Route traffic throught a site-to-site ipsec
-
Hi.
I have a site A with this subnet: 192.168.100.0/24
In this site there are two gateways with 2 differents internet connections (2 differents public ip):
The main gateway with ip 192.168.100.254. All traffic is routed to this gateway, except a few public ip address that is routed for secondary gateway. In the main gateway there are 7 static routes similar to:
Destination: 80.80.80.80 Route via: 192.168.100.22
The second gateway with ip 192.168.100.222.
The site B (in cloud) have a Pfsense installed with a tunnel configured from Site A (Main gateway) to Site B.
The Phase 2 in Site A is:
Local: 192.168.100.0/24
Remote: 192.168.50.0/24In Site B:
Local: 192.168.50.0/24
Remote: 192.168.100.0/24The diagram:
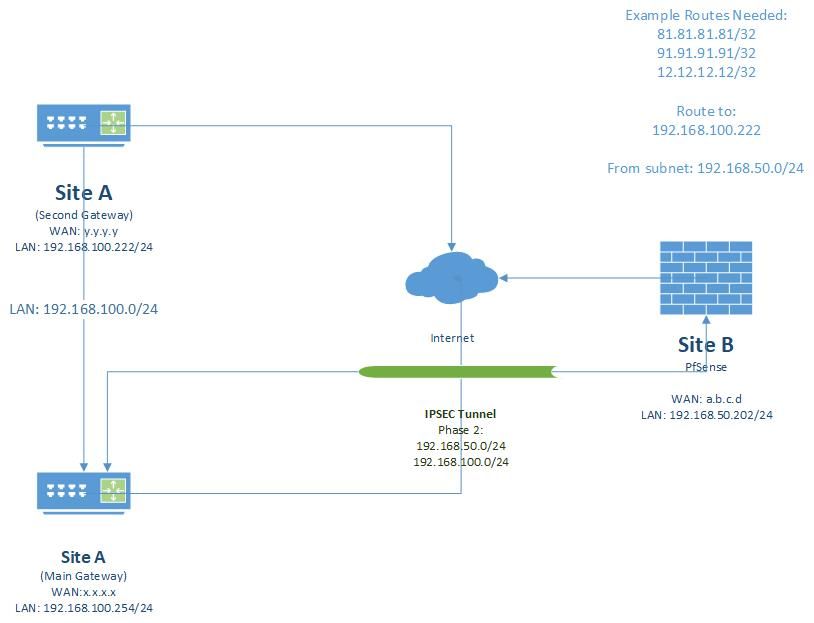
In Site B I need route 80.80.80.80 via 192.168.100.22 in Site A through vpn tunnel.The second gateway in Site A (192.168.100.222) is unmanaged for me, and main gateway 192.168.100.254 i have very limited access.
How i can route via second gateway in Site A from Site B?
In Pfsense i cannot create a static route because the subnet 192.168.100.0/24 is not in any interface in Pfsense.
Thanks you.
-
@albertcd
I guess, it's a policy-based IPSec. If so your only one option is to route the whole upstream traffic from B to A.
It's not possible to route certain destinations with that.This would work with VTI IPSec, OpenVPN or Wireguard, however.
-
@viragomann
Thanks you viragomann.
Then the options can be:- Add 0.0.0.0/0 in phase 2?
- Can i add 7 phase 2 and in Remote IP put the public ip address i want to reach?
It's correct?
Thanks u -
@albertcd said in Route traffic throught a site-to-site ipsec:
Add 0.0.0.0/0 in phase 2?
Can i add 7 phase 2 and in Remote IP put the public ip address i want to reach?Yes, both are possible, presumed it is accepted by the remote site.
It should be sufficient to have only a single phase 2 there with 0.0.0.0/0 as local network. But this is on the IPSec implementation of the certain device. Some insists on equal phase 2 on both sites. -
@viragomann
If i put 0.0.0.0/0 in Phase 2, can i set a rule to pass only the ip addresses i want through the tunnel?
Thanks u -
@albertcd
No, if you set 0.0.0.0/0 at site B all traffic is routed over the VPN. If you only pass certain destination IPs, the rest ist blocked. -
@viragomann
Then i think the best solution is create 7 phases 2, for example:Phase 2 for local subnet:
Local: 192.168.50.0/24
Remote: 192.168.100.0/24Phase 2 for public ip address (one phase 2 for each ip address)
Local: 192.168.50.0/24
Remote: 80.80.80.80/32Is correct?
-
@albertcd
Yes, but as I said, site A has to accept all settings. Which means, you either have to create all phase 2 on A as well or changing the local network in the existing one to 0.0.0.0/0 and see if it works. -
@viragomann said in Route traffic throught a site-to-site ipsec:
Yes, but as I said, site A has to accept all settings. Which means, you either have to create all phase 2 on A as well or changing the local network in the existing one to 0.0.0.0/0 and see if it works.
Reply
Then, if in Site A i change the phase 2 to 0.0.0.0/0 and in site B only created these:
Phase 2 for local subnet:
Local: 192.168.50.0/24
Remote: 192.168.100.0/24Phase 2 for public ip address (one phase 2 for each ip address)
Local: 192.168.50.0/24
Remote: 80.80.80.80/32It should work?
Thanks you for your help! -
@albertcd
It depends on the site A router. It would work if there is a pfSense, but certain other require, that all phase 2 match.
So just try it out. -
@viragomann
It’s a Cisco Meraki the router Site A!
But, i’m thinking now:
The traffic should be routed to 192.168.100.222, not for the gateway 192.168.100.1 (this is the router with the VPN tunnel).
In the 100.1 router have static routes for route the traffic specified throught the 100.222
Is it the same solution (change phase 2 to 0.0.0.0/24)???
Thanks again