Local VPN won't connect when on LAN port?
-
Everything was running smoothly until I started setting up Suricata. A few days ago I set up Suricata on Inline IPS Mode onto my LAN port. Ever since two days ago, the LAN port doesn't seem to have internet access so I disabled Suricata on it. It now has internet access but when I try to enable a commercial VPN on my phone, it doesn't connect -- the VPN will connect on OPT2 port or mobile data though. Several days ago, I still had internet access on LAN with Suricata enabled but just about every day, a new issue comes up now.
Additional details:
- Hardware: Protectli FW4B - 4 Port Intel J3160 + Samsung DDR3L SO-DIMM Memory Module - 8GB
- pfSense version: 2.7.2
- I don't know how to check the version of the Suricata package, but my rule set was has been getting updated daily.
- Network topology: IPS modem > Protectli vault > LAN port to Netgear router / OPT2 port to IPS router.
- Suricata is set to Inline IPS Mode.
1. How can I get Suricata to work?
2. How come local VPNs won't connect on the LAN port, even if Suricata is disabled?Any help is much appreciated!
-
You may need to clear the snort2c table. You might still have blocks in place.
Otherwise check the states opened or firewall blocks when you try to connect.
Steve
-
@magician-balmy-stainable said in Local VPN won't connect when on LAN port?:
How can I get Suricata to work?
If you are new to administering an IDS/IPS, then you should not enable blocking when first installing and configuring. You need to run the package in non-blocking mode (or ALERT only) for several days or even weeks to see what types of alerts are being triggered by traffic in and out of your network.
You need to regularly monitor the ALERTS tab during this period and investigate each alert received to determine if it is a false positive (you can have lots of false positives depending on what rules you have chosen to enable). You will want to disable the individual rules that generate excess false positives. You will also likely need to fine-tune the rule set by enabling suppression rules (also known as thresholding in the official Suricata docs).
You cannot simply install an IDS/IPS, enable a bunch of rules, and call it "done". That will likely lead to exactly the situation you were facing -- nuisance blocks and a dysfunctional network. An IDS/IPS is a very technically complex tool to configure properly. It requires quite a bit of detailed networking and even programming knowledge to understand the potential vulnerabilities in your particular network and how to use the IDS/IPS to mitigate them.
-
@stephenw10 Hi Steve, I've checked the snort2c table (Diagnostics > Tables > snort2c) but it states "No entries exist in this table."
When I check Services > Suricata > Alerts, there's a long list of GID:SID 1:2231001 Description "SURICATA QUIC error on data" up until 09/09/2024. Nothing is highlighted in red so no blocks seem to have occurred.
The Blocks tab under Suricata indicates that there are currently hi guitars being blocked by Suricata.
-
@bmeeks Fair enough. I did review my alerts briefly but after looking up the ones I got, I didn't see anything notable so I enabled blocking. At this point, what can I do to get the LAN port back online and Suricata working?
-
First add it in non-blocking mode and make sure you can still pass traffic there. This could just be coincidental and unrelated to Suricata.
-
@stephenw10 I've stopped Suricata and disabled blocking as well but the port still doesn't appear to have internet access. I've rebooted the modem, pfSense and router but to no avail. The LAN port used to have internet access prior to setting up Suricata.
-
@magician-balmy-stainable said in Local VPN won't connect when on LAN port?:
@stephenw10 I've stopped Suricata and disabled blocking as well but the port still doesn't appear to have internet access. I've rebooted the modem, pfSense and router but to no avail. The LAN port used to have internet access prior to setting up Suricata.
If the Suricata daemon is truly stopped, then it cannot have any impact on the interface. The only thing it does is switch the interface over to netmap mode when Inline IPS Mode is active. But it only does that when Suricata is running.
To be 100% sure that you do not have a zombie Suricata process running, disable Suricata on all interfaces by clearing the Enable checkbox on the INTERFACE SETTINGS tab. Save that change.
Reboot the box to kill any potential zombie Suricata instance. Suricata then will be 100% for sure out of the picture. If you still do not have LAN access, then something else is in play unrelated to the Suricata package.
-
@bmeeks I tried disabling Suricata and rebooting the firewall multiple times but when it comes back online Suricata is reenabled. Disabling it again still doesn't help though. If anything, when I connect the Ethernet cable to the LAN port now, the computer doesn't even recognize that it is connected at all (it used to indicate connected but no internet access).
I've also tried to leave Suricata's interface as unassigned but it indicates that it must be assigned in inline mode. I no longer see the option to change it to legacy mode.
How can I try changing it back to legacy mode?
If not Suricata, what else could be causing the connectivity issue to the LAN port or how can I fix it? -
@magician-balmy-stainable said in Local VPN won't connect when on LAN port?:
@bmeeks I tried disabling Suricata and rebooting the firewall multiple times but when it comes back online Suricata is reenabled. Disabling it again still doesn't help though. If anything, when I connect the Ethernet cable to the LAN port now, the computer doesn't even recognize that it is connected at all (it used to indicate connected but no internet access).
None of this makes sense to me. Please post some screenshots showing the INTERFACE SETTINGS tab for your LAN's Suriata interface.
If you uncheck the Enable checkbox and save that edit, then Suricata should not restart on a reboot. The status of that parameter is checked by all of the Suriata "start up" code, and if not checked Suricata is not started on the interface. See the checkbox I've highlighted in red below:
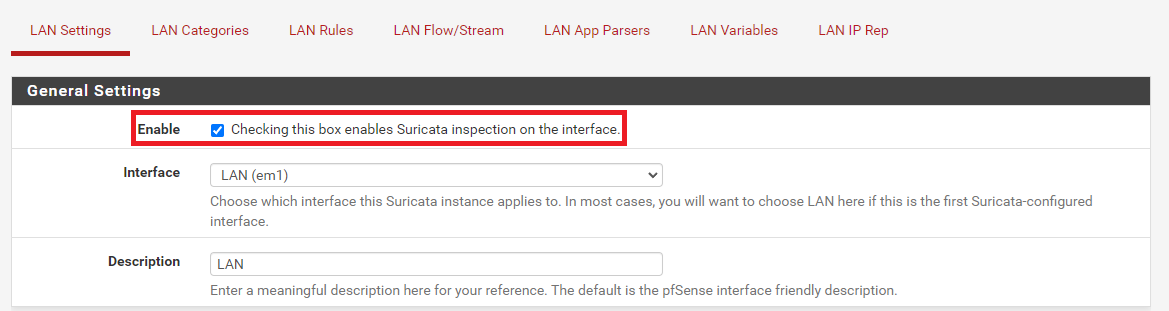
Clearing the checkbox highlighted above disables Suricata on the interface, and it will stop any running instance and prevent any future ones from starting if that checkbox is not checked.
@magician-balmy-stainable said in Local VPN won't connect when on LAN port?:
I've also tried to leave Suricata's interface as unassigned but it indicates that it must be assigned in inline mode.
If you meant you were trying to change value in the Interface drop-down, then that is not the correct method for disabling an instance. To disable Suricata on an interface, you clear the checkbox highlighted in the image above.
@magician-balmy-stainable said in Local VPN won't connect when on LAN port?:
How can I try changing it back to legacy mode? I no longer see the option to change it to legacy mode.
You can simply scroll down the INTERFACE SETTINGS tab page and clear the checkbox for Block Offenders and save the edit. That will turn off blocking completely.
In the same section of the page you can also change the drop-down selector to Legacy Mode blocking if desired. See the image below where I have highlighted the blocking mode drop-down selector. Simply change the setting to "Legacy Mode" and save the edit, then restart Suricata if desired:
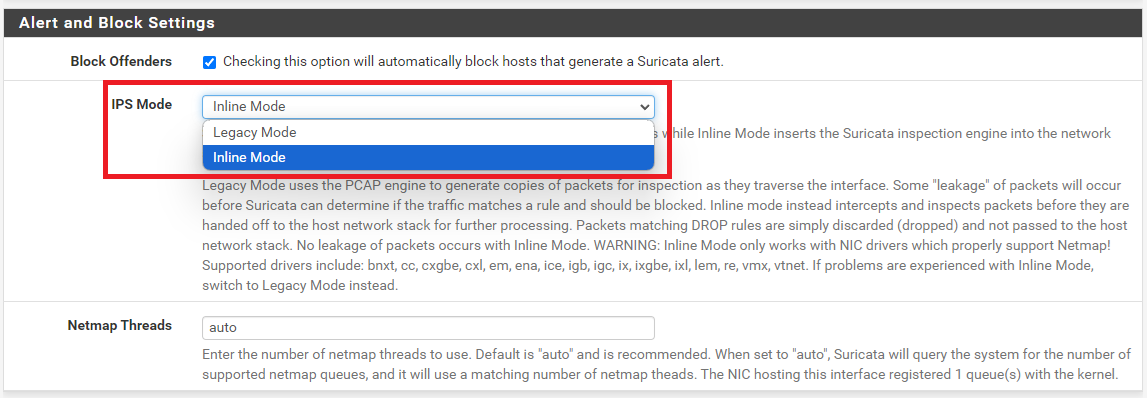
-
@bmeeks I was previously stopping Suricata from the Interface Settings Overview but now I understand how to disable it. Here's the screen capture (and yes, I saved after disabling).
After disabling, I rebooted the firewall and Suricata remains disabled but still no Internet access. It seems like Suricata may no longer be the issue. Do you know what might've changed on this interface or maybe it would be simpler to somehow reset it to regain Internet access?
-
You need to have:
Valid, non-conflicting, subnets on WAN and LAN.
A valid default route/gateway.
Outbound NAT between LAN and WAN. That's usually automatic as long as WAN has a gateway defined.
Firewall rules to pass the traffic.
-
@magician-balmy-stainable said in Local VPN won't connect when on LAN port?:
I was previously stopping Suricata from the Interface Settings Overview but now I understand how to disable it.
Using the Start/Stop/Restart icons on the INTERFACES tab only impacts any current sessions. Once you reboot, there is a shell script in
/usr/local/etc/rc.d/that automatically starts Suricata on any interface where it is enabled. Since you were only stopping the currently running instance and not disabling the instance, the shell script was starting it up normally upon reboot.@magician-balmy-stainable said in Local VPN won't connect when on LAN port?:
It seems like Suricata may no longer be the issue.
I'm not convinced Suricata was ever your issue. I think you have a configuration issue. It's possibly something like @stephenw10 mentioned where you might have overlapping IP subnets or some kind of rouge gateway set up so replies from your LAN interface are directed someplace other than the network where you are attempting to access the firewall GUI.