Under attack, anything I should do?
-
My home IP address has been under attack for a week. I opened port 443 to use with OpenVPN because it is a port that is not blocked in hotels. Over a week ago, I noticed that this port is being pounded by a range of different source IPs and ports at a rate of about 5 per second. There is no indication that anyone got through the firewall. Out of an abundance of caution I locked down port 443, so all requests are now blocked. However, the rate of attack remains the same. My cable provider does not provide a simple option to change the public IP address. Is there anything I should do other than waiting these attacks out?
Thanks for any advice in advance.
-
-
Does your public IP respond to ICMP pings? If so, figure out how to disable in your ISP kit and/or pfSense
-
Use Shields Up! tool to scan All Service Ports
https://www.grc.com/ -
Use Tailscale MESH VPN, which does not require any open ports and will traverse any level of NAT, including CGNAT.
https://tailscale.com
https://www.netgate.com/blog/tailscale-on-pfsense-software -
Consider this a vauable lesson to NEVER, under any circumstances, open any ports.
-
-
Hotels likely do not block 1194 which is OpenVPN and frequently used by business travelers. That is what I use for WireGuard.
I disagree about not opening ports. That is the whole point of having a good firewall and good services behind it. My web server is getting many hits per second.
-
@elvisimprsntr ICMP pings are blocked. No need to scan with shields up, I know which ports are open and why. Tailscale is worth looking at. I have it installed but am not using it. I am not sure this is a lesson to learn. If openvpn is secure, then all should be good. So perhaps it is just an annoyance.
-
@AndyRH I have certainly stayed at hotels that block 1194. When I ran into this, I installed a second instance of openvpn on port 443. I do have wireguard installed and it's working well. Perhaps that can be the backup for port 1194 in the future.
So far I gather I will be waiting until the attacks settle down. Not sure why the attacker is not giving up after days of hammering a port on which traffic is dropped without a return.
-
@revengineer
I think you are feeling a false sense of exceptionalism. There's nothing in what you've said to make me think that you are specifically getting attacked. Everybody with an IP address is getting scanned constantly by bots looking for weak spots. If the packet rate got high enough to consume most of your bandwidth, then maybe somebody is intentionally trying to DDOS you, but it didn't sound like you are anywhere near that. -
@revengineer said in Under attack, anything I should do?:
different source IPs and ports at a rate of about 5 per second
Call the record books - its the new largest ddos ever recorded ;)
Dude its NOISE.. really yes the internet is noisy..
I don't even log all the noise, only the syn, an a few common udp ports.. I log 3000 last entries, and it only goes back like 5 hours.
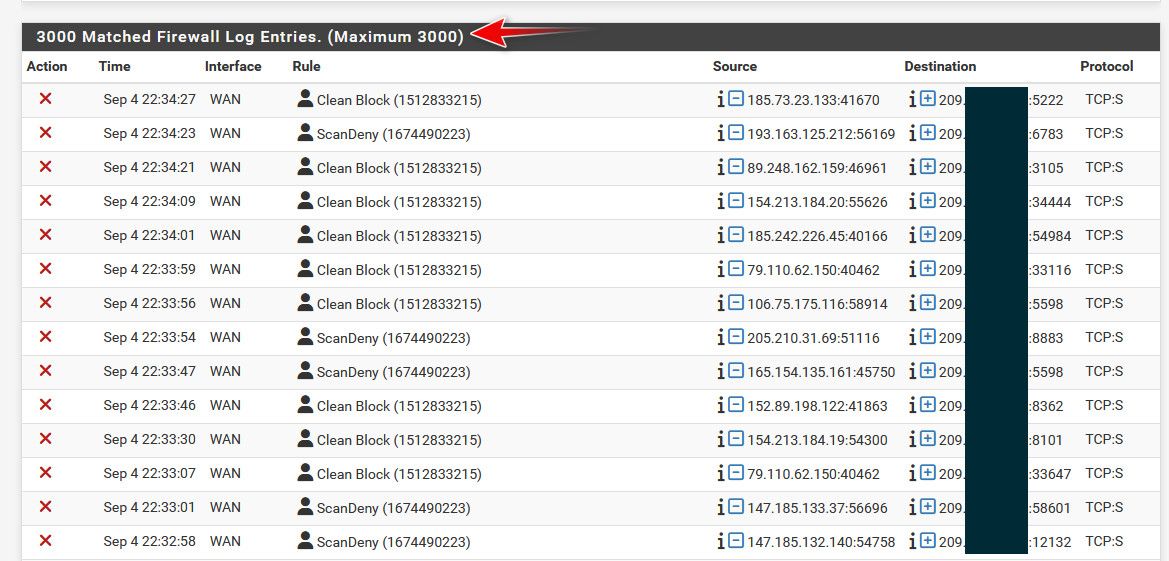
Users that are new to a firewall that actually logs, unlike most soho wifi routers are surprised at the amount of noise there is..
-
@elvisimprsntr said in Under attack, anything I should do?:
Consider this a vauable lesson to NEVER, under any circumstances, open any ports.
If everyone followed this nothing would work.
Email, DNS, NTP, nothing.In fact if noone ever opened any ports the internet would probably be broken.
I think the real lesson is "any port opened has a probability >99% of being scanned by bots"
443 is https, typically leading to a web server, web servers are typically a "good" point of attack.
All the openvpn client configs I've seen typically reference ports 1194 and 443 as fallback. -
@mer said in Under attack, anything I should do?:
If everyone followed this nothing would work.
Email, DNS, NTP, nothing.In fact if noone ever opened any ports the internet would probably be broken.
I have exactly zero (0) manual port forwarding open and I have no issues.
The OP chose to open/use port 443 for OpenVPN, which they saw the results.
-
@elvisimprsntr you understand you are seeing the same hits right.. none of those ports being seen in my logs are open..
Unless your behind a nat, and the internet can not talk to pfsense wan - your seeing the same traffic.
-
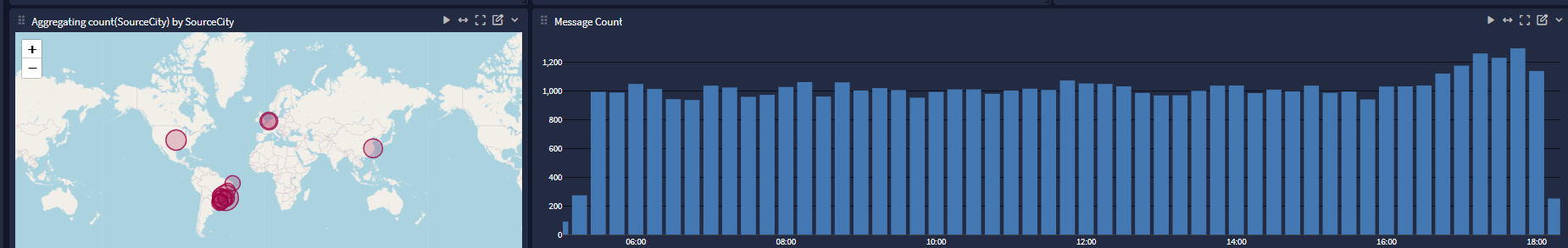
Noise is sometimes an understatement. When a DDOS group gets your IP address and keeps hammering at a single port for 24 hours from Brazil. Port isn't open but they don't care compute, and network is cheap to look for open ports and vulnerability.
-
Yep.
I stopped looking at WAN side logs because there is so much noise that it’s pointless to look at, because there is not a [redacted] thing you can do about it other than make sure there are no manual or UPnP port forwards and keep all your systems updated.
-
@ronv42 what is that about 8k hits in 2 hours.. Works out to what 1 hit per second or so.. Again lets add this to the record books as huge dos attack ;)
-
If this annoys you, you could make an exception for your mobile phone provider only (Source-Address ASN with pfBlocker). Then, if you want to use hotel-wifi, you would only open the port manually to that IP or disable your exception for the time being. John is probably right that this is not enough for a DDoS.
-
@revengineer said in Under attack, anything I should do?:
Out of an abundance of caution I locked down port 443, so all requests are now blocked.
I guess you did this by white listing the IP addresses you allow.
I use an IP alias in pfsense for this which includes the address of my laptop while I'm on the road (via a dynamic domain name client on my laptop).@Bob-Dig said in Under attack, anything I should do?:
you could make an exception for your mobile phone provider only
Yep that can be included in the above alias as well if required.
-
@AndyRH said in Under attack, anything I should do?:
My web server is getting many hits per second
Thanks for the reminder.
Look like my web server's port 80 has an issue : there are none
@AndyRH said in Under attack, anything I should do?:
Hotels likely do not block 1194 which is OpenVPN and frequently used by business travelers
Hotel here, that's what I use pfSense for, with the captive portal

I block just 1 (one) port : any destination, TCP 25. For, imho, obvious reasons.
And as Andy said, the real clients, not the tourists but the professional one, use some kind of VPN. I'm not going to block them as they are good for 75 % of the turnover. -
@revengineer said in Under attack, anything I should do?:
I have certainly stayed at hotels that block 1194.
Cycle through other VPN ports. Some will be open.
80, 443, 20 and 21 will always be scanned frequently. I am sure there are others that are favorites.
For those afraid of the
jungleinternet, check your logs, those popular ports will have been scanned in the last few seconds. -
@Gertjan said in Under attack, anything I should do?:
Hotel here
I have been to hotels where vpn is blocked on say 1194, because they want you to pay for the "special" internet package that allows for it ;)
So it is a thing ;) heheh
Its funny you stay at a budget hotel and you get wifi and breakfast for free, you stay at a higher end place and they charge you for wifi and breakfast ;) hehehe
-
@revengineer said in Under attack, anything I should do?:
Is there anything I should do other than waiting these attacks out?
That's most probably the only option you have.
A DOSS has just one goal : saturating your down-link thus saturating your uplink.
Even if there is a way to 'suck up' all the useless data, your 'pipe' to the net is bandwidth limited, and the goal is : filling it up.
It doesn't matter which port is focused, but an 'open' port will use a lot more 'firewall/router', so if there is one, it will be used, as the DOSser will get more bang for the buck.If a solution exist, it's the one that the ISP can give you :
As you've said : get another IP.
Or an active DOS protection system, ISP based.
So, next time when you switch ISP, make these criteria part of your selection-list.Or, solve the problem with pure 'Kevin style' : as DOS is a question of "who has the biggest", get that symmetrical 10 Gbit ISP connection.
Now, when a DOSser comes around, he has to bring in a lot of DOS power to fill up that pipe. And better : when you are DOSSed now, it will show up at the ISP-dashboard and as the ISP tends to protect that amount bandwidth avaible, they will act.
( and while doing so, they will also terminate your subscription as you're to hot to handle ^^) -
@revengineer said in Under attack, anything I should do?:
My home IP address has been under attack for a week. I opened port 443 to use with OpenVPN because it is a port that is not blocked in hotels. Over a week ago, I noticed that this port is being pounded by a range of different source IPs and ports at a rate of about 5 per second. There is no indication that anyone got through the firewall. Out of an abundance of caution I locked down port 443, so all requests are now blocked. However, the rate of attack remains the same. My cable provider does not provide a simple option to change the public IP address. Is there anything I should do other than waiting these attacks out?
Thanks for any advice in advance.
Opening port 443 to incoming connections on your firewall's WAN interface makes your setup appear to be a web server. As mentioned by others, web servers are favorite targets for all manner of vulnerability searches using various exploit kits. Nefarious folks are always searching for web servers to compromise.
The normal open port for OpenVPN is UDP port 1194. Most vulnerability scanners won't bother trying to get in via port 1194 because they know guessing the correct certificate key is darn near impossible. So, short answer there is that serious hackers usually don't waste their time scanning for an open UDP port 1194. HTTPS (port 443), on the otherhand, is often times a very attractive target as they are looking for unpatched web servers to try and gain access via an exploit kit.
But 5 hits per second is honestly nothing. A true DDoS attack would be thousands of attempts per second.
If I were you, I would reconsider opening port 443 on the WAN. All it would take is a slight configuration mistake on your end of the firewall to make your firewall's web GUI login available on the Internet. I'm sure you would not want that! If port 1194 access is giving you trouble from some locations (as in being blocked by the admin whose network you are currently using), then perhaps Tailscale is a viable workaround ??