IPSec behind NAT
-
Hello, everyone,
I would like my server that is behind NAT to be able to surf using the public ip of a PFSense01 firewall, all by creating a Routed VTI or Transport Mode IPSec tunnel. I have already tried creating this with a Routed VTI mode (PFSense01 in responder only) but to no result, as PFSense was receiving packet-in but not giving packet-out. Could you please help me understand how to do this confiuguration?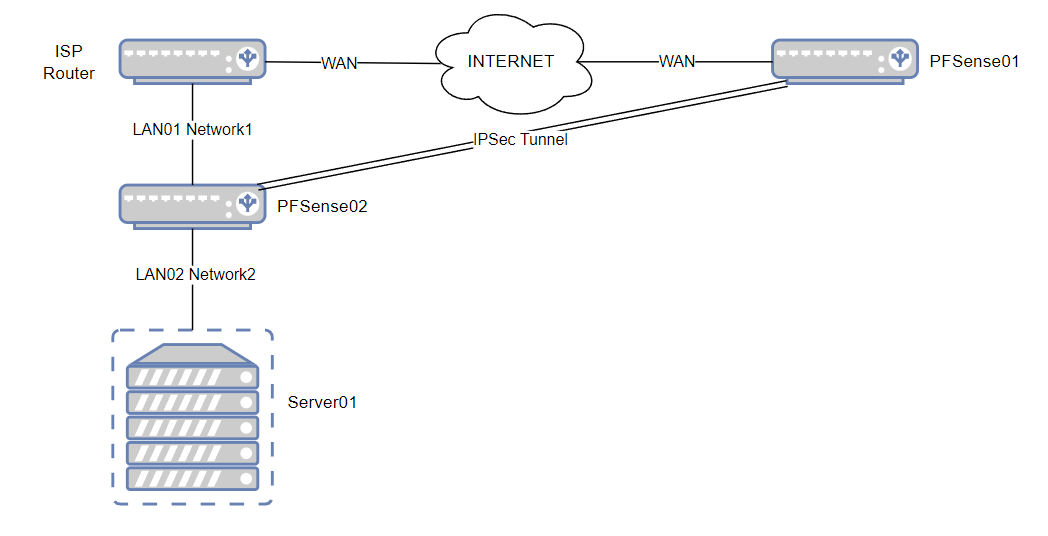
-
@xElectro_FX
Did you configure an outbound NAT rule for packets from the remote site? -
@viragomann On PFSense01 Firewall I haven't configured any NAT
-
@xElectro_FX
You need natting your internal IPs to the WAN IP, when talking to the outside world. pfSense adds rules for local subnets automatically. But if you route traffic from the remote site out to the WAN you have to add rules for that manually.Firewall > NAT > Outbound
Switch to hybrid mode and save this. Then add a rule:
Interface: WAN
source: the severs IP
Dest: any
Translation: WAN addressApart from this, you need to configure your VPN properly. Should work with either policy-based or routed IPSec.
-
@viragomann I actually currently have this problem
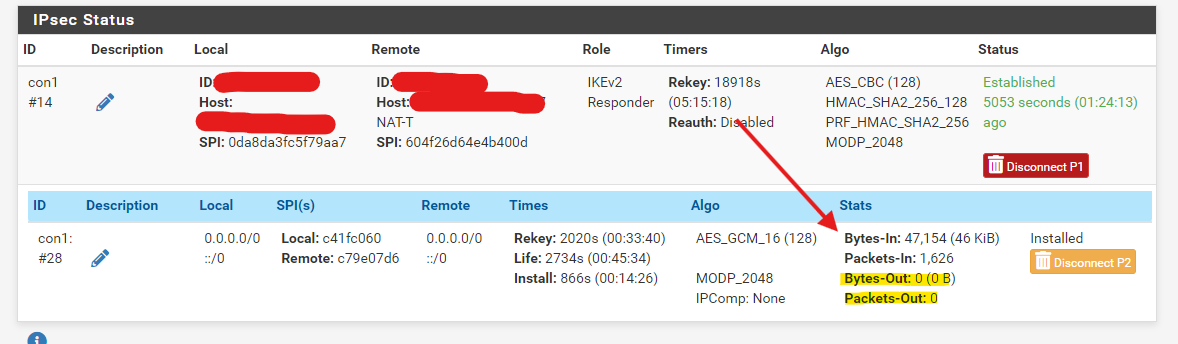
In PFSense01 Firewall -
@xElectro_FX
Having the locale and remote set to 0.0.0.0/0 in the p2 might not be a good idea at all. -
@viragomann I don't know why 0.0.0.0 is shown there, but that's my config
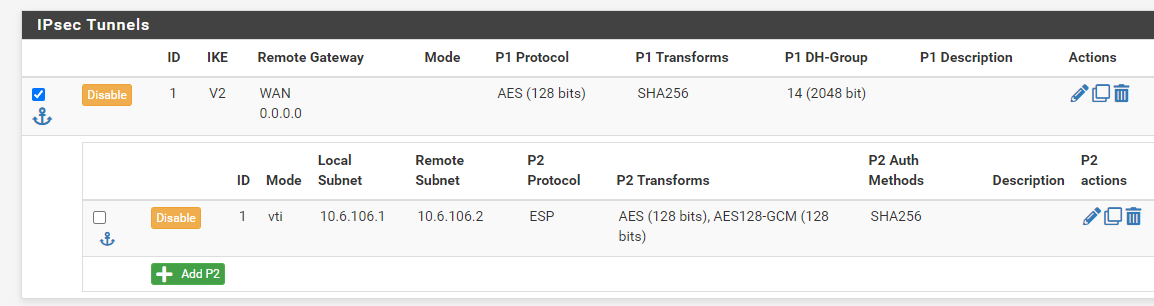
In this case Remote Gateway is 0.0.0.0 'cause it is in Responder-only mode
-
@xElectro_FX
So ab it's a vti. Ensure that the remote site is configured accordingly as well. -
@viragomann Also PFSense02 is in VTI Mode
-
@xElectro_FX
And did you policy route the upstream traffic of the server on pf2? -
@viragomann Before routing the traffic of Server, I would like PFSense01 and PFSense02 to ping on the VTI interfaces, because from the screenshot that I showed before on PFSense01 there are 0 outbound packets, and I don't now why