Why is the FW responding?
-
I was doing a little test for a friend about how much traffic is hitting 32400. I did a packet capture on pfSense and was surprised that I was seeing responses to 32400 even though that port is not open. Is this normal?
In the log I cleverly hid my IP...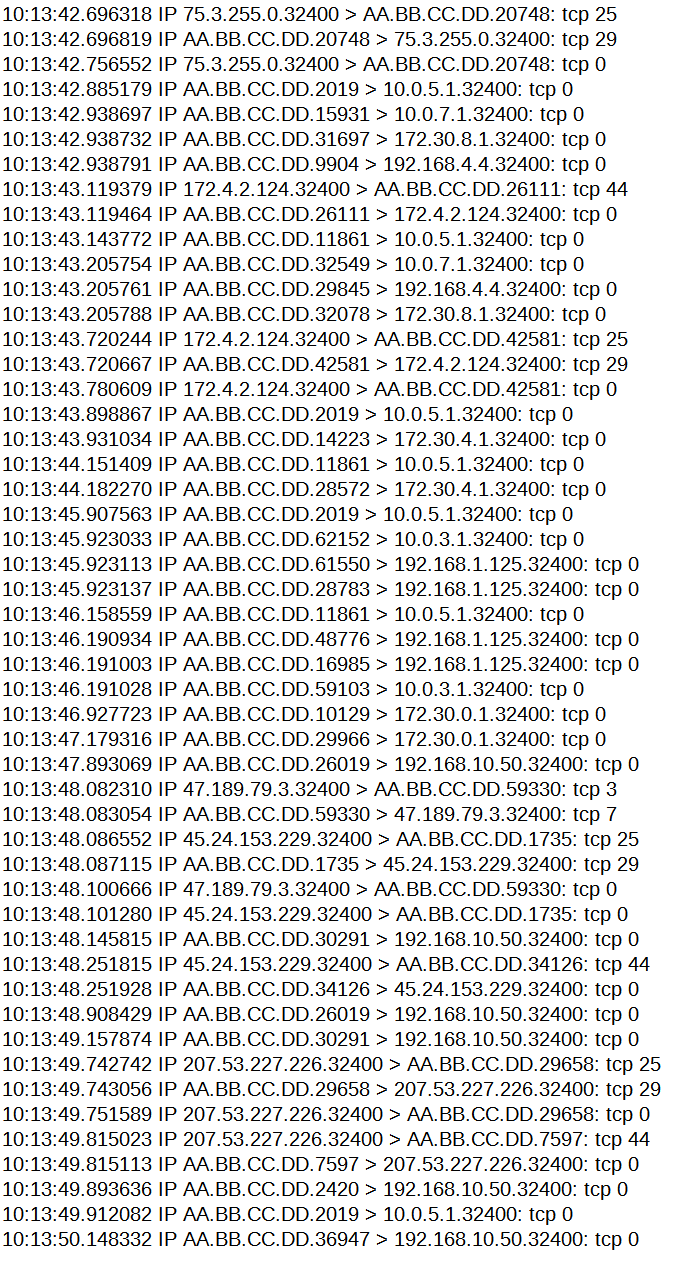 code_text ```10:13:42.696318 IP 75.3.255.0.32400 > AA.BB.CC.DD.20748: tcp 25 10:13:42.696819 IP AA.BB.CC.DD.20748 > 75.3.255.0.32400: tcp 29 10:13:42.756552 IP 75.3.255.0.32400 > AA.BB.CC.DD.20748: tcp 0 10:13:42.885179 IP AA.BB.CC.DD.2019 > 10.0.5.1.32400: tcp 0 10:13:42.938697 IP AA.BB.CC.DD.15931 > 10.0.7.1.32400: tcp 0 10:13:42.938732 IP AA.BB.CC.DD.31697 > 172.30.8.1.32400: tcp 0 10:13:42.938791 IP AA.BB.CC.DD.9904 > 192.168.4.4.32400: tcp 0 10:13:43.119379 IP 172.4.2.124.32400 > AA.BB.CC.DD.26111: tcp 44 10:13:43.119464 IP AA.BB.CC.DD.26111 > 172.4.2.124.32400: tcp 0 10:13:43.143772 IP AA.BB.CC.DD.11861 > 10.0.5.1.32400: tcp 0 10:13:43.205754 IP AA.BB.CC.DD.32549 > 10.0.7.1.32400: tcp 0 10:13:43.205761 IP AA.BB.CC.DD.29845 > 192.168.4.4.32400: tcp 0 10:13:43.205788 IP AA.BB.CC.DD.32078 > 172.30.8.1.32400: tcp 0 10:13:43.720244 IP 172.4.2.124.32400 > AA.BB.CC.DD.42581: tcp 25 10:13:43.720667 IP AA.BB.CC.DD.42581 > 172.4.2.124.32400: tcp 29 10:13:43.780609 IP 172.4.2.124.32400 > AA.BB.CC.DD.42581: tcp 0 10:13:43.898867 IP AA.BB.CC.DD.2019 > 10.0.5.1.32400: tcp 0 10:13:43.931034 IP AA.BB.CC.DD.14223 > 172.30.4.1.32400: tcp 0 10:13:44.151409 IP AA.BB.CC.DD.11861 > 10.0.5.1.32400: tcp 0 10:13:44.182270 IP AA.BB.CC.DD.28572 > 172.30.4.1.32400: tcp 0 10:13:45.907563 IP AA.BB.CC.DD.2019 > 10.0.5.1.32400: tcp 0 10:13:45.923033 IP AA.BB.CC.DD.62152 > 10.0.3.1.32400: tcp 0 10:13:45.923113 IP AA.BB.CC.DD.61550 > 192.168.1.125.32400: tcp 0 10:13:45.923137 IP AA.BB.CC.DD.28783 > 192.168.1.125.32400: tcp 0 10:13:46.158559 IP AA.BB.CC.DD.11861 > 10.0.5.1.32400: tcp 0 10:13:46.190934 IP AA.BB.CC.DD.48776 > 192.168.1.125.32400: tcp 0 10:13:46.191003 IP AA.BB.CC.DD.16985 > 192.168.1.125.32400: tcp 0 10:13:46.191028 IP AA.BB.CC.DD.59103 > 10.0.3.1.32400: tcp 0 10:13:46.927723 IP AA.BB.CC.DD.10129 > 172.30.0.1.32400: tcp 0 10:13:47.179316 IP AA.BB.CC.DD.29966 > 172.30.0.1.32400: tcp 0 10:13:47.893069 IP AA.BB.CC.DD.26019 > 192.168.10.50.32400: tcp 0 10:13:48.082310 IP 47.189.79.3.32400 > AA.BB.CC.DD.59330: tcp 3 10:13:48.083054 IP AA.BB.CC.DD.59330 > 47.189.79.3.32400: tcp 7 10:13:48.086552 IP 45.24.153.229.32400 > AA.BB.CC.DD.1735: tcp 25 10:13:48.087115 IP AA.BB.CC.DD.1735 > 45.24.153.229.32400: tcp 29 10:13:48.100666 IP 47.189.79.3.32400 > AA.BB.CC.DD.59330: tcp 0 10:13:48.101280 IP 45.24.153.229.32400 > AA.BB.CC.DD.1735: tcp 0 10:13:48.145815 IP AA.BB.CC.DD.30291 > 192.168.10.50.32400: tcp 0 10:13:48.251815 IP 45.24.153.229.32400 > AA.BB.CC.DD.34126: tcp 44 10:13:48.251928 IP AA.BB.CC.DD.34126 > 45.24.153.229.32400: tcp 0 10:13:48.908429 IP AA.BB.CC.DD.26019 > 192.168.10.50.32400: tcp 0 10:13:49.157874 IP AA.BB.CC.DD.30291 > 192.168.10.50.32400: tcp 0 10:13:49.742742 IP 207.53.227.226.32400 > AA.BB.CC.DD.29658: tcp 25 10:13:49.743056 IP AA.BB.CC.DD.29658 > 207.53.227.226.32400: tcp 29 10:13:49.751589 IP 207.53.227.226.32400 > AA.BB.CC.DD.29658: tcp 0 10:13:49.815023 IP 207.53.227.226.32400 > AA.BB.CC.DD.7597: tcp 44 10:13:49.815113 IP AA.BB.CC.DD.7597 > 207.53.227.226.32400: tcp 0 10:13:49.893636 IP AA.BB.CC.DD.2420 > 192.168.10.50.32400: tcp 0 10:13:49.912082 IP AA.BB.CC.DD.2019 > 10.0.5.1.32400: tcp 0 10:13:50.148332 IP AA.BB.CC.DD.36947 > 192.168.10.50.32400: tcp 0 -
Check the states for port 32400 while that's happening.
That could just be something behind pfSense opening a connection to that port externally.
Steve
-
I should have known to look there.
There is an amazing number of connections outgoing that are explainable.Thanks for the quick response and the point in the right direction.
-
@AndyRH 32400 is the plex port btw.
But sure it could be random luck that is a port being used as source while something(s) talk to outside ports.
But those other ports look pretty random, so those seem like source ports.
You have stuff talking to plex servers your buddies are running or something.. 2 of those IPs are
lightspeed.rcsntx.sbcglobal.net.
-
@johnpoz The state table had a number of internal computers talking to other Plex servers. My last server change left Plex on another port.
-
@AndyRH said in Why is the FW responding?:
The state table had a number of internal computers talking to other Plex servers.
yup that sounds right from what it looks like.. So you don't want your devices talking to plex?
-
@johnpoz said in Why is the FW responding?:
So you don't want your devices talking to plex?
No, a friend noticed that he was getting lots of hack attempts against his Plex server and wondered how many I was getting. Because mine is on a different port I figured a pcap on the wan for 32400 would tell me more. And it did. Really just looking and comparing.
-
@AndyRH hack attempts??
Sure wasn't just his users or plex checking its available remote?
What are some of the IPs he thinks are attacking him? Could be known scanners, strechoid likes to scan for 32400.. I just block all those known scanner Ips. And like you I don't run plex on 32400 external, I use a different port. And I only allow US ips as well. And belgium currently since I have family living there at the moment.
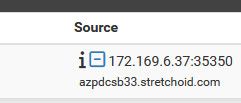
Here is the only hit I currently see in my firewall to 32400
Now I if I just look IPs I block in my scan deny list, see quite a lot of hits, but they are to all sorts of ports
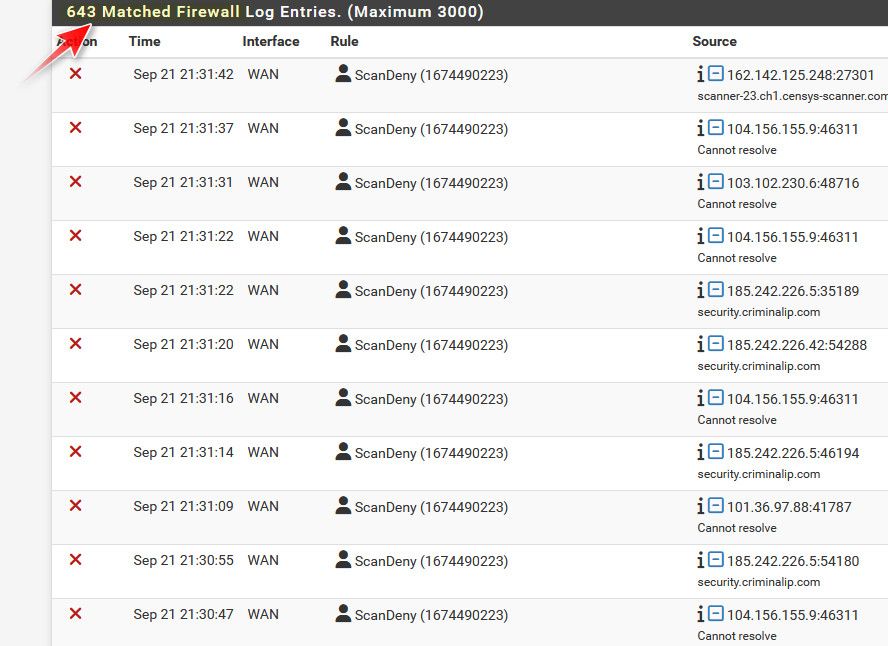
-
643 matched hits in your firewall, your an popular man, I only had 67 hits from scanners

I don't know what you have been doing to piss them off, hehe -
@MoonKnight you sure you have identified all the different scanners as scanners?
-
@johnpoz
I believe so, maybe you have lot more. Like to share?
I do have all of them from the "Feeds" in pfBlocker -
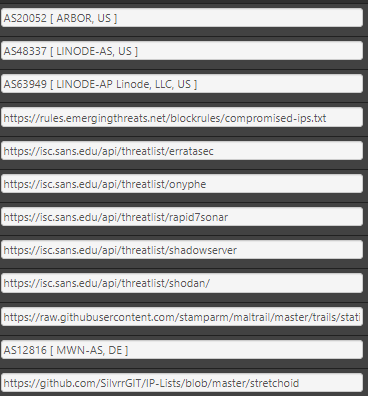
@MoonKnight this is all the IPs currently in my scandeny table
-
Wow I only had 8K ips in my lists. Can I borrow your list? :)
You don't have the IPv4 source definitions ? -
@MoonKnight this is what I pull from.
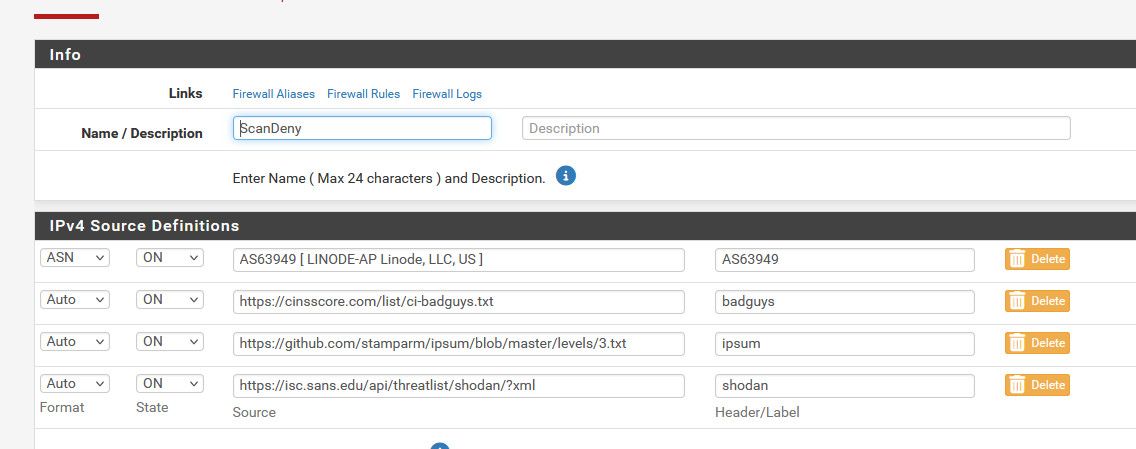
But then I have a whole bunch of IPs in custom, not exactly sure where I pulled them all from.. So figured it might be easier to just dump the table that gets created.
-
@johnpoz
Thanks, this is the list i'm using. Am going to add yours too :)