Secondary separate LAN on OPT1 with WAN access
-
Hello everyone,
I'm trying to wrap my head around this and understand how to do this properly.
The setup here is as follow:WAN and LAN properly configured on pfSense and working without any problem.
Now I have a igc2 port and an old router here that I want to use for a complete separate network.my main LAN on igc1 is set to 10.27.33.xxx range of ips.
pfSense gateway is 10.27.33.1.So the new LAN (OPT1) I'm setting DHCP on and setting the ip as 192.168.0.1/24
the router is in bridge mode with DHCP disabled and set to 192.168.0.197.Is it possible to have 2 LANs like this?
Right now I can't get any IP when connecting over WIFI to this new router.What I want in the end is: have a separate LAN that everything under in can see each other and can also access internet but can not see the 10.27.33.xxx LAN.
EDIT:
I had to enable the DHCP server on OPT1.
And set OPT1 to static IPv4 as 192.168.0.1.Ok, it's working and now I can connect to it and get an ip address on this other network.
Now.. I need to figure out how to let it access WAN, including unbound DNS and pfblockerNG.
-
This are my settings on firewall:
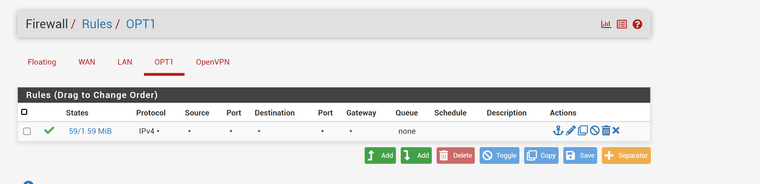
I can access LAN <-> OPT1 which is what I did not want but I can't get internet to work on OPT1.
pinging 8.8.8.8 isn't working either. So it's not a DNS forwarder issue which is configured to input ALL interfaces and output to ALL interfaces.
-
Did a packet capture when trying to ping 8.8.8.8
and
23:38:21.591747 ARP, Request who-has 8.8.8.8 tell 192.168.0.10, length 46
23:38:22.132178 ARP, Request who-has 8.8.8.8 tell 192.168.0.10, length 46
23:38:23.136584 ARP, Request who-has 8.8.8.8 tell 192.168.0.10, length 46
23:38:24.134020 ARP, Request who-has 8.8.8.8 tell 192.168.0.10, length 46
23:38:25.130533 ARP, Request who-has 8.8.8.8 tell 192.168.0.10, length 46
23:38:26.120836 ARP, Request who-has 8.8.8.8 tell 192.168.0.10, length 46
23:38:27.131531 ARP, Request who-has 8.8.8.8 tell 192.168.0.10, length 46
23:38:28.124257 ARP, Request who-has 8.8.8.8 tell 192.168.0.10, length 46
23:38:29.125770 ARP, Request who-has 8.8.8.8 tell 192.168.0.10, length 46
23:38:30.128332 ARP, Request who-has 8.8.8.8 tell 192.168.0.10, length 46
23:38:31.128601 ARP, Request who-has 8.8.8.8 tell 192.168.0.10, length 46
23:38:32.124133 ARP, Request who-has 8.8.8.8 tell 192.168.0.10, length 46
23:38:36.435784 IP 192.168.0.10.57956 > 192.168.0.1.53: UDP, length 36
23:38:36.435995 IP 192.168.0.1.53 > 192.168.0.10.57956: UDP, length 12
23:38:36.439121 IP 192.168.0.10.62011 > 192.168.0.1.53: UDP, length 36
23:38:36.439125 IP 192.168.0.10.63713 > 192.168.0.1.53: UDP, length 36
23:38:36.439220 IP 192.168.0.1.53 > 192.168.0.10.62011: UDP, length 12
23:38:36.439225 IP 192.168.0.1.53 > 192.168.0.10.63713: UDP, length 12
23:38:36.452486 IP 192.168.0.10.63475 > 192.168.0.1.53: UDP, length 36
23:38:36.452547 IP 192.168.0.1.53 > 192.168.0.10.63475: UDP, length 12
23:38:36.455896 IP 192.168.0.10.63475 > 192.168.0.1.53: UDP, length 36
23:38:36.455945 IP 192.168.0.1.53 > 192.168.0.10.63475: UDP, length 12
23:38:36.459264 IP 192.168.0.10.63475 > 192.168.0.1.53: UDP, length 36
23:38:36.459315 IP 192.168.0.1.53 > 192.168.0.10.63475: UDP, length 12
23:38:36.462737 IP 192.168.0.10.63475 > 192.168.0.1.53: UDP, length 36
23:38:36.462781 IP 192.168.0.1.53 > 192.168.0.10.63475: UDP, length 12
23:38:36.466126 IP 192.168.0.10.63475 > 192.168.0.1.53: UDP, length 36
23:38:36.466170 IP 192.168.0.1.53 > 192.168.0.10.63475: UDP, length 12
23:38:36.469195 IP 192.168.0.10.50363 > 192.168.0.1.53: UDP, length 36
23:38:36.469243 IP 192.168.0.1.53 > 192.168.0.10.50363: UDP, length 12
23:38:36.472204 IP 192.168.0.10.50349 > 192.168.0.1.53: UDP, length 36
23:38:36.472224 IP 192.168.0.10.53015 > 192.168.0.1.53: UDP, length 36
23:38:36.472260 IP 192.168.0.1.53 > 192.168.0.10.50349: UDP, length 12
23:38:36.472312 IP 192.168.0.1.53 > 192.168.0.10.53015: UDP, length 12
23:38:36.475274 IP 192.168.0.10.61481 > 192.168.0.1.53: UDP, length 36
23:38:36.475283 IP 192.168.0.10.54480 > 192.168.0.1.53: UDP, length 36
23:38:36.475347 IP 192.168.0.1.53 > 192.168.0.10.61481: UDP, length 12
23:38:36.475357 IP 192.168.0.1.53 > 192.168.0.10.54480: UDP, length 12
23:38:36.478302 IP 192.168.0.10.54480 > 192.168.0.1.53: UDP, length 36
23:38:36.478348 IP 192.168.0.1.53 > 192.168.0.10.54480: UDP, length 12
23:38:36.481302 IP 192.168.0.10.54480 > 192.168.0.1.53: UDP, length 36
23:38:36.481360 IP 192.168.0.1.53 > 192.168.0.10.54480: UDP, length 12
23:38:36.484347 IP 192.168.0.10.54480 > 192.168.0.1.53: UDP, length 36
23:38:36.484393 IP 192.168.0.1.53 > 192.168.0.10.54480: UDP, length 12
23:38:36.487355 IP 192.168.0.10.54480 > 192.168.0.1.53: UDP, length 36
23:38:36.487405 IP 192.168.0.1.53 > 192.168.0.10.54480: UDP, length 12DNS Resolver is excepted to receive at port 53..
So still no idea what is going on here.
-
Finally got it working!
Had to reload DNS Resolver and it started working.
Now I need to create proper rules to block access from one LAN to another and only have WAN access on OPT1. -
@Fandangos this should help :)
https://docs.netgate.com/pfsense/en/latest/solutions/netgate-4200/opt-lan.html
DNS Resolver needs to know about/bind to the new interface.
You probably don’t want to access WAN subnet, but the Internet (any).
-
@SteveITS said in Secondary separate LAN on OPT1 with WAN access:
https://docs.netgate.com/pfsense/en/latest/solutions/netgate-4200/opt-lan.html
This is exactly what I was looking for!
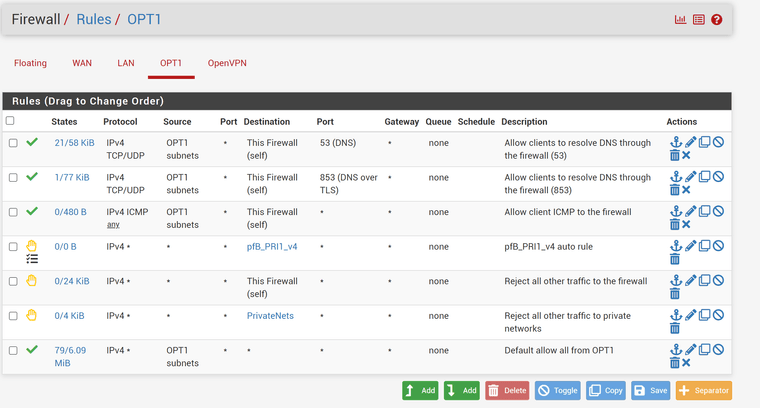
Now I can access from LAN to OPT1 but OPT1 can NOT access LAN and have internet access!
I guess this isn't possible since it's not the gateway (pfsense) that controls the traffic inside a LAN but is it possible to block any client on this network to connect to each other?
-
@Fandangos If you want OPT to access LAN then disable the privatenets block rule.
-
actually what I want is for each device to not be able to see each other which is not possible without a manged switch.
But.. my router has this guest network option:
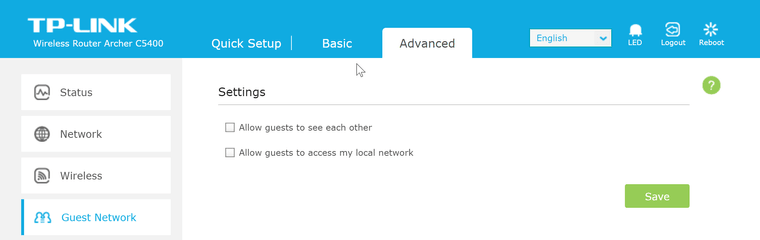
That prevents each device from accessing each other under the same guest network.
But for this to work I need to have DHCP server enabled on my router that is now just an access point in bridge mode.
Is it possible to have a router to connect with it's WAN port to pfsense, receive and IP, have a "sub" DHCP server and enable this feature?
Or this will cause more problems than it should?
-
@Fandangos said in Secondary separate LAN on OPT1 with WAN access:
Is it possible to have a router to connect with it's WAN port to pfsense, receive and IP, have a "sub" DHCP server and enable this feature?
Sure. It's just its own network at that point so it can have its own router.
However you won't be able to prevent the guests from accessing LAN, and have the non-guests access LAN. If the TP-Link provides NAT then they are all the same "WAN" IP coming from the TP-Link.
-
Thank you for answering all my questions.
I just found a managed smart switch that I'll try to create a few VLANs here.
This forum always helps even if I'm too confused to properly put out my doubts.So thank you.