How to DNS resolve with Wireguard Site to Site VPN using two pfSense installations?
-
So I was previously using a single laptop with wireguard installed to connect to create a wireguard tunnel to a remote pfSense server. With this setup on the laptop it was fairly easy to control DNS resolution within the laptop wireguard instance as I would add the pfSense unbound DNS server to the configuration:
DNS = 10.0.1.1, domain.com10.0.1.1 represents the unbound local IP address running on pfSense.
Fast forward to a just a tad more involved setup years later where at the second site I installed pfSense which is also running unbound for DNS resolution. So now I have a setup:
---Site #1 - pfsense with unbound server with local DNS host overrides
---Site #2 - pfsense with unbound server with local DNS host overridesI've managed to configure a site-to-site VPN using Wireguard between the two pfsense installations. My problem however is with DNS resolution as I'd ideally like clients on either site to be to DNS resolve by first consulting the local pfsense installation, then if entry isn't found consult the remote site pfsense, and then finally if not found use some sort of remote external DNS server (9.9.9.9) for name resolution. For some reason I can't get this setup working.
I've searched posts on this forum and came across one post where @LTS_Tom mentioned that Site #1 DNS server should pull and update it's own DNS records from Site #2 and update the local DNS records accordingly. This sounds great in theory but I can't figure out how to do this with pfSense.
With each pfSense installation I've tried adding the local IP address of the other pfSense to the DNS resolver section within System->General Setup->DNS Server Sections. Within this list however on each site I have external DNS servers additionally listed such as 9.9.9.9 and 1.1.1.1. This setup however doesn't seem to quite work.
When attempting a dns lookup locally hoping to get the local DNS address from the remote site, I can receive the proper IP address is specifically the DNS server:
nslookup test.domain.com 10.0.1.1however if not specifying the specific DNS server:
nslookup test.domain.comthe local unbound server will resolve using an external DNS server such as 1.1.1.1 or 9.9.9.9.
Is there an easy way to accomplish what I want to do? In theory this seems like it should be easy if I could specify an order of preference of DNS lookups such as local DNS server, wireguard remote DNS, remoted DNS servers -- or -- have site 1 pull DNS records from site 2 and update it's own DNS records accordingly -- however I can't seem to find a way to do this within pfSense.
-
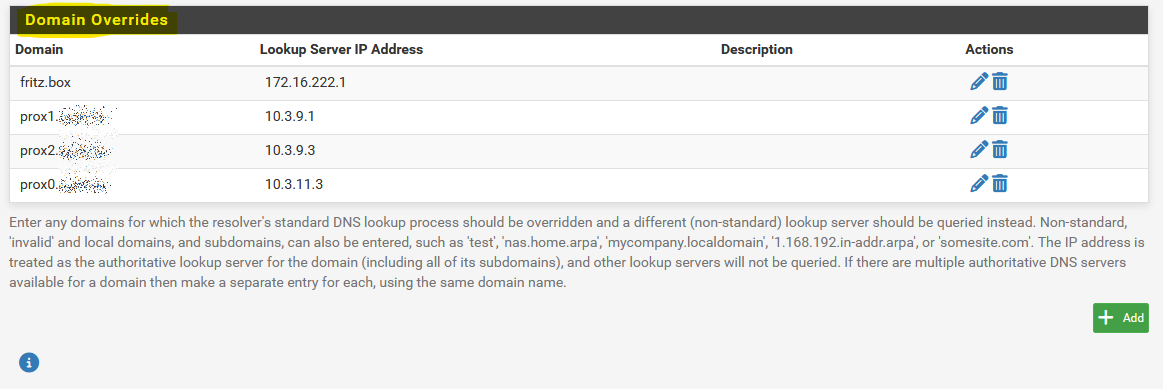
@kevdog You need to use the Domain Overrides.
There is not one local IP-address for unbound, it uses every LAN type Interface. Use the nearest one.
And finally, you need different (sub-)domains for every site. You can't just use the same domain for both.
At least that is working for me. -
@Bob-Dig I have one common base domain between the sites with different subdomains on the two sites. I have a lot of Domain Overrides on each pfsense installation. I'm not sure how to have pfSenseA query pfSense's B host overrides prior to querying external DNS servers. It also has to work in reverse -- pfSenseB should query pfSense's A host overrides as well. I'd like to avoid manually copying the host overrides from one host to the other as this would mean everytime I add a host override, I would need to add it twice (once to pfSense A and the other to pfSense B).
Not sure what you mean by stating use the nearest LAN interface.
-
-
@Bob-Dig
Ok thanks for picture, but I take it this domain override section is present on every host -- prox0, prox1 and prox2? With this configuration, I'm still not sure how this helps solve the issue. If the remainder of the Domain Overrides section is different on prox0 as compared to prox1, how do LAN clients on the prox0 LAN query DNS domain overrides that are present on prox1?
-
@kevdog said in How to DNS resolve with Wireguard Site to Site VPN using two pfSense installations?:
Ok thanks for picture, but I take it this domain override section is present on every host -- prox0, prox1 and prox2?
Right. And the one where this picture is taken from.
With this configuration, I'm still not sure how this helps solve the issue. If the remainder of the Domain Overrides section is different on prox0 as compared to prox1, how do LAN clients on the prox0 LAN query DNS domain overrides that are present on prox1?
Are you really talking about Domain Overrides? For Host Overrides they only will be looked up if the domain part is matching with the Domain Override.
-
@Bob-Dig Ahh I think I became pigeon holed in my understanding -- Domain override -- not Host Override.
Ok I think I'm back on track a little. Just a few followup questions. I different (sub)dowmain, I take it that each site has a different domain specified here:
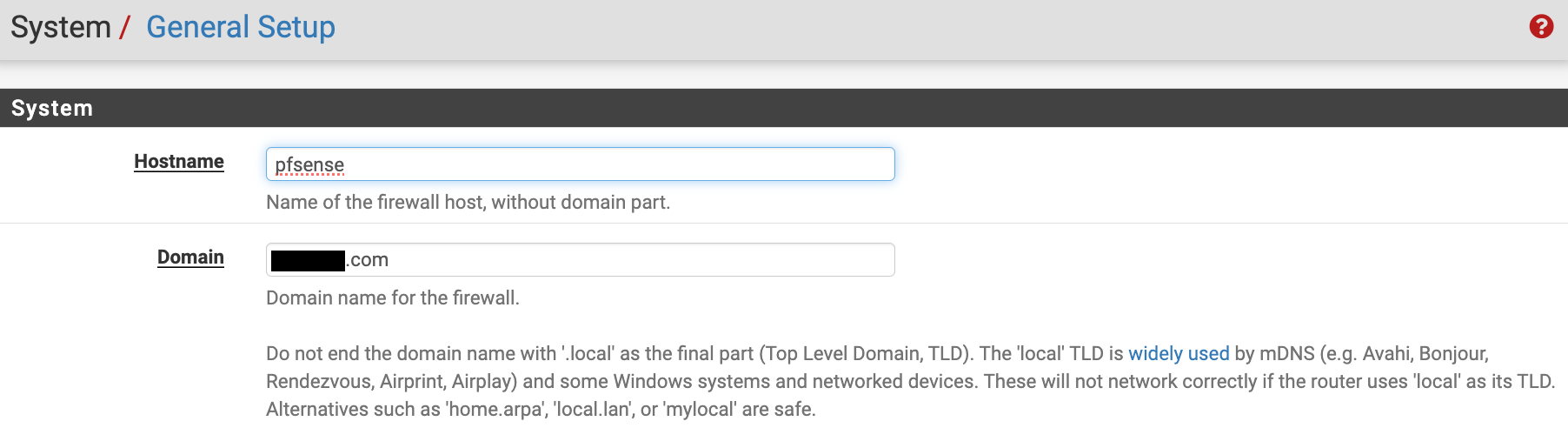 .
.When establishing the wireguard site to site connections - do you specify IP address or use domain names as the endpoint? I only ask this since my endpoints are setup using domain names rather than IP addresses. The domain names require an external DNS lookup via an external server to establish the IP address. I don't have a fixed IP address and although it doesn't change that option theoretically could change, hence using pfSense's dynamic DNS updater to update the DNS record at cloudflare.
You've given me somethings to think about. Thanks.
-
@kevdog A different (sub-)domain, right.
For WireGuard, it would be better if at least one side has a static IP-address. But when both are dynamic, sure, go with DDNS. If it doesn't change regularly, you shouldn't notice any problem.