unable to access webserver with static ip and port from pfsense only
-
Yeah without seeing what those are allow/deny they are not all that helpful..
That 2nd rule to pfb_pri would assume is a block, and that for sure could be blocking access, it has been evaluated some.
And as @viragomann mentions that last rule also assuming its a block would not allow access to some port 846 because it doesn't seem like you allow that port above it.
When you post rules, you should include the top part showing what actual interface of pfsense its on.. And we need to see if the rules are allow, deny, reject, etc. Yeah we would assume this is on the lan.. But then the any any rules make no sense unless this is a transit network.. How would you have any source IPs coming into lan that were not lan net? So rules with any as source don't make a lot of sense.
Also do you have any floating rules?
-
@viragomann @johnpoz all rules are allowed except dns 2nd rule and pfblockerng which is reject, also i have tried to clear all rules to default but same issue
no floating rules
I changed to bydefault rules prior to this configuration
this is my home network now i am away my network..please suggest basic standard rules so that i can access webserver from pfsense
-
@Samuelking so your saying with the default any any rule and no other rules, and no rules in floating.. You can not access some public IP on port 846.. Could you pm me this IP and I can check.
I would sniff on your wan when you try and make the connection - do you see the traffic leaving pfsense - is there any response, maybe it is sending back RST, or maybe its just not answering to your IP.
Do you show a state being created in the state table? Are you using a vpn connection?
-
@johnpoz no state table no vpn conf
-
@Samuelking said in unable to access webserver with static ip and port from pfsense only:
please suggest basic standard rules so that i can access webserver from pfsense
I just use any any.. I have no need to limit what my pc can go to ;) My other segments have limiting rules, etc.
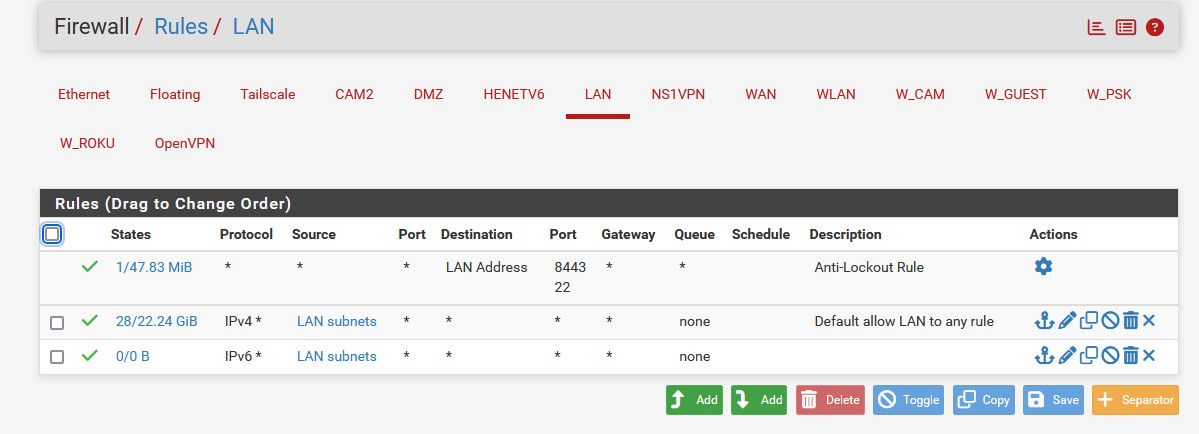
-
@Samuelking said in unable to access webserver with static ip and port from pfsense only:
no state table
Well if there is not state for you trying to go to 1.2.3.4:846 then no you wouldn't ever be able to get there.. Is your client even going through pfsense.. If so there would be a state.. Unless a firewall rule is blocking it.
Your not using an overlapping IP address on your lan are you - have seen crazier things.. Users thinking they can just pull some rando public IP space out of thin air and use it on the local network.. And then can not figure out why they cant get to the public IP range out on the internet ;)
A state would be created for any traffic that is allowed by the rules - even if nothing answers - example just attempted to create a connection to 1.2.3.4:846 you can see the states created.
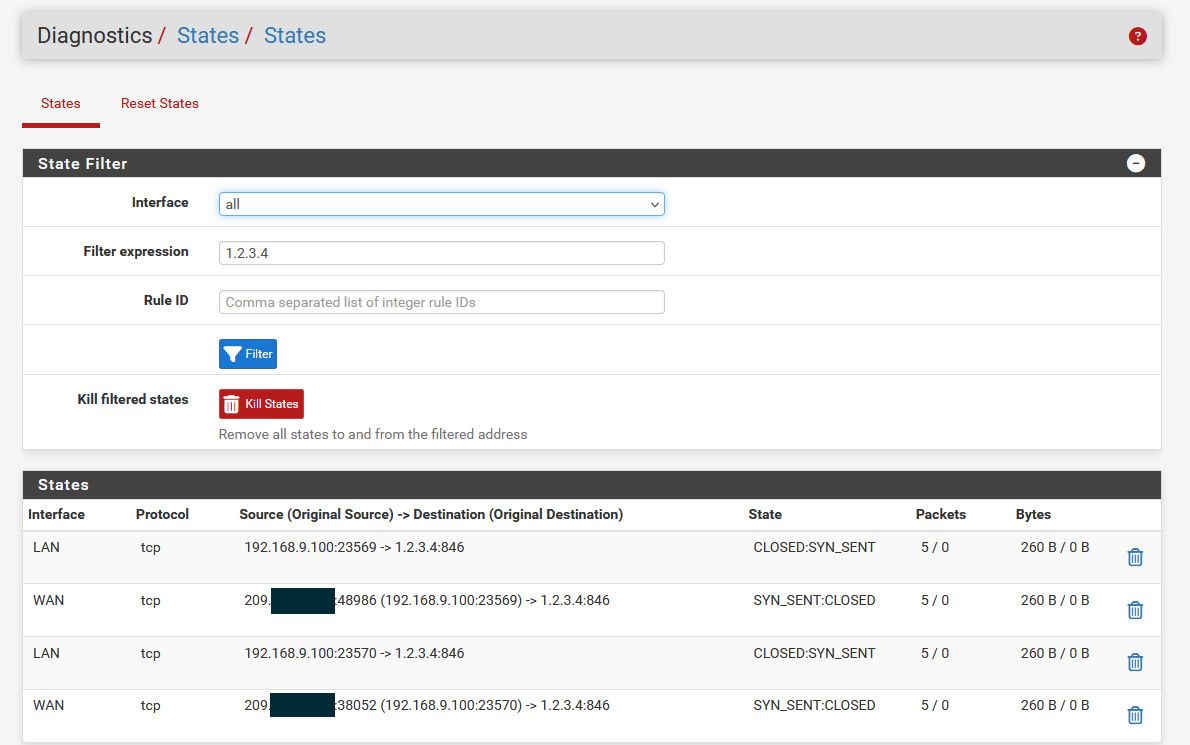
-
@johnpoz @viragomann thanks for replies, now i changed the rules to default but still can't access the webserver with ip i dont know what is going wrong......
-
@Samuelking
What exactly do you get in the browser, when trying to access the website.Did you sniff the traffic on WAN while trying that as @johnpoz suggested?
It's quite easy. Diagnostic > Packet Capture. Select WAN interface, enter the specific port used into the port filter box and start the capture. Then try to access the website and check if you can see the packets. -
@viragomann no packets are captured when trying to access this webserver
-
That's your answer : no traffic, with destination = your web server, reached your WAN interface.
You can stop looking if the issue is related to a pfSense settings as the issue is upstream.Is your WAN IP a RFC1918 or not ?
Same question : is your upstream device an ISP router ? -
@Gertjan said in unable to access webserver with static ip and port from pfsense only:
yes upstream device an ISP router but it is in bridged mode
issue is only with pfsense when i replace it with tplink router i can access easily -
@Samuelking
As there are no relating packets on WAN, sniff on LAN with filtering to the destination port only, to get sure, that the packets even are routed to pfSense.Possibly your testing device uses not pfSense as upstream gateway.
-
Normally, packet capturing isn't even needed.
Here are my WAN firewall rules, some of them are part of a NAT rule :
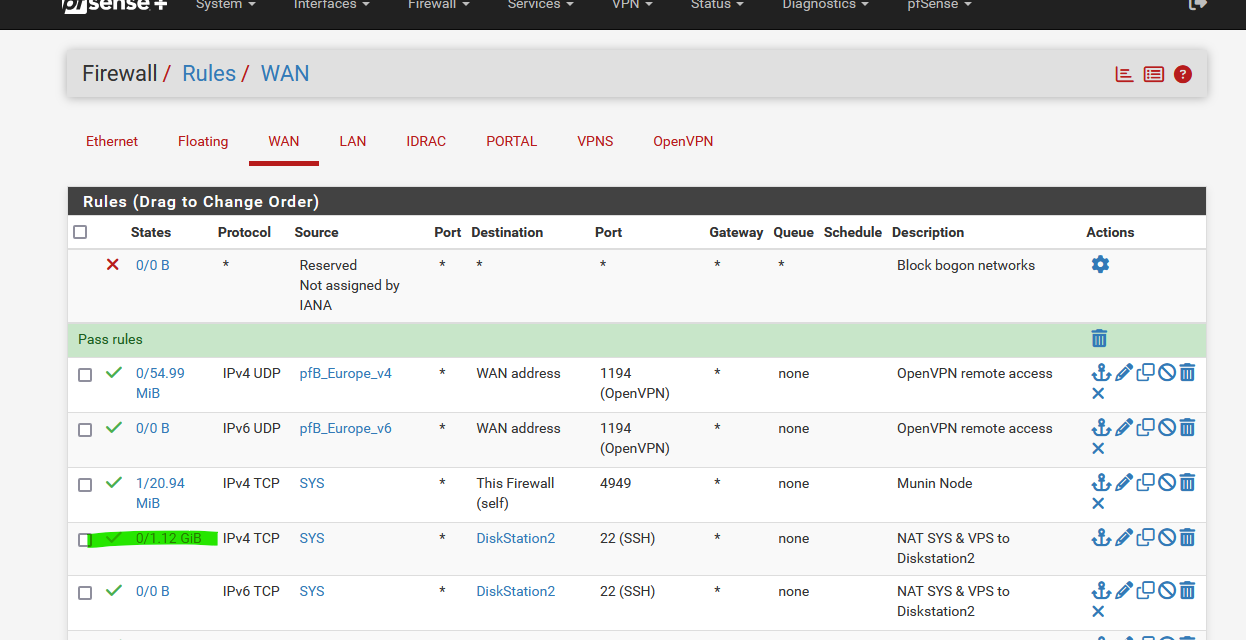
For example (the line marked green), is not a web server (port 80 or 443) but a SSH server on port 22, my diskstation ( = alias diskstation2), living on my LAN, IP 192.168.1.32.
You see the counters marked green ? That means traffic was handled by that rule, which means matching traffic, send to my diskstation2 device, entered the WAN interface.
Is your WAN IP a RFC1918 or not ?
-
@Gertjan I thought he was going outbound to something on the internet.. Not inbound from the internet to pfsense.
@Samuelking your on a client behind pfsense.. And your trying to go to what public IP, please pm me this IP your trying to go to... Or are you trying to let people out on the internet get to some server your running behind pfsense on this port?
If your trying to go outbound to the internet - sniff on the lan side interface do you see your client send the traffic? So you see the traffic get to pfsense lan interface?
-
@Gertjan you were right i am trying to access a webserver on th internet has ip address with port from my network i was using tplink router it was (and is working fine can access webserver when remove pfsense) now i want to change my router to pfsense so that i have more advance features, every is working great can access any every thing but only this webserver causing issues pfsense.
-
Make sure that the WAN IP pfSesne is using is the same one as the TPlonk was using ....
( if possible ) -
@Samuelking said in unable to access webserver with static ip and port from pfsense only:
i am trying to access a webserver on th internet has ip address with port from my network
So you are trying to do a reflection. This IP is your wan IP of pfsense, and your hitting it from some client behind pfsense - and you want to be forwarded to some rfc1918 address on your network..
This is handled with split dns - there really is little reason to hit your public IP if the ip is the box next you on the same network.. Or you have to setup nat reflection.