25
NIC 2 of the Windows machine: Assign an IP within this range, e.g., 10.0.0.1 with no gateway
cameras 1 to 4 set with no gatewayExample Configuration:
pfSense Gateway: 192.168.0.1/24
Windows Machine NIC 1 (Network 1): 192.168.0.10/24
Windows Machine NIC 2 (Network 2): 10.0.0.1/25
Access Point 1: 192.168.0.2
Access Point 2: 192.168.0.3Also create a vpn to access the 192.168.0.0/24 network
Apologies, its been a while since I messed with network configs.
-
@johnpoz said in Open up a vlan ip to the outside:
Why would the windows PC with a 2nd nic added it to it need a gateway on the interface?
Over the years I have come across some devices that required all the setting to be configured, including gateway whether it was needed or not. I'm not saying that will happen here, but it's always possible.
-
Yes, that's correct and yes you can use the same PoE switch, provided it supports VLANs.
-
@JKnott - yep its a managed switch
-
@JKnott said in Open up a vlan ip to the outside:
, but it's always possible.
What part are you not getting that this is a Windows PC??
His cameras should point to pfsense as their gateway.. That is if he wants them to talk to the internet to say get firmware updates. Or if he wants to talk to them directly via his vpn connection without doing source natting. Or any other local networks.
-
refering to this:
@rashadmahmood said in Open up a vlan ip to the outside:
So I'm thinking of implementing the following
Network 1:
Subnet: 192.168.0.0/24
Gateway: 192.168.0.1 (pfSense)
Windows machine for viewing cameras: Assign a unique IP within the range, e.g., 192.168.0.10/24
Other LAN devices: Assign unique IPs within the range.
VLAN 1:VLAN 1 Interface for Access Point 1: 192.168.0.2/24
VLAN 1 Interface for Access Point 2: 192.168.0.3/24Network 2 (CCTV):
Subnet: 10.0.0.0/25
NIC 2 of the Windows machine: Assign an IP within this range, e.g., 10.0.0.1 with no gateway
cameras 1 to 4 set with no gatewayExample Configuration:
pfSense Gateway: 192.168.0.1/24
Windows Machine NIC 1 (Network 1): 192.168.0.10/24
Windows Machine NIC 2 (Network 2): 10.0.0.1/25
Access Point 1: 192.168.0.2
Access Point 2: 192.168.0.3Also create a vpn to access the 192.168.0.0/24 network
Apologies, its been a while since I messed with network configs.
So I need to add the gateway into the 2nd LAN, it does kind of make sense for updating firmwares etc..
-
@rashadmahmood I would set your cameras with pfsense as their gateway, they are not multihomed, etc.. If you want to talk to them directly from any other local network or via your vpn.. They need to be able to talk back..
The only device that you would not set a gateway on is your NVR box that you will have multihomed..
-
Network 1:
Subnet: 192.168.0.0/24
Gateway: 192.168.0.1 (pfSense)
Windows machine for viewing cameras: Assign a unique IP within the range, e.g., 192.168.0.10/24 - dont set gateway
Other LAN devices: Assign unique IPs within the range.
VLAN 1:VLAN 1 Interface for Access Point 1: 192.168.0.2/24
VLAN 1 Interface for Access Point 2: 192.168.0.3/24Network 2 (CCTV):
Subnet: 10.0.0.0/25
NIC 2 of the Windows machine: Assign an IP within this range, e.g., 10.0.0.1 with gateway of lan1 192.168.0.1
cameras 1 to 4 set with gateway of lan1 192.168.0.1Example Configuration:
pfSense Gateway: 192.168.0.1/24
Windows Machine NIC 1 (Network 1): 192.168.0.10/24
Windows Machine NIC 2 (Network 2): 10.0.0.1/25
Access Point 1: 192.168.0.2
Access Point 2: 192.168.0.3Also create a vpn to access the 192.168.0.0/24 network
Does this make sense?
-
@rashadmahmood Not sure why you are calling out vlan 1 or what IPs your AP are going to be on - what does that have to do with anything?
What vlan are you going to create on your switch for this camera network? It would not be the default vlan 1 if that is the network your putting your normal 192.168.0 network on.
-
the cameras will go in the 10.0.0.0 range, no vlan
-
@rashadmahmood said in Open up a vlan ip to the outside:
no vlan
There needs to be a vlan on your switch.. You don't need to tag it on pfsense, it would jsut be a native - but if you just put it on vlan 1 on your switch there is no actual isolation..
Your vlan you create on yoru switch, lets call it vlan 10, because your going to be using the 10.0.0 network on this network.. Would be access port (ie not tagged) in vlan 10 to your port on pfsense. Then ports your cameras plug into would be also untagged vlan 10 on the switch.
If your on vlan 1 only on the switch - your dhcp isn't going to work for your different networks, any device on vlan 1 on the switch could get either IP from your camera network or your lan network.. All broadcast and multicast would go to all ports, etc. Your cameras could get dhcp from either network, etc.
So yes you need to create a camera network vlan on your switch.
-
I really appreciate the responses, I figured, I throw all this into chatgpt and its has come up with the following
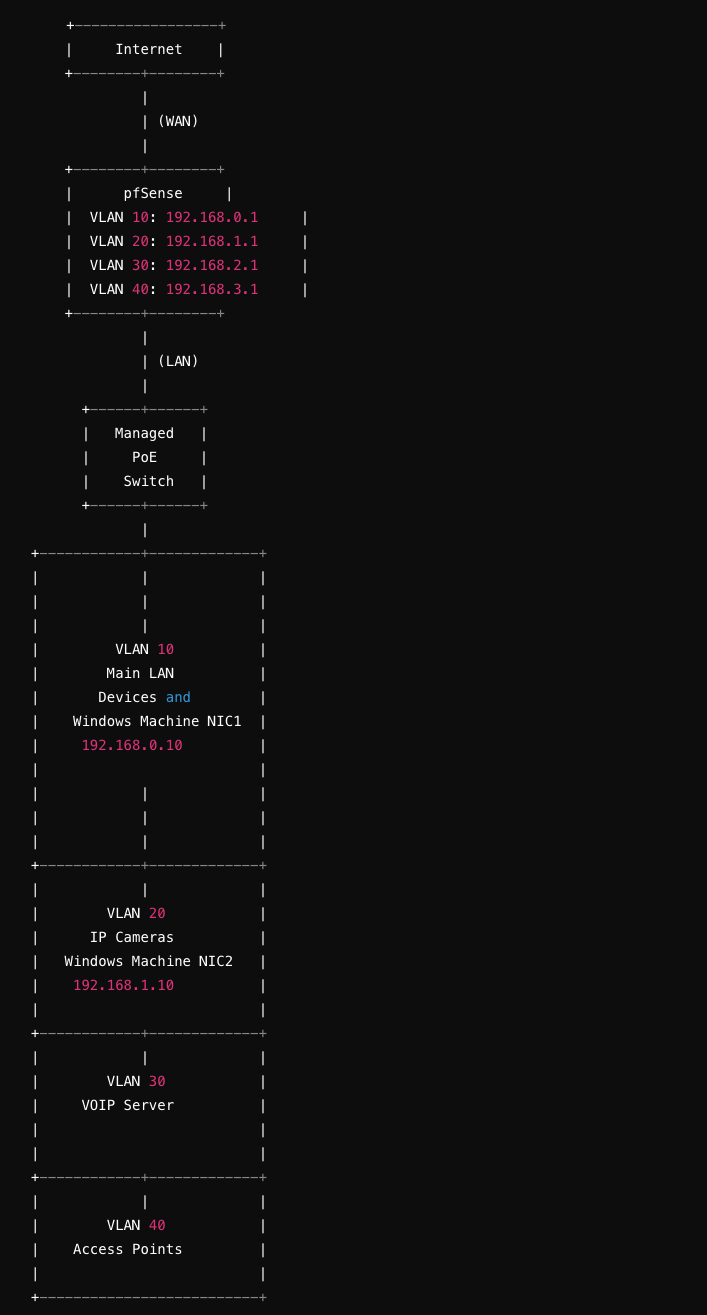
Network Design
Components
- pfSense (Firewall/Router)
- 2 Access Points
- 1 Windows Machine with Two NICs
- NIC1: Network to view cameras
- NIC2: Separate network for the IP cameras (4 cameras)
- 1 VOIP Server
- 1 Managed PoE Switch
- VPN for remote access
- IP Cameras
Requirements
- Privacy between access points and LAN computers
- IP cameras connected to the PoE switch
- VPN access to view cameras remotely
- IP cameras able to access the internet for firmware updates
Network Design with VLANs
Subnets and VLANs
- Main LAN: 192.168.0.0/24 (VLAN 10)
- Gateway: 192.168.0.1 (pfSense)
- Camera Network: 192.168.1.0/24 (VLAN 20)
- Gateway: 192.168.1.1 (pfSense)
- VOIP Network: 192.168.2.0/24 (VLAN 30)
- Gateway: 192.168.2.1 (pfSense)
- Access Points: 192.168.3.0/24 (VLAN 40)
- Gateway: 192.168.3.1 (pfSense)
Network Topology
+-----------------+ | Internet | +--------+--------+ | | (WAN) | +--------+--------+ | pfSense | | VLAN 10: 192.168.0.1 | | VLAN 20: 192.168.1.1 | | VLAN 30: 192.168.2.1 | | VLAN 40: 192.168.3.1 | +--------+--------+ | | (LAN) | +------+------+ | Managed | | PoE | | Switch | +------+------+ | +------------+-------------+ | | | | | | | | | | VLAN 10 | | Main LAN | | Devices and | | Windows Machine NIC1 | | 192.168.0.10 | | | | | | | | | | | | +------------+-------------+ | | | | VLAN 20 | | IP Cameras | | Windows Machine NIC2 | | 192.168.1.10 | | | +------------+-------------+ | | | | VLAN 30 | | VOIP Server | | | | | +------------+-------------+ | | | | VLAN 40 | | Access Points | | | +--------------------------+Configuration Steps
-
pfSense Configuration:
- Configure interfaces for each VLAN:
- VLAN 10: Main LAN (192.168.0.1/24)
- VLAN 20: Camera Network (192.168.1.1/24)
- VLAN 30: VOIP Network (192.168.2.1/24)
- VLAN 40: Access Points (192.168.3.1/24)
- Set up DHCP for each VLAN if needed.
- Configure firewall rules to allow appropriate traffic between VLANs.
- Set up VPN to provide remote access to the camera network.
- Configure interfaces for each VLAN:
-
Managed PoE Switch Configuration:
- Create VLANs:
- VLAN 10: Main LAN
- VLAN 20: Camera Network
- VLAN 30: VOIP Network
- VLAN 40: Access Points
- Assign ports to the respective VLANs.
- Ensure ports connected to IP cameras are in VLAN 20.
- Configure trunk ports for pfSense connection.
- Create VLANs:
-
Access Points Configuration:
- Configure the access points to use VLAN 40 (192.168.3.0/24).
- Set up SSIDs and security settings as required.
-
Windows Machine Configuration:
- NIC1 (Main LAN): Static IP 192.168.0.10, Subnet Mask 255.255.255.0, Gateway 192.168.0.1.
- NIC2 (Camera Network): Static IP 192.168.1.10, Subnet Mask 255.255.255.0, no Gateway.
-
VOIP Server Configuration:
- Assign a static IP in the VOIP Network (e.g., 192.168.2.10).
- Ensure proper VLAN tagging for the VOIP server port.
-
IP Camera Configuration:
- Assign static IPs in the Camera Network (192.168.1.0/24).
- Ensure cameras can reach the internet through pfSense for firmware updates.
- Set up necessary routes and firewall rules on pfSense to allow camera network internet access.
-
VPN Configuration:
- Configure OpenVPN or another VPN solution on pfSense.
- Ensure VPN clients have access to the Camera Network (192.168.1.0/24) and any necessary resources.
Summary
This setup provides separation between different network segments using VLANs, ensuring privacy and security. The managed PoE switch is configured to support multiple VLANs, and pfSense is set up to route traffic and manage firewall rules between these VLANs. VPN allows remote access to the camera network while maintaining security.
-
@rashadmahmood that is with only the 1 physical connection with your vlans running over it..
Just create a new uplink from your switch in say vlan 10, not tagged and connect to pfsense on another interface that you put your 10.0.0 network on..