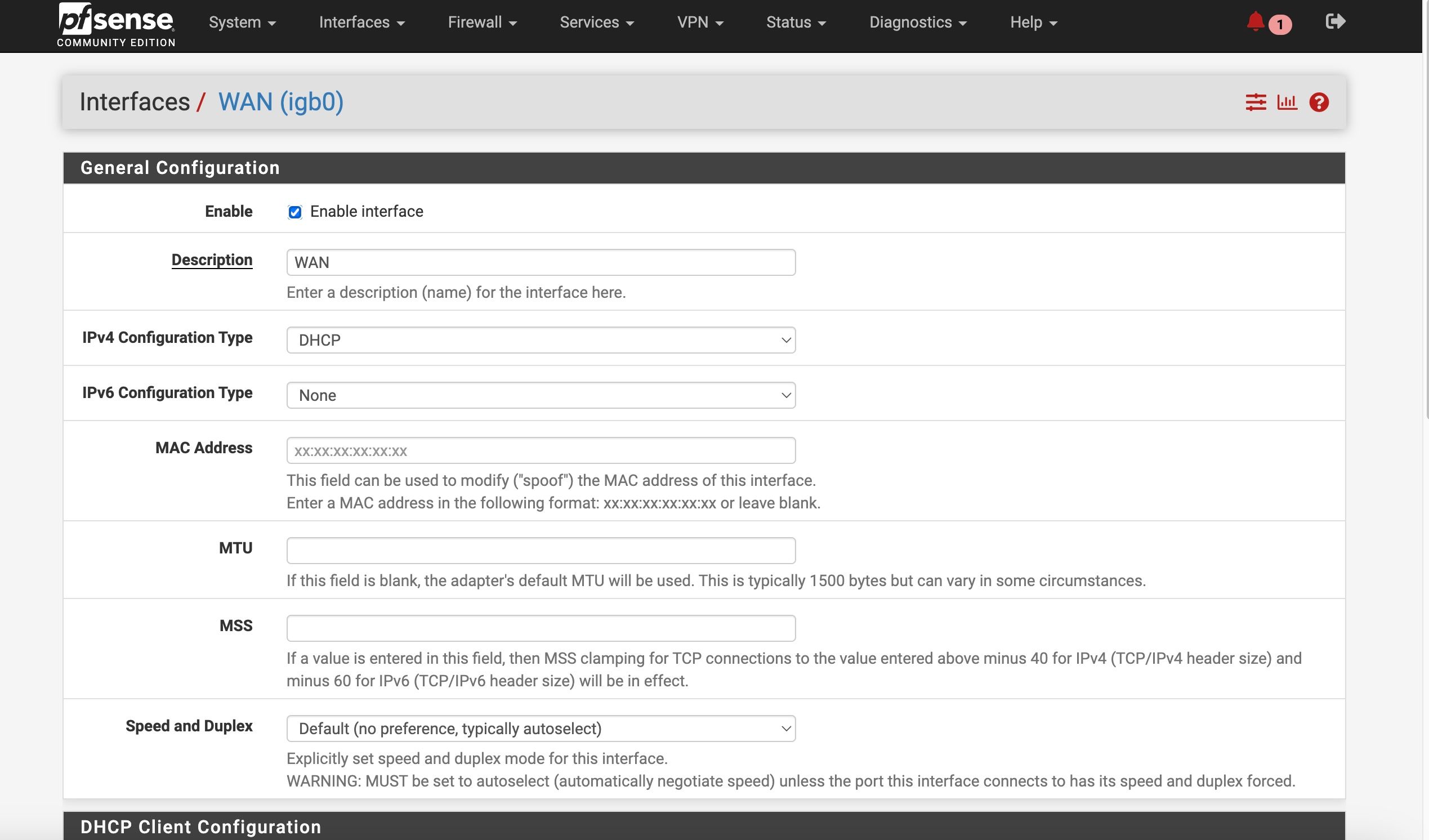
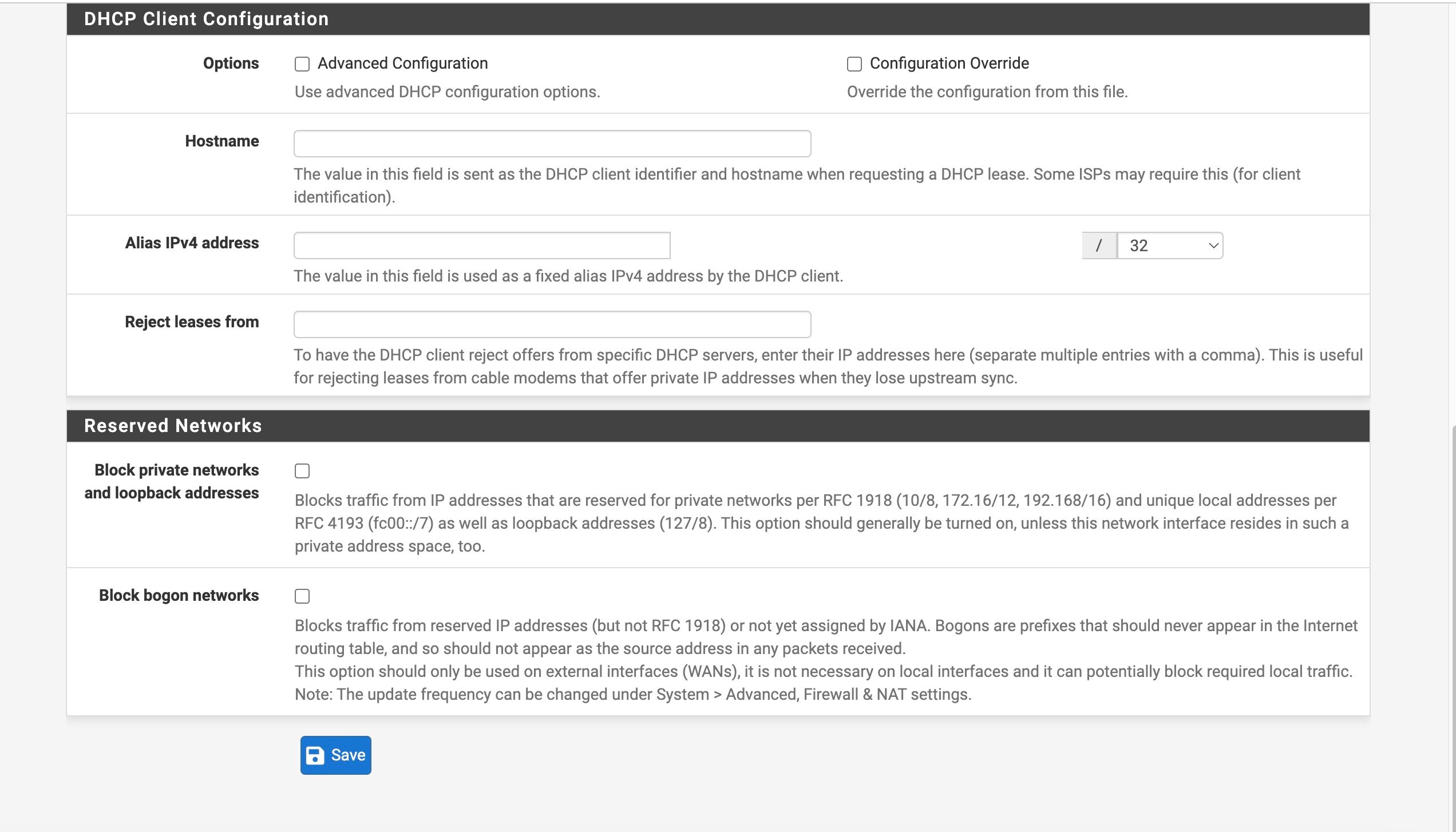
ATT Internet AIr
-
@stephenw10
So it does appear that somehting is blocking things, looking up this SYN_SENT CLOSED errorThoughts on how to fix?
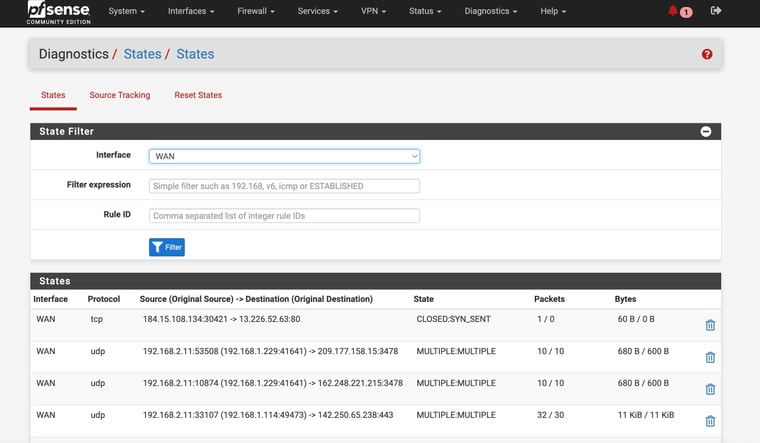
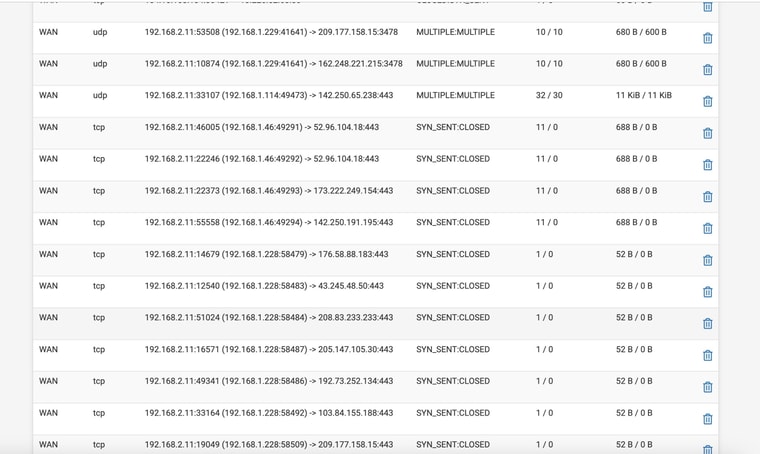
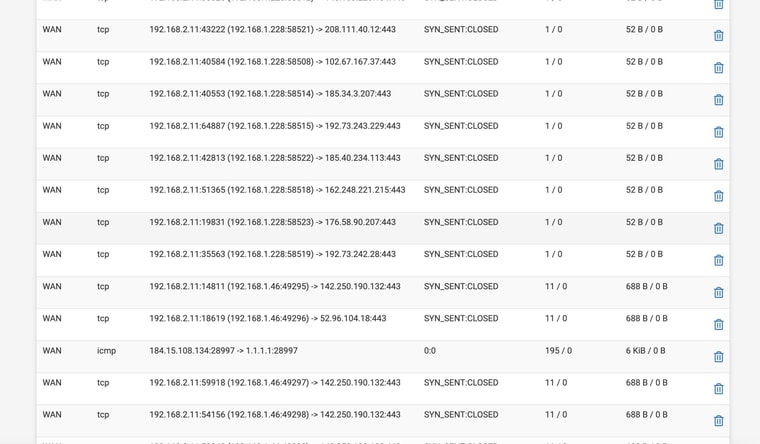
-
@stephenw10
Other weird thing is that during the failed state , while on the LAN, I can bring up a google web page and sucessfully google something and it will bring up a page sucessfully -
There are no DNS connections shown there.
Try setting All interfaces and filtering by:
:53Make sure there are at least some on WAN and they're not all on WAN2.
Did you try the state kill setting?
-
@stephenw10
I am baout ready to pull my air out - lol
I can't get anyone that speaks english (my primary language) from ATT support and what's worse nobody that knows what "bridge mode" is.I reverted my Internet Air back to the original factory 192.168.1.1 address
Then changed it to 192.168.1.155
That then gave my connection form the LAN of the Internet Air to the WAN configured interface of the pFsense an IP of 192.168.1.156
Setup the gateway and the gateway groupWhen pulled the ethernet cord on the WAN2 it goes to failed state as it should
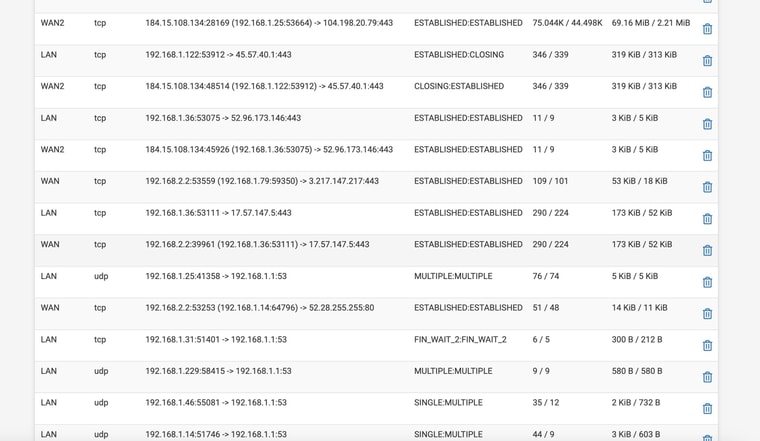
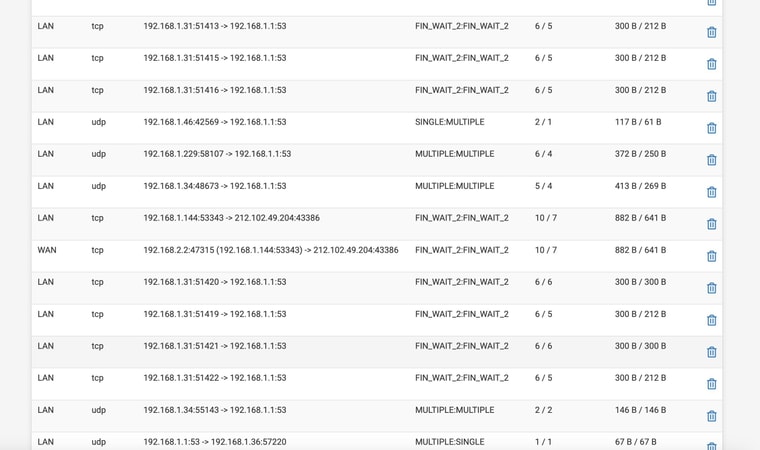
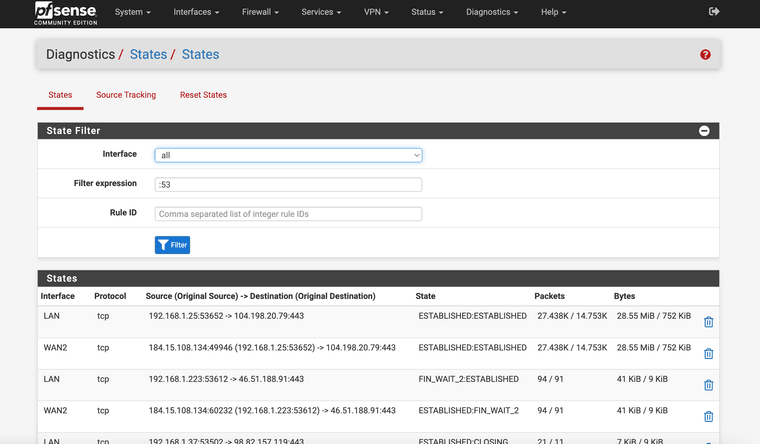
Still NO DNS -- I have attched the STATE you mentioned filtered for 53
The crazy thing is that despite the setting the state kill setting I still have to reboot the box inorder to get internet / DNS back after the failed state is corrected
I'm at a complete loss - ugh
-
Ah, it looks like your LAN is also using 192.168.1.0/24?
if
That's a subnet conflict between WAN and LAN. You need to change one of those to a different /24 subnet. That obviously wouldn't be a problem if you had a public IP on WAN.However it's also different to when you set it up above where the WAN was using the 192.168.2.0/24 subnet.
-
@stephenw10
Ok I can change back to 192.168.2.0but we were running into the same issue there as well??
Also - question -- when I create the interface connection and set up as a DHCP connection for the created WAN it seems to create some "dummy" gateway (that is greyed out and not available for use in the gateway group area). Do I just create an additional gateway ? Or how to handle that?
-
Change it back. Any tests with the subnets conflicting will definitely fail an just confuse matters.
We want to see DNS states on the WAN, without being NAT'd, and check if there are any reply packets.
Is your outbound NAT still set to automatic?
-
@stephenw10
yes automatic re outbound nat -
-
@stephenw10
Sorry for being a pain in the butt -- but the really bad issue is that I can't seem to find a work around to get things working after the "fail" without literally rebooting the pfsense box!! Makess testing so hard -
Ok, two odd things there.
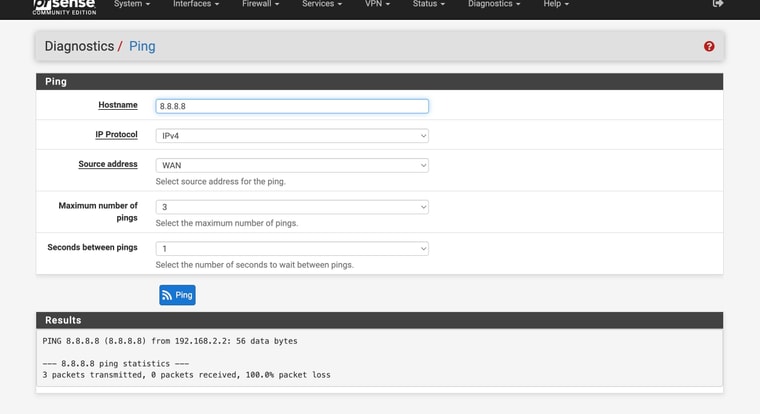
You fail to get any ping replies from 8.8.8.8 when pinging from WAN. That should work.
There is DNS traffic from WAN directly but the states show it's still being outbound NAT'd from it's own address which should never happen.
On the outbound NAT page what rules are shown for the auto generated rules?
-
-
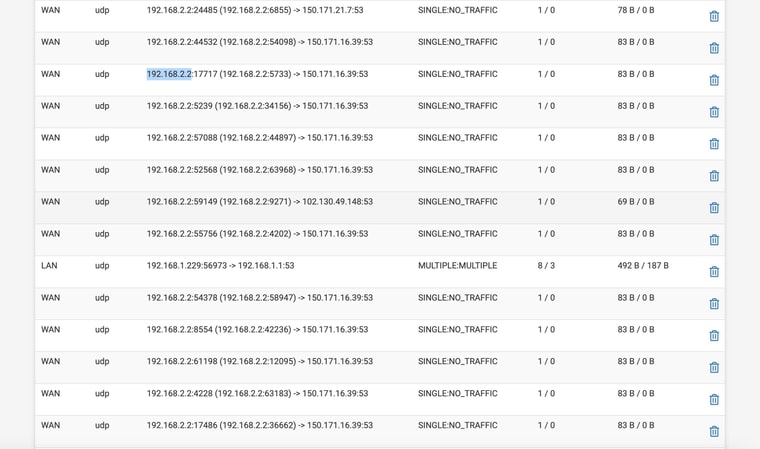
Hmm, that looks OK.
You have NAT states showing 192.168.2.2 being NAT'd to itself just on a different port. That normally wouldn't hurt DNS but it also shouldn't happen so it's unclear exactly what it's doing.
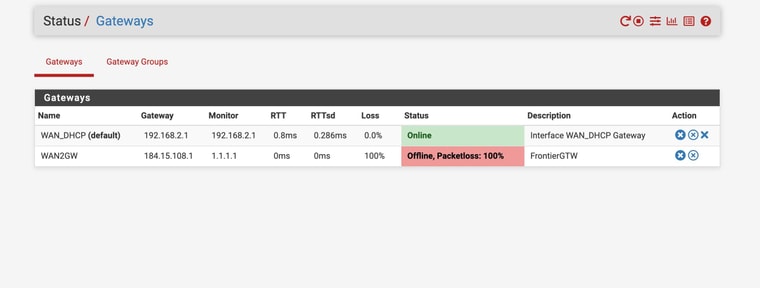
What happens if you reboot with WAN2 disconnected?
-
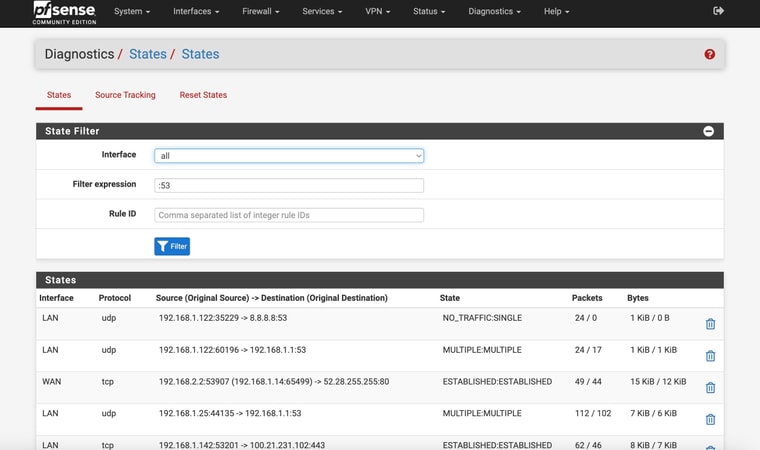
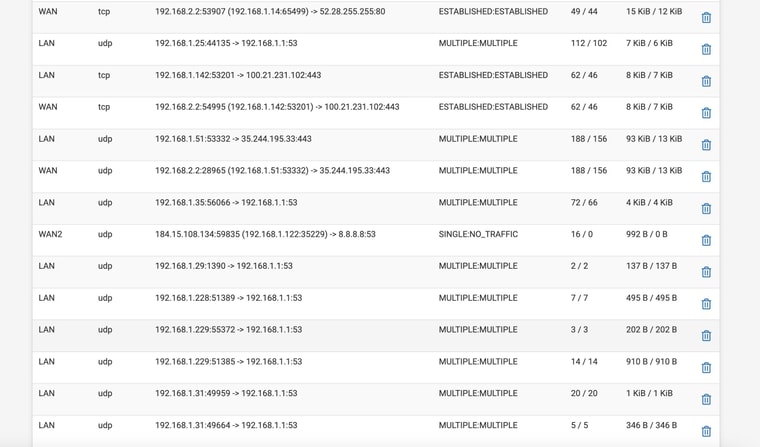
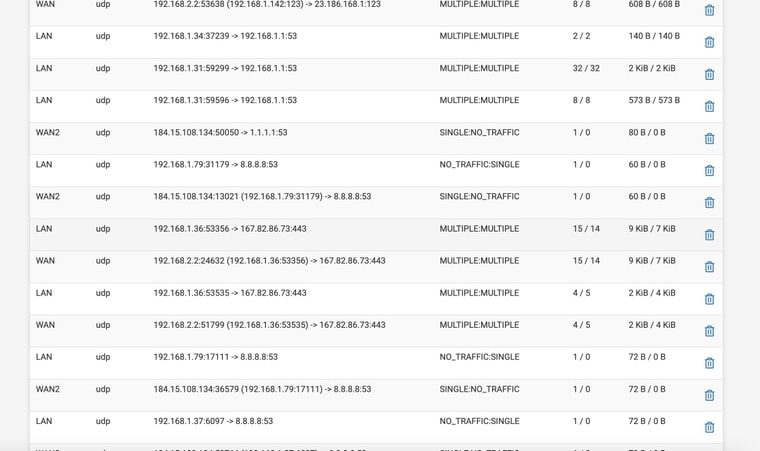
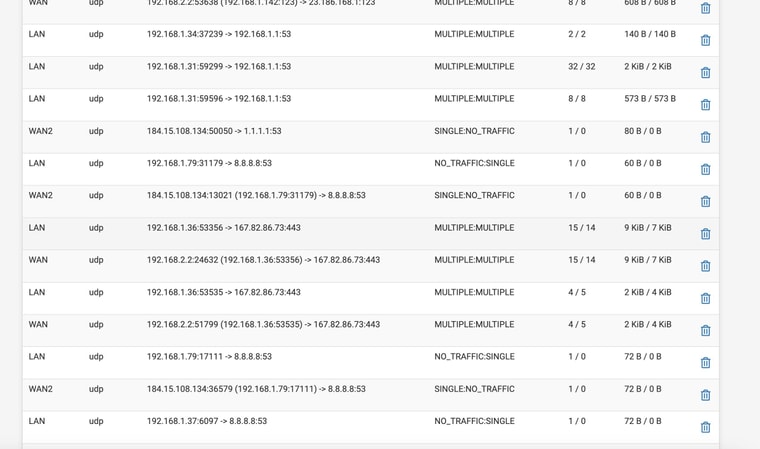
@stephenw10 So attached are shots where rebooted with WAN2 disconnected
Still no DNS
-
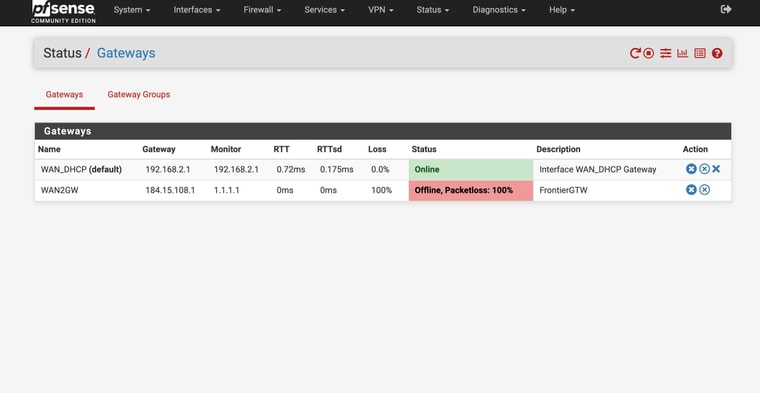
Ok. So there is no DNS traffic on WAN there.
There are clients that are configured to use 8.8.8.8 directly, 192.168.1.79 there, but it appears 8.8.8.8 is statically routed via WAN2 so it's failing.
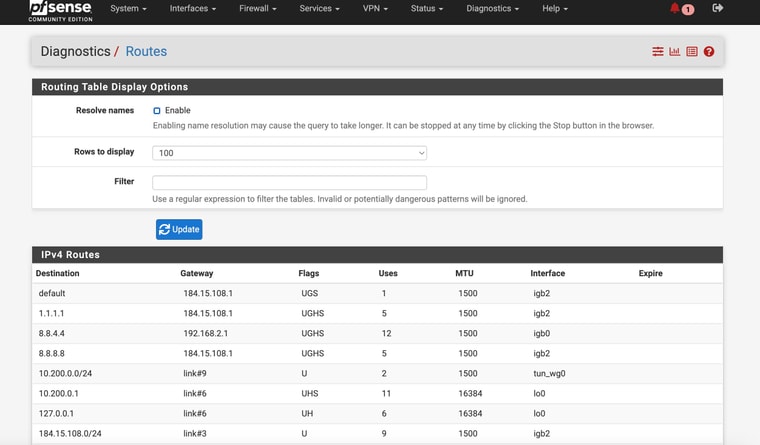
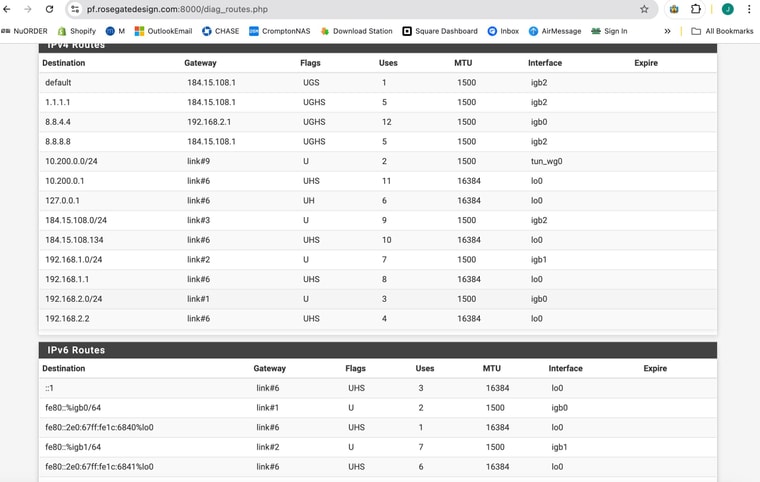
Check the routing table in Diag > Routes.
That would usually be either the gateway monitoring or in the general setup if 8.8.8.8 is configured as a DNS server.
In your previous screen shots you have 8.8.8.8 used on WAN for both those but it looks like something has changed because it's being forced via WAN2.Is 192.168.1.79 a client you're testing from?
-
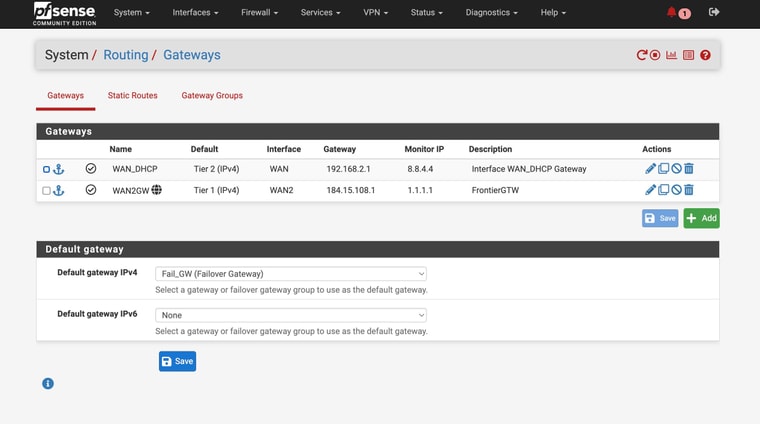
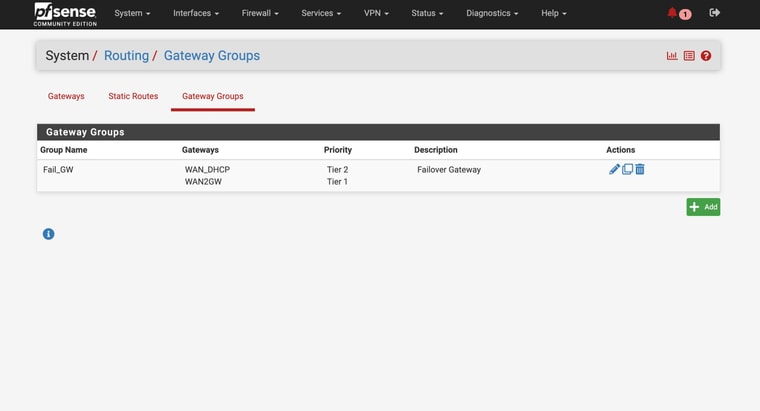
@stephenw10
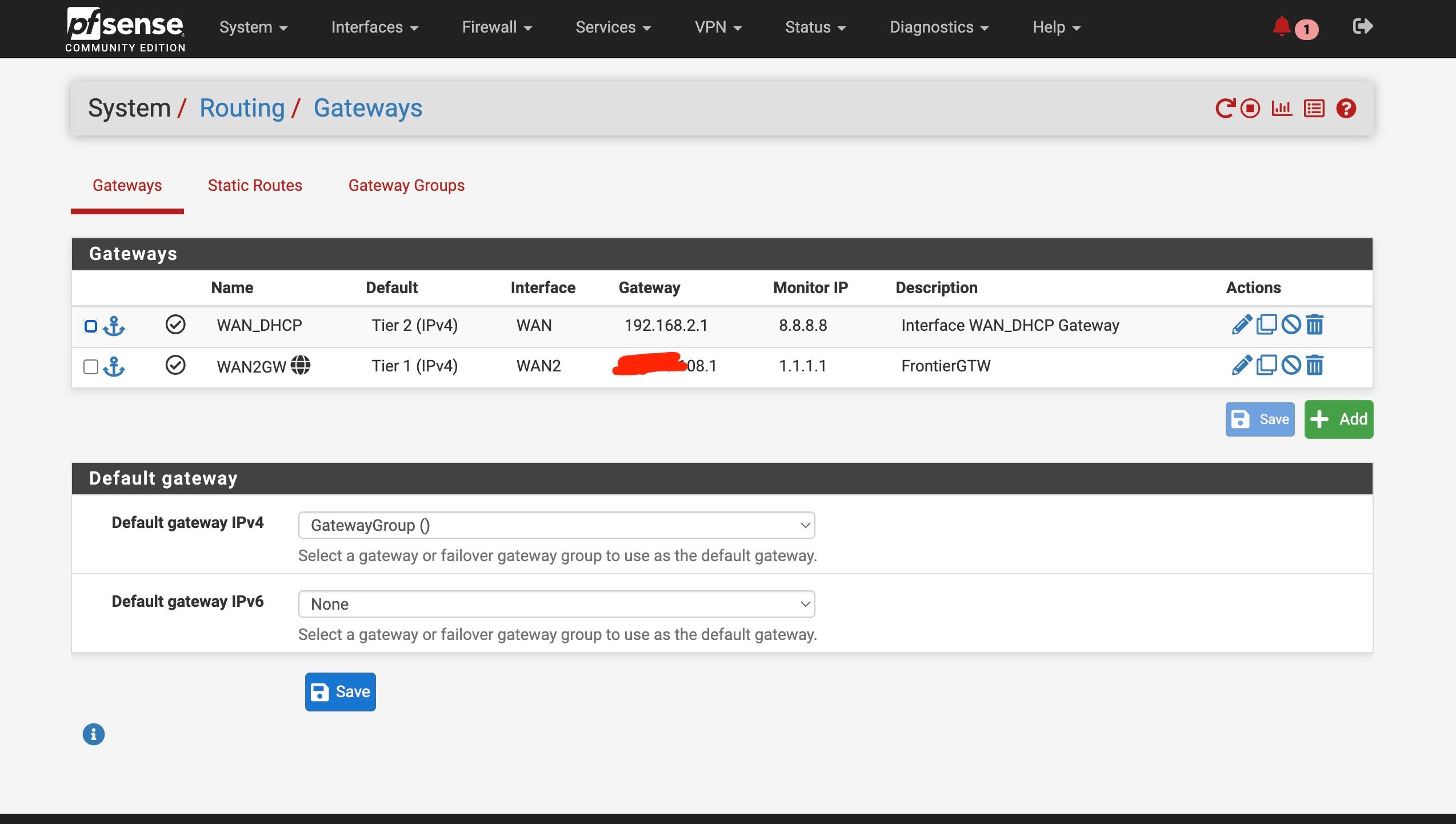
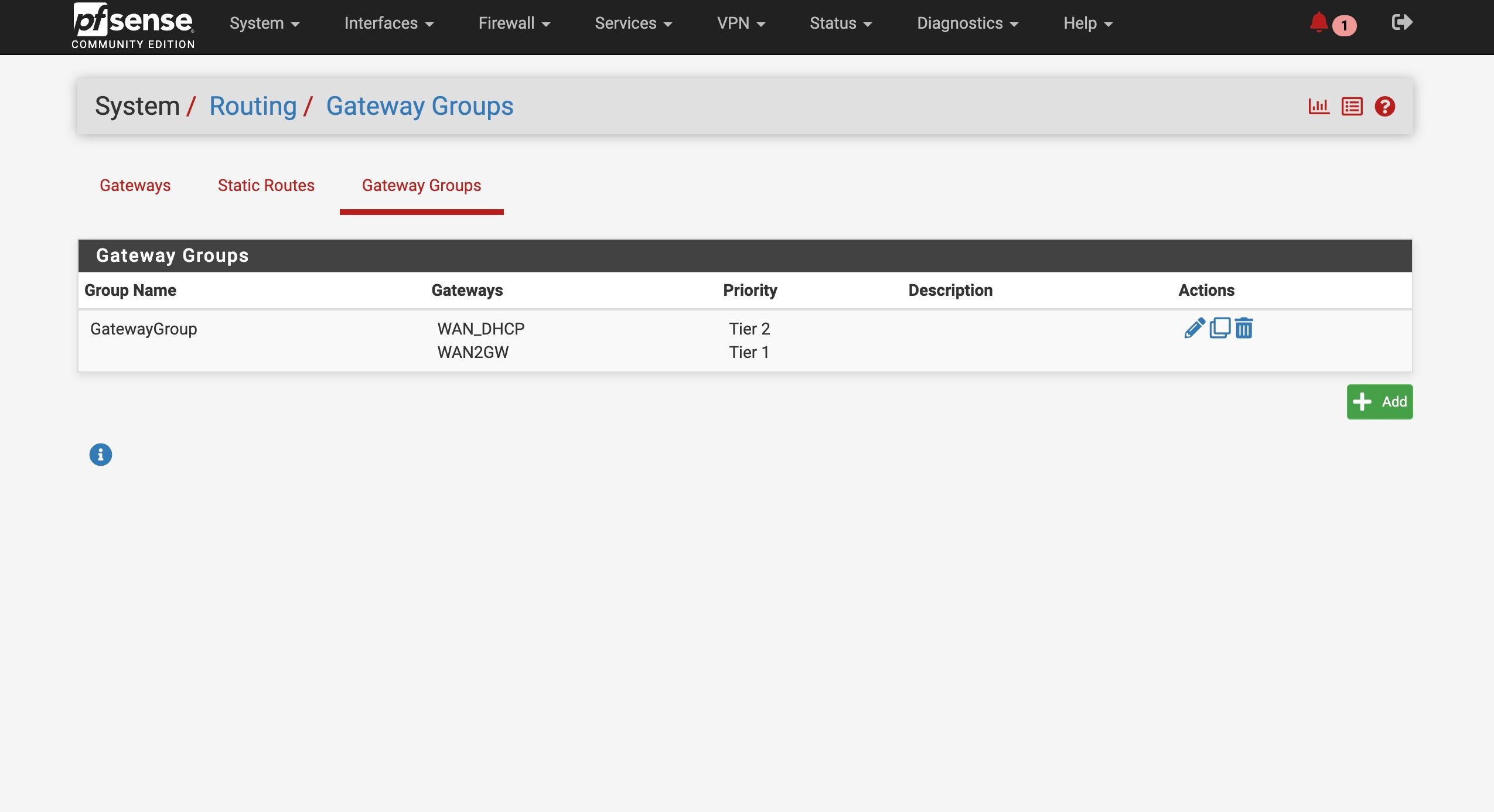
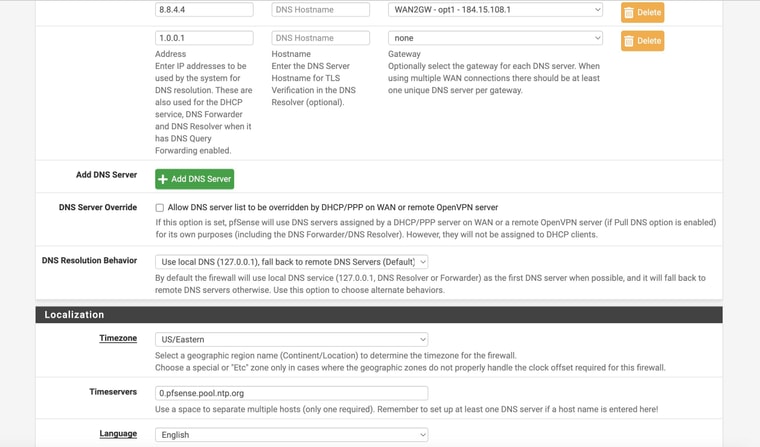
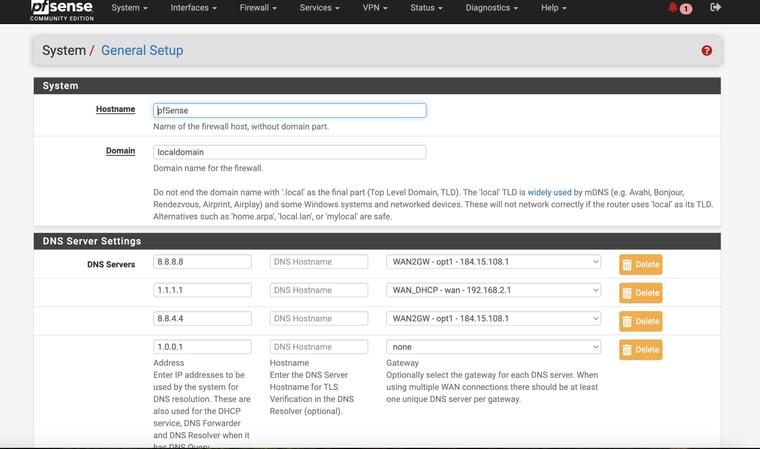
So I am attaching the Diag > Routing tableI am attaching my current setup for my interfaces / gateways
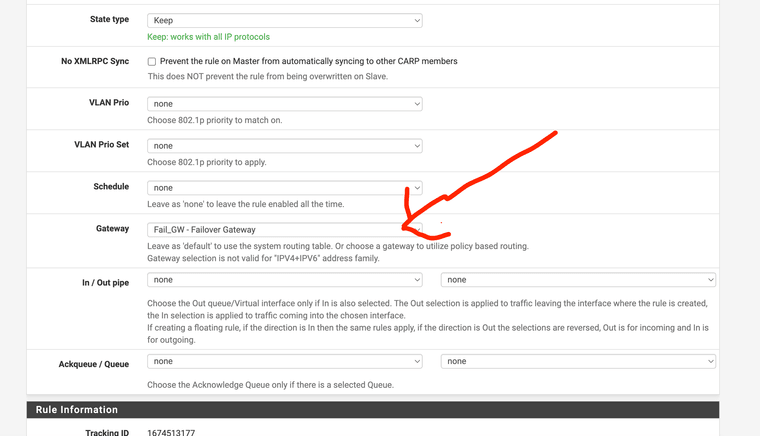
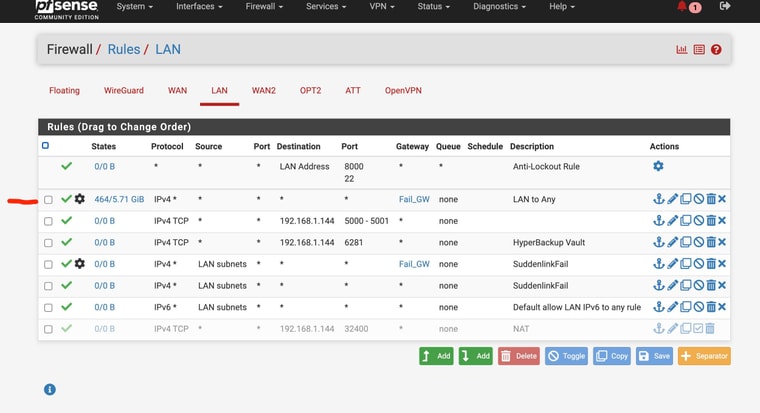
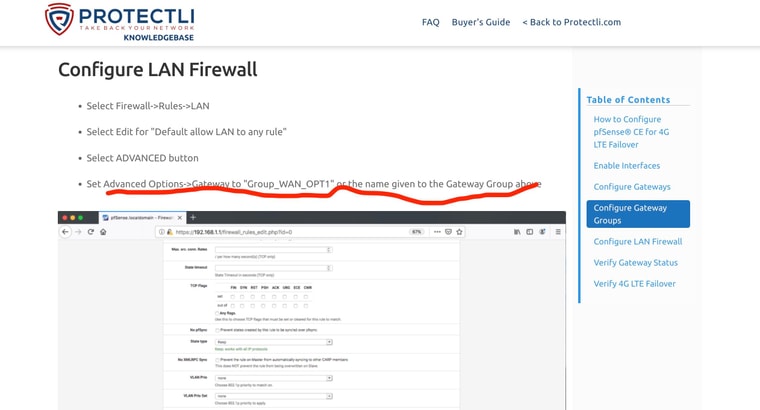
And my current setting in the General Setup DNS pageLastly I am attaching what I thought / hoped might work form a Protectli support page for setting up LTE modem on thier devices (in the Advanced Settings of the LAN Rules - forcing it to use the Failover GW
But this AM tested and it still failed -- AND had to completely reboot to get internet back up and going once the main WAN2 was plugged back in!
-
-
-
also btw, I am not sure what .179 is
it is not the device I'm testing form - but the network is large with probably more than 50 or 60 devices connectedThe routing table does not gicve the device a name (like many have) - it just gives a MAC address
-
Ok you have some conflicting settings there. You have DNS servers set with specific gateways and you also have the same DNS servers set as monitoring IPs for the gateways. Both those thing add static routes and must match to work correctly.
In your setup you don't need to set gateways on the configured DNS servers because they should work on either WAN and you're using a failover group as the default gateway. Additionally your are resolving directly so the DNS servers configured there are only used as a backup. However the conflicting static routes still breaks DNS for anything trying to use those servers directly. So remove the gateway settings from the DNS servers on the general setup page.
If you add a failover group to the pass rules on LAN you bypass rules for local traffic. That includes DNS traffic from LAN side clients to the LAN interface. Otherwise it will be forced out of the WAN and never reach Unbound in pfSense.