sipeed nanoKVM
-
Just wanted to share something cool I bought..
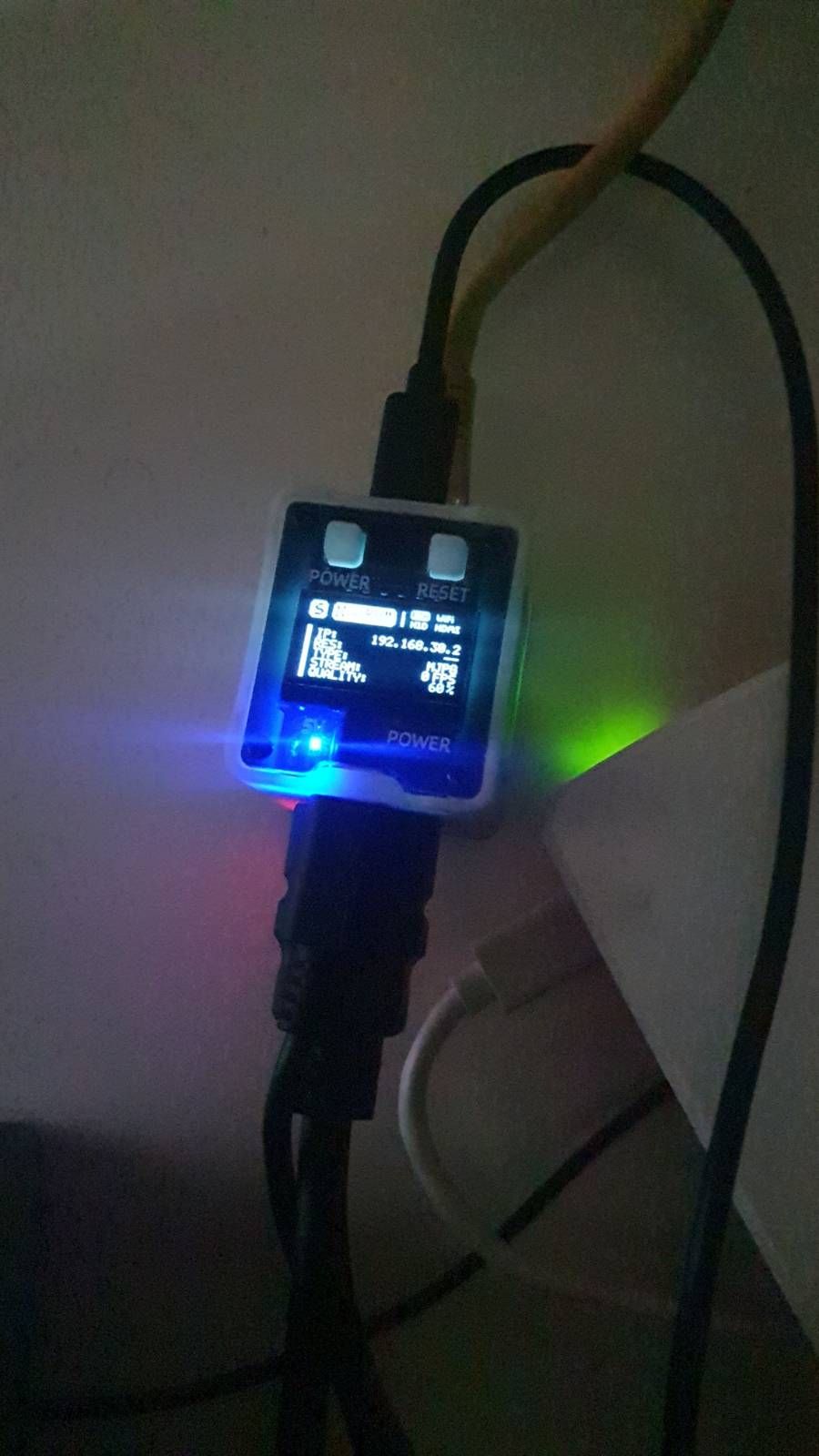
Sipeed nanoKVM, installed it yesterday..
Man, what a nice little thing to have, cheap and can save you a lot of headache.I can press the power button from the PC from anywhere connecting directly to it through Tailscale.
So, if you are behind a CGNAT, no problem, tailscale to it and press the power button.I did upload an .ISO image to the /data folder through SFTP and guess what ? You can mount that iso and boot from it !! Install OS just like that, from anywhere.
One thing to note is a problem in the design that backfeeding power from the PC-USB to the motherboard which may cause it to don't boot.
You can fix this by removing the 0 ohm resistor and replacing it with a diode, but I just modded the USB cable by putting an electrical tape in the PIN 1 of this USB cable and that is it, fixed.Little guy:
-
Ooo fun!

-
@stephenw10 said in sipeed nanoKVM:
Ooo fun!

A lot

Having fun since it arrived here, a grown up man with new toys hehe -
This post is deleted! -
@QuantumShade said in sipeed nanoKVM:
That sounds like an awesome little tool! The Sipeed nanoKVM seems like a game-changer, especially for remote management of PCs behind CGNAT. The ability to press the power button and even boot from an ISO remotely is incredibly useful for troubleshooting or installations without being physically present.
Indeed, and so cheap =)
The mod you made to fix the backfeeding issue is a clever workaround, though it's always nice when manufacturers take such potential problems into account from the start.
The product is in a beta stage, I guess that they will fix this in the final release.
Platforms like Howscribe often highlight how innovative hardware like this can save time and hassle for both hobbyists and professionals. It's great to see affordable, compact solutions making a big impact! Thanks for sharing your experience!
Really nice to see the market taking something that was expensive making really affordable.
There is lite version which is even cheaper, it doesn't come with the box or SD-card, but works the same way, so another option if you need to buy a bunch of those. -
@mcury geometry dash lite said in sipeed nanoKVM:
That sounds like an awesome little tool! The Sipeed nanoKVM seems like a game-changer, especially for remote management of PCs behind CGNAT. The ability to press the power button and even boot from an ISO remotely is incredibly useful for troubleshooting or installations without being physically present.
Indeed, and so cheap =)
How much does it cost?
-
Example : Amazon => search for "NanoKVM" ?
-
And a review of it (not all positiv):
https://www.youtube.com/watch?v=plJGZQ35Q6I -
@patient0 said in sipeed nanoKVM:
https://www.youtube.com/watch?v=plJGZQ35Q6I
Love the 'has a build microphone and all the software to support it'

-
The nanoKVM is deployed in a /30 DMZ and can only access the Internet, with no connectivity to other internal resources, and it is now opensource.
NTP connectivity is functional, but I configured it to use a known NTP server for reliability.
Tailscale attempts uPNP, which is normal, but it is blocked by the firewall. Tailscale is operational, with an ACL on the tailnet that blocks all outbound connections from the nanoKVM while allowing inbound connections to it. Tailscale uses a dedicated account exclusively for this device. I am not using port forwarding for Tailscale; instead, I configured static outbound NAT in pfSense and set randomizeClientPort in the JSON configuration.
DNS is configurable, and I am using 8.8.8.8 for the nanoKVM.
Connections to Sipeed are expected as this is how the device checks for updates.
Regarding a ping to the gateway, the comment "I don't like the gateway, so let's ping it" is unclear and seems irrelevant.
mDNS and IGMP are not an issue, as they are completely blocked. Note: I don’t believe mDNS or IGMP should be active on this device, and I’m unsure why they might be attempted or if Tailscale relies on these protocols for functionality.
They remain blocked as a precaution.In summary, like all network devices, the nanoKVM should be configured and operated with security best practices in mind.
-
@patient0 said in sipeed nanoKVM:
And a review of it (not all positiv):
https://www.youtube.com/watch?v=plJGZQ35Q6IThings have improved a bit, but I recommend Anyone who is considering purchasing one of these watch that video, and read through the associated Github issue thread. If you buy one of these, I would re-flash the unit prior to use.
As an alternative, for about the same price (ex shipping) there is JetKVM which is physically very nice. Here is apalrd's security video on JetKVM, which is also worth watching.
FWIW, I have no association with JetKVM other than as a user.