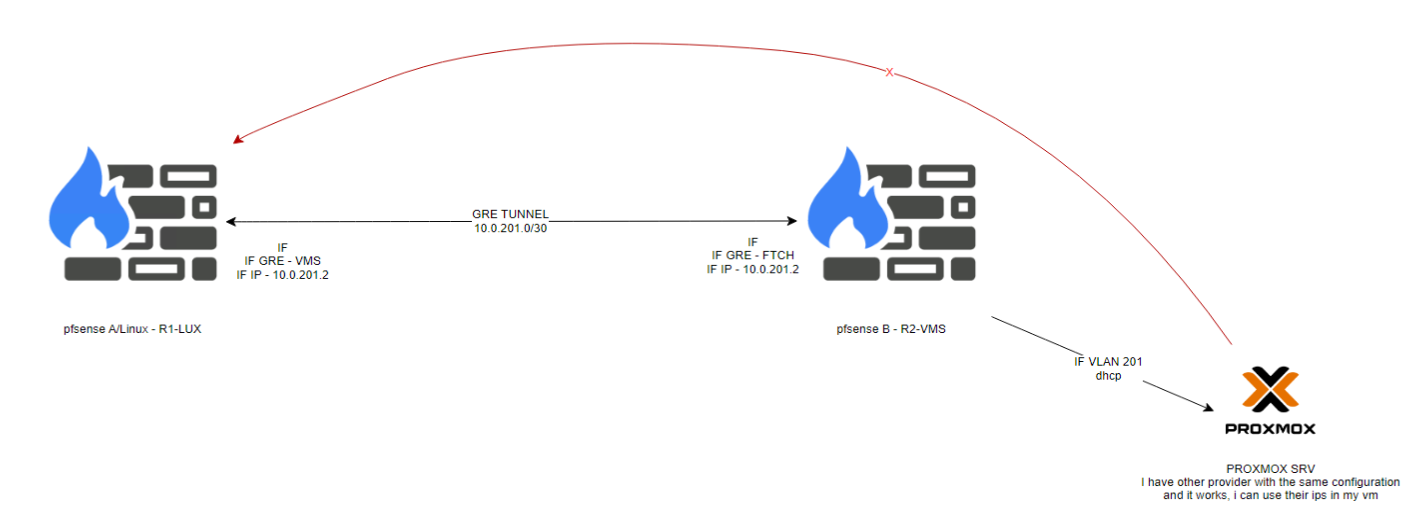
Tunnel GRE from linux server to pfsens
-
@Jsetive said in Tunnel GRE from linux server to pfsens:
You mean the VPS has one IP and the 198.x.x.x IP is additional? Is it in the same subnet?
Yes correct:Mmm, it looks like it's not in the same subnet.
In which case you might be able to route it across the tunnel.
The first test I would do here is to add that IP as a IPAlias VIP in pfSense on localhost and make sure that works as expected when pinged from something external.
-
In which case you might be able to route it across the tunnel.
With iptables, i guess is how it is right now, right ? Im not expert in this matter.
The first test I would do here is to add that IP as a IPAlias VIP in pfSense on localhost and make sure that works as expected when pinged from something external.
Wich interface i use?
I used WAN and VLAN201, it seems still pingable -
Well I suggested adding it on localhost but it should respond from any interface on pfSense. Adding it on VLAN201 should be fine.
Ok so you can ping that from some external address and see pings come back from pfSense? I would want to confirm that in Diag > States.
If so then you should be able to route that IP to an internal VM in pfSense. Just add a static route to it.
-
Well I suggested adding it on localhost but it should respond from any interface on pfSense. Adding it on VLAN201 should be fine.
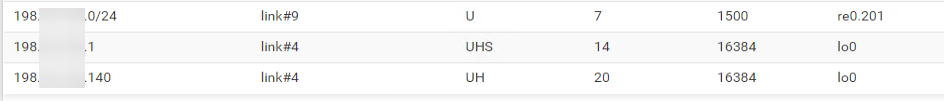
State:
If so then you should be able to route that IP to an internal VM in pfSense. Just add a static route to it.
-
So 198.x.x.140 is the provided IP used in the alias?
You only have that one IP as I understand it? You can't use the full /24 that contains it. You have to use some other subnet there and add the single IP as a VIP on the VM instead of pfSense.
Unless the Provider are routing the full /24 to you. Which seems very unlikely!
-
So 198.x.x.140 is the provided IP used in the alias?
Yes
You only have that one IP as I understand it? You can't use the full /24 that contains it. You have to use some other subnet there and add the single IP as a VIP on the VM instead of pfSense.
Yes
/24 is showned in route because the gateway/ip of interface VLAN 201 is gateway of that ip: 198.x.x.1/24
What is the alternative i have to be able to use the IP directly in VM?
-
@Jsetive said in Tunnel GRE from linux server to pfsens:
the gateway/ip of interface VLAN 201 is gateway of that ip: 198.x.x.1/24
You can't use that it's not your IP address, the provider is likely already using that upstream.
You can only use a full public subnet on VLAN201 if the provider is routing it to you and that is only going to happen if you're paying them for it. Otherwise use a private subnet there and route the public IP to the private IP on the VM. Add the public IP as a VIP on the VM.
-
Sorry if i don't understand, but it seems in the above topics, they are able to use in VM directly:
https://forum.netgate.com/topic/173892/gre-tunnel-to-protect-ip
https://forum.netgate.com/topic/189477/the-curl-command-is-not-working-correctly -
There they are using an IP that is in the same subnet as the VPS public IP. That means they cannot route it and have to bridge the interfaces at both ends to create a single layer 2 segment.
So there they used OpenVPN in TAP mode a bridged it.You don't need to do that because your additional IP is not in the same subnet. You can just route it to the VM directly. But you still need to use a private subnet between pfSense and the VM to route it across.
-
Hello,
How can i create that route to GRE.
If i use VLAN 201 - 10.0.201.0/24
I need to configure the ip as alias and made nat translation ? Just that? -
You can use NAT and put the IPAlias on the firewall.
Or you can put the public IP on the VM directly as a virtual IP and route to it in pfSense. Which is what I thought you are trying to achieve.
-
Or you can put the public IP on the VM directly as a virtual IP and route to it in pfSense. Which is what I thought you are trying to achieve.
You mean configure 198.x.x.x directly in VM and some how route in pfsense? How should i do that?
-
You have to add it to the VM as a virtual / secondary IP. Then add a static route in pfSense to that IP via the private IP on the VM.
-
Hello Again,
Sorry for delay.
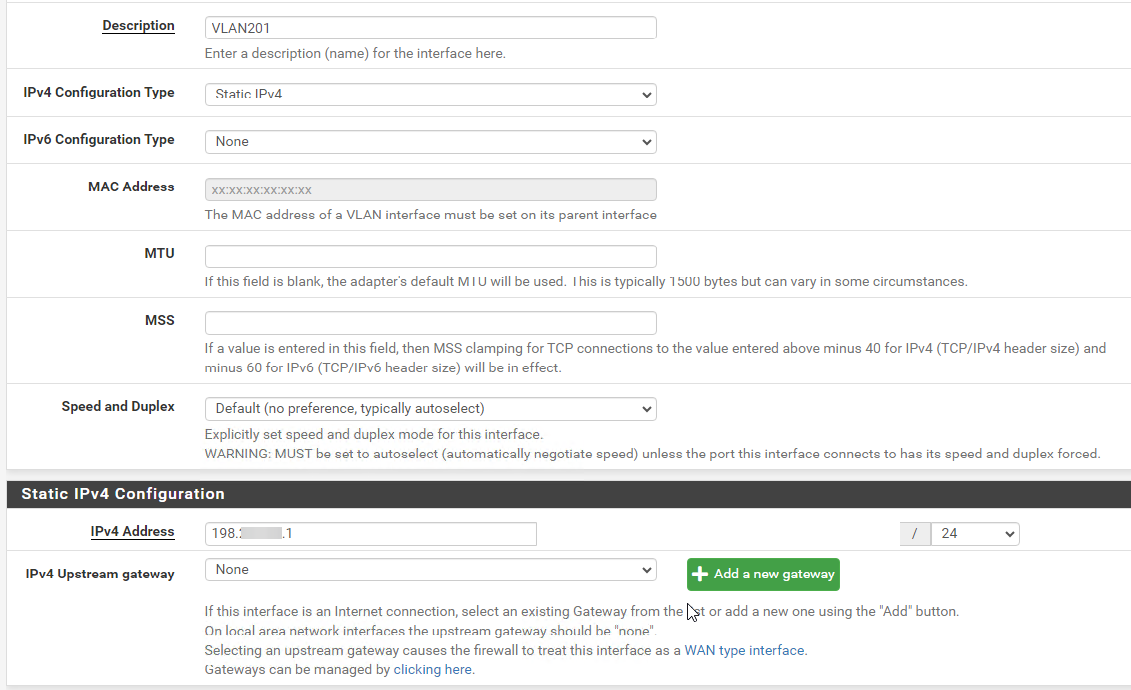
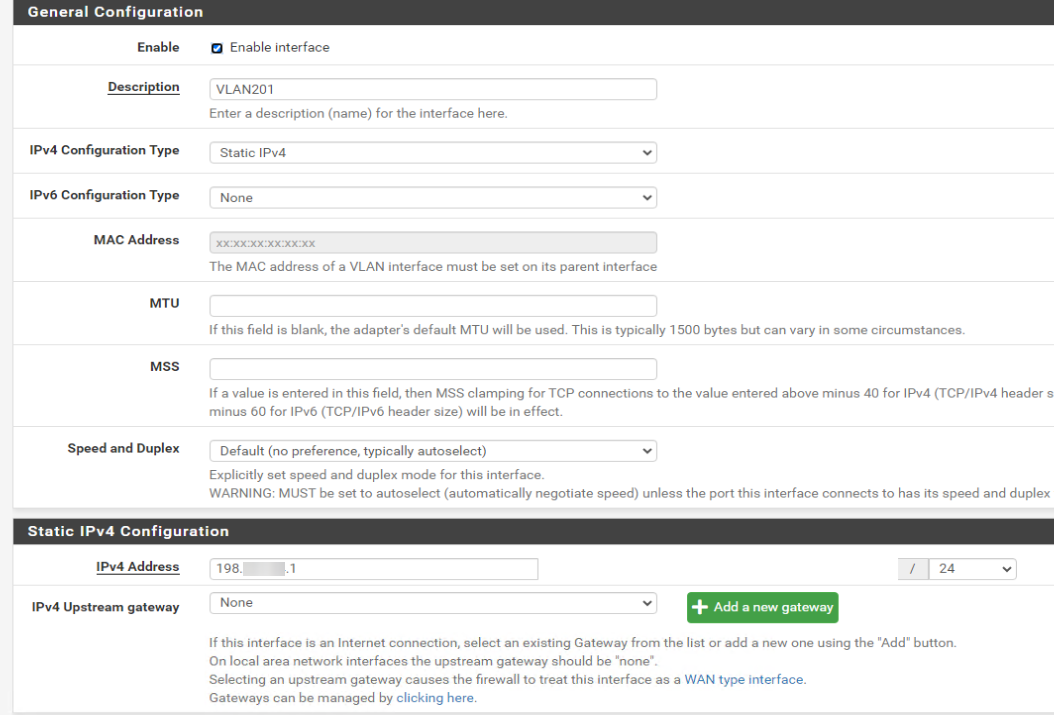
I've mantained the configuration in Linux server, in pfsense i made this configuration:Created a VLAN with gateway so i can reach the gateway localy (?)
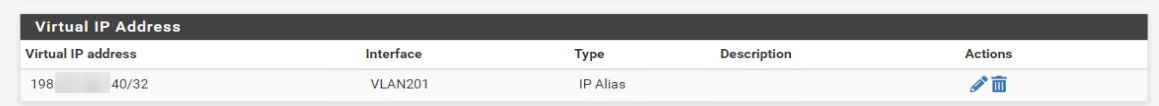
Created a VirtualIP with ip i wan't:
And route it to GRE Interface:
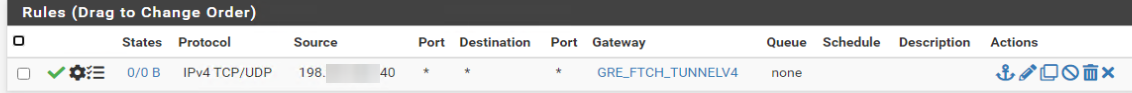
Config in VM:
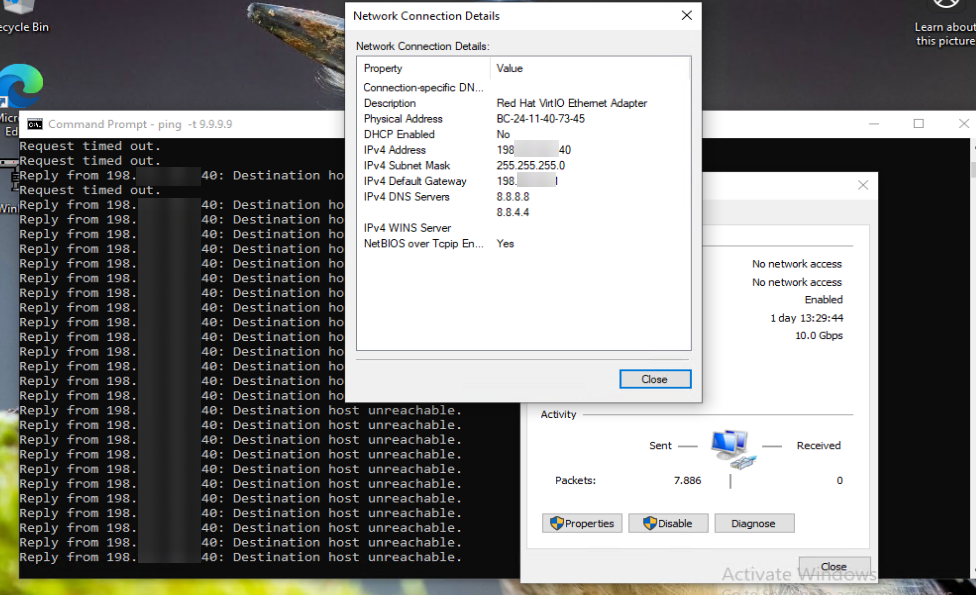
It seems i made something wrong :/
-
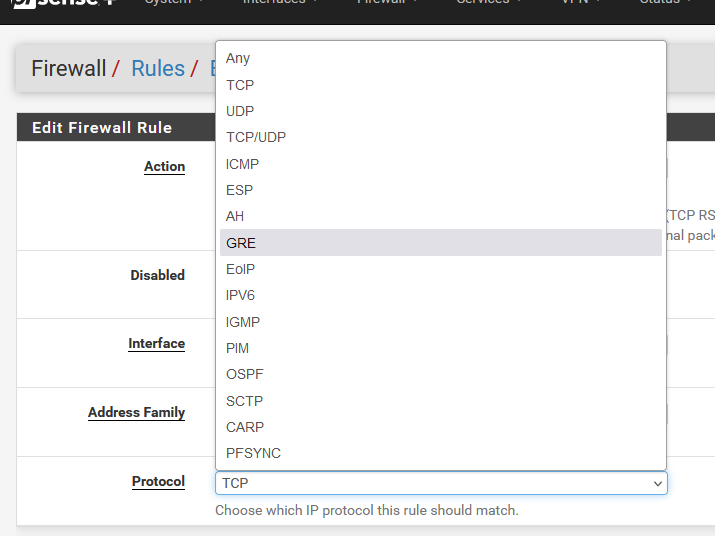
GRE is not TCP neither UDP, not ICMP.
The network connection is done via the GRE protocol (IP protocol number 47. For more information, refer to Wikipedia: List of IP protocol numbers. Since GRE is an IP protocol, it is not based on either TCP or UDP and has no concept of ports. It is an IP protocol by itself.
So, when I see this :
that that rule will never match ;)
-
@Gertjan Thank you for reply, i didn't know that. Already fix the rule.
-
@Jsetive said in Tunnel GRE from linux server to pfsens:
They have one guide
If you have NAT rules on one side of your tunnel, remember to chose 'GRE' as the protocol as well.
-
No you should not have a gateway on the VLAN201 interface directly.
You will need a gateway but you should add it separately and it should be the VM internal private IP.
You need to add a static route to 198.x.x.40 via that gateway.
You should not have a VIP on pfSense. You need to add 198.x.x.40 on the VM dircetly so you can route to it.
The policy route should work OK for outbound traffic.
-
@stephenw10 said in Tunnel GRE from linux server to pfsens:
You will need a gateway but you should add it separately and it should be the VM internal private IP.
Im confuse, you mean, i need to create a "custom" range to this vlan (eg 172.16.201.x/24) and the gatewa on VM will be that?
In vm i configure:
IP 172.16.201.40
Nmask /24
GTW 172.16.201.254Then i create a static route to 198.x.x.40?
-
Yes, that would work. The static route in pfSense would then be to 198.x.x.40 via 172.16.201.40.