IPv6 still logging despite rule
-
@marcosm
I think i found the setting?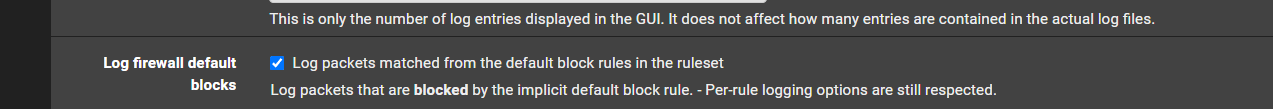
-
@michmoor That's the one.
-
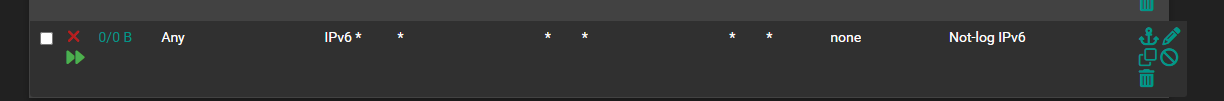
@michmoor yeah if look your rule has never been triggered see the 0/0 in the states column.. That tells you while your rule would block and not log. There was something before it that was blocking and logging.. That checkbox to block all IPv6 puts a rule high up in the rules that is not actually shown in the gui that blocks and logs. There probably should be a block all ipv6 and not log it option.
Or you could just not check that block IPv6 and do your own blocking of it, and log or not log per your rules, etc.
-
Yup that^. If you choose to allow IPv6 in Sys > Adv > Net and then block it with your user rule you can still log IPv4 default blocks which you probably want to see.
-
I typically add a global logging rule to each interface
As an example
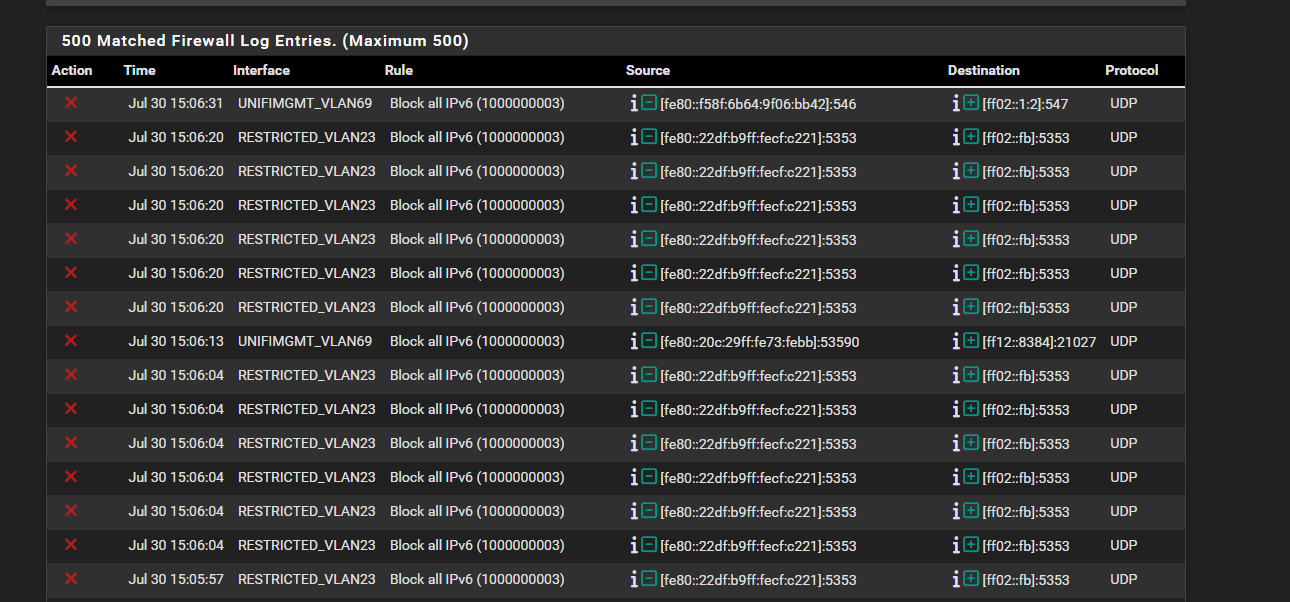
IPv6 was just flooding logs
-
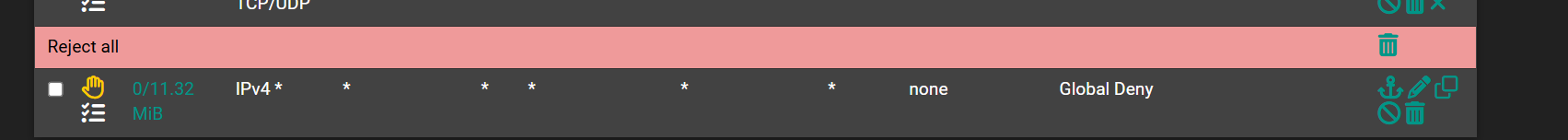
@michmoor out of the box the default deny logs anyway.. If your going to add a reject on the end of your interfaces that logs vs the default deny which is just a block.. You could just turn off the default deny logging.
-
@johnpoz Maybe its me (i accept my limitations here) but this just seems confusing to me. Uncheck this setting or check this setting. Log here but it wont log there...
I feel this should be handled a bit better or at least a clearer explanation. -
@michmoor out of the box it logs default deny.. If you don't want it to log - uncheck the box that says it will log the default deny.. Not sure how that could be confusing?
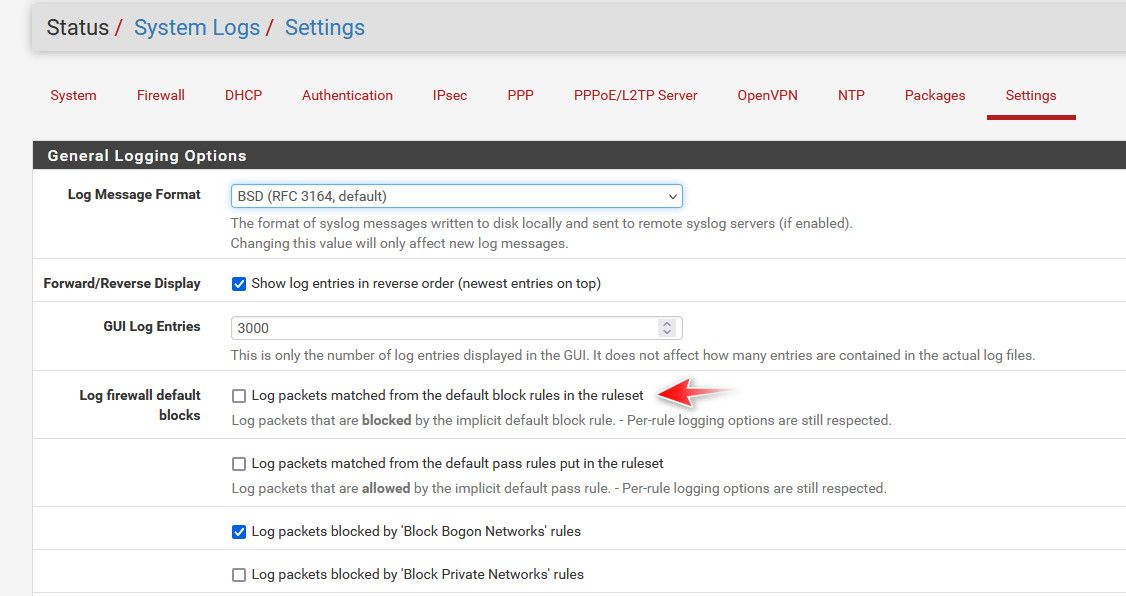
-
@johnpoz
Out of the box log default denies is good but where I’m getting tripped up on is why was IPv6 traffic that is hitting default deny even though I had a rule to stop logging in my floating rules hence this thread. I fixed it but it just seems a bit not straightforward -
@michmoor its not hitting the default deny, its hitting the block all you set..
When you uncheck allow IPv6
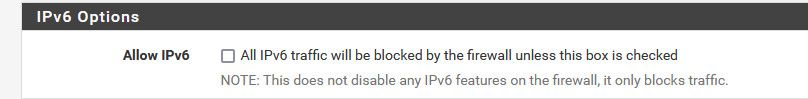
It creates this rule
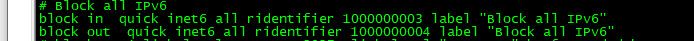
Notice there is no log statement.. BUT!!! if you have the default deny set to log, which is default then when it creates that rule it includes the log statement in the rule
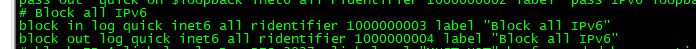
Could it been done a bit better.. Yeah maybe.. Vs using the default deny log setting to determine if the block all IPv6 rule should log, they could have a different check box under where you allow or block all IPv6..
Or maybe in the log settings where they have log bogon, rfc1918, allow and deny etc.. they could have a check box to turn off logging when you uncheck the allow IPv6..
I have personally always turned off the logging of default deny... I have my own rules that log what I want to see, etc. I don't want or need to see all the noise that is blocked by the default deny.. Now if troubleshooting something sure prob a good idea to turn on logging of default deny... But in normal day to day operation I don't need or want to see the vast amount of noise.. For example on my wan I log only SYN traffic that hits my wan that is not allowed.. And then some common UDP ports..
-
@johnpoz Ok i see what you are saying now. I went back and re-read the documentation to solidify my understanding. Granted i think the wording around IPv6 could use some work in the GUI i generally understand what the knobs do here.
Thanks for having patience