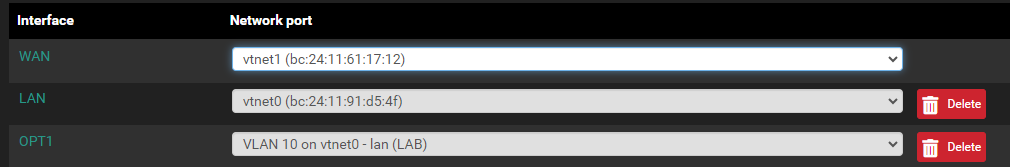
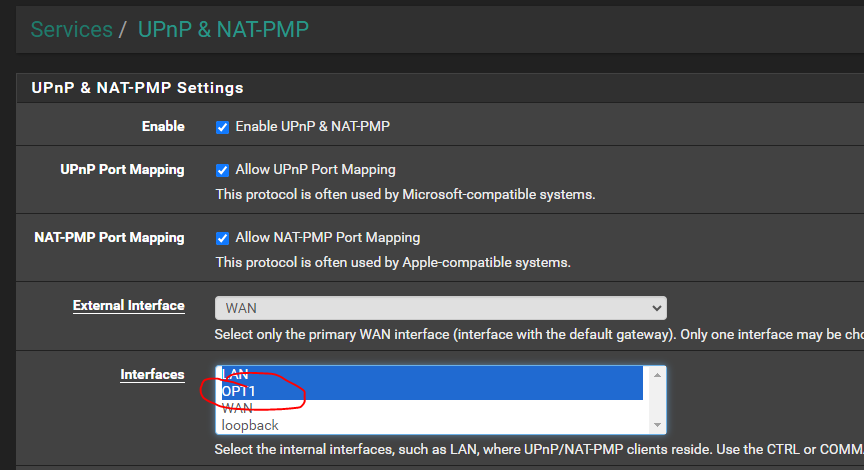
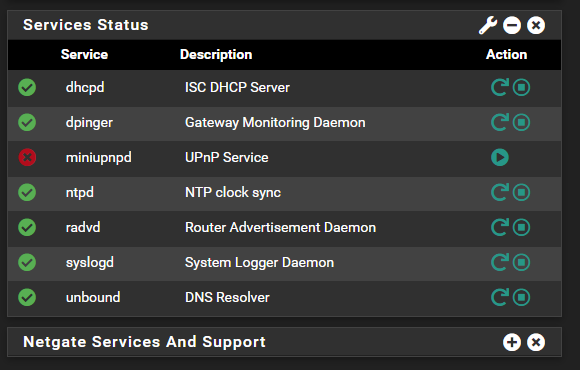
UPnP and VLANs
-
You need to change the subnet on that VLAN to something in a private range. That would mean renumbering everything using that interface, yes.
-
That is gonna be fun - Domain Controllers hate to have their IP changed.
-
I mean if you actually own that subnet then you can just route to it and UPnP becomes unnecessary. But.......

-
Own it? I own it on my home (inside my firewall) network. LOL
I am doing this with the lab domain stuff, because at some point I want to possibly put my WiFi on its own segment (for SmartHome stuff) - seeing how people are persuading me not to use the pfSense box as a WiFi controller AP/router, etc.
-
@bearhntr if you want something that sticks out then use one of the other rfc1918 address schemes from your other networks use 192.168 on your other networks and 10.x.x on the other..
10.20.30.x would standout I would think ;)
Pulling public space out your u know what and using internally - while technically possible, it almost always going to lead do some issue.
-
The number of people I've seen using 1.1.1.0/24 still boggles the mind.

-
Shame I could not use 10.90.280,xxx LOL
I am still trying to get my head around the IPv6 Private IPs of fdxx:xxxx:xxxx:yyyy:zzzz:zzzz:zzzz:zzzz
I was toying with the idea of fd10:0009:0028:1977:zzzz:zzzz:zzzz:zzzz and let DHCP handle the :zzzz:zzzz:zzzz:zzzz part
I simply do not understand the "Track Interface" to the WAN in the LAN setup well enough to get that part working.
Thanks to you and all others for the input/guidance.
-
@stephenw10 yeah, which hey if that is what they do fine. But what bugs me is when the same person comes here and wonders why they can't talk to cloudflare for dns ;)
Still in favor of basic network understanding test to even download pfsense ;)
@bearhntr you could for sure use 10.90.280
You can also use whatever local IPv6 range you want that falls in the link-local range fe80::/10 . -Not going to do you any good if you want those clients talking to the internet.. And using a link-local address has zero to do with tracking what gua prefix you get and using one of the subs on lan side interfaces.
Did you want to use the ULA range? fc00::/7
Personally I would get a handle on IPv4 before messing with IPv6 ;)
If you don't like prefixes that change, or the size of the prefix your isp will give you, or if they will give you one at all.. You can always just run a tunnel from Hurricane Electric - they will give you a /48, that never changes. And you can use whatever prefixes out of you want for your networks.. I match them up so they line up with an octet I use out of my IPv4 range. So I can easy look at the prefix and know what network it is since it lines up with the IPv4 I have on that network.
example my lan is 192.168.9.0/24 my IPv6 on that network is 2001:470:xxxx:9::0/64
And the last number matches, so for example pfsense IP on my lan is 192.168.9.253, while its IPv6 is 2001:470:xxxx:9::253
-
@johnpoz said in UPnP and VLANs:
@bearhntr you could for sure use 10.90.280
Oh just noticed - sorry no you can't use .280, that isn't a valid octet.. You could use 10.90.255 or maybe 10.90.28. would be better and closer
-
@johnpoz and @stephenw10 and @Gblenn and @WN1X
I changed the VLAN to be another 10.xx,xx,xx/24 segment and UPnP starts up with no errors. Thanks everyone for your assistance. I managed to do it all without breaking the DC either.
NSLOOKUP still does not function properly - it never has since I built the DC (well it works on that server - but nothing else in the lab domain). There are FWD and REV Lookup records in DNS on the DC...but they still do not work. :-(
-
@bearhntr what is not working for nslooup? Can you set debug on it and do the query for what your looking for