Puzzling CPU Usage
-
@jrey Thanks Jrey, I noticed in the log that the only message is " ASN Token not defined. Terminating Download. " and nothing more. I see a number of feeds that show the asn token not defined message and dont recall these feeds requiring one. I am going to look at them and see if I can suss out the problem. I reached the max uploads so I have posted what I can from the logs. I need to look into your alias question, I know the feeds are capturing packets as indicated in the dashboard but how they are configured is not something I looked at, just inferred once the feed was setup the filtering would just happen. I will upload what I can find, not something I looked at before.
Log entries:
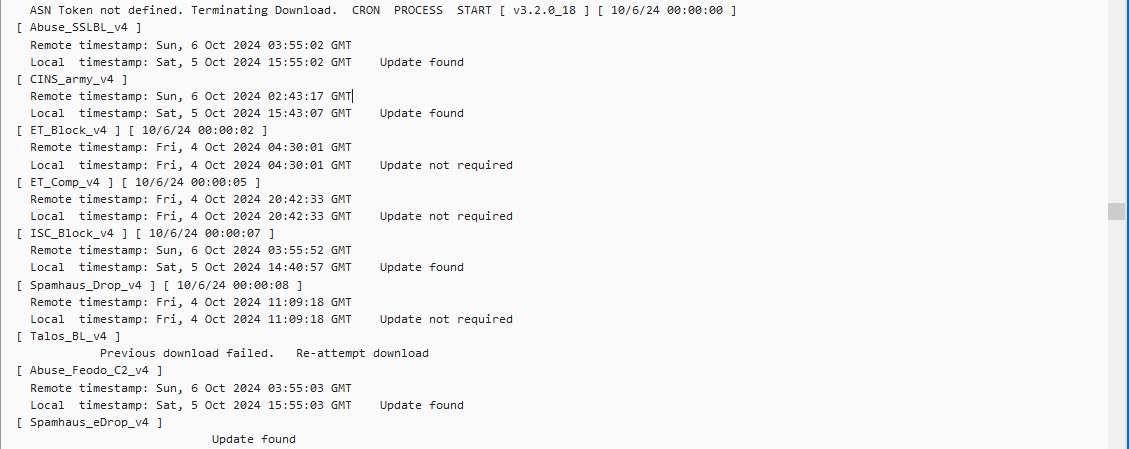
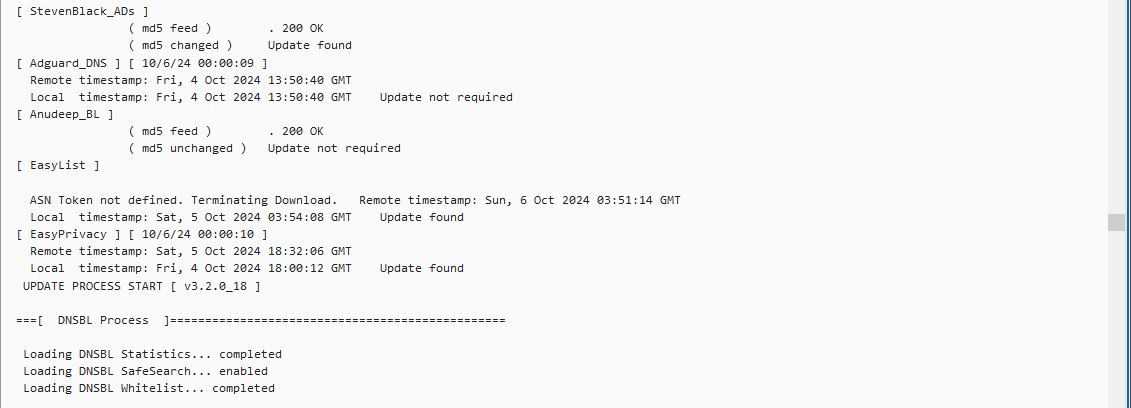
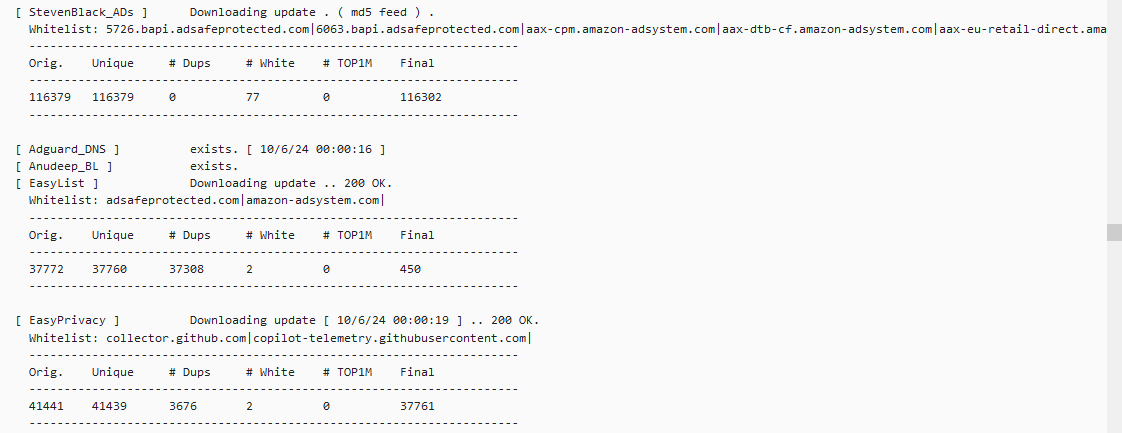
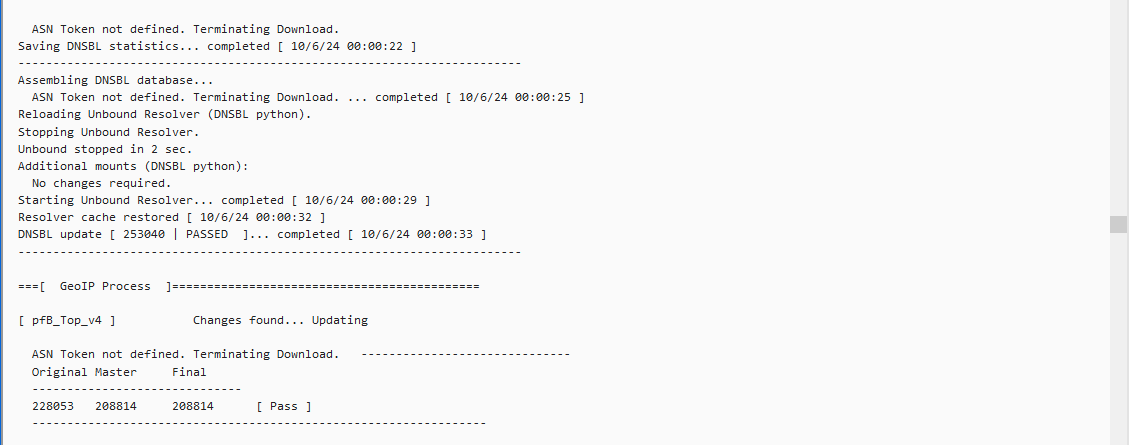
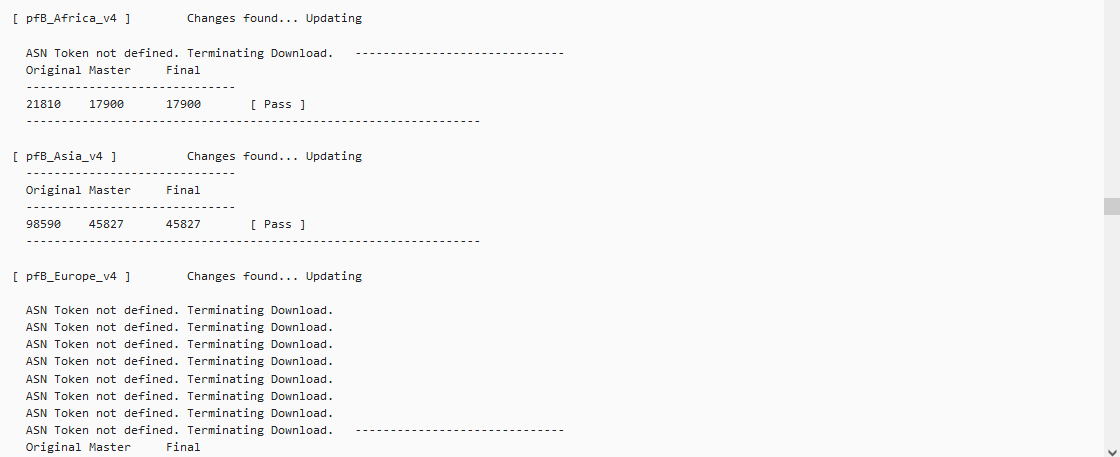
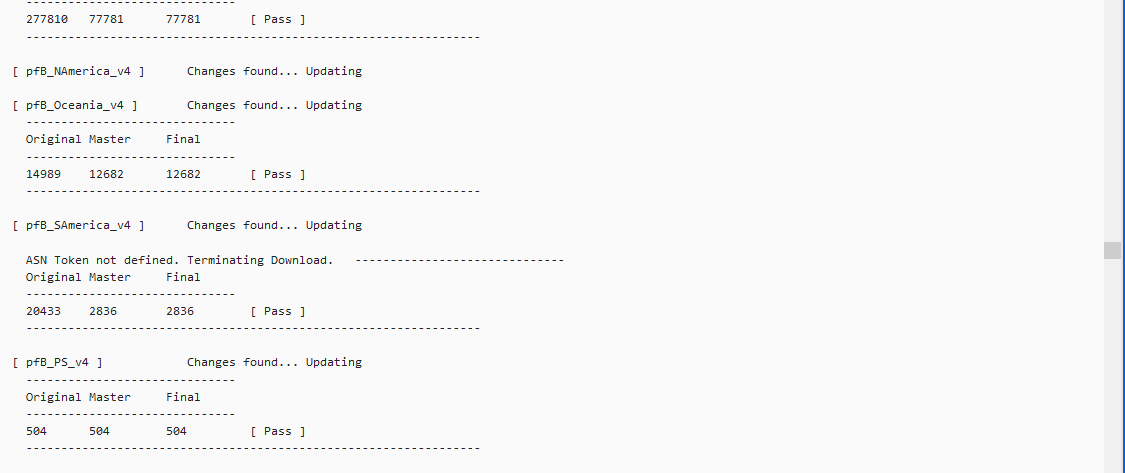
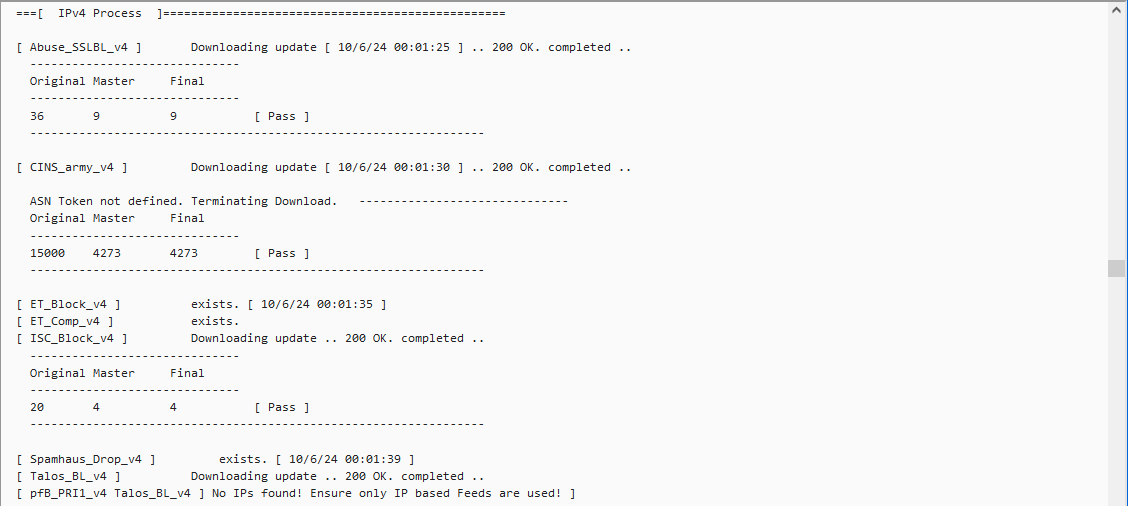
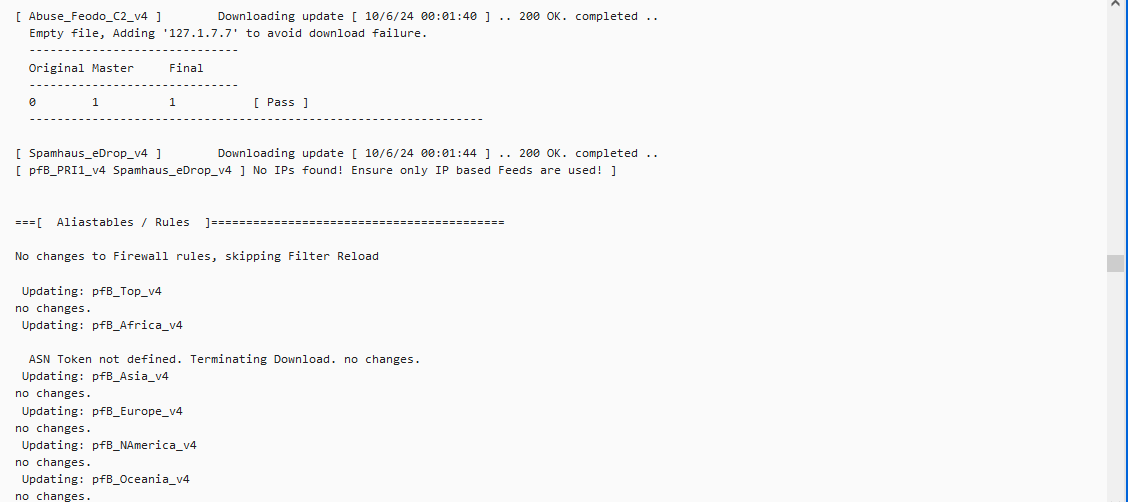
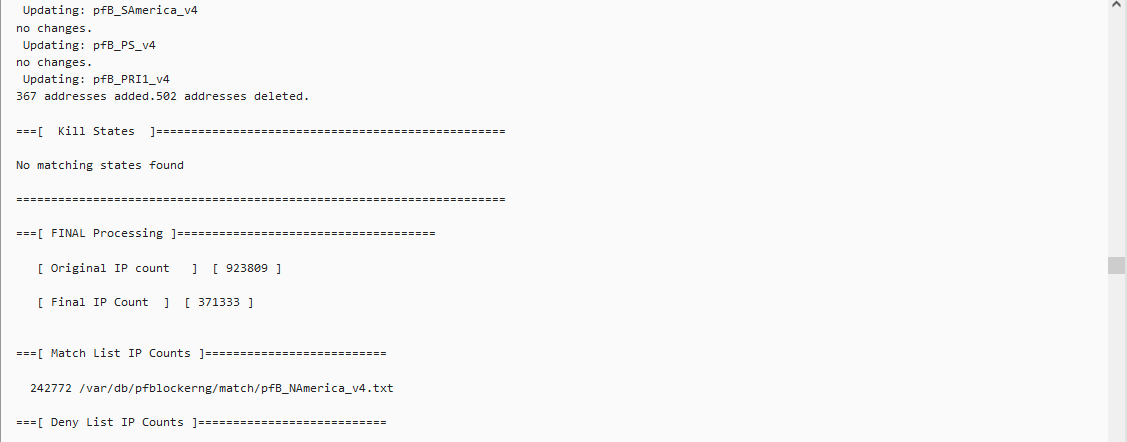
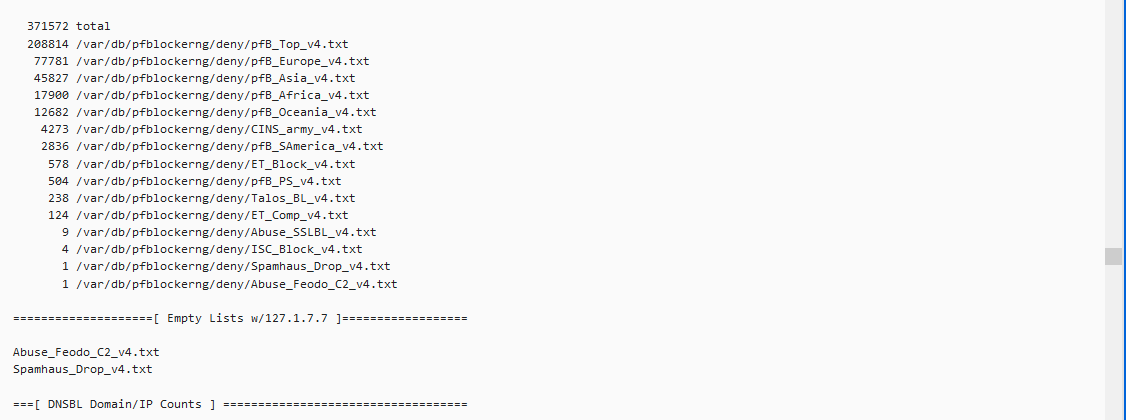
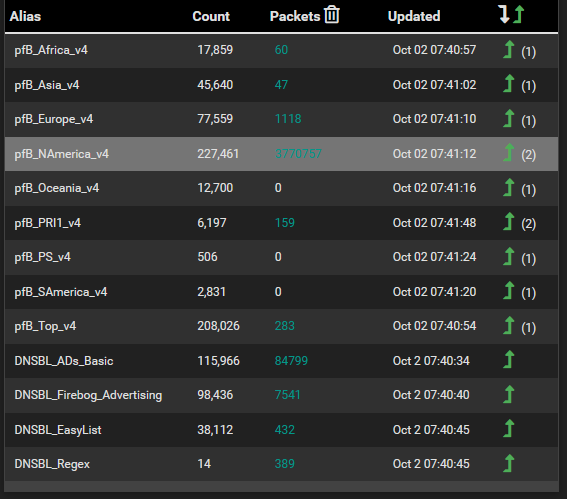
Update: As per your question regarding lists/rules for the feeds yes based on what I can take from the below SS they are being blocked, rejected, and matched, does this answer your question?
-
@jrey said in Puzzling CPU Usage:
something like this - what do you see?
pfSense Table Stats
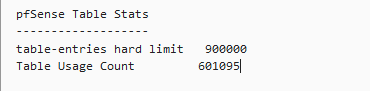
table-entries hard limit 600000
Table Usage Count 142826
notice the error references the same list I asked about here..Some interesting things in the log parts you have provided, but I don't think you went down far enough (or at least I'm not seeing this section in what you provided)
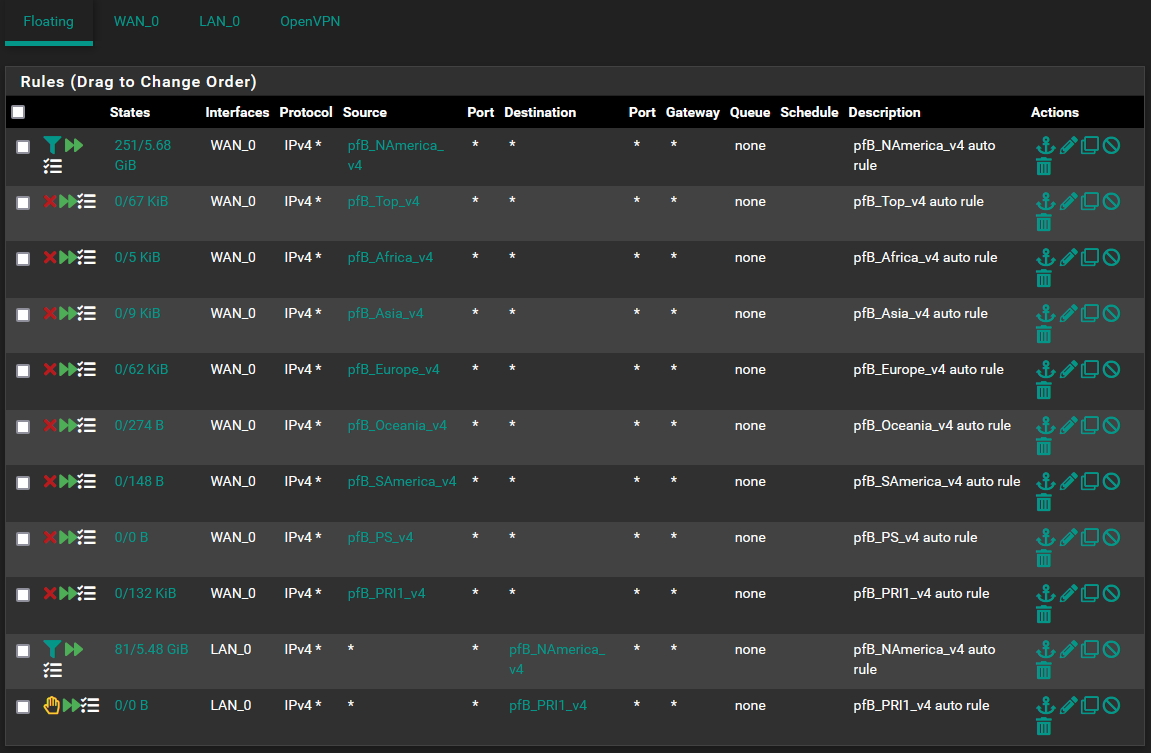
it should be very close to (if not just before the logging of UPDATE PROCESS ENDED.)What exactly is your expectation for the NAmerica rule at the top of the rules list?
-
@jrey I found that section in the logs and included below
My goal for any of the lists is to reduce/remove ads including youtube, limit access to questionable url's, IP's, domains, etc, spam, and so on. The NAmerica v4 you asked about is actually very active:
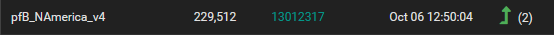
It think it is associated with the IP>GeoIP Summary list which I think is setup as part of the install. I know I selected the ip4 country list sometime back.
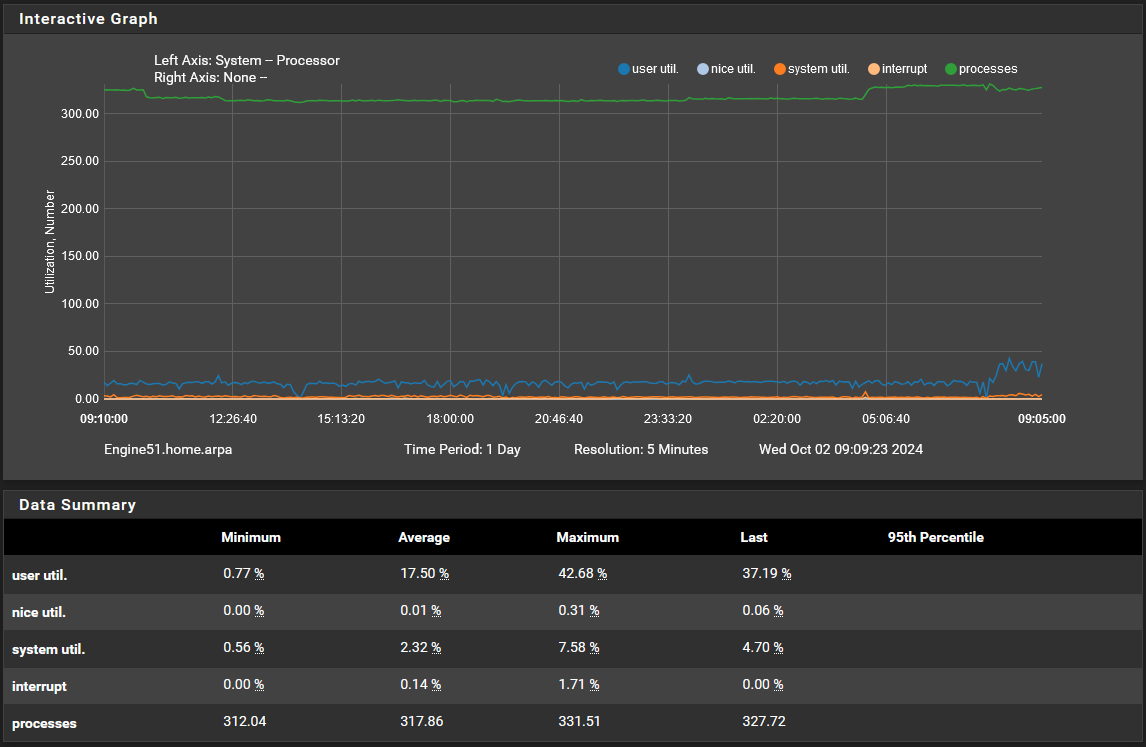
I was seeing a slowdown in browser loads in various devices in the network and thought maybe i had overdone it with the feeds so I disabled PFB and DNSBL reloaded (cron) and tested the browsers and there was no change so I feel that so far PFB is not slowing things down.
Does the order of the feeds within the rules list make a difference in performance or other?
Let me know what you are seeing from the SS and what you think could be done to achieve the goals with lower system utilization and or greater performance. Thank you.
-
So generally the rule of thumb is you want the top number (900000 in your case) to be 2 times the size of the bottom number. You obviously know where to change that because you have.
However that top rule that you have is a match rule, right... here is the summary from your log.
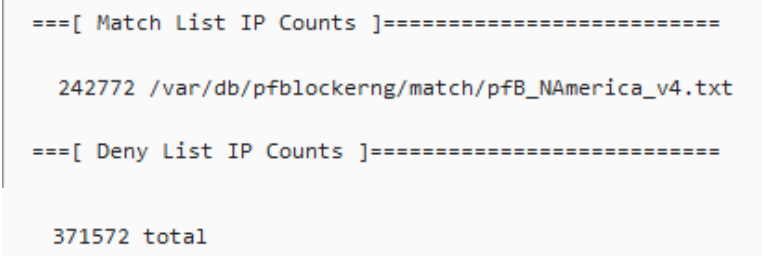
"The match action is unique to floating rules. A rule with the match action will not pass or block a packet, but only match it for purposes of assigning traffic to queues or limiters for traffic shaping. Match rules do not work with Quick enabled."
but you have no queue "queue = none" and likely don't need one in most cases.
you will see traffic logged because traffic will "match", but honestly likely not doing what you think.Based on your stated goal having the entire NAmerica list of IPs especially on a match rule is not serving the purpose you might be thinking. So it is taking resources and providing no value to your end goal.
The list of NAmerica is sourced from MaxMind, I don't use MM for GeoIP, but you should be able to "unselect" NAmerica and it will actually make no difference to traffic, but a difference in resource usage.
The strategy for blocking "ads" then is usually DNSBL and then perhaps creating a list of specific block rules for ones that slip through. But DNSBL is only part of that.
Ads that appear within Youtube content is a very different thing because often the ads come from the same servers as the content they are embedded within. So it is harder to block one without blocking both.
The rules are one thing to control the traffic source and destination. Blocking ads can be part of that, but generally other techniques are better at doing that.
-
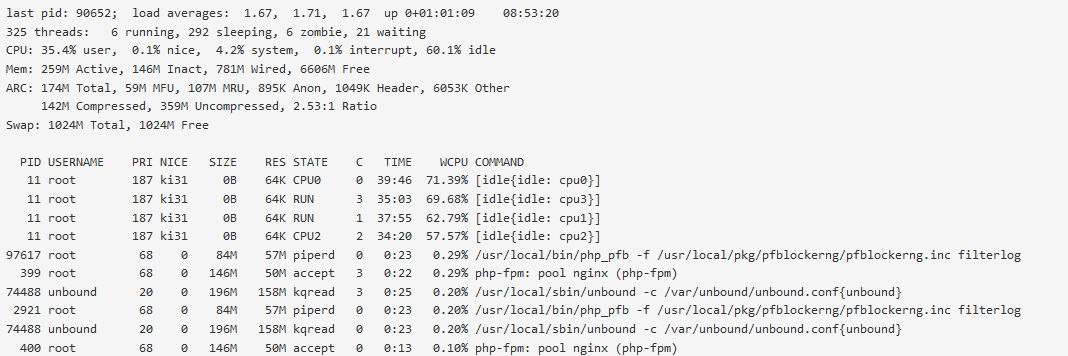
How long after boot are those logs from?
You can see pfBlocker updating which can use a lo of CPU but that would be shown in the top output.
-
@stephenw10 said in Puzzling CPU Usage:
How long after boot are those logs from?
Yes, and
while true - the log file appears to be from the scheduled "midnight" run - so that particular log does not appear to be related specifically to a reboot.
Once we sort out the rules and list sizes, we'll look at the "ASN Token not defined, Terminating download" messages that are scattered throughout the file..
We still need to fix these as well
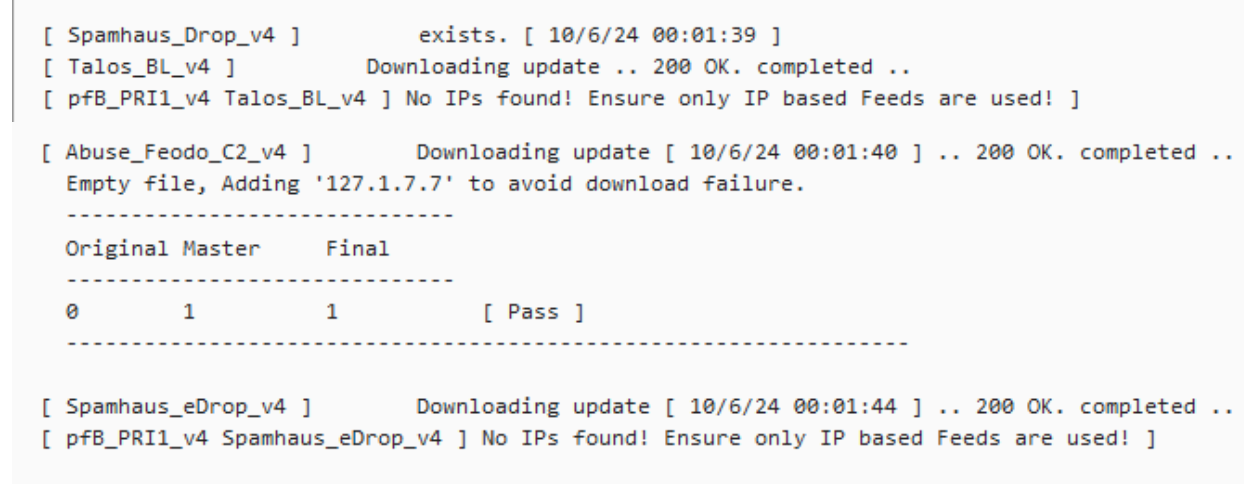
All three have been discussed in other topics. One won't work because the download now requires an accept button press every time a download happens, one in fact an empty list, and one needs a small code change. to the _18 -devel package.
Currently they are not causing operational issues and so are minor issues.Yes pfblocker will cause CPU usage when updating, One way we can tie the spike together would be to see both the start time (which we have) and the updated complete time (which I do not see in what has been provided) and also the update schedule. When pfblocker is updating and logging all the stuff we can see (errors and all), if that process takes say 30 minutes to run (we don't know), the processor would appear to be spiked during that time. If the schedule is "default" and with the error, if it is running hourly and attempting to do everything again, because it has not been successful, then every hour you get 50% of the hour in a spiked position.
-
This post is deleted! -
to address the "ASN Token not defined", you need to obtain if you have not already done so a key from ipinfo.io,
you need to enter that Token here:
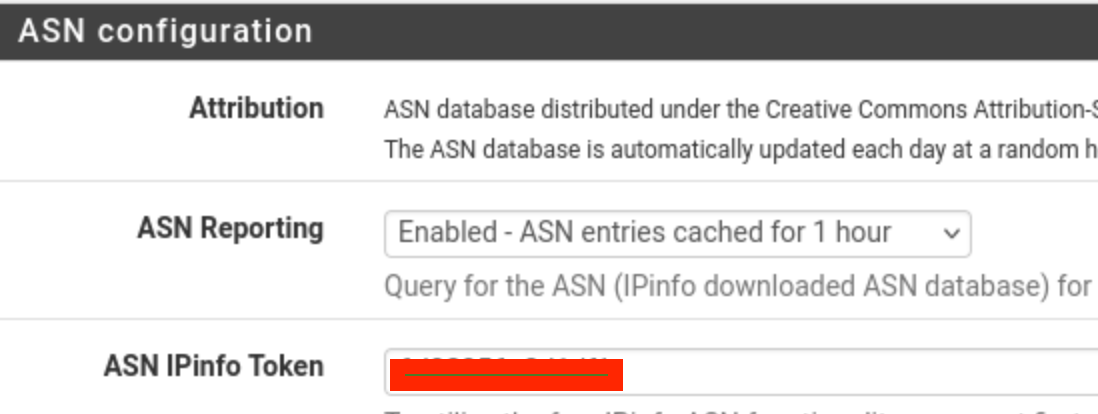
you must also select the ASN Reporting - enabled with 1 hour as shown.
and setup at least one ASN (I'm assuming you already have this because of the ASN Token messages in pfblockerng.log that we can see.
Check the extras.log to see if the asn database(s) have been downloaded.
-
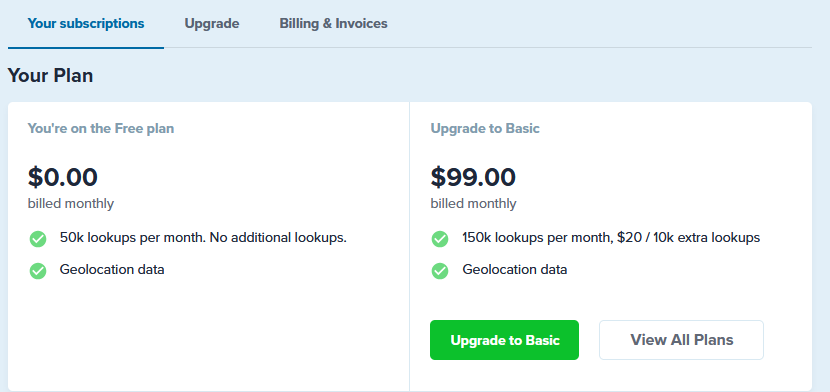
Hmm, ASN appears to be a paid service now. Something I hadn't noticed.

-
@stephenw10 said in Puzzling CPU Usage:
Hmm, ASN appears to be a paid service now. Something I hadn't noticed.

up to 50K lookups per month with no cost
-
Ah, confusing website! Nice.

-
nope - people should be signing up for the free level - same as they do for MaxMind - you just need a token for it to work since pfb _18 was released
the free version should be more than generous for what will be (and is) required
And again the key difference is that under the old bgpview each ASN was downloaded with every cycle as required.
with ipinfo.io it is one download per day, and it include ALL ASN data. when pfblocker then runs it scheduled ASN updates - all the data is already local. and honestly there is no use scheduling those feeds to update more than once a day. the data won't change.
Edit: The message being seen in the log "ASN Token..." is caused by 3 things
a) no token
b) ASN Reporting must be enabled (this is a change from previous version where you could still get the ASN downloads with the setting as disabled.)
c) you actually have to have something trying to use the ASN data.. (because it is logged for OP, this is not likely a problem - only A and/or B) -
@stephenw10 @jrey Sorry for being MIA. Having work done at the house and they keep taking down my internet because of the circuit it is on and the cable is in the way. As soon as I have stable connection I will respond to your comments/suggestions. Cant rely on my cell hotspot since I am in a gully and signal strength is lousy. So much for 5G. Be back online soon.
-
@stephenw10 Not sure how long after. It would have been a half day at least.
-
@jrey So based on this if I am reading this right you feel I need to correct the feeds with no ips, I havent looked into it but it seems that disabling or removing the "lists" would be the way to go?
Sorry just getting caught back up. Was without internet for 2 days, fiber got cut while work was being done what a hassle.
-
All I am suggesting is that the NAmerica list you are using, is likely not doing what you want/require if anything of benefit to you at all, and therefore you could likely not use that list and save the resources it requires.
Based on the information provided, that is a match action and as such as quoted from the manual
"The match action is unique to floating rules. A rule with the match action will not pass or block a packet, but only match it for purposes of assigning traffic to queues or limiters for traffic shaping. Match rules do not work with Quick enabled."without the associated queue (and it appears you have "none") the rule will only be logging the traffic nothing else
You certainly don't want it blocking all traffic, so Block and Reject are likely not a choice. At the same time you don't want to allow all traffic to pass into your network so Allow is not a choice.
Remember by default, out of the box, traffic will not get in unless you specifically allow it. You don't need to specifically allow inbound for devices that make an outbound request to website (for example) The return traffic will be allowed.
Only you can say what you need and want it to do based on your requirement, but it looks to me based on what we see, that NAmerica does not need to be selected.
-
@jrey @stephenw10 I got an IPinfo token and added it and the token missing messages are gone, will see if it makes any difference.
-
@jrey Understood, so if I understand you, having all within the list blocked is not a good idea but blocking some may be of value. How do you determine which would be good for blocking/rejecting, etc? Do you suggest I disable it and see what happens or would that not be a good idea as some would be wise to block?
-
@stephenw10 Yes I have the free version, dont think I would exceed the 50k lookups in a month but not sure yet how this actually works but I can see the details in my ipinfo dashboard. I setup the cache for the ASN entries for 12 hours which seems reasonable. Is there anything in PFS that shows what is being blocked/filtered by IPinfo? I also have maxmind setup and not sure what effect that is having on filtered/blocked requests. I havent logged into that in a while and will see if it has any stats on that.
-
@LPD7 said in Puzzling CPU Usage:
missing messages are gone
The ASN missing messages are gone - good.
that's part of the issue.
and now after the latest update in the latest pfblockerng.log file what do the pfSense Table Stats values look like?
What are you doing with the GeoIP list NAmerica ? (part 2 since I see you just asked more)
Correct changing the match (which is doing nothing) nothing to blocking and/or allowing is likely not needed in your case, but ..All inbound traffic to devices inside is blocked by default. So unless you are running a service (server) that you need the outside to have access to - that match rule is currently providing no value. Unless you have created a specific rule allowing access, just remove NAmerica from your selection. The others are fine because the have both inbound and outbound rules blocking rules associated. (you are blocking your users from going to addresses in those Geo locations)
@LPD7 said in Puzzling CPU Usage:
How do you determine which would be good for blocking/rejecting, etc?
Do you run any servers/services (a web server/mail server etc) inside that require access from the outside? if not then nothing. The inbound traffic is blocked by default.
if you are talking about outbound traffic that you want to block then, dnsbl, specific ASN (or individual address - in an Alias and block them that way.. define (or tell us more specifically what you are trying to block)
Don't confuse the GeoIP with the ASN blocks the rules(lists) are normally different.