NAT External ip vs Internal ip (Cisco vs Pfsense)
-
I have moved over to pfsense from a cisco router, most things seem to be working properly.
The problem that I am trying to solve I believe is related to NAT.
I have several public ip addresses coming in from my isp. I have 2 email servers, 3 web servers, and some other internal servers like DB, Backup, etc.
I have 3 networks, WAN,LAN,DMZ(public accessible servers).
I have setup the WAN interface and gateway correctly, LAN is setup on 192.168.1.0 network and DMZ setup on 192.168.0.0. I have setup NAT port forwarding with pure NAT reflection on the WAN interface pointing to the internal servers ip addresses in the DMZ for Web,Mail.
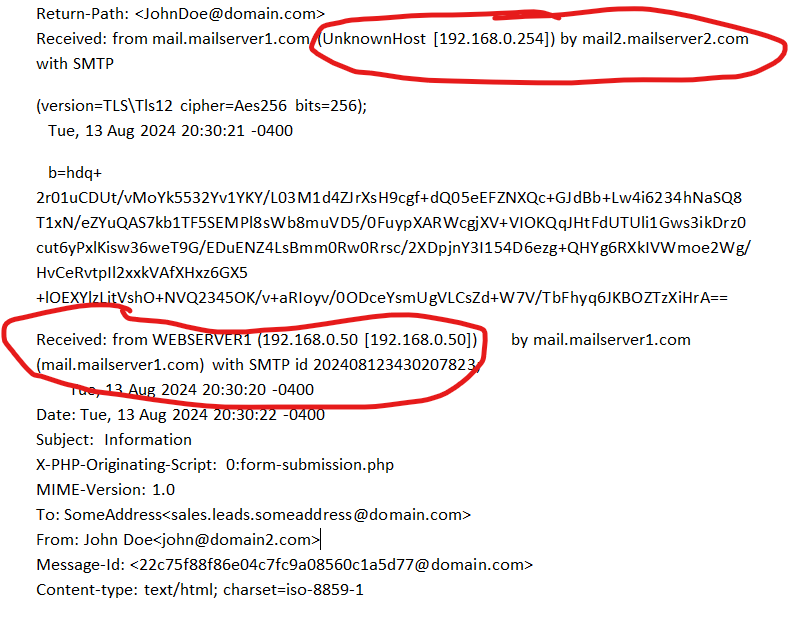
Accessing the Web Servers and Mail Servers from the internet seem to be working fine. I can access them using their public ip addresses. The issue that I have is when mail server1 sends email to mail server2 (both on the same internal DMZ network), the internal ip addresse are used in the email headers which is messing up spf records not to mention revealing internal ip structure. Same thing happens when the web server sends a form, the internal ip address of the web server is used in the email headers.
I have not changed anything in my internal network, just unpluged each network from Cisco router and plugged into pfsense to corresponding network interface.
In my previous setup with the Cisco Router, the existing internal ip structure was the same, NAT was the same. But the IP addresses were showing properly (external ips) in the email headers with the cisco setup in both situations described above.
** Does anyone have any idea on where to look to solve this. I have been trying for a while without success.LAN Interface: 192.168.1.254
DMZ Interface: 192.168.0.254*** EMAIL HEADER ***
********* Below is was my Cisco Configuration *********
interface GigabitEthernet0/0
description CONNECTION TO SERVER SWITCH - DMZ
no ip address
duplex full
speed 1000
no cdp enable
no mop enabled
!
interface GigabitEthernet0/0.100
description SERVER SWITCH 0/24 - DMZ
encapsulation dot1Q 100
ip address 192.168.0.254 255.255.255.0
ip nat inside
ip virtual-reassembly in
!
interface GigabitEthernet0/1
description CONNECTION TO ISP - WAN
no ip address
duplex full
speed 1000
media-type rj45
no cdp enable
no mop enabled
!
interface GigabitEthernet0/1.300
description INTERNET - WAN
encapsulation dot1Q 300
ip address 218.195.172.2 255.255.255.252
ip access-group 135 in
ip nat outside
ip inspect fwout out
ip virtual-reassembly in
no cdp enable
!
interface GigabitEthernet0/2
description CONNECTION TO OFFICE SWITCH - LAN
no ip address
duplex full
speed 1000
no cdp enable
no mop enabled
!
interface GigabitEthernet0/2.200
description OFFICE SWITCH 0/24 - LAN
encapsulation dot1Q 200
ip address 192.168.1.254 255.255.255.0
ip nat inside
ip virtual-reassembly in
ip nat inside source list 5 interface GigabitEthernet0/1.300 overload
ip nat inside source static 192.168.0.30 218.195.172.50 ! Web 1
ip nat inside source static 192.168.0.31 218.195.172.51 ! Web 2
ip nat inside source static 192.168.0.32 218.195.172.52 ! Mail 1
ip nat inside source static 192.168.0.33 218.195.172.53 ! Mail 2
ip nat inside source static 192.168.0.34 218.195.172.54 ! Web 3
ip route 0.0.0.0 0.0.0.0 218.195.172.1 -
I'm going to assume your servers have already been mapped on the NAT.
Here's my two cents beyond that:
Your cisco set up was masking the internal IPs using "overload". This function automatically performs a port address translation and you'll have to manually input that into pfsense if you want to specify the external IP used by your servers when reaching out over the WAN.
You can do this in firewall>NAT>outbound. Select "Manual Outbound NAT rule generation." Create a rule similar to the Cisco setup:
Interface: WAN
Source: 192.168.0.0/24 (DMZ network) or 192.168.1.0/24 (LAN network)
Translation Address: Use the WAN address or specify the public IPs. -
J jrey referenced this topic on