IPv6 EUI-64??
-
@JKnott does that provide a way to protect my separate networks? I have 2 separate/64 networks on my firewall running each provinces dhcp for IPv6. I have no issues so far I even get my streaming services fine over ipv6. We gave up completely on Android phones, way to many issues with them. Invasive containers and such. Just felt unsafe with them. iPhones are what we got. I can see why… android might want the good containers to be auto loaded with IPv6 also… I was concerned about invasive ones.
-
@JonathanLee Your tinfoil hat is bit tight I think.. You and your invasive containers.. Why/How do you think eui-64 has anything to do with protecting networks.. What IP you use on your different segments has zero to do with anything be it ipv4, ipv6.. Or what method you use to get said address be it dhcp, dhcpv6 or slaac..
-
@JonathanLee said in IPv6 EUI-64??:
@JKnott does that provide a way to protect my separate networks?
For that, it makes no difference whether you use SLAAC or DHCPv6. It's your firewall that protects your network.
-
@johnpoz I just want eu-64 to track addresses is all on private lan, it would link MAC address to ip6
-
@JKnott True, but it would be kind of cool if the Firewall, NBD and DHCPv6 were all interlinked (When using GUA addresses) so that:
- A client which does not complete DHCPv6 for a GUA address is not allowed access to anything through the firewall. Either you have a DHCPv6 address (static/dynamic) or you are dead in the water.
- The DHCPv6 server issues only EU64 GUA addresses to clients to make tracking of MAC/IP combinations straight forward
- The firewalls NBD service only responds to static mapped MAC->IP addresses listed by the DHCPv6 servers clients. (obviously NBD for Link local v6 needs to work - otherwise the client would newer get a IPv6 address in the first place)
Sure would make tracking clients a fair bit more simple. :-)
But - the real ballbuster in client tracking is the fact that we are STILL missing IP level protocol support for forcing the clients to identify themselves with a OS name and OS type/version and have that registered in DNS/DHCP dynamically. Why that is not a part of DHCPv6 so you can set that as a requirement in RA packets still escapes me.
Easily spoofed I know, but so is everything else. But for normal clients this would make management, tracking and forensics infinitely more simple. -
What part of IPv6 wanting to hide client info is not clear.. Shoot clients now change their mac also as a way to hide client info, and ipv6 temporary address change, and that is what they normally use as source for outbound connections.
If you want to know what client is what in ipv6 - set a static. and disable its use of temp addresses. Effective filtering IPv6 needs to be done at the prefix level if your wanting to control where a client can go or can't go.
-
@johnpoz again a static IPv6 still requires the admin to use a client MAC address. Eui-64 just uses the mac as part of an IPv6 address. Any MAC address can be spoofed again eui-64 for home use it just makes it a bit easier to track stuff without hand inputting every static mapping. Is there anyway to enable eui64 in pfSense?
-
@JonathanLee I have no idea what your going on about.. Let your device get whatever IP it wants to get, its going to use a temp address to talk to stuff anyway.. Unless you have disabled that.
With ipv6 you filter at the prefix level - who cares what the devices IP address is..
The only time your going to need to know the clients IP address is if its serving something that you want to all other devices to get too.. So either set it static, or set it via dhcpv6..
-
@JonathanLee said in IPv6 EUI-64??:
about 2 hours ago
@johnpoz again a static IPv6 still requires the admin to use a client MAC address. Eui-64 just uses the mac as part of an IPv6 address. Any MAC address can be spoofed again eui-64 for home use it just makes it a bit easier to track stuff without hand inputting every static mapping. Is there anyway to enable eui64 in pfSense?
What you do is start by blocking everything and then enabling only what you want. With SLAAC, a device will have 1 consistent address and up to 7 privacy addresses, where you get a new one every day. The privacy addresses are used for outgoing connections and you'd use the consistent one if you wanted to set up a server, etc..
-
@johnpoz this temp IP is new to me I haven’t used IPv6 much it is still weird to see 3 ip addresses for IPv6 on a device. Just to confirm pfSense can’t enable EUI-64 there is no option for it?
-
@JonathanLee said in IPv6 EUI-64??:
still weird to see 3 ip addresses for IPv6 on a device.
Give it a week. You'll see 8 global address and 1 link local. 7 of those global addresses are temporary. You get a new one every day and the oldest falls off the list. For more fun, you can enable Unique Local addresses for another 8!
-
@JonathanLee said in IPv6 EUI-64??:
pfSense can’t enable EUI-64
I have not use it myself and therefore don't know the effect it got on pfSense but check this Reddit thread:
https://www.reddit.com/r/freebsd/comments/1awv0jw/ipv6_privacy/
Quote from the thread:
Privacy extensions can be enabled with these sysctl tweaks.
net.inet6.ip6.use_tempaddr=1 net.inet6.ip6.prefer_tempaddr=1To make it persistent add it to your sysctl.conf
Also add this to your rc.conf
ipv6_privacy="YES" -
@patient0 thank you that is what I am after. A way to activate that protocol Thank you. I would need to disable them on my needs thoe
-
@JonathanLee said in IPv6 EUI-64??:
How do I enable IPv6 EUI-64 on my IPv6dhcp server?
I missed the EUI-64 part of the question earlier. EUI-64, like EUI-48 before it, is simply a MAC address. It's not something you enable. With IPv6, it's emulated by sticking FFFE in the middle of the 48 bit MAC and flipping the 7th bit.
Given that EUI 48 or 64 is determined by hardware, I don't see why you're worried about it. Here's some info about where EUI-48 & EUI-64 are used.
-
@JKnott Yes I want to use it. I would like to utilize EUI-64/EUI-48
I want to expose my MAC address inside of the ipv6 address for local hosts. I want to see the MAC address of the host inside of every ipv6 address that is assigned from pfsense to the clients.
That is my ultimate goal.
net.inet6.ip6.use_tempaddr is set to 0 already however I am not seeing a mac addresses within the ipv6 addresses
"bit-reversed order, non-canonical form" So it might be in big-endian or little-endian. I might have them already displayed however to the average user that is something they would assume is incorrect.
-
@patient0 said in IPv6 EUI-64??:
ipv6_privacy
They are all prebuilt system tunables and they have it auto disabled
RESOLVED:
To enable EUI-64
change system tunables
net.inet6.ip6.use_tempaddr=1 net.inet6.ip6.prefer_tempaddr=1 ipv6_privacy=YEScheck status IPV6 dhcp leases and specifically look at the DUID this will now reflect the MAC address of the host using the address. That is it. Mine are clear and match the MAC address now. Easy
"DUID (Device Unique Identifier) is a key part of the DHCPv6 protocol that helps to ensure that each client device on a network has a unique IP address. This prevents the possibility of duplicate IP assignments, which can lead to network issues such as routing loops and DNS conflicts."
-
@JonathanLee said in IPv6 EUI-64??:
@JKnott Yes I want to use it. I would like to utilize EUI-64/EUI-48
On Ethernet, your MAC is EUI-48 and there's nothing you can do about it. If you want EUI-64, you'll have to run something like Firewire or Zigbee. As I mentioned, IPv6 emulates it by converting the EUI-48 by sticking FFFE in the middle. There is nothing else to do.
What's described above, in the system tunables, is enabling privacy addresses. With SLAAC, you normally get up to 7 of them anyway. Privacy addresses have a lifetime of 7 days and you get a new one every day.
Read the link above about EUI-64 and this:
-
@JKnott thanks for the reply. per network fundamentals, EUI-64 at its basics takes the a clients 48bit MAC address and utilizes it in a IPv6 addressing scheme, devices have a hardware address that is vendor assigned into the MAC address that is what is used. However it can be done in different ways it seems…
Don’t quote me on this part, I think every IPv6 has the MAC address ciphered into the address temp or not it just is masked better. The original design is for tracking logs etc. it is just sugar coated now makes everyone feel better about it. The DUID (Device Unique Identifier) is still coded into the IPv6 addresses. I think they use different ciphers for IPv6 unknowingly. No one gets untraceable untrackable devices, how could anyone call anyone else if that was the case. It needs some way to find a device on a network.
In pfSense If you test out turning on or off the directives shared with us, you can see the DUID will include a vendor MAC address into it with clear text, the IPv6 address just masks it better with the DUID. If you set that directive to zero only part of the MAC is included in the DUID, and if you turn the directive to on or 1 it is fully visible under leases area you can see the DUID matches a MAC address. It gets rid of arp request this way.
-
@JonathanLee said in IPv6 EUI-64??:
MAC address ciphered into the address temp or not it just is masked better.
BS.. and this would be done on the client anyway.. Not pfsense..
Why would you think there is something in the pfsense to tell the client how to create their IPv6 address when using slaac?
-
@johnpoz test it you can see the DUID change and it will show a MAC address. The only reason pfSense would let you adapt the DUID in that way is to save time with static IPv6 dhcp addressing. If the directives are turned on the MAC address is inside the DUID in clear text without it on it’s seems to only include two parts of the MAC address in DUID on my system. New to me… again I could be wrong. PfSense would allow you adapt the DUID, just like pfSense gives you the ability to create private addresses and subnets. this adjustment is on the IPv6 dhcp so it’s this is used for private addresses or lan side assignments side. With Non SLAAC.
Is SLAAC public assignments? SLAAC is stateless management right?
I am talking about dhcp of ipv6 where duid is used. They have an algorithm that does not mask the MAC address makes it clear in duid before the ipv6 dhcp lease and creations.
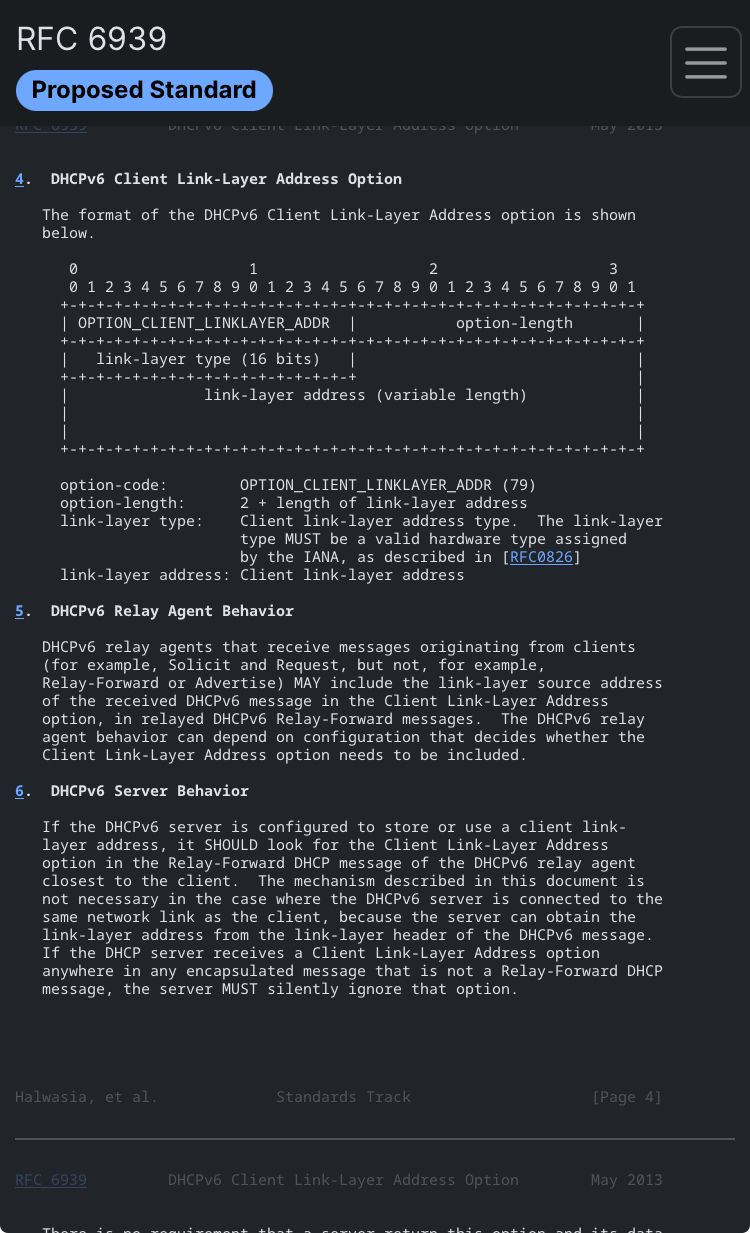
https://datatracker.ietf.org/doc/html/rfc6939
https://datatracker.ietf.org/doc/html/rfc6355
https://www.rfc-editor.org/rfc/rfc8415They do have RFC info for DUID and Mac addressing. IPv6 still makes my head hurt. Again If you can spoof a Mac what good is the secure side of it …