Using Managed Switch for Company and Private Networks
-
@bookie56 any "smart" switch that can do vlans can do this.. It could be some 40$ 8 port gig from any of the players tplink,dlink,netgear, and many others that make such switches.
And sure they make 16 ports as well.. Going to be a bit more than the 40$ most likely - 16 port switch are normally a bit more advanced then the very basic "smart" switches that really have basic functionality of being vlan capable.
Do you have any sort of budget in mind? Are you wanting poe as well? Do you care if it has a fan? Do you want it to be cable of L3 stuff, or some of them call them L2+ where they can do basic routing at the switch, etc.
You could do it with 2 of these entry level smart switches as well vs the 4 where you have 8 ports, or 7 really since you need an uplink to pfsense.
Or you could look for say a 24 port switch, maybe give yourself some room for growth.. Are you wanting multigig capabilities, ie 2.5 or 5 or 10ge ports?
You could prob get some old enterprise level gear off ebay for cheap - But!!! keep in mind they normally sound like a jet taking off, and suck lots of juice normally.. While you might save some money up front, you can eat through any savings really quickly with cost of elec to run them.
I am kind of in the market myself - but I keeping my eye out for my unicorn switch ;) managed, multigig, poe, etc.. For under 200 bucks.. Since my cisco sg300-28 is starting to get pretty long in the tooth..
-
@johnpoz Hi

I sort of like TP-Link....they always seem to have good guarantees on their products....have been using them for a while and haven't had any issues.
I don't want it to cost an arm and a leg...but am prepared to pay for the right product...a 24 port switch would be a good solution...
I don't need PoE...
Prefer without a fan...
And I don't need multigig capabilities......
Does that help...
bookie56
-
@bookie56 Not really a fan of the tplink switches.. But sure they should work, few years back they had some issues where you couldn't remove vlan 1, took them forever to fix.. And at first they didn't see anything wrong not being able to remove vlan 1 from any port you wanted to put into a different vlan.
I see the TL-SG1024DE on amazon right now for 89 bucks.. For sure would be able to do what your wanting to do.
edit: I currently have a tplink behind my tv.. It works, its one of the 8 port models that had the vlan 1 issue.. There was a thread on there where user was having a problem with vlans. And was like is this user just an idiot - hehehe.. So I got one myself to play with.. Yup it was borked.. They finally fix the problem, but they never back ported the fix to the older hardware versions. But it was possible to install the v3 hardware firmware onto the v2 hardware..
My tv is on one vlan, and also have a pi sitting back there on a different vlan, etc. Once got the vlan thing fixed only thing I have run into with it.. Is now and then the web gui not working.. Have to reboot the switch to get gui back up, and it has no ssh access, etc.
But even when they were having that vlan 1 issue, pretty sure people said their higher port switches didn't have the problem.. So yeah that switch should work, and not a bad price.. Checks off all the functionality you should need.
-
@johnpoz I can have a look...if you were to recommend a switch?
bookie56
-
@bookie56 see my edit, only reason not a "fan" of tplink is the issues they had with their smaller 8 port switches.. But I don't think that problem was ever on their higher port density models. I am currently using a 8 port tplink switch, it works..
Some quick looking around - that 89$ price seems pretty good to be honest.. I would prob jump on it, since that switch seems to check off all your requirements.
-
@johnpoz ok will do...I will check back in when I have it up and running...
Thank you so much for your time...bookie56
-
@bookie56 happy to help you get it up and running with your vlans when your ready.. You could just use 1 port into pfsense, or 2 since you have 4 networks.. Or since you prob have more ports than you need, you could use 4 uplinks into pfsense for your different segments.
And not have to worry about setting up any tags on any ports, etc.
edit: btw moved this to more appropriate section.. The vlan section.
-
 J johnpoz moved this topic from Routing and Multi WAN on
J johnpoz moved this topic from Routing and Multi WAN on
-
@johnpoz I will be sure to be in touch....have a little to do right now...but will be in touch!
bookie56
-
@bookie56 said in Using Managed Switch for Company and Private Networks:
LAN_PRIVATE
LAN_COMPANY
WIFI_PRIVATE
WIFI_COMPANYAs mentioned, you can use VLANs. You might also want to combine the LAN & WiFi networks, so you only have one each for private and company.
-
@JKnott Thanks for the info

-
@JKnott said in Using Managed Switch for Company and Private Networks:
@bookie56 said in Using Managed Switch for Company and Private Networks:
LAN_PRIVATE
LAN_COMPANY
WIFI_PRIVATE
WIFI_COMPANYAs mentioned, you can use VLANs. You might also want to combine the LAN & WiFi networks, so you only have one each for private and company.
And when you do move to VLAN, you only need one port instead of all 4. It may simplify things a bit and will save you three ports on the switch.
What are you using for WiFi AP's today? If that equipment is capable of VLAN, you can use the same AP for private and corporate, just separate SSID's and subnets.
Perhaps create a diagram showing your setup which will help in restructuring, and deciding what size switch you need.
-
Hi guys...Sorry have been busy....
Ok further to what we discussed earlier..
As shown I have my quad network card that is divided up into the 4 networks as shown below:
LAN_PRIVATE 192.168.120.1 (example)
LAN_COMPANY 192.168.121.1 (example)
WIFI_PRIVATE 192.168.122.1 (example)
WIFI_COMPANY 192.168.123.1 (example)
I am happy with that setup and don't really want to mess with it...I have assigned static IP's in pfsense for several computers and for arguments sake I can assign 192.168.120 10 to keep it on my private system for ease of access...
Now in the TL-SG1024DE I can create vlans...which I need some help with...
on port 1 I have the link from pfsense so that would be used for this port...
I would like to assign 2-16 with my vlan for LAN_PRIVATE...is that possible?I have port17-24 left and would like to assign them to my LAN_COMPANY and use port 17 as the link from pfsense...is that possible?
I have under VLAN: MTU VLAN, Port Based VLAN, 802.1Q VLAn, and finally 802.1Q PVID Setting..
This would mean I can remove three swithches and replace it with just this one...It would be nice to utilise the one swithch for different vlans so that I can keep my private network away from the company one...
How do I proceed?
Or do you need more info?bookie56
-
@bookie56 Fist off all, you use 802.1Q VLAN, which involves two separare Tabs in the TPLink UI (802.1Q VLANS and 802.1Q PVID Settings).
You will need to make Port 1, connecting to pfsense, into a TRUNK port for the VLAN traffic that you want so it can pass to and from pfsense. All ports already handle default VLAN ID 1, so lets say you chose the following:
LAN/WIFI_PRIVATE - default (no changes)
LAN/WIFI_COMPANY - VLAN ID 10And then you need to make ports 17-24 into Untagged ports for VLAN 10.
You could create separate VLANs for WIFI as well but is that really necessary? I guess you want anywone connecting to COMPANY to be able to talk to each other without any special arrangements?
To get started and have pfsense setup for your VLANs you go to Interfaces > VLANs and add a VLAN. Select your LAN interface as your parent interface and enter e.g. 10 for the ID, give it a "name" in the description, like COMPANY, click save.
Now under Interfaces > Assignments there is a new entry where you select your new VLAN and click Add. Then you can Edit this entry and fill in the IP (subnet) for example 192.168.10.0/24 (different from 192.168.1.0/24 as in your default LAN). Simply make it so it mimics what you have under LAN.
Then you go to Services > DHCP Servers and edit the DHCP Server for that VLAN. Finally you need to create rules for the VLAN under Firewall > Rules > COMPANY_VLAN or what that interface ended up being called. Add at least a default allow all rule, but preferably also block rules above that to stop that VLAN from reaching your LAN, and perhaps vice versa.Then, in the TPLink UI, you go to 802.1Q VLANS and start by entering ID 10, COMPANY and tick the TAGGED
So it looks something like this: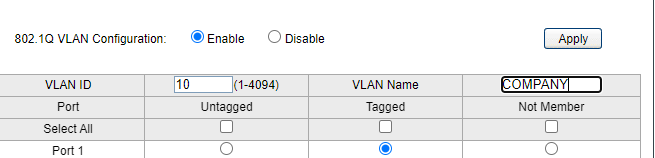
Click Add/Modify.
Then enter 10 again in the box for VLAN ID. Now you click the Untagged button for all the ports that you want to use for COMPANY (17-24) and again Add/Modify, and then Apply.Now go to 802.1Q PVID Settings and tick all the ports you want to make into VLAN ID 10. Enter 10 in the ID-box and click Apply and now anything you connect to those ports will "see" the COMPANY DHCP Server and receive an IP from192.168.10.0/24.
Not sure what you have for WIFI, but there are two alternatives.
- If you have "dumb" AP's you connect them to either a PRIVATE or COMPANY port, and set it's SSID name to something corresponding.
- If you use AP's that can handle VLAN's you need additional TRUNK ports (like port 1) on the TPLink switch for the APs as well. And in the AP(s) you create two wifi networks (separate SSIDs) for PRIVATE and COMPANY. And for the COMPANY network, you give it VLAN ID 10.
The AP will then set any traffic on that wifi network to VLAN ID 10 and it's ethernet port will be set to be able to TRUNK that traffic connected to your switch.
That should do it...
-
Hi Gblenn

Sorry not following much of what you have written...
I reserved port 1 on my private network by using a static IP and Mac address...
I then logged into the switch and applied the settings to keep that IP assigned to port 1
This info?
LAN/WIFI_PRIVATE - default (no changes)
LAN/WIFI_COMPANY - VLAN ID 10
In pfsense I chose my company lan as said for my vlan and as suggested I gave it 10 as an ID and called it Company...
I clicked on Interfaces > Assignments and added the new entry.....
Under Vlan Company I chose IPv4 as my configuration type but couldn't add my company ip subnet because it was the same or being used by LAN_COMPANY...
I want the subnet to reflect my original LAN_COMPANY or am I thinking wrong?
I have 192.168.121.2 to 192.168.121.20 as my range for that card...
Sorry....this is not my best area of expertise....bookie56
-
@bookie56 Ok, as I read your first post again I realize there might be a mixup between ports on pfsense and the TPLink switch.
I was referencing Ports on the switch, not pfsense. And I was assuming only one LAN port being used on pfsense.
Your current setup however is if I understand it correctly, utilizing all four ports on the Quad Card that you have.What are you using for wifi? Some AP's like Unifi or TPLink perhaps?
Do you agree that it can be a good idea to maintain only two "networks". One for Private and one for Company? That means LAN and Wifi are on the same subnet...
Anyway, if you want to keep COMPANY in 192.168.121.0/24 range that can be done, if you need it. But then you need to remove or change your current COMPANY LAN to something else. Doesn't matter what. Because you want to use that subnet for the VLAN instead...
Same thing with both your WIFI networks. There I assume the subnet doesn't matter that much, right?? No static leases for servers etc?So let's say igb0 is your WAN and igb1 is your LAN used for PRIVATE today. Let's say that interface has IP 192.168.1.0/24, and your pfsense web interface is accessed at 192.168.1.1
So igb1 will need to be connected to Port 1 on the TPLink switch. None of the other ports on the Quad card need to be connected.
Here's the documentation on VLAN configuration.
https://docs.netgate.com/pfsense/en/latest/vlan/configuration.html#web-interface-vlan-configurationStep 1: Create the VLAN to be used for COMPANY, using VLAN ID 10. The only difference from the picture in the documentation is that you select igb1 (if that is your LAN).
Step 2: Interfaces > Assignments will show a new item at the bottom where you click +Add. Then you edit this new interface and call it COMPANY and set it to static IP 192.168.121.0/24. (Assuming this is not already used elsewhere, in which case you need to change or delete the other interface).
Step3: Services > DHCP Server, edit the new COMPANY DHCP Server as you need.
Step4: Firewall > Rules > COMPANY_VLAN, create a pass all rule. Later on when you have it working you should consider adding a block rule for other VLAN's.
Now you log into the TPLink switch and follow the instructions I had before, starting with the picture I pasted and then to the end of that post.
-
@Gblenn Hi again...
When I was looking for a setup at home ...run business from home...
I mentioned I would like a private network and a company one...plus I wanted en access point for private and one for company...they are tp-link men not at home at the moment...so not sure...
I was told that a quad would suit my needs....
Because I only thought logically...that is why I bought the quad...
Anyway I will be at home later and can work with your info...
I had a thought...I only have reserved ip addresses on my private network so it doesn't matter what I name the range for company....
Just that port1 is directly linked to the private network and all computers that are linked to the private network already have reserved ip adressen and I would like to keep them as such...Thank you so much for your time
bookie56
-
@bookie56 said in Using Managed Switch for Company and Private Networks:
@Gblenn Hi again...
When I was looking for a setup at home ...run business from home...
I mentioned I would like a private network and a company one...plus I wanted en access point for private and one for company...That is perfectly understood and makes complete sense. However access point and wifi access can mean slightly different things.
Most Access Points (AP's) can serve multiple SSIDs = multiple wifi networks. So one single AP can let you have several wifi-networks with different passwords. Depending on the capabilities you could then have them separate the traffic by VLAN.they are tp-link men not at home at the moment...so not sure...
Ok so check out what model it is so we can figure out the capabilities... Also, how many do you have? And where are they located? Not that it matters from the perspective of VLANs but it may matter from a radio coverage perspective. Are they in different parts of the home for example? My point is that if you have two AP's, at either ends of your house, they can still serve both Private and Company needs.
Also on the Private side you may have connected TV's, Receivers and the likes that are connected via cable (Ethernet). Or you have a media server in your NAS perhaps. Then it will help if your phone ends up on the same subnet as the server, so they can "find each other" without any additional work from your side.I was told that a quad would suit my needs....
Because I only thought logically...that is why I bought the quad...No worries, might prove to be useful at some point. Are you running pfsense directly on the PC/Server or is it perhaps virtualized?
Anyway I will be at home later and can work with your info...
I had a thought...I only have reserved ip addresses on my private network so it doesn't matter what I name the range for company....
Just that port1 is directly linked to the private network and all computers that are linked to the private network already have reserved ip adressen and I would like to keep them as such...Sure, that is no problem at all. So the way forward is to keep Port 1 as it is. And I was anyway assuming it is actually the default LAN that you started out with, when you first set up pfsense. That will be your LAN also going forward, so no changes there. And the Company network will run as a VLAN on top of that, clean and simple.
And I have to ask, are you located in Sweden by any chance?
-
@Gblenn Sweden....what ever gave you that idea

I have 2 x TP-Link EAP245 AP's
My wifi doesn't get affected by this switch at all...they have there connections to:
WIFI_PRIVATE and WIFI_COMPANY on my quad...
This switch is mainly for the LAN side of things...most computers are LAN_PRIVATE.
I have firewall rules in place so that those networks don't talk to each other... or with LAN_COMPANYWhen I work on customer computers I either connect to the WIFI_COMPANY which is just above my head....
 or the LAN_COMPANY which up and til now has been two standard unmanaged switches.... hence my interest to get rid of them and replace them with the new one...
or the LAN_COMPANY which up and til now has been two standard unmanaged switches.... hence my interest to get rid of them and replace them with the new one...This is only an 84 square meter flat so one AP is in the living room behind the tv and the other above my head in the office....YES I understand what you are saying about using both to feed both networks....but because of the size of the flat I have very good connections speeds where ever I am...(Good point though)
If I run speed tests from my kitchen to the living room which is around the corner....YES I lose some speed - but we have 500 up and 500 down so it doesn't really affect us...Like I said the Wifi AP's are directly fed by network cables coming from my pfsene router which at the moment is an old Asus Gaming:
Motherboard 1155
Processor i7-3770 3.4GHz
2 x 4 GB PC3-1200
Intel 520 Series SSD
Dell Pro 1000 VT PCieI even have a reserve router with pfsense that I keep updated so that if something goes pear shaped I am up and running quite quickly
All private connections are ip and mac reserved in pfsense....I have a cubiQ CS 1794 from Aten on an adjustable height bench which is always up....
Under there I have several feeds that come from this switch so I can work on several computers at once...
These cable feeds have two network cables that serve the private or company LANS depending what I have connected at the time..bookie56
-
@bookie56 Sorry just a quick update to information....
I have the quad card just for my networks and the inbuilt network is for WAN which keeps it totally separate from the quad Card...Not to complicate things ....just a thought....I really only need max 10 ports for my LAN_PRIVATE and I hve a server which has two network ports one for main incoming (connected by reserved ip on LAN_PRIVATE) and the other for Clonezilla...it would be nice to utilise 4 ports for that....one for the link from the server and the other 3 for cloning...never going to need to clone more at once than that....
Is that possible in this setup.... I then have got rid of a third switch ?bookie56
-
@bookie56 said in Using Managed Switch for Company and Private Networks:
@Gblenn Sweden....what ever gave you that idea

Two tiny skrivfel...

plus I wanted en access point for private and one for company...
they are tp-link men not at home at the moment...so not sure...I have 2 x TP-Link EAP245 AP's
My wifi doesn't get affected by this switch at all...they have there connections to:
WIFI_PRIVATE and WIFI_COMPANY on my quad...
This switch is mainly for the LAN side of things...most computers are LAN_PRIVATE.
I have firewall rules in place so that those networks don't talk to each other... or with LAN_COMPANYOk so if you don't want to touch that, it's fine but I'm just saying it would perhaps streamline and simplify things from a rules perspective. And it would free up two additional ports on your pfsense... With that CPU/Motherboard you have plenty power to run other things on it as well. Why not Omada controller for your AP's...? Then you can manage both AP's from one single interface.
When I work on customer computers I either connect to the WIFI_COMPANY which is just above my head....
 or the LAN_COMPANY which up and til now has been two standard unmanaged switches.... hence my interest to get rid of them and replace them with the new one...
or the LAN_COMPANY which up and til now has been two standard unmanaged switches.... hence my interest to get rid of them and replace them with the new one...This is only an 84 square meter flat so one AP is in the living room behind the tv and the other above my head in the office....YES I understand what you are saying about using both to feed both networks....but because of the size of the flat I have very good connections speeds where ever I am...(Good point though)
If I run speed tests from my kitchen to the living room which is around the corner....YES I lose some speed - but we have 500 up and 500 down so it doesn't really affect us...Sounds like you are all good then, wrt wifi...
Like I said the Wifi AP's are directly fed by network cables coming from my pfsene router which at the moment is an old Asus Gaming:
Motherboard 1155
Processor i7-3770 3.4GHz
2 x 4 GB PC3-1200
Intel 520 Series SSD
Dell Pro 1000 VT PCieI even have a reserve router with pfsense that I keep updated so that if something goes pear shaped I am up and running quite quickly
All private connections are ip and mac reserved in pfsense....I have a cubiQ CS 1794 from Aten on an adjustable height bench which is always up....
Under there I have several feeds that come from this switch so I can work on several computers at once...
These cable feeds have two network cables that serve the private or company LANS depending what I have connected at the time..Ok so then you will only drop one of the connections from pfsense, the COMPANY port.
This since you will be basing the COMPANY VLAN on the same Port you use for PRIVATE.Basically no changes at all on the PRIVATE side, rules, DHCP or anything. If you are ok using a new subnet for COMPANY, I suggest you do that. Then you can just disable the current COMPANY interface and leave it until you might need it for something else.
So all you need then is to create the VLAN for COMPANY as per the Netgate documentation, making sure you select the right parent interface (the one used for PRIVATE LAN).Edit the rule on PRIVATE (if you have one) so that it can't access COMPANY_VLAN), and add a rule for COMPANY_VLAN so that it can't connect to PRIVATE and you are done...