pfSense Exit Node Direct Connections
-
I have my pfSense box configured as an exit node to replace the mobile IPsec configuration I was using before. There are no Tailscale clients inside my local network. I have several mobile devices that need to connect to the Tailscale exit node when they are away from home.
Everything is working except I can only get direct connections when the mobile devices are on the cellular network. Once they are at a workplace and behind another router they stay stuck in relay mode.
It seems like all the information I find is related to setting up pfSense to make sure that Tailscale clients behind pfSense are able to use NAT-PMP or static NAT rules in order to facilitate direct connections. Are there any rules that need to be setup to make it easier for remote clients to create direct connections to an exit node running directly on pfSense?
-
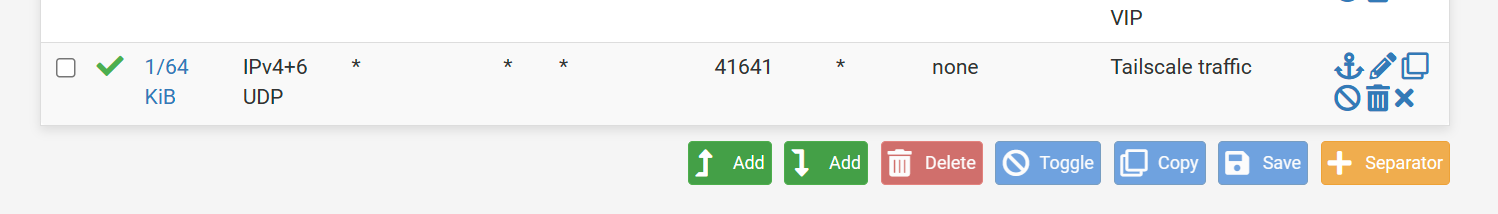
After a crazy amount of web searching, I ran across this blog: https://blog.pilif.me/2022/07/28/tailscale-on-pfsense/
Creating the WAN rule to allow traffic to port 41641 has allowed all the machines that were previously relayed 100% of the time to connect directly.
If anyone sees anything inherently dangerous about this rule, please let me know. Otherwise, hopefully this will help someone else to have more direct connections to their pfSense exit node / subnet router.
-
@cwagz Came to say thank you this worked a treat!
All the available guides talk about NAT outbound rules (but I presume that is for older versions). A simple input of this wan rule and immediately I can have a direct connection to my network over cellular

-
Same here. Glad I found this!
EDIT: I think the only thing I would say to clean up the rule in this scenario is to have the destination be the WAN address? We are using the pfSense as an exit node itself so it doesn't need to pass 41641 through to the LAN as well.
If you're accessing anything behind the router it will just route it as normal.
This is the same for a WireGuard road warrior setup. -
@chickendog Perchance are you using pfSense as an exit node for other clients from another pfSense? I cannot figure out how to route particular clients from site A out to site B as an exit node.
-
@bearach Sorry no I am not. My clients to my pfSense is my phone and a couple laptops that connect to various public/office networks while I'm away from home.
-
@bearach I don't think it's possible. You can't set the Tailscale package to use an exit node.
See this for a hacky method someone came up with, maybe see if that could work for you.
https://forum.netgate.com/topic/175712/use-other-tailscale-exit-nodes/5 -
@chickendog I've been looking at this for a while and I believe that is indeed the case. Thanks for confirming.