WAN with /64 Delegation
-
@Bob-Dig
Perfect. I was able to get it up and running using NAT! All my clients can get out on the one single IPv6 address my pfSense has on the WAN side.Now for my next project... Incoming port forwarding.... I expected it to work the exact same way as IPv4 does using Firewall/NAT/Port Forwarding, but for some reason, it isn't that simple.... I guess back to the drawing board for that part :)
Either way, thank you so much @Bob-Dig for your help! I at least got my outbound IPv6 up and running!
-
@meluvalli said in WAN with /64 Delegation:
Now for my next project... Incoming port forwarding.... I expected it to work the exact same way as IPv4 does using Firewall/NAT/Port Forwarding
Actually it is. If it is not working it may be a problem with your ISP? It has been some days (years) when I ran pfSense like this though.

-
@Bob-Dig
I did a packet capture in pfSense for port 443 (It's a website) and it sees it coming in, but never gets to my server... So I know the ISP isn't blocking it... It's got to be something I have screwed up :(. I'll keep looking into it! Again, I really appreciate your help! Thanks again! -
@meluvalli said in WAN with /64 Delegation:
I expected it to work the exact same way as IPv4 does using Firewall/NAT/Port Forwarding, but for some reason
IPv6 - if implemented correctly, doesn't need NAT anymore.
Just a firewall rule on the WAN that says :
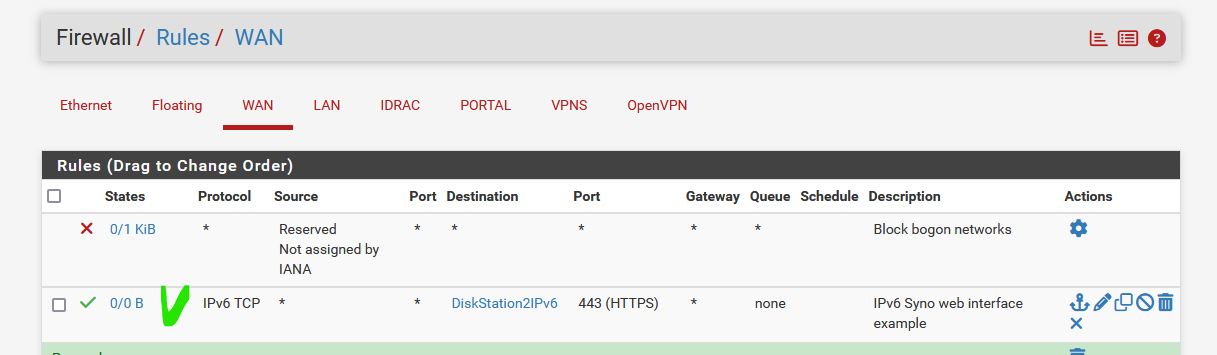
As the WAN interface will be "all the prefixes" so, a /56 or whatever
and- example here -the alias DiskSaton2IPv6 is the GUA IPv6 (an IPv6 in one of my prefixes used on one of my LANs)
this is all it needs to make it accessible.
There is no more Network Address Translation. You can of course still use Port Address Translation, like port "443" to "8443"
After all, the IPv6 my Diskstation2 is using is an IP address that is usable (addressable) world wide. -
@meluvalli said in WAN with /64 Delegation:
I did a packet capture in pfSense
I did too and it is working. Now I don't run anything on that IP, will have to look if I find something to test easily.
-
@Bob-Dig
I got it working! It was my Linux server didn't have the gateway set :) Once I inputted the gateway for IPv6 all is well!Thanks again!!!!
-
@Gertjan said in WAN with /64 Delegation:
If an ISP providing just one /64 then that is actually completely wrong.
Not completely.

If you have only one /64, it is still good for some NPtv6. Because with that there is some end-to-end reachability for outgoing.
The firewall has not to "change ports" for outbound traffic, as long as real ULAs are used.Example: Lets say we have 3 interfaces with ULAs:
fd1::123
fd2::456
fd3::789fd2::456 gets translated to 2001::456 and goes out to google.
Now the firewall has a firewall state for google and fd2::456.
When traffic comes back in from google to 2001::456 it will be translated to all three ULAs. Two will be dropped but one will pass because there is a state.At least that is how I think this works.

For unsolicited incoming traffic this is not done, maybe it is to dangerous? It will be translated only to the first ULA-Prefix in the list.
Maybe I made this up and there is a NAT-Table for NPT, although it is said that NPT is stateless.
@stephenw10 can slap me if I am wrong. But I do think that you can use one GUA-/64 and use it with several ULA-/64 in pfSense for outgoing. Would be interesting to know how that is actually working.
-
@meluvalli said in WAN with /64 Delegation:
Unfortunately, IPv6 has very limited configuration in the gateway itself.
Is it in bridge or gateway mode? You need bridge mode. ISPs use DHCPv6 to provide a prefix to a router, such as pfSense. However, gateway mode will not pass it. Your ISP should have a /64 on the WAN and hand out a prefix.
I've been using pfSense for about 8 years and it works fine with IPv6. In fact, IPv6 was the reason I switched to it, as the Linux based firewall I had been using wouldn't work with DHCPv6.
-
@meluvalli said in WAN with /64 Delegation:
I got it working! It was my Linux server didn't have the gateway set :)
The gateway should be provided automagically by pfSense, using router advertisements.
-
@JKnott said in WAN with /64 Delegation:
The gateway should be provided automagically by pfSense, using router advertisements.
That is true, you should activate Services>Router Advertisement on all interfaces with IPv6. Unmanaged probably will do.
-
@Bob-Dig
I'm using RA in Managed mode. I also have enabled DHCPv6 Relay. I have a DHCP server that hands out IPv6 addresses because I prefer to have managed IPv6 addresses so I know the IPv6 address of each client statically. I then assign IPv6 addresses based on UUID.My servers I have set for STATIC IPv6 addresses instead of DHCP.
Only problem I have seen with this setup is some devices (Like Google Display Hub) do not get an IPv6 address. I am not really sure as to why though since all my Windows/Linux devices can get an IP via my IPv6 DHCP Server.
-
@meluvalli said in WAN with /64 Delegation:
I have a DHCP server that hands out IPv6 addresses because I prefer to have managed IPv6 addresses so I know the IPv6 address of each client statically.
I only do that for my servers. But in a NAT scenario I wouldn't care.
Thanks to @JKnott everyone around here knows that Android is not supporting DHCPv6.
-
@Bob-Dig
Yah. I think I remember reading that somewhere :) But, my AppleTV doesn't either (Odd considering my Macbook and iPhone both do though.). So... Google isn't alone...
-
@meluvalli said in WAN with /64 Delegation:
I have a DHCP server that hands out IPv6 addresses because I prefer to have managed IPv6 addresses so I know the IPv6 address of each client statically.
Use SLAAC. It just works. Thanks to some genius at Google, Android doesn't support DHCPv6. Also, with SLAAC, you get 1 consistent address, which can be based on the MAC address or a random number. You also get up to 7 privacy addresses, with a new one every day. The most recent is used for outgoing connections. Use the consistent address as static, as it is, unless you change the prefix.
-
@JKnott
On my network I am using dnsdist and use specific DNS servers based on source Address (local client). If I use SLAAC and the IPv6 address changes on the client, then dnsdist wouldn't be able to determine the client and would use the wrong DNS server for that client. That's why I am using DHCPv6 with assigned IPv6 addresses based on UUID. -
OT: Maybe you don't want IPv6...
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-38063 -
@Bob-Dig
Why not? They apparently fixed it! ROFL :) -
@meluvalli said in WAN with /64 Delegation:
If I use SLAAC and the IPv6 address changes on the client, then dnsdist wouldn't be able to determine the client and would use the wrong DNS server for that client.
Make sure Advanced / Networking / Do not allow PD/Address release is selected. Otherwise your prefix will change. If your prefix is changing, it makes no difference whether you're using SLAAC or DHCPv6. As I mentioned, with SLAAC, you get a consistent address, which is what you point your DNS to. If your prefix still changes, despite that setting, then you may want to consider Unique Local Address, as they won't change unless you change them. You can have both global and ULA addresses on the same interface.
BTW, I've had the same prefix for around 5.5 years. It has survived changing, at different times, both my pfSense computer and modem.
-
@Bob-Dig said in WAN with /64 Delegation:
OT: Maybe you don't want IPv6...
Yeah, well who uses Windows anyway?

-
@JKnott said in WAN with /64 Delegation:
BTW, I've had the same prefix for around 5.5 years.
I have the same prefix since my parents met.
