Allowing random IP/PORT into LAN
-
@wwdot_computers if you want port 25568 that hits you public facing interface (wan) to get forward to some inside machine say 192.168.1.100 that would just be a port forward.
That and then the associated firewall rule that the port forward can auto create for you.. Just need to make sure the rule is in the correct place on your wan so some other rule you might have placed there doesn't block the traffic your trying to allow.
edit: if this is machine A talking to B that are on the same network - as @SteveITS mentions pfsense has nothing to do with that traffic.
-
-
@wwdot_computers but that is outbound traffic - you would have to adjust your rules to allow for the traffic.. So you see that blocked.. By default default deny is logged.. So if your rules do not allow these to talk to something in the cloud, ie the internet then one of your rules is not allowing it.
Did you inherit this set of rules? I would assume someone that created all those would understand how to allow something else..
You say this is inbound
Inbound connectivity on the protected machine:
TCP port 25568 (for Datto Windows Agent service)I find it highly unlikely that some service you backup to in the cloud would need unsolicited inbound traffic from the internet to some machine behind pfsense.. But that would be a port forward.
-
@SteveITS
It was a joint effort? Under guidence I created the rules. However the person that helped is no longer able to do so. Long story.Would you suggest going back through the rules and starting over?
So the inbound connection:
Inbound connectivity on the protected machine:
TCP port 25568 (for Datto Windows Agent service)Is really outbound? How does that track? It seems that they are requesting an inbound connection?
-
@wwdot_computers see my edit.. I have never heard of some backup service to the cloud that would require you to open a port from the internet to your server your backing up - that makes no sense at all.
Unless you have turned off default deny logging that is logged, and your last reject rule is set to log - so if pfsense blocked something from it would be logged
-
Sorry wrong person
@johnpoz
It was a joint effort? Under guidance I created the rules. However, the person that helped is no longer able to do so. Long story.Would you suggest going back through the rules and starting over?
So the inbound connection:
Inbound connectivity on the protected machine:
TCP port 25568 (for Datto Windows Agent service)Is really outbound? How does that track? It seems that they are requesting an inbound connection?
How do I see the edit? New to the forum as well.
-
Here is the KB:
https://continuity.datto.com/help/Content/kb/siris-alto-nas/KB213994246.html -
@wwdot_computers said in Allowing random IP/PORT into LAN:
https://continuity.datto.com/help/Content/kb/siris-alto-nas/KB213994246.html
Datto runs on a backup device in the office and backs up PCs in the office. "on the protected machine" is each PC in the office.
-
No, I get what it is saying. We do not have the appliance though and each system has an agent installed on it. The agent talks back to the Datto cloud for backup.
I hope that I am making sense.
-
@wwdot_computers that screams the local firewall on the device your running that agent, not from the internet.. Since that makes zero sense at all that you would have to make
Here is a drawing on their site..

See the local network cloud.. This siris box talking to your protected box... So unless this box is on some other vlan in your local network than the protected machine.. There is no firewall rules needed in pfsense.. But the protected machines local host firewall would have to all that traffic.
-
@wwdot_computers said in Allowing random IP/PORT into LAN:
We do not have the appliance though and each system has an agent installed on it. The agent talks back to the Datto cloud for backup.
You linked the Datto BCDR backup which AFAIK is only via an on site device, either Alto or Sirus.
Do you have Endpoint Backup?
https://continuity.datto.com/help/Content/kb/EB/EB-GettingStarted.htm
(or others going down the left menu on that page) -
That is an inaccurate representation of our setup as we do not have a Siris box or any other for that mater. Each machine needs to connect to the internet directly for the backup. All of the machines are not able to connect, so I do not think it is a local machine firewall issue.
-
That is correct. We have the Datto Endpoint Backup
Endpoint Backup is our fully cloud-based backup and recovery solution for Windows Servers or PCs. You can leverage its features to restore single files or the entire backup image to a new device without any extra equipment required. Select a topic from the left navigation pane to continue.I am not sure why the tech support linked me that other link. Sorry, was just not looking. However, that being the case, still have the issue :(
-
@wwdot_computers said in Allowing random IP/PORT into LAN:
We have the Datto Endpoint Backup
ok so here
https://continuity.datto.com/help/Content/kb/DEBPC/360001005506.html
Getting Started with Datto Endpoint Backup for PCsWhere does it say anything about inbound?
-
@johnpoz said in Allowing random IP/PORT into LAN:
@wwdot_computers said in Allowing random IP/PORT into LAN:
We have the Datto Endpoint Backup
ok so here
https://continuity.datto.com/help/Content/kb/DEBPC/360001005506.html
Getting Started with Datto Endpoint Backup for PCsWhere does it say anything about inbound?
/
Looking at that KB, which I should have caught the first time around, there is not an inbound. I have opened the appropriate ports of outbound, but in the logs, it seems to block 587/443 and such.Ideas?
-
@wwdot_computers yeah open the ports they list outbound - no where in that list does it say anything about the port you were listing.
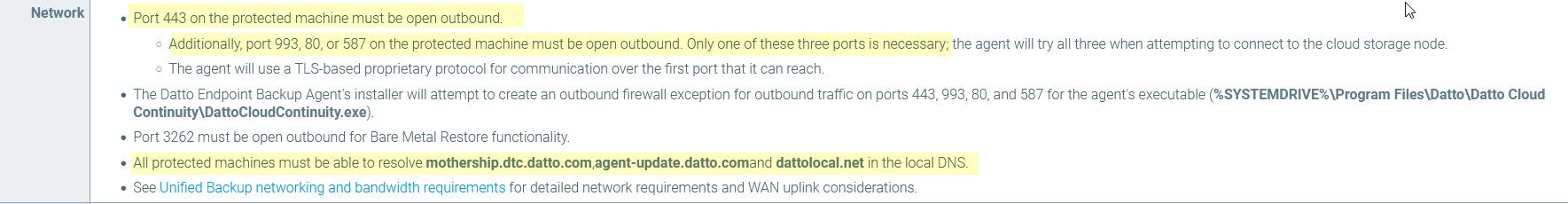
There is also that 3262 port, but that seems to only be needed for bare metal restore.
edit: most of these rules make zero sense if you have endpoint only

Those ports are not listed in their doc, what do you have in the alias?
edit2: As a troubleshooting tool, create a rule on the top that allows one of your machines your trying to backup any any.. Log its traffic - what ports does it talk on for talking to backup?
Maybe your issue is dns related? And it can't resolve what that list says it needs to be able to resolve.. But looks like it need only 443 outbound, and then one of those 3 ports.
-
Here are the ports in the alias that I have from the rules I posted prior:
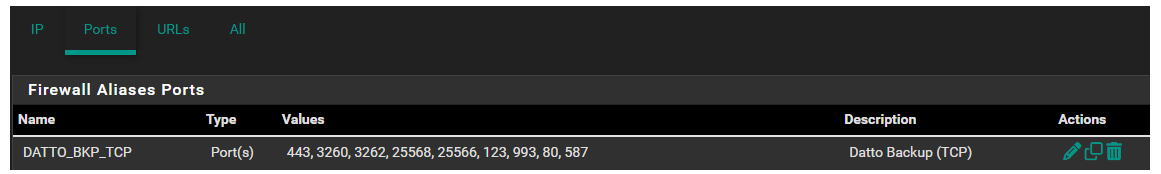
-
Well that 3260 and 25xxx ports are not needed per their doc.. And 123 is ntp and wouldn't be tcp, that would be udp.. And while sure the box should sync time it wouldn't do it over tcp.. And it can get time just from pfsense ntp server.. There doc doesn't list that as a requirement that I saw..
Maybe your issue dns related? Validate you can resolve those listed fqdn at the host your trying to backup.
-
Interesting. Can not resolve "dattolocal.net" Ideas?
-
@wwdot_computers said in Allowing random IP/PORT into LAN:
dattolocal.net
Something is really odd there... I can not resolve it either get servfail - and they clearly failing dnssec
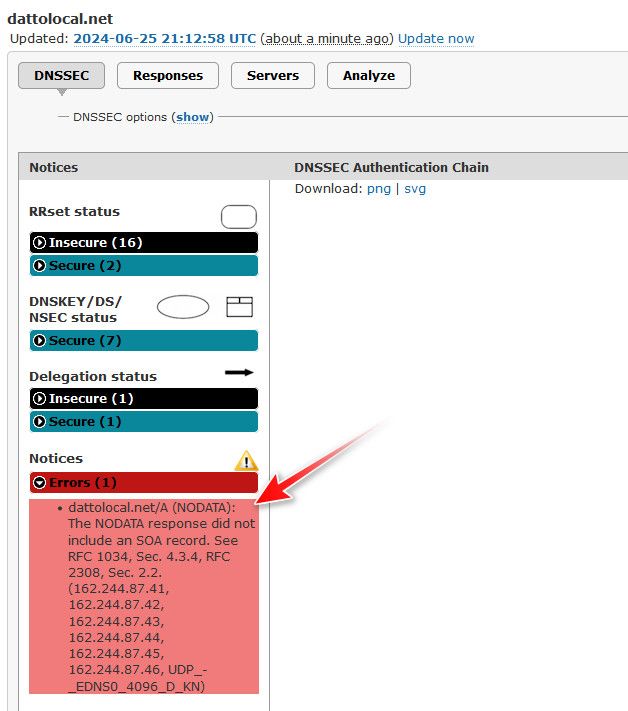
If I ask google, I get this EDE info back about the servfail
; <<>> DiG 9.16.50 <<>> dattolocal.net @8.8.8.8 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 36032 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 512 ; EDE: 0 (Other): ([162.244.87.41] Unexpected dlt-rly-tracker-4.datto.com/a in received ANSWER at dattolocal.net for dattolocal.net/a) ; EDE: 0 (Other): ([162.244.87.43] Unexpected dlt-rly-tracker-6.datto.com/a in received ANSWER at dattolocal.net for dattolocal.net/a) ; EDE: 0 (Other): ([162.244.87.44] Unexpected dlt-rly-tracker-2.datto.com/a in received ANSWER at dattolocal.net for dattolocal.net/a) ; EDE: 0 (Other): ([162.244.87.45] Unexpected dlt-rly-tracker-5.datto.com/a in received ANSWER at dattolocal.net for dattolocal.net/a) ; EDE: 0 (Other): ([162.244.87.42] Unexpected dlt-rly-tracker-3.datto.com/a in received ANSWER at dattolocal.net for dattolocal.net/a) ; EDE: 0 (Other): ([162.244.87.46] Unexpected dlt-rly-tracker-5.datto.com/a in received ANSWER at dattolocal.net for dattolocal.net/a) ; EDE: 22 (No Reachable Authority): (At delegation dattolocal.net for dattolocal.net/a) ;; QUESTION SECTION: ;dattolocal.net. IN A ;; Query time: 209 msec ;; SERVER: 8.8.8.8#53(8.8.8.8) ;; WHEN: Tue Jun 25 16:08:19 Central Daylight Time 2024 ;; MSG SIZE rcvd: 818If I do a +trace where no dnssec is actually performed I can get an answer
; <<>> DiG 9.18.16 <<>> dattolocal.net +trace ;; global options: +cmd . 19823 IN NS h.root-servers.net. . 19823 IN NS i.root-servers.net. . 19823 IN NS j.root-servers.net. . 19823 IN NS k.root-servers.net. . 19823 IN NS l.root-servers.net. . 19823 IN NS m.root-servers.net. . 19823 IN NS a.root-servers.net. . 19823 IN NS b.root-servers.net. . 19823 IN NS c.root-servers.net. . 19823 IN NS d.root-servers.net. . 19823 IN NS e.root-servers.net. . 19823 IN NS f.root-servers.net. . 19823 IN NS g.root-servers.net. . 19823 IN RRSIG NS 8 0 518400 20240707170000 20240624160000 5613 . TbfcxHfBUFXoWqSj9MqO9XQ/zZje2qfrSBhdeaVf3xpiuZqUxxGANBN8 KcQR5tNFbDRP/vPgFPAjWwR4nzAWe/Cv9KTz6lAjn2+O46GhsTIO7Zvu 4Y/r6C3KJsSXF1D7DdumS+rAI+eip3xStAghcSbqAQJfkwfUb2jy7m4k lcs1d6qT2CIcEcSU/i/z44gkJH5rtIH9zQfjF1i+1VQf66lx6PPAw4Aq t7Dsu8Hp0jrHeAvKUGAIemAZhfayXcU1EGGVa3uwWKjlcLgiaJPp6B0d lf5WBI1TsMsI7Zbr+r4lzsk5IsIwGgsblm3orML1HwMg2zmBlEjnVsRb UbMsug== ;; Received 525 bytes from 127.0.0.1#53(127.0.0.1) in 0 ms net. 172800 IN NS a.gtld-servers.net. net. 172800 IN NS b.gtld-servers.net. net. 172800 IN NS c.gtld-servers.net. net. 172800 IN NS d.gtld-servers.net. net. 172800 IN NS e.gtld-servers.net. net. 172800 IN NS f.gtld-servers.net. net. 172800 IN NS g.gtld-servers.net. net. 172800 IN NS h.gtld-servers.net. net. 172800 IN NS i.gtld-servers.net. net. 172800 IN NS j.gtld-servers.net. net. 172800 IN NS k.gtld-servers.net. net. 172800 IN NS l.gtld-servers.net. net. 172800 IN NS m.gtld-servers.net. net. 86400 IN DS 37331 13 2 2F0BEC2D6F79DFBD1D08FD21A3AF92D0E39A4B9EF1E3F4111FFF2824 90DA453B net. 86400 IN RRSIG DS 8 1 86400 20240708200000 20240625190000 5613 . GUngUjWt7Wug0Z5OCnh1v5eVmd94d23+Lh8HdgFVVb9U9N6/htHgAeM0 emATeJbRTuKXfvEZPBJVs7nZi7/GmmWtAjmPXDjZMqUI5Uzu+TDftifG sFnBKsbKak4jaFwJfZGJk+SZiXd8Gpo9EHHefUk4BX5hDiM2HePJFVW6 FiQXacAOT2LjpZvz5se//Lq9qlFsJWp2guUWhl04ulyMYMUD7doH6Z08 5MrCWnqo/hxS6CU10zvrwe3hSfHniIU1+s75c+Dc6ZyH+z9bwcRGbDGq xXO0FmCftLbX4UfDYBGlIh9qJhcV4nPEcdO4ikEx2BBEJ7fJ4wy+AI8X qu7gbQ== ;; Received 1171 bytes from 170.247.170.2#53(b.root-servers.net) in 30 ms dattolocal.net. 172800 IN NS dlt-rly-tracker-1.datto.com. dattolocal.net. 172800 IN NS dlt-rly-tracker-2.datto.com. dattolocal.net. 172800 IN NS dlt-rly-tracker-3.datto.com. dattolocal.net. 172800 IN NS dlt-rly-tracker-4.datto.com. dattolocal.net. 172800 IN NS dlt-rly-tracker-5.datto.com. dattolocal.net. 172800 IN NS dlt-rly-tracker-6.datto.com. A1RT98BS5QGC9NFI51S9HCI47ULJG6JH.net. 86400 IN NSEC3 1 1 0 - A1RTLNPGULOGN7B9A62SHJE1U3TTP8DR NS SOA RRSIG DNSKEY NSEC3PARAM A1RT98BS5QGC9NFI51S9HCI47ULJG6JH.net. 86400 IN RRSIG NSEC3 13 2 86400 20240629024642 20240622013642 51809 net. hF4q89ZVBO55eWZL8q6wAOUvnOxAkEC0F6kFXLduI8SUKrUBJeteDhVc 7ErTVKxfUq7nrA3QJEy2gw2FEOSRbA== Q3HBHI4I2FNO0GDMKEMKT7TPSL5TGAKO.net. 86400 IN NSEC3 1 1 0 - Q3HHVPH6AM4SSQ6LMDCUHI413ISDSBIE NS DS RRSIG Q3HBHI4I2FNO0GDMKEMKT7TPSL5TGAKO.net. 86400 IN RRSIG NSEC3 13 2 86400 20240629025141 20240622014141 51809 net. zkHGAQm9SQf01Os21pcWOpH+0U7bsKF2y+kYUKv2OW3nkPW26fwjYmGS a0B2GshLKGwfjhW/TcEhtjvbEqWx5Q== ;; Received 601 bytes from 192.31.80.30#53(d.gtld-servers.net) in 38 ms dlt-rly-tracker-3.datto.com. 300 IN A 162.244.87.43 dlt-rly-tracker-4.datto.com. 300 IN A 162.244.87.44 dlt-rly-tracker-5.datto.com. 300 IN A 162.244.87.45 dlt-rly-tracker-2.datto.com. 300 IN A 162.244.87.42 dlt-rly-tracker-6.datto.com. 300 IN A 162.244.87.46 dlt-rly-tracker-1.datto.com. 300 IN A 162.244.87.41 ;; Received 256 bytes from 162.244.87.45#53(dlt-rly-tracker-5.datto.com) in 31 ms [23.09.1-RELEASE][admin@sg4860.home.arpa]/root:I would contact there support, because clearly they got something broken in their dns, or there is something specific you need to do to resolve that? But my point of view its broken.. It does say something about "in local dns" so maybe your suppose to create a specific record to resolve that locally?
I would contact their support - its not something broken in pfsense that is for sure.. Here is a query to 1.1.1.1 and it also comes back empty..
[23.09.1-RELEASE][admin@sg4860.home.arpa]/root: dig dattolocal.net @1.1.1.1 ; <<>> DiG 9.18.16 <<>> dattolocal.net @1.1.1.1 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 51315 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ;; QUESTION SECTION: ;dattolocal.net. IN A ;; Query time: 34 msec ;; SERVER: 1.1.1.1#53(1.1.1.1) (UDP) ;; WHEN: Tue Jun 25 16:23:45 CDT 2024 ;; MSG SIZE rcvd: 43 [23.09.1-RELEASE][admin@sg4860.home.arpa]/root:So its not just you.. Or pfsense anything.. Doesn't resolve correctly on the public internet..
Maybe their doc isn't quite right and there is some specific host.dattolocal.net your suppose to resolve?
But you can see in the ede info, looks like they are not returning the SOA when there is no A record for just the domain dattolocal.net, which is a borked config, it should return a soa.. if there is no record..
See if I ask for something where the record does not exist - you should get back the SOA that tells you hey this NS is authoritative for this domain, and he says there isn't a record for what your asking for.
$ dig sljdflsjdflsjfl.google.com ; <<>> DiG 9.16.50 <<>> sljdflsjdflsjfl.google.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 15435 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 1232 ;; QUESTION SECTION: ;sljdflsjdflsjfl.google.com. IN A ;; AUTHORITY SECTION: google.com. 3600 IN SOA ns1.google.com. dns-admin.google.com. 646028540 900 900 1800 60 ;; Query time: 40 msec ;; SERVER: 192.168.3.10#53(192.168.3.10) ;; WHEN: Tue Jun 25 16:30:31 Central Daylight Time 2024 ;; MSG SIZE rcvd: 105