communication between vlan
-
Hi, I have set up firewall rules to prevent communication between VLANs, but I can still ping IP addresses from a different VLAN. Can you help troubleshoot this issue please ?
here is the first rule in the VoIP vlan which should block :
Block
Protocol : IPv4 *
Source : VoIP subnets Port : *
Destination : GUEST subnets Port : * -
How are those VLANs defined? How are clients connected to them?
That rule should prevent that traffic if if goes through the firewall, assuming you are trying to ping something in the GUEST subnet.
Unless it is being passed by something else such as a floating rule which would be applied first.
Check Diag > States when the ping is running. Do you see states open on both VLANs to pass it?
Steve
-
here is my vlan configuration:
WAN (wan) -> em0.101 -> v4/DHCP4: 192.168.138.28/24
LAN (LAN) -> em0.102 -> v4: 192.168.102.1/24
VOIP (opt1) -> em0.103 -> v4: 192.168.103.1/24
INVITATIONS (opt2) -> em0.104 -> v4: 192.168.104.1/24as well as my config in the switch:
Port Frame type PVID Input filter Transmit tag Port type
1 101 All disabled Detach PVID Ignoring
2 102 All disabled Detach PVID Ignoring
3 103 All disabled Detach PVID Ignoring
4 104 All disabled Detach PVID Ignoring
5 105 All disabled Detach PVID Ignoring
6 106 All disabled Detach PVID Ignoring
7 107 All disabled Detach PVID Ignoring
8 108 All disabled Unmark PVID Ignoring
9 Untagged Disabled Delete Port C PVIDVID VLAN Name Ports
101 1.9
102 2.9
103 3.9
104 4.9
105 5.9
106 6.9
107 7.9
108 8.9Therefore a computer is connected with an ethernet cable on vlan 3 (VoIP) and at the IP address 192.168.103.4.
Another computer is connected via a wifi terminal which is on the vlan 4 (INVITATIONS) and has the IP address 192.168.104.5.and when I ping I don't see the one in the sates table and I don't have any floating rules either
-
@Nimizu having a really had time understanding what you posted..
Looks like pfsense has this one interface em0 is connected to a switch and everything is tagged.
But what you posted as switch config doesn't make any sense.. There should be a port where your 101-104 vlan IDs are tagged.. Then where you plug your pc into that is on vlan 103.. This should be untagged. Could you post a screenshot of your switch config? Your wan shows its tagged vlan 101 - where is the port on your switch where your modem is connected, that should be untagged I would assume on vlan 101.
And rules on your interface - screenshot also easier to read.
Not sure where your wifi comes into play on what port? but that switch config isn't making much sense.
If your not seeing states in your stateful firewall that you say traffic is working on - this screams that traffic never went through the firewall (pfsense).. Because if pfsense allowed it, there would be for sure a state.
here is my pinging from my lan to my dmz.. notice the state..
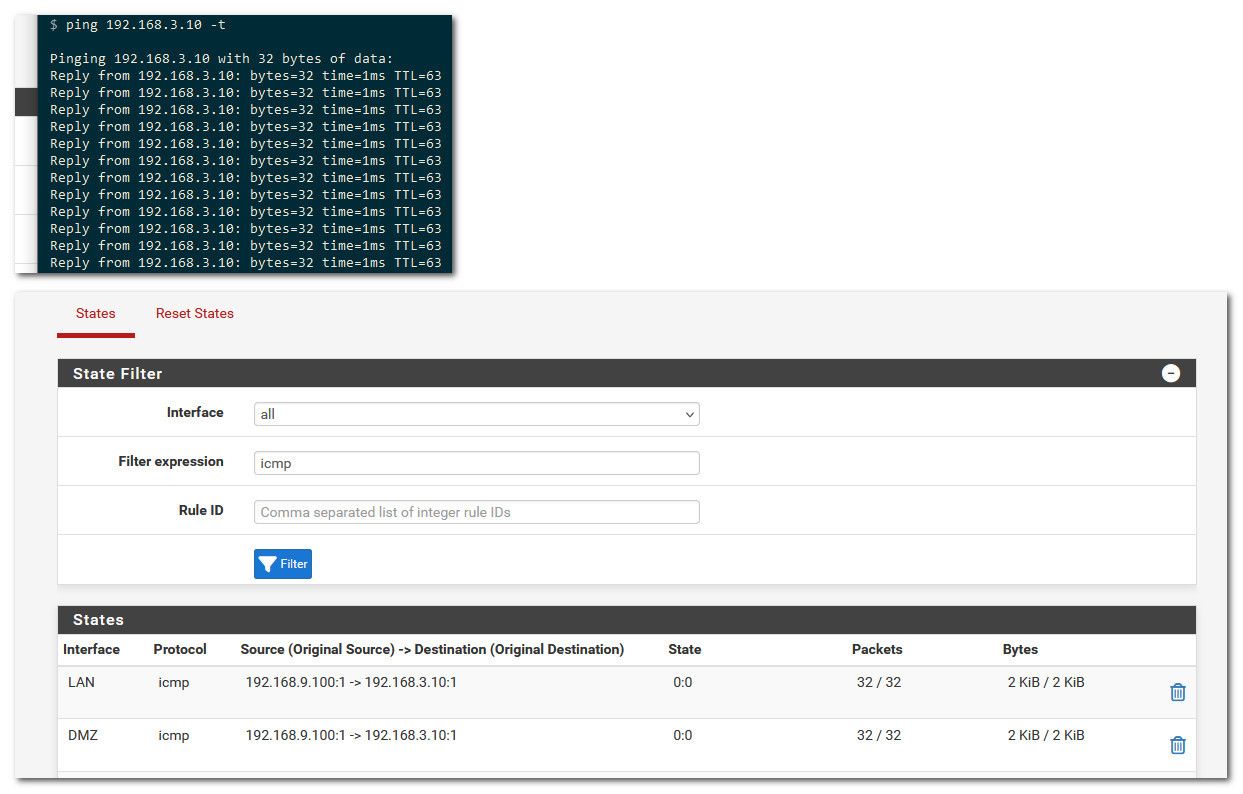
-
@johnpoz said in communication between vlan:
Looks like pfsense has this one interface em0 is connected to a switch and everything is tagged.
That's exactly what it is. The appliance has an on-board switch that must be setup via serial port. See:
https://forum.netgate.com/topic/154826/install-pfsense-on-stormshield-sn300/It's not a layer 3 switch though AFAIK so if no states are created but the ping works between subnets I'd check that one of those device doesn't have IPs in both subnets.
That would imply the switch is leaking traffic between ports however.
-
I redid a configuration from scratch and I still have no state in States.
I tried to ping 8.8.8.8 from the LAN and still don't see anything in States.
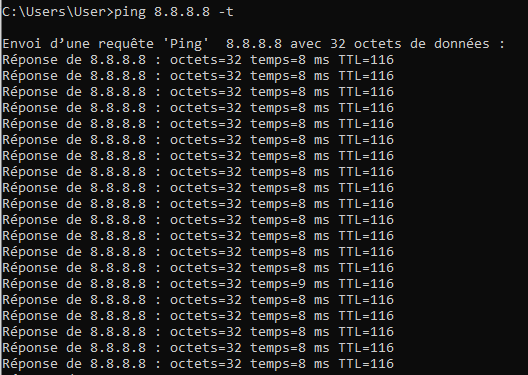
I only have the WAN interface which continually receives icmp packets.
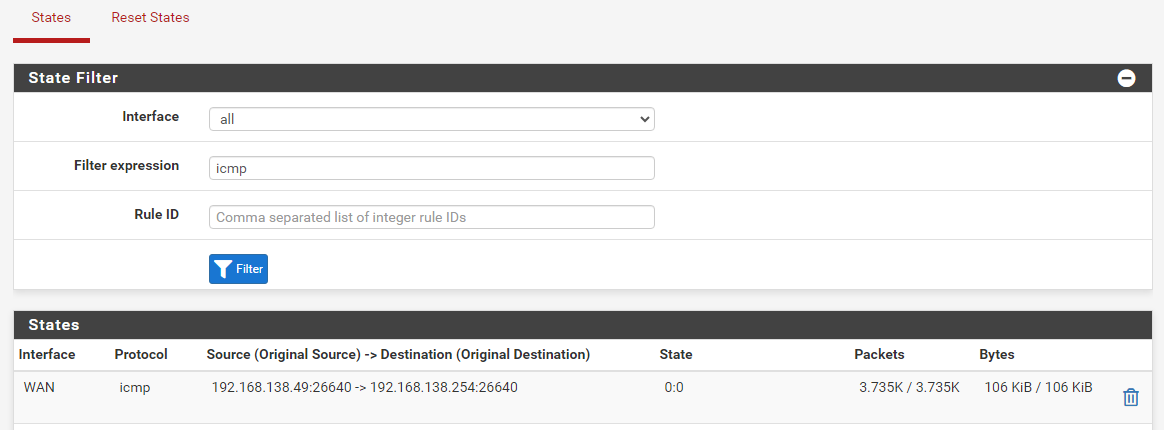
And I checked none of these devices have IP addresses in both subnets. moreover in DHCP leases there are only two IPs distributed to two different stations
-
Ok so that ping is not going through the firewall at all. I assume it must be going directly to your upstream router since that appears to be providing a private IP address to pfSense.
So either that client has more than one NIC or it's connecting to the other router directly through the on-board switch. In both cases though the client would have an IP address in the 192.168.138..0/24 subnet. Does it?
-
@Nimizu said in communication between vlan:
WAN interface which continually receives icmp packets.
I would assume that is pfsense checking if its gateway is alive. Not pfsense being pinged.
If you do not see states in pfsense - then the traffic isn't flowing through pfsense.. Lets see the output of one of these clients on one of your vlans, windows ipconfig /all or linux ifconfig, etc.
But if you ping 8.8.8.8 and you see no state, then the traffic didn't go through pfsense.. what about a traceroute from one of these clients to 8.8.8.8
example - here is trace from one of my clients behind pfsense - clearly see 1st hop is pfsense, and then next hop is my isp, etc.
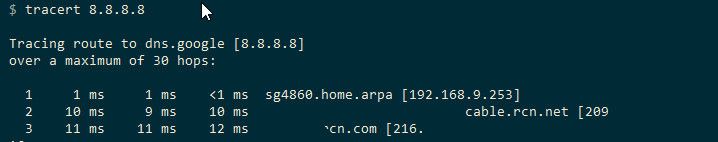
Your trace should show either the 102.1 or 103.1 ip address of pfsense lan and opt1 interface depending on which client your tracing from, then that 192.168.138.254 which I assume is the isp router/gateway in front of pfsense then your isp network, internet, etc..
-
effectively, pfSense is connected directly to the upstream router via a switch which delivers the DHCP address via ethernet cable.
I could have an address of this router via WIFI but when I do the pping I disconnect from this WIFI and only leave the connection via ethernet.
Here is my ipconfig of the client connected on the LAN. I only have this interface connected:
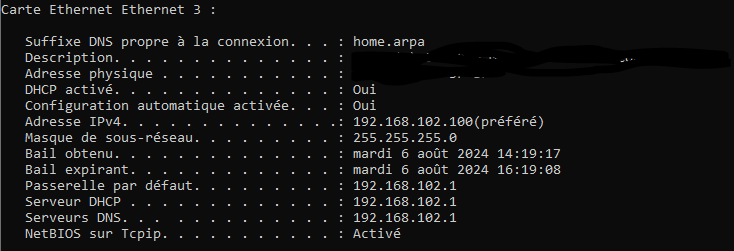
when I do a traceroute of 8.8.8.8 :
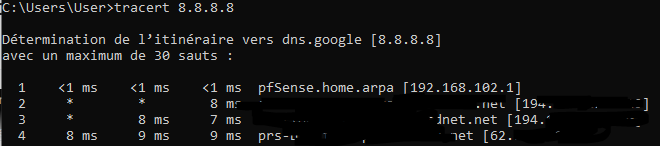
and when I do a traceroute of my other client's IP I get this :
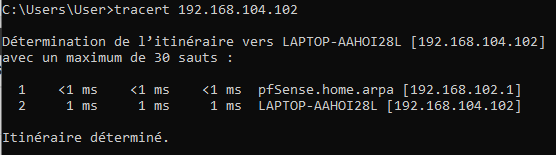
and of course no ping marked in States
-
@Nimizu said in communication between vlan:
and of course no ping marked in States
the icmp states wont be there long.. get a constant ping going
ping ipaddres -t
is windows way to do it..
Now while that ping is running look in your states..
You sure you have firewall running? The only way I could see that working is if firewall is off, but that would disable nat, these clients have internet access while like that, or only if you enable wifi on them? But if you were using pfsense as router only.. It wouldn't be showing you the states for the pings you showed either.
The only other way it could work with firewall off is if your upstream device was natting downstream networks.
-
I don't have a NAT rule to configure and yes my firewall is activated. I tried pinging 192.168.102.102 -t but no apparent change.
For the LAN, internet access was automatic but for the WIFI vlan I had to put rules in place to have internet access
-
Where 192.168.102.1 is the pfSense interface in that VLAN?
If you just ping that directly do you see a state opened for it?
-
@Nimizu well if there are no states being created, there would be no way to block the traffic with a firewall rule.. Because how the firewall blocks the traffic is prevention of a state being created.
So your client on lan or opt can ping 8.8.8.8 - and you see no states with that either?
-
the 192.168.102.1 interface is the gateway for port 2 which corresponds to my LAN.
I tried to ping 8.8.8.8 with the pfsense tool using the LAN interface as the source. But no open state.
All my firewall rules are Pass and not Block or Reject.
-
@Nimizu said in communication between vlan:
I tried to ping 8.8.8.8 with the pfsense tool using the LAN interface as the source. But no open state.
Hmm, you should definitely see a state for that. As long as you are looking whilst the ping is running because the ICMP states expire quickly as johnpoz said.
Try running it from the pfSense command line:
ping -S 192.168.102.1 8.8.8.8Then check for a state in the gui.
-
@stephenw10 said in communication between vlan:
ping -S 192.168.102.1 8.8.8.8
I tried, but again the same result.
I pinged directly into the pfsense shell:
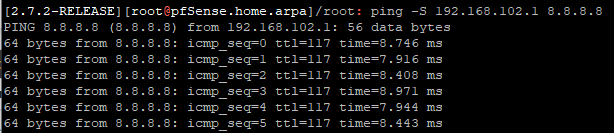
mais je vois toujours uniquement ce résultat meme en regardant en meme temps que le ping :
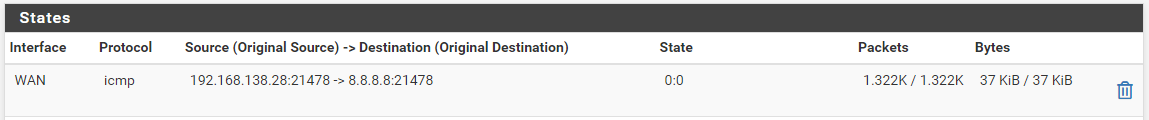
-
Hmm, are you 100% sure that's the same firewall? There is almost no way to have it not open a state for that ping whilst also opening a state for the monitoring pings. You would have to set a rule to pass pings without opening a state. Which is possible but pretty advanced!
Unless that state view is filtered?
You should see like:
[24.08-DEVELOPMENT][admin@6100.stevew.lan]/root: ping 1.1.1.1 PING 1.1.1.1 (1.1.1.1): 56 data bytes 64 bytes from 1.1.1.1: icmp_seq=0 ttl=56 time=25.121 ms 64 bytes from 1.1.1.1: icmp_seq=1 ttl=56 time=5.349 ms 64 bytes from 1.1.1.1: icmp_seq=2 ttl=56 time=5.644 ms 64 bytes from 1.1.1.1: icmp_seq=3 ttl=56 time=5.487 ms 64 bytes from 1.1.1.1: icmp_seq=4 ttl=56 time=6.221 ms[24.08-DEVELOPMENT][admin@6100.stevew.lan]/root: pfctl -vss | grep -A 1 1.1.1.1: ix3 icmp 172.21.16.246:64122 -> 1.1.1.1:8 0:0 age 00:00:58, expires in 00:00:10, 59:59 pkts, 4956:4956 bytes, rule 119, allow-opts -
yes I am indeed on the same firewall.
I tried to do what you just did and I got this result :
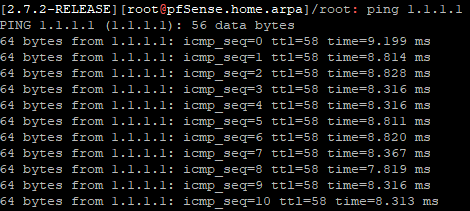
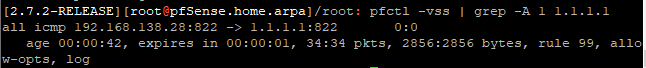
-
Ok, good. You should see that in the gui also if it's not filtered.
You should also see states for pings between VLANs with the correct filtering.
If not try that at the command line too.
-
yes indeed on the graphical interface I see this clearly but as I showed you this is what is there on the graphical interface and which corresponds to the result that I sent previously.
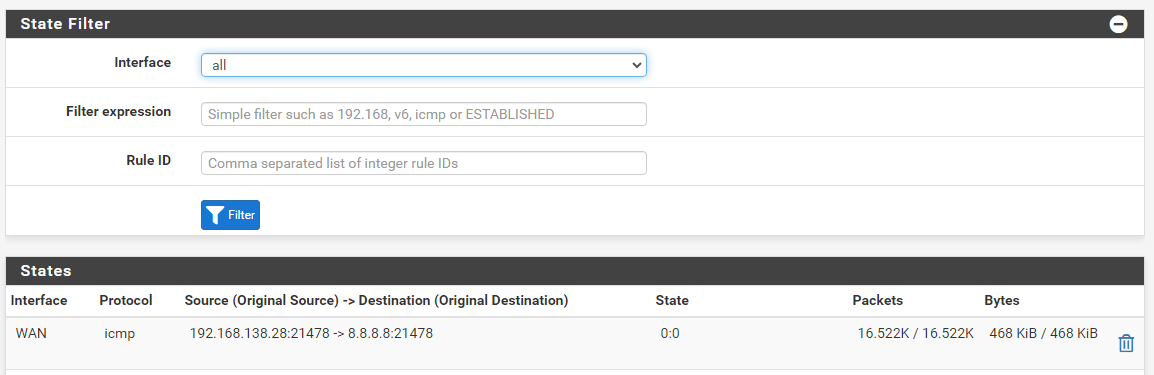
I receive dozens of packets every second in this state even though no ping is in progress