3CX & NAT (Again)
-
@patch
Thanks for the screenshots, what's PBX_IP_in_SIP in your rules ?I edited my rules to make them looks like yours except for the PBX IP alias :
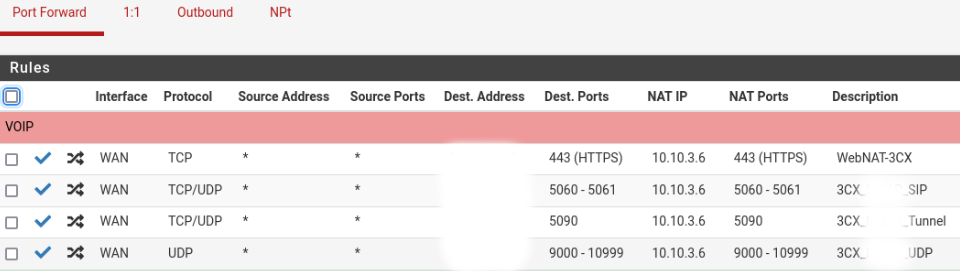
Dest. Address is our VIP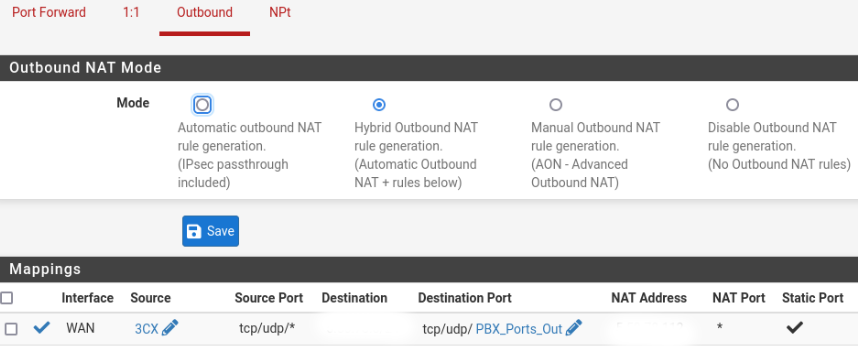
NAT Address is our VIPThere is some progress on 3cx firewall checker. Now the SIP ALG passes :
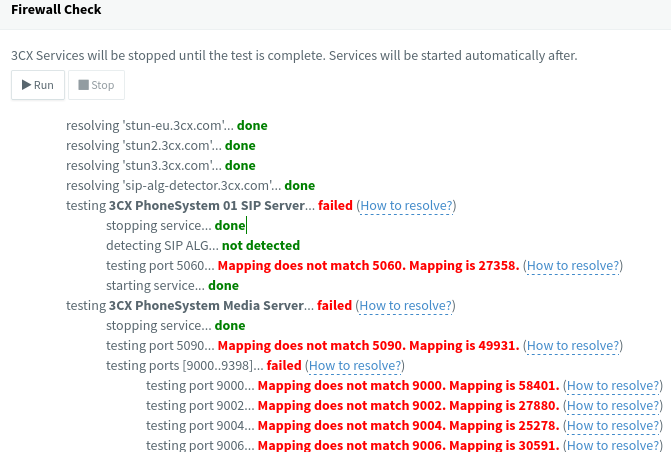
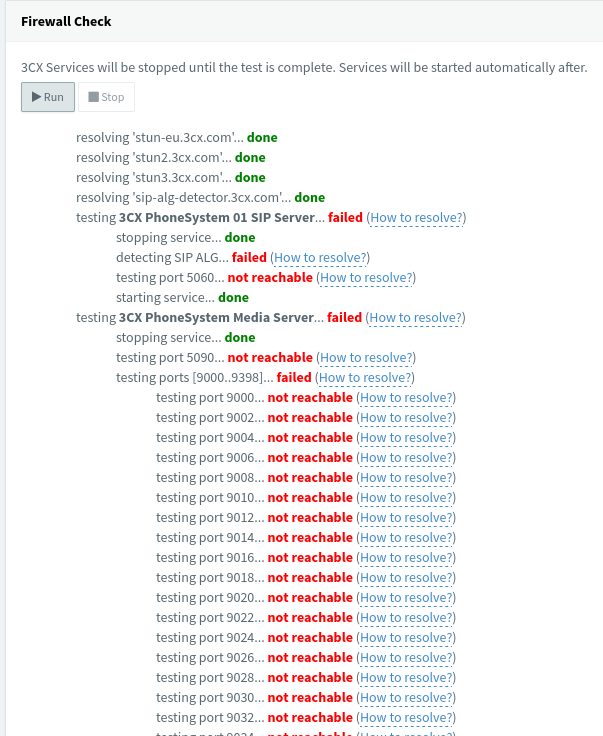
But still the same problem with the ports. -
@alek said in 3CX & NAT (Again):
what's PBX_IP_in_SIP in your rules ?
The SIP address of the VoIP suppliers I use. Mostly defined by FQDN but some as small ranges of IP addresses (stored in a separate alias). Using it means I white list the IP addresses which can access my 3CX, decreasing it's attack surface.
Note this must also include the 3CX SIP server IP addresses to enable passing the fire wall testing.
3CX console -> Settings -> Network -> External IP Configuration
plus
sip-alg-detector.3cx.com@alek said in 3CX & NAT (Again):
But still the same problem with the ports.
I suspect double NAT / CGNAT
-
@patch
If I put our VIP in source Address for Port Forward and Destination in Outbound I pass the SIP ALG test but I still have a problem with the ports match.
I'm waiting for an answer from our ISP about double NAT / CGNAT... -
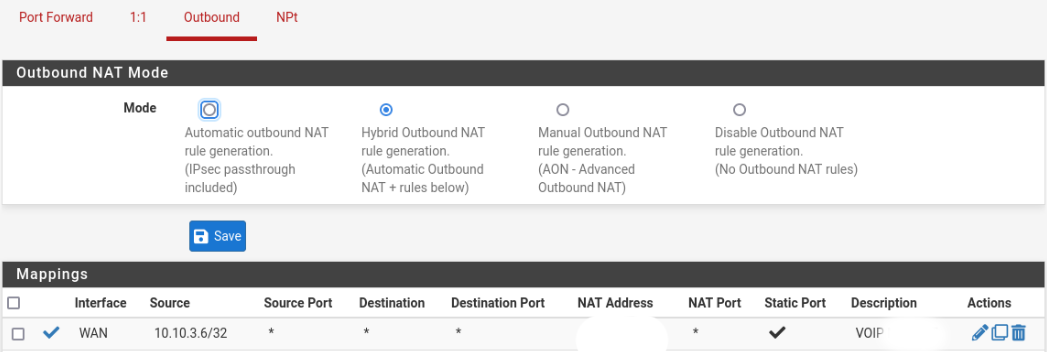
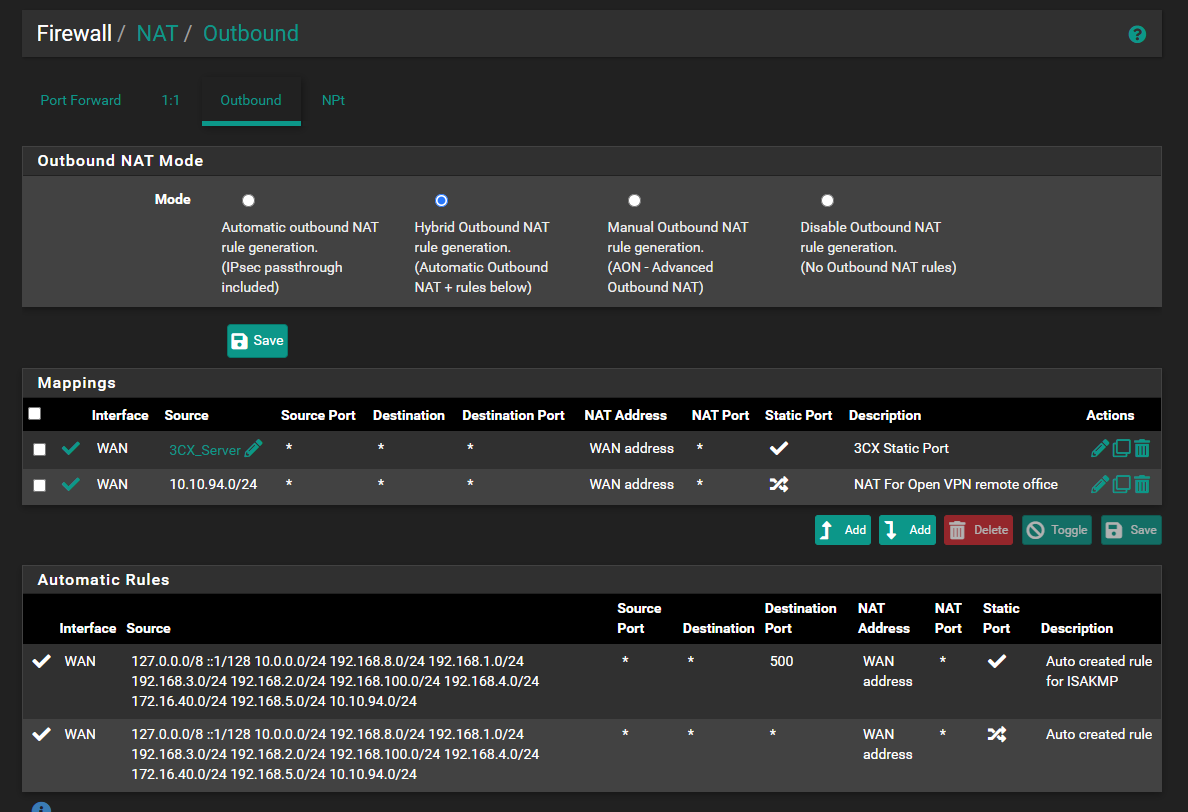
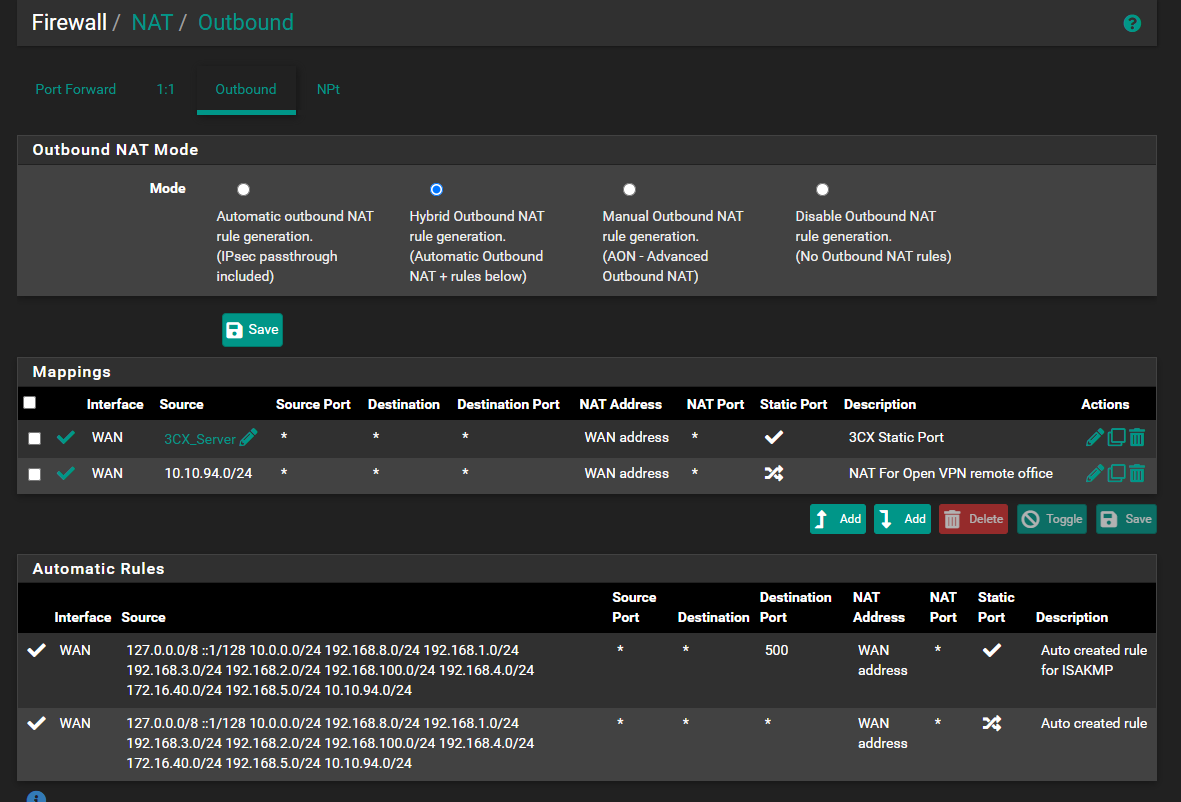
@alek Have you enabled static port mapping?
pfsense -> Firewall -> Nat -> Outbound -> Mapping -> Edit
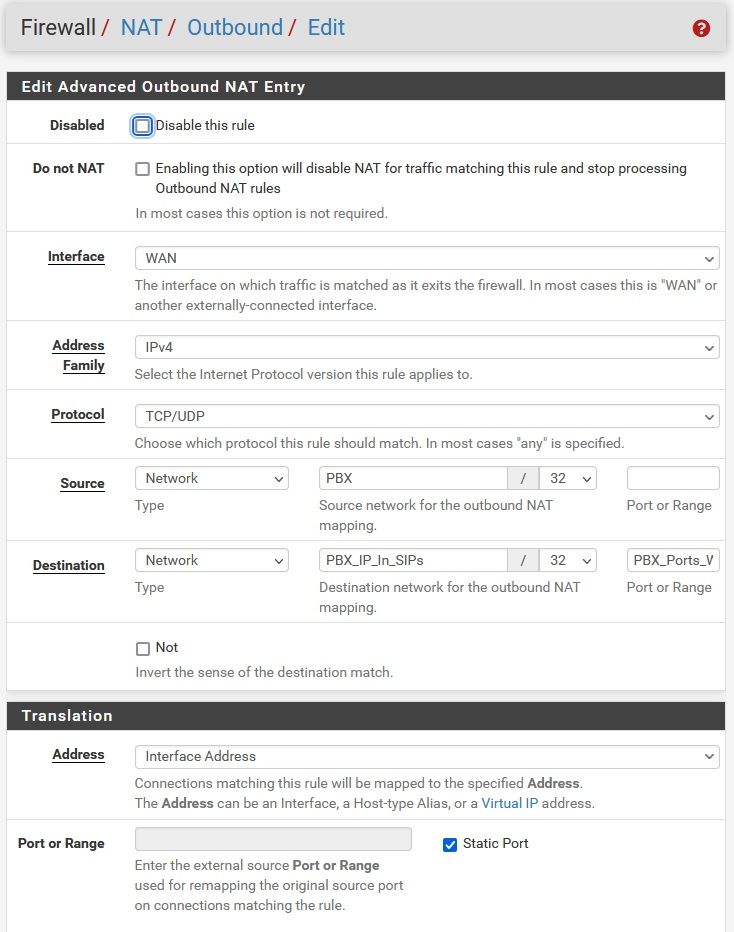
-
@patch Yes it's checked
-
Hello
i have the same problem with pfsense 2.7.2 CE on baremetal (no provider router)
3CX ver20 on premise
IP Server 3CX in the LAN 192.168.1.137Have you resolved?
I also followed this guide
ENG:
https://www.3cx.com/docs/pfsense-firewall/ITA:
https://www.3cx.it/doc/configurazione-firewall-pfsense/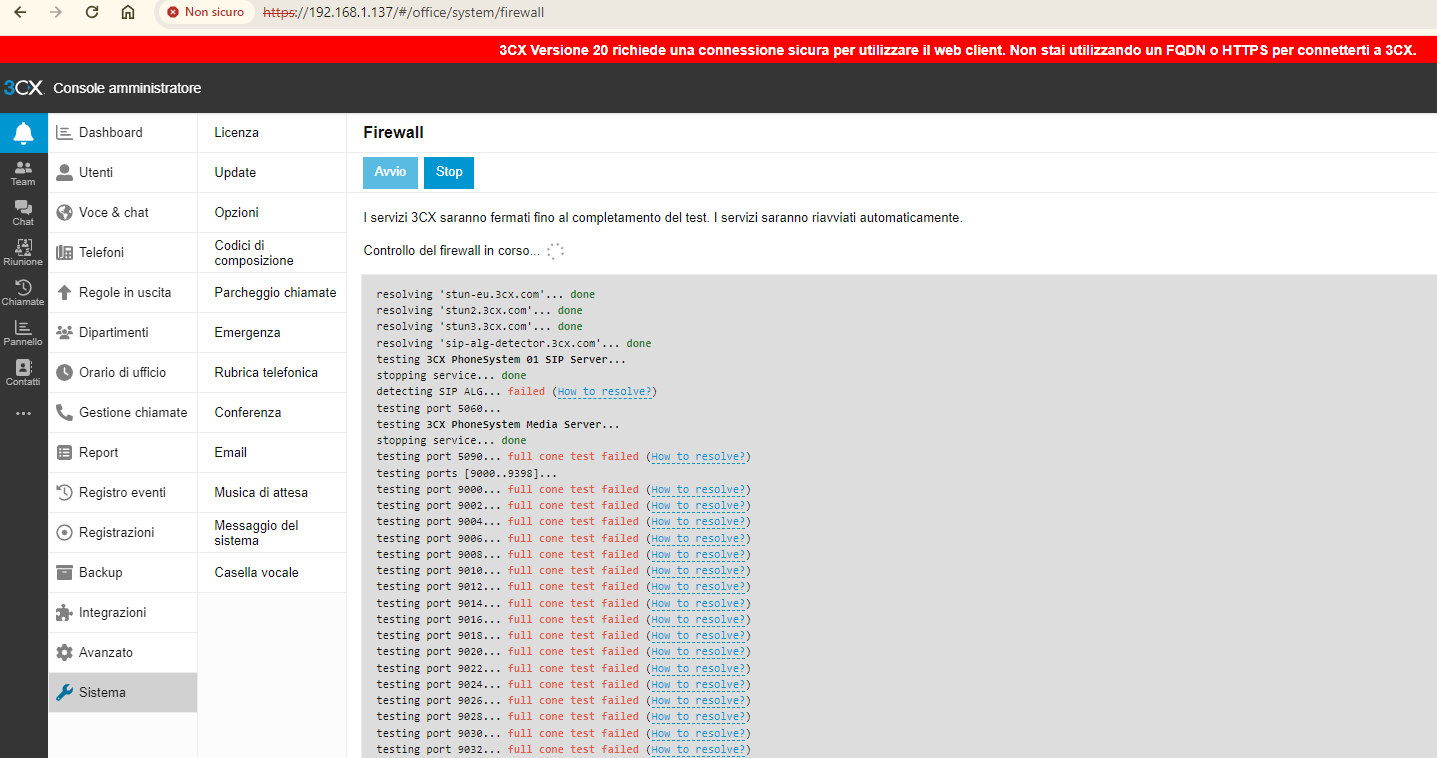
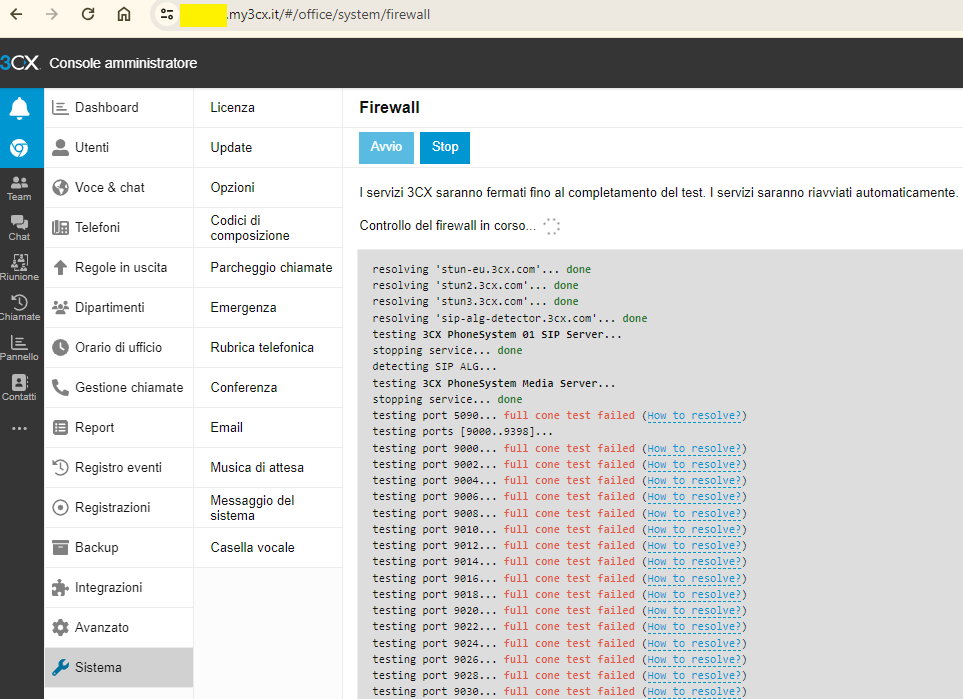
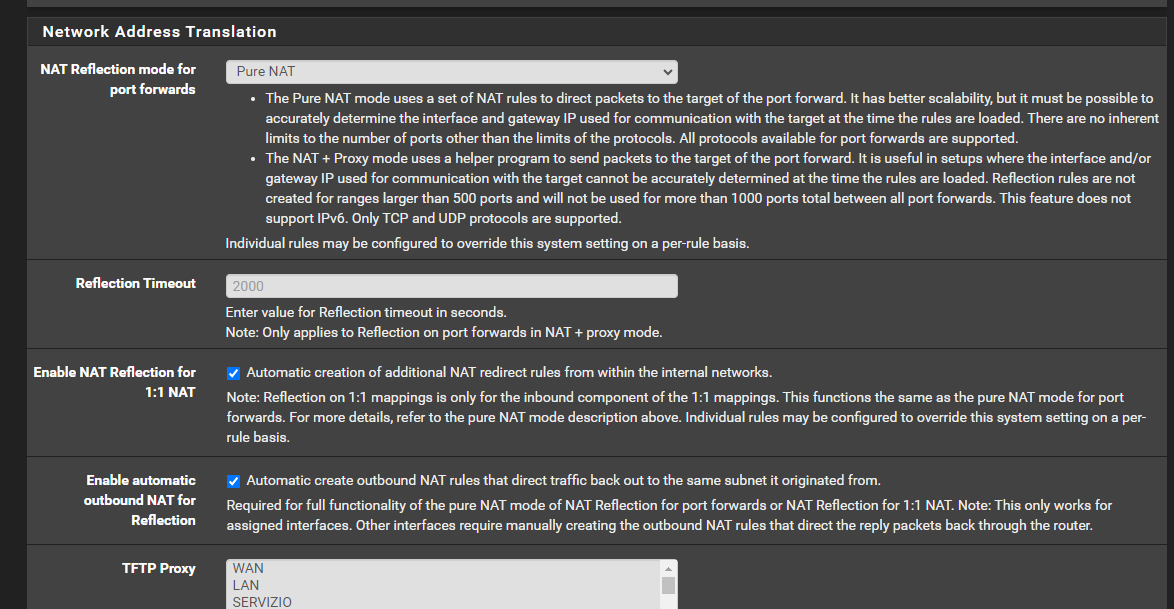
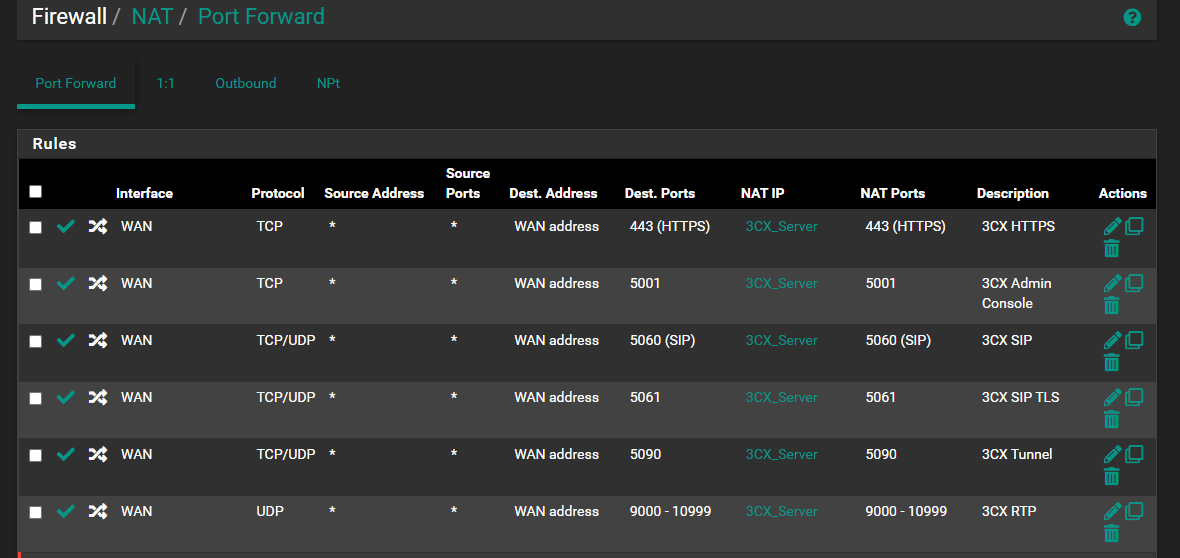
System Advanced Firewall & NAT :
-
@Unoptanio
Hi o/Yes resolved. Started everything from scratch and it worked.
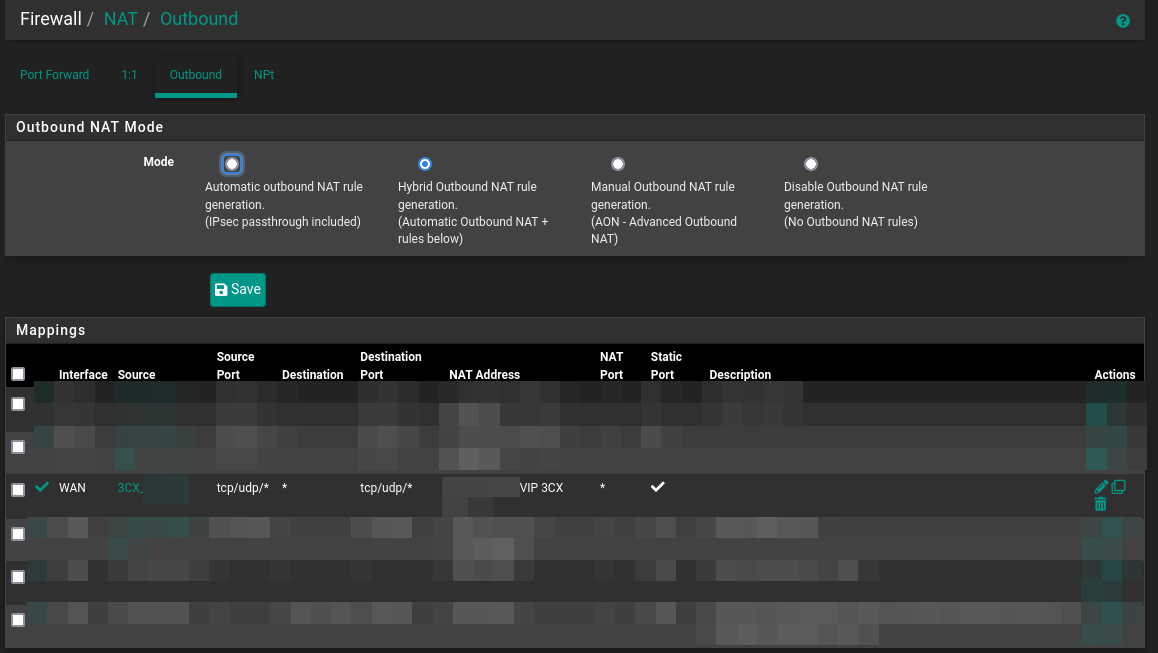
My outbound rule is :
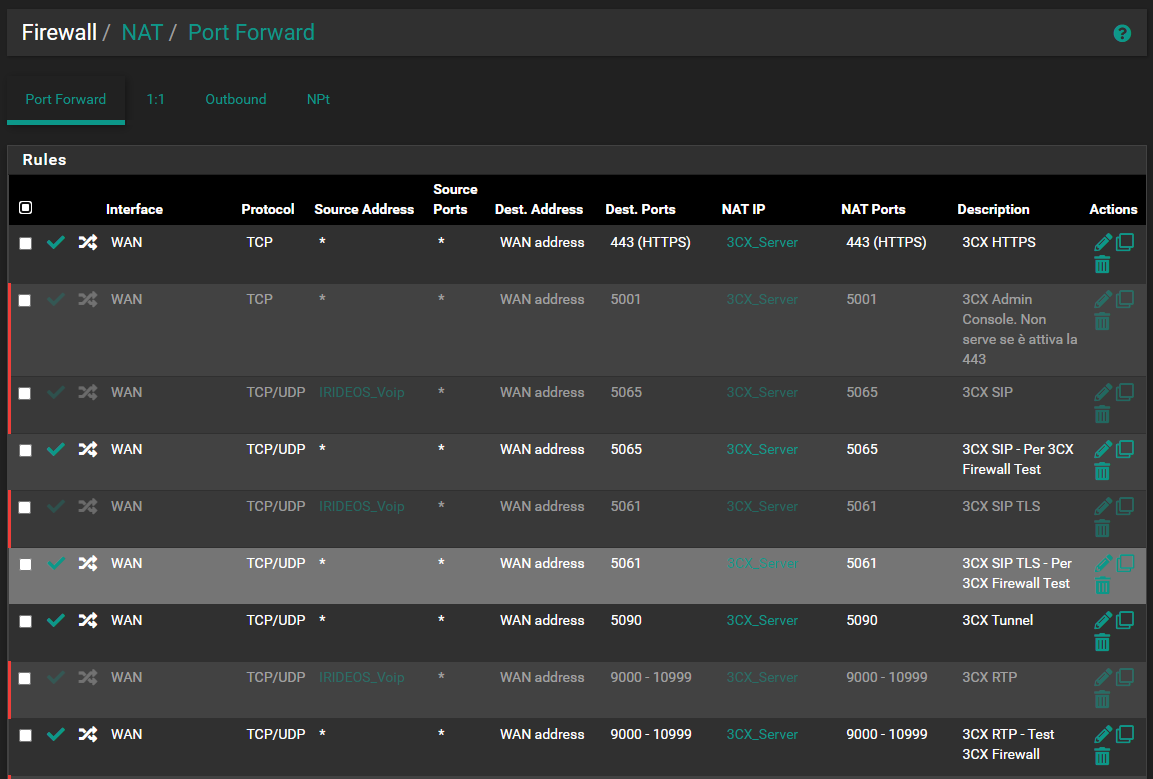
My inbound rules :
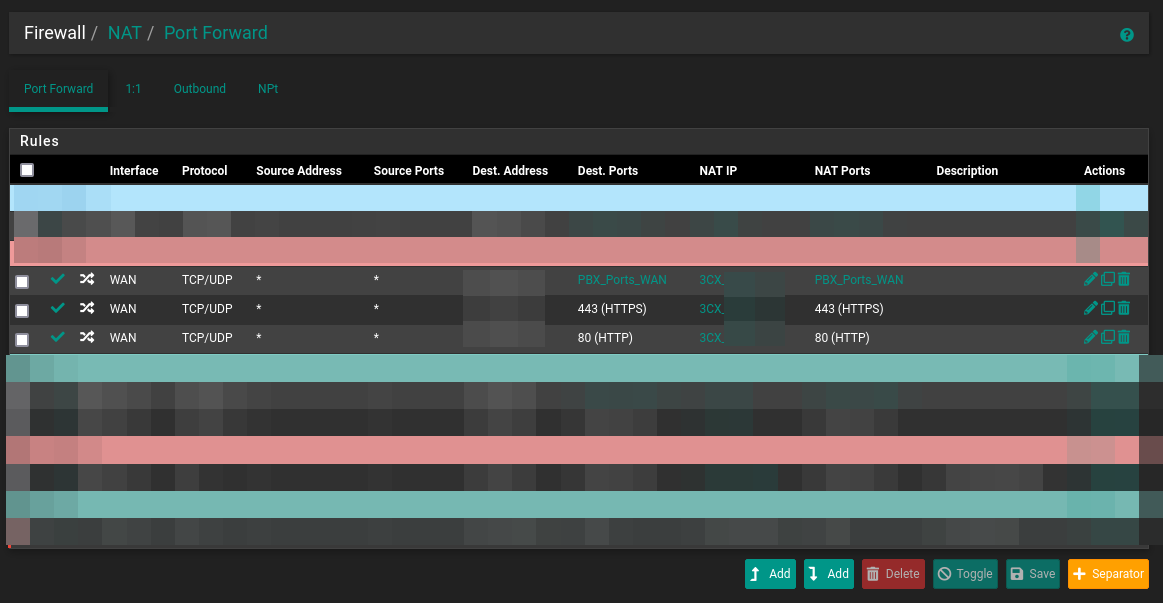
PBX_Ports_WAN contains :
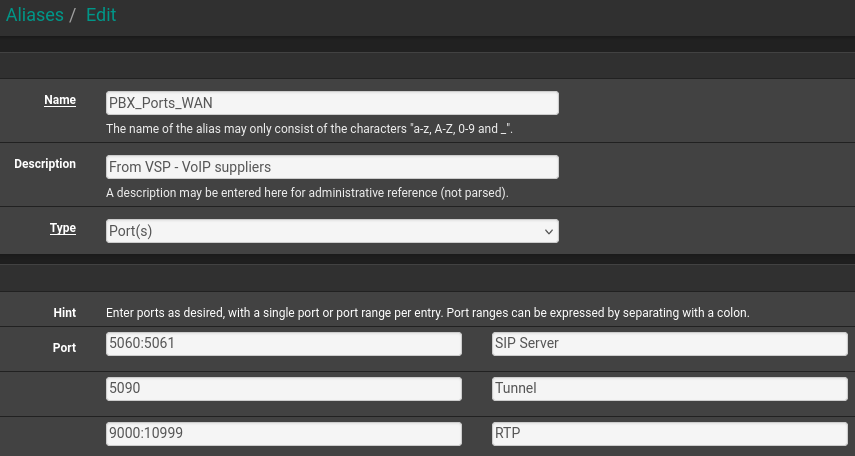
NAT is in Pure Nat too.
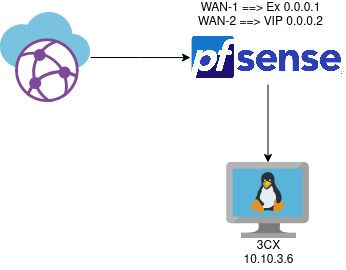
Verify the your 3CX server is using the correct WAN if you have multiple WAN/VIP.
-
-
@Unoptanio I don't think pfSense even has SIP ALG, check your ISP router for SIP ALG and disable it there.
-
The problem in your case is for sure that you have to change some parameters on 3cx.
From the web UI of 3cx go to Advanced->Parameters. Search with the local ip address value. It will find many entries. Change them to the public ip address. There should be only one left with the local ip.
Once you do this it will work and the firewall test will pass but there is still another problem with the port forwarding i think. Forx example i cant chat. Can't change the status on yhr 3cx client.. -
In the meantime I solved it and now everything works correctly.
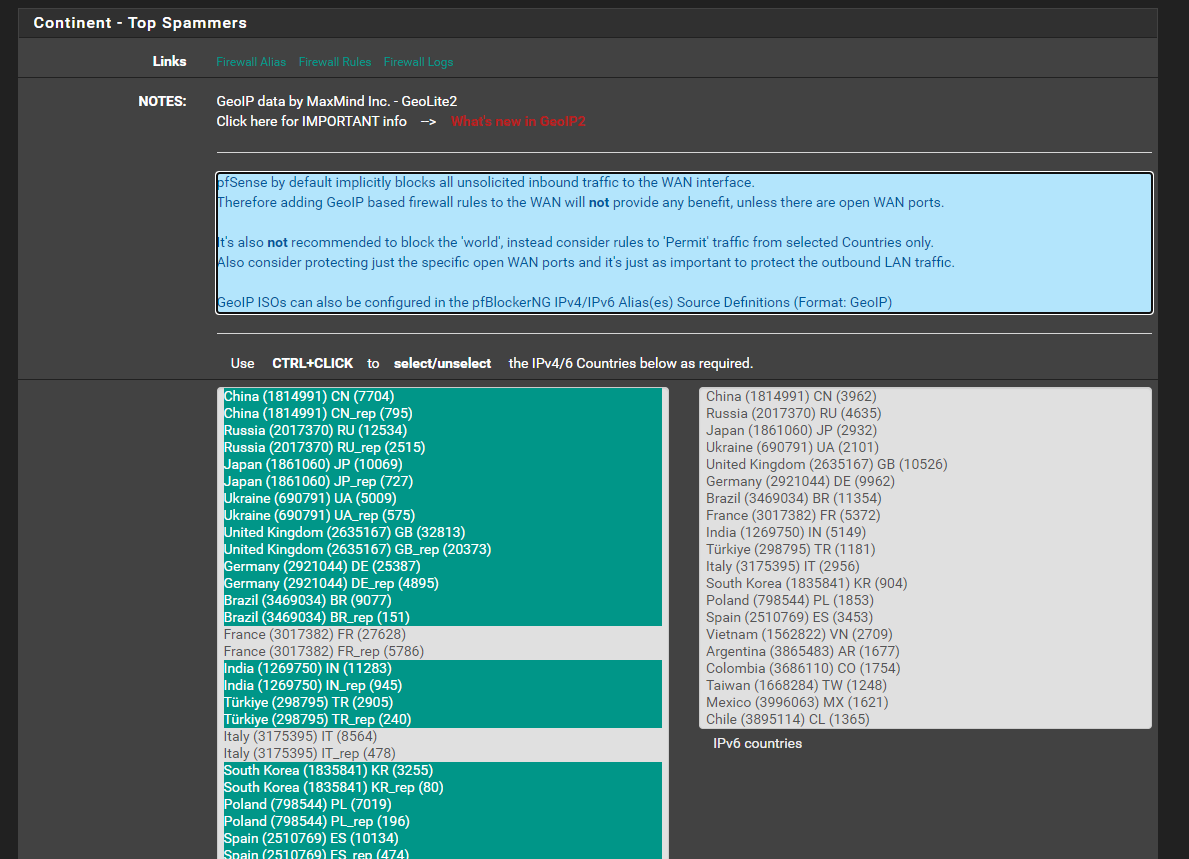
I disabled pfsense's pfBlockerNG module and now the firewall test has improved significantly:I discovered that by disabling the Top Spammers GEOIP category the 3CX test of full cone nat ports passes
Digging deeper and leaving the GeoIP Top Spammers category enabled, the entry causing the problem was "France" which I deselected from the list. (I connect from Italy)
more information here:
https://www.3cx.it/community/threads/configurazione-del-firewall-pfsense-con-3cx.116324/#post-429317
Another issue causing the firewall test to fail within 3cx:
having a pool of static public addresses I had reserved a specific one for the 3cx server. This caused the problem because it must be identical to the public address you use to go out on the internet. After setting it equal the test passed. -
@Unoptanio said in 3CX & NAT (Again):
GeoIP Top Spammers
FWIW, as I recall "top spammers" is simply a horribly named list of entire-country IPs.
It is however valid to run the 3CX firewall test and then block IPs/countries to limit access. We do so on the 3CX servers we host.
-
-
@Unoptanio I white list the IP address 3CX needs to work. White listing is done by adding an allow rule high up.
Required IP address include some 3CX company address as well as those used by your voip service providers. -
@Unoptanio my firewall test is okay and all green. I can call and recieve also calls. Strangly, it is not working perfectly on the android app. I see the following
The only difference from the standard install is that i changed the https port to 5001 and of course added a NAT entry for that.
No idea why it is not working.
-
@albgen is your app using wireless or cell data/out of the office?
-
@SteveITS whatever network connection i was using, it was not working and i found he culprit.
The reason is that you cannot just change the port of the https where the nginx web server of 3cx is listening. That will hange the Web UI interface.
You need also to go to the parameters of the 3cx(from the Web UI, Advanced->Parameters) and change a bunch of parameters. What i did was to find all the parameters containing the url https://.... and add the new port at the end.Now seems everything works perfectly.
-
@albgen Ah. To change ports the supported method is to reinstall 3CX.
-
@SteveITS yes, that is correct and it is written everywhere.
The problem is that, 99% of the cases, you cannot reinstall and that was my case :)