Traffic Not Routing Over Tailscale
-
I have Tailscale installed on pfsense and it’s been working great until I added a new machine to my Tailnet yesterday. The screenshots below shows that my new Tailscale IP should be routing through the Tailnet, however, the traffic is actually routing over my WAN. I’ve restarted Tailscale and even rebooted pfsense but am still getting this issue. Any ideas on how to fix it?
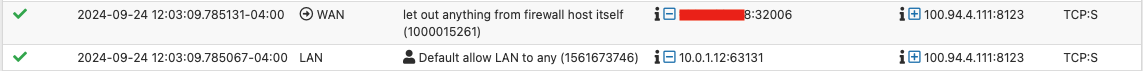
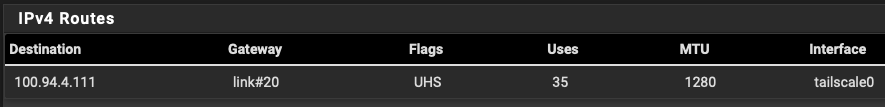
-
Is it just that one device that is routed incorrectly?
Other devices are correctly routed over tailscale? The gateway is the same?
-
@stephenw10 It's any new device I add. Older devices seem to be fine.
-
Are you policy routing traffic?
Do the new routes appear identically to the working ones?
-
I had a strange issue as well, but I'm not sure if it is related.
Like you, I've been using Tailscale for a while without any issues. I have a number of subnets behind my pfsense device which are accessible from remote Tailscale hosts, and likewise I could access the remote Tailscale hosts from behind my pfsense device. Today, when I tried to access one of the Tailscale remote hosts, it didn't work. I was unable to ping the remote host from my PC, but ping from the pfsense web interface did work (unless I would select a particular internal VLAN as the source). The pfsense routing table looked fine and the outbound NAT rule was still there.
I rebooted the pfsense device, just in case, but that did not make any difference. I removed and re-added the outbound NAT rule, and again that did not make any difference. As a last resort, I reinstalled Tailscale from the package manager menu, and lo and behold all is working fine again after that! So, if you haven't tried reinstalling Tailscale yet, that might be worth doing...
-
Hmm, odd.
If you were able to ping it from pfSense but not from the VLAN address you had a test client in that implies the source address must have been the issue. Policy routing could not affect that. NAT rules still could though.
-
I agree, it's very odd. I can confirm that it was the same client address on the VLAN before and after the reinstall, no other changes were made. Unfortunately, I wasn't aware of a way to debug pfSense to find out what happens to the request after it passes the VLAN firewall 'allow' rule. As I mentioned, the routing table looked fine and the outbound NAT rule was there, so it should have worked, and it used to work before, but something stopped it from working. (Perhaps the pfBlockerNG upgrade issues earlier in the week had something to do with it, but luckily I got that sorted thanks to your instructions @stephenw10, so thank you
 ).
). -
@stephenw10 The new routes do look identical to the older/working routes.
-
@AberDino I tried to re-install the package but it still didn't work.
I also have another weird issue where tailscale shows the new IP/machine's status as a "-" as opposed to "offline", "active", or "idle". So I'm not sure what that's about but that could be part of my problem.

-
@420ow6jv953u https://tailscale.com/kb/1080/cli#status provided the answer for the above. But not the original pfsense issue.
-
Do you see the new device on-line in the tailscale web interface?
The only thing I can really imagine there is that the crypto-routing for that new device is not valid so tailscale rejects it. I'm not sure why that would be though.