Under attack, anything I should do?
-
@stephenw10 said in Under attack, anything I should do?:
Mmm, you should definitely consider limiting the source on the rule allowing that IMO.
yep
@Patch said in Under attack, anything I should do?:
use an IP alias in pfsense for this which includes the address of my laptop while I'm on the road (via a dynamic domain name client on my laptop).
-
@johnpoz STT was an example. Calm down....
-
@dennypage said in Under attack, anything I should do?:
Does your public IP respond to ICMP pings? If so, figure out how to disable in your ISP kit and/or pfSense
@dennypage said in Under attack, anything I should do?:
While many people suppress ICMP echo for IPv4, attempting to imitate a black hole, suppressing echo responses really has no impact on security. Also of note is that suppression of echo response is specifically prohibited with IPv6.
Thank you! This. The whole stick about being invisible or somehow stealth by not answering ICMP is so completely bullshit I don' even know how that got so famous in the first place! TTL and other measures can easily show if there's another hop on the line that is playing dead. Hell even ISPs on dialup lines often have the first hop not responding to anything and you know it's there. Allowing ICMP echo reply is no bad thing or makes you a target. Playing sneaky and stealthy makes you one. Comparable to the nonsense of hiding a WiFi SSID that also adds a whole lot of other problems for other WiFis.
@Bob-Dig said in Under attack, anything I should do?:
Already forgotten that it is OpenVPN behind Port 443?

Seems so
 With that little traffic it should be no problem to re-open the port. I'd throw in to use pfBlockerNG, add the PRI1-3 or even PRI1-5 lists and the "SCANNER" list and silent block drop them on WAN in front of the allow rule for the VPN. That should eliminate quite a bit of that noise one sees on ports like 443/tcp. That will shut up nonsense hosts, scanners like censys or Shodan and stuff so it won't ring the bell that often.
With that little traffic it should be no problem to re-open the port. I'd throw in to use pfBlockerNG, add the PRI1-3 or even PRI1-5 lists and the "SCANNER" list and silent block drop them on WAN in front of the allow rule for the VPN. That should eliminate quite a bit of that noise one sees on ports like 443/tcp. That will shut up nonsense hosts, scanners like censys or Shodan and stuff so it won't ring the bell that often.@revengineer said in Under attack, anything I should do?:
Having used pfSense for a long time, and having monitored my firewall logs, I can tell that the current activity is unusual. I am well accustomed to many opportunistic hits from various IPs htting various ports. But certain block of IPs trying to access a single common port is new. Hence my inquiry.
You should take into consideration that with the whole shebang of AI bullshit out there, the amount of bots and crawlers has gone awry. Working for a company that besides firewalls and network stuff does hosting for a big chunk of our business, we see things like facebooks crawlers, claudebot from openAI and stuff spiking at an all time high and running wild on webservers of our customers. That got large enough we block whole IP ranges now to stop them from crawling as quite a number of them are ignoring stuff like robots.txt to reign in their crawling behavior.
So if you're running on a dynamic IP it's not impossible that this IP was somehow known for a web service beforehand or that some crawlers and bots simply don't care and try to exploit it. Also there were a number of HTTPS/webservice exploits again, so scanner/exploit kits searching for targets in a kind of "wave-like" surge in traffic isn't that unusual. It happens. That's why I'd add pfB IP blocks in front of the VPN rule and be done with it. OpenVPN itself is quite capable of ignoring those BS connection attempts :)
@revengineer said in Under attack, anything I should do?:
I have not stated that I am suffering a DDOS attack. I agree that 5/s is low, and my connections are in no way affected.
Yeah absolutely. Didn't read it as DDOS, but your wrote "under attack" while most of is wouldn't count 5/s on any service as even an attack ourselves but of course YMMV.
@revengineer said in Under attack, anything I should do?:
but I am not sure what the attacker is trying to accomplish.
It doesn't have to be attackers at all! As stated before, there are numerous scanner services like censys, Shodan etc. that will also spike in traffic when new CVEs or exploits are released and they kick off their search for vulnerable systems.
@provels said in Under attack, anything I should do?:
FWIW, I run my OpenVPN on a rando high port and NAT it. But is many moons since I traveled anywhere that offered WiFi over anything more sophisticated than a Netgear router. LOL
Wanted to add to that comment a general recommendation: just run OpenVPN on localhost and udp/tcp 1194 for basic setup. Then add port forwards with an alias and a small set of ports and redirect them to localhost/1194 for either udp/tcp. Done.
You now have the same fallback strategy implemented like the "bigwig" VPNs that spam your ad channels everywhere, like PIA, Nord, etc. They all run on a number of IPs but with various different ports for fallback reasons for when the default 1194/udp/tcp won't work.Normally those are like:
- UDP: 1194, 80, 4569, 5060, 51820
- TCP: 1194, 443, 8443, 7770
Those are quite common for Nord or Proton and other VPN providers to use as alt ports and even in some restrictive hotel environments and with shitty portals I normally get through to home with them.
Otherwise when not wanting to open any port at all, using a VPN with an intermediate (run by yourself or from the VPN provider) like tailscale (or self hosted headscale) or sth. would be another possibility.Cheers :)
-
ASN in pfBlocker still has problems most of the time. But if you have working lists already, you are good.
-
@dennypage said in Under attack, anything I should do?:
Information available here.
And where in pfblocker would I put this token? I am not seeing it in any of the pfblocker settings, I have my maxmind token setup..
But if reading that right, that really has little to do with pulling the info from an ASN for your table of IPs.. But more of to do with pulling this info in real time for asn reporting?
Am I not understanding this correctly? When using ASN in an alias, why should you need to pull this info more than say every 24 hours, they sure are not updating this info on the hour every hour, etc.. Says right in that thread that they only update every 24 hours anyway. And to be honest there normally is not a lot of changes to IPs listed in an ASN...
Per that thread there is also info to 10 downloads a day.. I don't see how that would be an issue.. That is a lot of downloads of the db per day for how they should it should be used.
-
-
@AndyRH said in Under attack, anything I should do?:
Hotels likely do not block 1194 which is OpenVPN and frequently used by business travelers.
While I haven't had a problem using OpenVPN from a hotel, once I moved my local subnet away from what hotel's often use, I know some places such as my local community centre & library block it. If I come across a place that blocks my VPN, I just connect by tetherning to my cell phone.
-
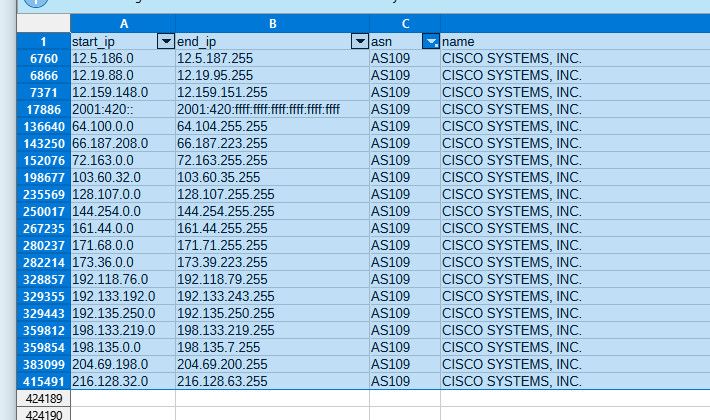
@Bob-Dig thanks... So yeah something is not right.. I just added a test alias with cisco asn AS109, and get nothing, just the placehold added to the file..
But from a look of the prefixes listed https://bgpview.io/asn/109#prefixes-v4
There should be plenty of prefixes in the table.
Where would you put in this token you can get, I got my token.. And just from the gui I can download a db.. And in that db I find prefixes for that AS109 I used for my test..
So why can this not be done in pfblocker?
-
@johnpoz @BBcan177 said in pfblockerNG ASN bgpview trouble:
The current code in pfB contains a User Agent Header which is being blocked en masse by them.
But I don't know anything about a token. Just using the patch again, which alters the User Agent Header worked for me.

-
I have a PR pending approval to switch to IPInfo for ASN data.
But in the short term, you could change the agent string to something else to avoid BGPview blocking you. They don't want to support open source and I can't even get them to update their API usage policy.
pfBlockerNG code
FILE: /usr/local/pkg/pfblockerng.shLINE 761
-
@Bob-Dig
Patience - the fix is coming as mentioned in the thread you referenced. (and now here) It is looking really good at this point and good riddance to bpgview.
watch the -devel branch for the update. No ETA, but soon-ish as @BBcan177 mentions above the PR is pending.
PS: you won't need the patch, and it won't apply so after the update releases at which time you can delete it.
-
@Bob-Dig said in Under attack, anything I should do?:
Just using the patch again
what patch is this? I don't see anything related in the patches? From what @BBcan177 mentioned, sounds like would just manually edit that file. Is there some patch to auto do that?
edit
Oh your talking about the patch shown in this threadhttps://www.reddit.com/r/pfBlockerNG/comments/1ey2sza/update_on_asn_issues_with_bgpviewio/
edit2:
well I tried editing the ua string, and still not loading that as109 I setup as test. -
I had provided the fix as a "patch" file well over a year ago - the last time bgpview did this actually.
Original version of the patch I created should be on this forum somewhere - I never provided it to reddit- it changed a couple of other things as well.
Like not providing your device's NDI to bgp (they don't need it, and I viewed it as an issue) especially in light of the fact that Netgate gives you the option to not even send it to them in the URL and they have made such a "fuss" about NDI and registration being a problem why send it where it is not required.
I'm no longer providing the patch directly with various reasons mentioned in the other thread. and now with new version that doesn't need it
if your downloads are not working.
a) Just wait for the release,
b) find the patch,
c) or change the line as referenced.I recommend a) for good reason at this point
- it changed a couple of other things as well.
-
@johnpoz said in Under attack, anything I should do?:
well I tried editing the ua string, and still not loading that as109 I setup as test.
let me try this for you - standby
-
@jrey said in Under attack, anything I should do?:
c) or change the line as referenced.
I did change the line.. does it need a specific format or something?
ua="pfSense/pfBlockerNG cURL download agent-"
to
ua="different-"
And that doesn't seem to be working.. My current aliases that have table entries, they might be a bit out of date it seems.. I can for sure just wait til the new version comes out, etc. and already have my ipinfo token ;)
But now just curious to get it working if all you would have to do is change the ua..
-
@jrey said in Under attack, anything I should do?:
let me try this for you - standby
Also interested in a how-to.
-
@johnpoz said in Under attack, anything I should do?:
pfSense/pfBlockerNG
this is what they are currently blocking on.. change that
the curl that actually pulls it looks like this: (I log it in the pfblockerng.log (cause I like logging)
/usr/local/bin/curl -A "pfSense/pfBNG cURL download agent-60835222024" -sS1 https://api.bgpview.io/asn/109/prefixes
it send the output to a tmp file as part of what gets called.
Works fine here{"status":"ok","status_message":"Query was successful","data":{"ipv4_prefixes":[{"prefix":"12.5.186.0\/23","ip":"12.5.186.0","cidr":23,"roa_status":"None","name":"CISCO-SY729-186","description":"CISCO SYSTEMS","country_code":"US","parent":{"prefix":"12. -
@johnpoz delete the ASN file. So if the asn is a block it's in the "deny" folder. You can do that in the Log tab to delete the file. Once that file is deleted run a Force update to get the new update
-
 S stephenw10 forked this topic on
S stephenw10 forked this topic on
-
@jrey said in Under attack, anything I should do?:
this is what they are currently blocking on.. change that
I did, I changed the whole ua variable to be "different-"
@BBcan177 should a force reload do that.. not using any asn in any pfblocker rules - just an native alias and doesn't seem to want to pull any info for the AS109 test alias I created.
But I do see a AS109 file, let me try deleting that file. And then running a forced update.
edit: ok I deleted the AS109_v4.tx file in /var/db/pfblockerng/native
But still show this error
[ AS109_v4 ] Reload . completed ..
Empty file, Adding '127.1.7.7' to avoid download failure. -
@johnpoz no a Force Reload uses the existing downloaded files and makes any changes that you might have made with the settings. New downloads only occur if the downloaded file is missing (which is why I said to delete it) or at the Cron Frequency setting that you set.