Blocking DNS over HTTPS. Seems the only way is to fire a shotgun at it
-
@Tzvia said in Blocking DNS over HTTPS. Seems the only way is to fire a shotgun at it:
Feels like a cat and mouse game, or wack a mole...
Concur - its really no better than the spammer changing their tactics to find a way to get their spam to users through corp filtering.. Now its the likes of google and cloudflare.. We will get your users data someway, no matter what you say corp IT..
They really want to send us their data, honest they do because we told them you were spying on their dns.. You know on the network you own and run, and them using the device you gave them to work with.. They clearly need to be able to resolve shop.tld
Oh you don't really want that to happen corp IT.. Here

JUMP!
-
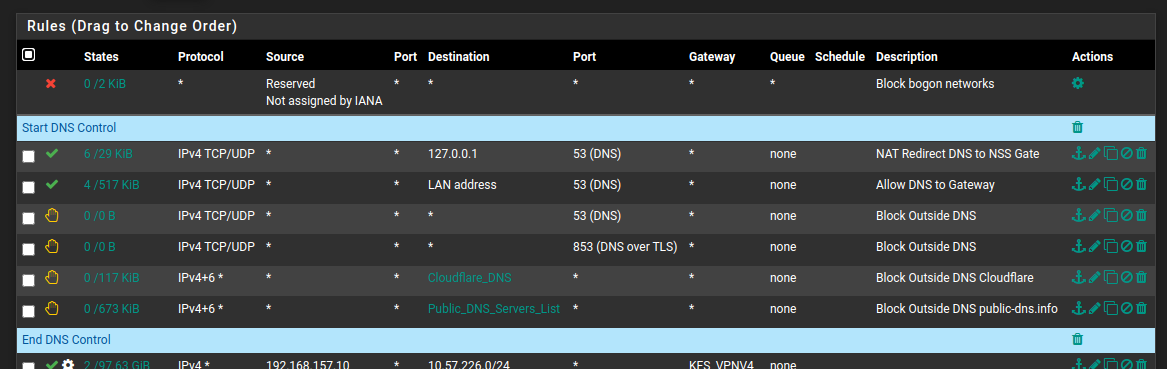
Anyway, TheGreatWall feeds are added to the latest version of pfBlockerNG-devel:


-
@Lanna said in Blocking DNS over HTTPS. Seems the only way is to fire a shotgun at it:
. . . and adding the following IP lists to the firewall as blocked aliases. . .
Trying to wrap my head around this one ...
Are you blocking everything to these IP's , or just 443 ??Are you pointing the alias to the listfiles via this one ??
Thanx for doing this
I have setup my pfSense (unbound) to use (forward) all queries to use two Linux Bind9 servers i have locally (vlan100) , doing all the resolving.
They have to have "access to the root servers" UDP 53 , if i enable (dns) portforwarding on vlan 100 , can i make an exception for these two so they're not redirected ?
I'm already handing out pfSense IF as DNS via dhcp to clients , and blocking
53/853 to other(s). No UDP 53 portredirect yet.I'm not that intertested in pfblocker-ng , i use Pihole (also vlan 100) for "scrubbing" my mobile devices.
So i suppose i have 4 local ip's i'd like to prevent from being redirected.
local DNS1 - A root server access
local DNS2 - A root server accesspihole - Allow dns from Phone vlan + Mmedia Vlan
Express-VPN ATV DNS - Allow dns to this one from my ATV's on Mmedia vlan
/Bingo
-
@bingo600 said in Blocking DNS over HTTPS. Seems the only way is to fire a shotgun at it:
@Lanna said in Blocking DNS over HTTPS. Seems the only way is to fire a shotgun at it:
Are you blocking everything to these IP's , or just 443 ??
I am blocking all ports to those IPs, but adjust to your liking
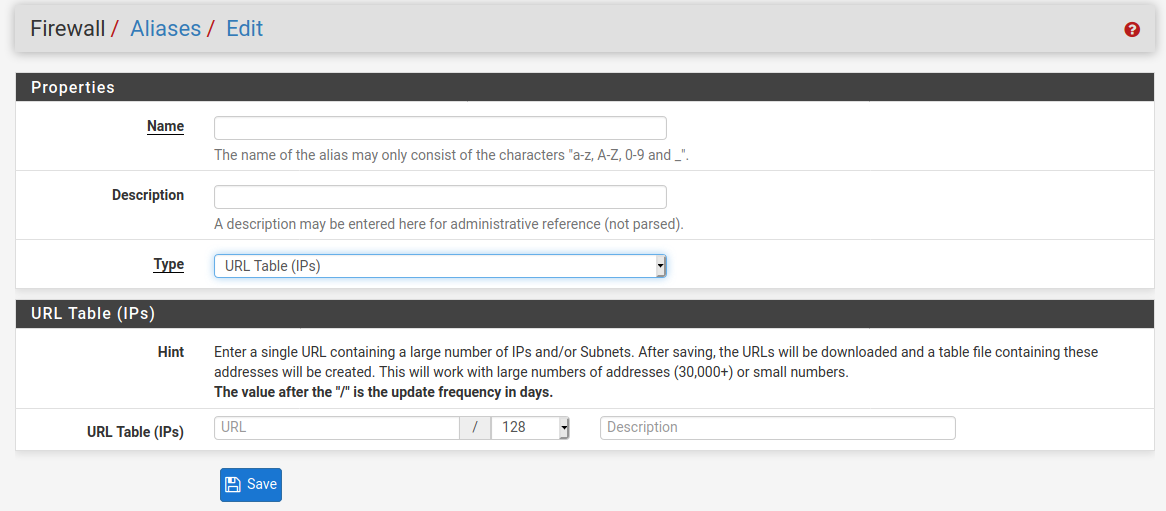
Are you pointing the alias to the listfiles via this one ??
That's right, I am using the URL Table option
-
@Lanna said in Blocking DNS over HTTPS. Seems the only way is to fire a shotgun at it:
Just to update this topic, setting the following in my resolver's custom options. . .
server: local-zone: "use-application-dns.net" always_nxdomain local-zone: "cloudflare-dns.com" static. . . and adding the following IP lists to the firewall as blocked aliases. . .
https://public-dns.info/nameservers.txt
https://raw.githubusercontent.com/Sekhan/TheGreatWall/master/TheGreatWall_ipv4. . . completely hamstrings Firefox and Chrome's attempts to use DoH. I'm sure they will find new ways to screw with network admins, but for the time being, this appears to be highly effective, while keeping things pretty neat and tidy. This is what I am deploying on my production network.
NOTE: Anyone reading this, don't just throw this into your config and forget. You MUST also have the DNS redirects to your local resolver/forwarder in place first.
Just as an addition to the above, I've spent the last 24 hours playing around with DNSBL and I realised that with the BETA of 'Enable TLD' you can in fact just add those domains in a custom blacklist and every subdomain will be blocked there too. Probably neater for some setups.
-
NOTE: Anyone reading this, don't just throw this into your config and forget. You MUST also have the DNS redirects to your local resolver/forwarder in place first.
I'm curious about how you have your NAT redirects set up. Are you port forwarding the packets destined to IP's (in the IP lists above) on port 443 back to pfSense's resolver?
Currently I have NAT port forwards to redirect all DNS requests to non-internal networks on ports 53 and 853 back to pfSense's resolver. I'm wondering if the ideas is to do the same with the DOH requests, or are you just blocking those request outright?
-
@dma_pf I'm just redirecting ports like for like. DoH is just blackholed or rejected completely. If anyone tries to set their browser to use DoH only, they will get an ssl config error when trying to visit a website.
-
Just wanted to add this great resource (see the doc subdir)
https://github.com/jpgpi250/piholemanualI snipped the url from here
https://forum.netgate.com/post/953474He has made a neat PDF pfSense guide on how2 block DoH
https://github.com/jpgpi250/piholemanual/blob/master/doc/Block%20DOH%20with%20pfsense.pdfBest is that he states in th pfSense PDF , that he is collecting/consolidating his list from the below "other" lists , and his lists are getting updated frequently.
I’ve searched and found several lists, containing references to DoH servers: - https: //raw.githubusercontent.com/bambenek/block-doh/master/doh-hosts.txt- https: //raw.githubusercontent.com/Sekhan/TheGreatWall/master/TheGreatWall.txt https: //raw.githubusercontent.com/oneoffdallas/dohservers/master/list.txt https: //raw.githubusercontent.com/vysecurity/DoH-Servers/master/README.md https: //raw.githubusercontent.com/tjay/DoH-List/master/hosts https: //raw.githubusercontent.com/flo-wer/doh-list/master/domains.txt https: //raw.githubusercontent.com/wiki/curl/curl/DNS-over-HTTPS.md https: //download.dnscrypt.info/dnscrypt-resolvers/json/public-resolvers.json https: / /dtm.uk/dns-over-https-doh-servers https: //raw.githubusercontent.com/Jigsaw-Code/Intra/master/Android/app/src/main/res/values/servers.xml https: //raw.githubusercontent.com/dibdot/DoH-IP-blocklists/master/doh-ipv4.txt https: //raw.githubusercontent.com/dibdot/DoH-IP-blocklists/master/doh-ipv6.txt https: //raw.githubusercontent.com/crypt0rr/public-doh-servers/main/dns.listHe's doing a super job , and has some god PDF guides.
Edit:
Glad i used "floating rules" , as they use "openDNS w DoH" on my "work (from home) pc"
And guess what is in the list ....
I chose to remove DoH from my Guest/Inet-Only VLAN , where it's connected./Bingo
-
 J jpgpi250 referenced this topic on
J jpgpi250 referenced this topic on
-
@johnpoz This is old topic, but when try to put this in custom options. Received error:
The following input errors were detected:The generated config file cannot be parsed by unbound. Please correct the following errors:
/var/unbound/test/unbound.conf:110: error: syntax error
read /var/unbound/test/unbound.conf failed: 1 errors in configuration file -
@johnpoz said in Blocking DNS over HTTPS. Seems the only way is to fire a shotgun at it:
local-zone: "use-application-dns.net" always_nxdomain
local-zone: "local." always_nxdomain
local-data: "dns.adguard.com. 120 IN A 172.19.19.19"
local-data: "dns-family.adguard.com. 120 IN A 172.19.19.19"
local-data: "dns.google. 120 IN A 172.19.19.19"
local-data: "cloudflare-dns.com. 120 IN A 172.19.19.19"
local-data: "dns.quad9.net. 120 IN A 172.19.19.19"
local-data: "dns9.quad9.net. 120 IN A 172.19.19.19"
local-data: "dns10.quad9.net. 120 IN A 172.19.19.19"Oh, now clear me forget to set option "server:"