[SOLVED] Route pfsense itself over VPN.
-
@stephenw10 said in Route pfsense itself over VPN.:
You should be able to policy route traffic coming into the firewall from Tailscale the same as any other traffic. The only I could foresee there is that you cannot assign the tailscale interface. You would have to put the rules on tailscale group tab.
I created a rule on tailscale group, however there is no option to select tailscale subnets. Just tailscale networks. See bellow
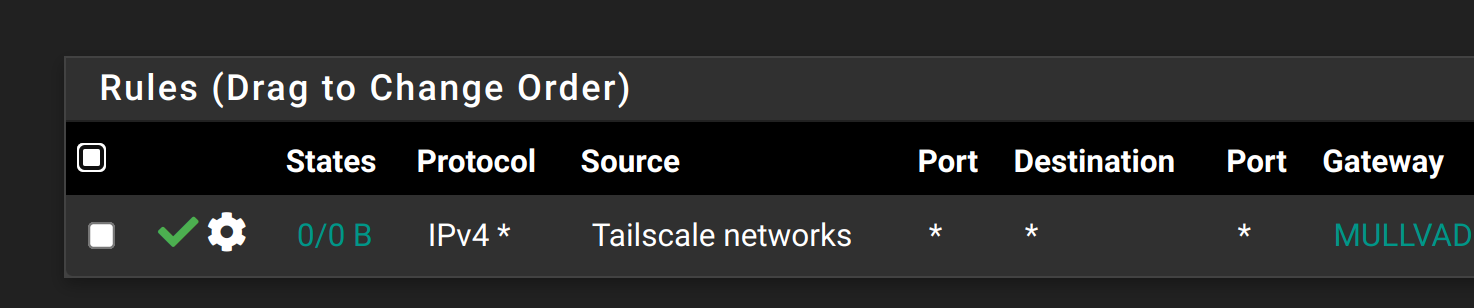
This firewall rule immediately produced an error bellow:
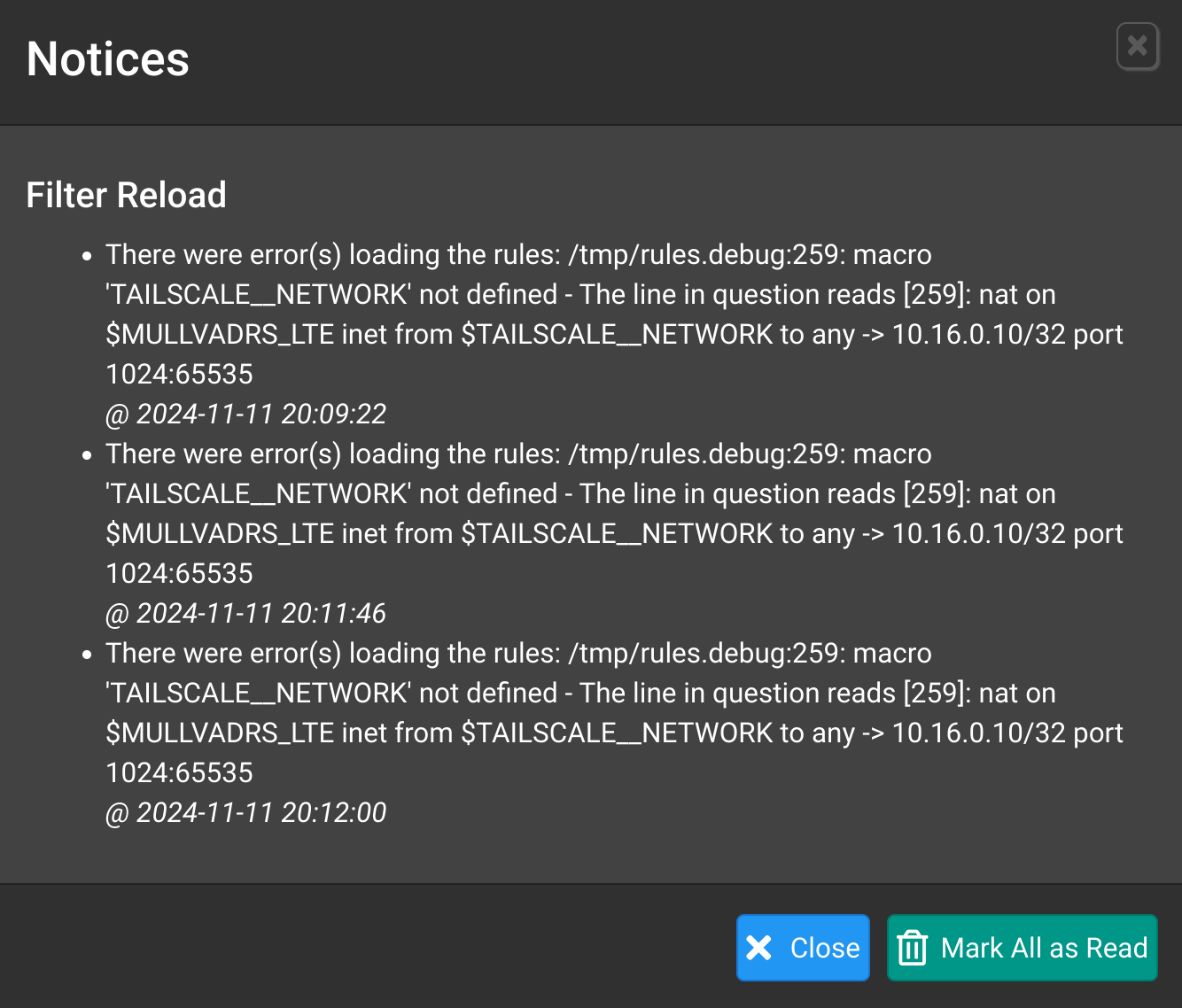
All traffic still goes to default gateway instead of VPN. Also, there is no option to choose tailscale subnets when creating a NAT rule either.
What did i do wrong ?
-
@nimrod said in Route pfsense itself over VPN.:
I created a rule on tailscale group, however there is no option to select tailscale subnets. Just tailscale networks. See bellow
Could be better use alias than
-
@Antibiotic said in Route pfsense itself over VPN.:
@nimrod said in Route pfsense itself over VPN.:
I created a rule on tailscale group, however there is no option to select tailscale subnets. Just tailscale networks. See bellow
Could be better use alias than
Alias for what ? There are no tailscale subnets available.
-
Create an alias containing the tailscale subnets you're routing. Then use that as source.
-
I created the alias with tailscale cidr ip. Used it as a source in a firewall rule on tailscale group, and the traffic is still going through my ISP instead of VPN. Here is the rule.
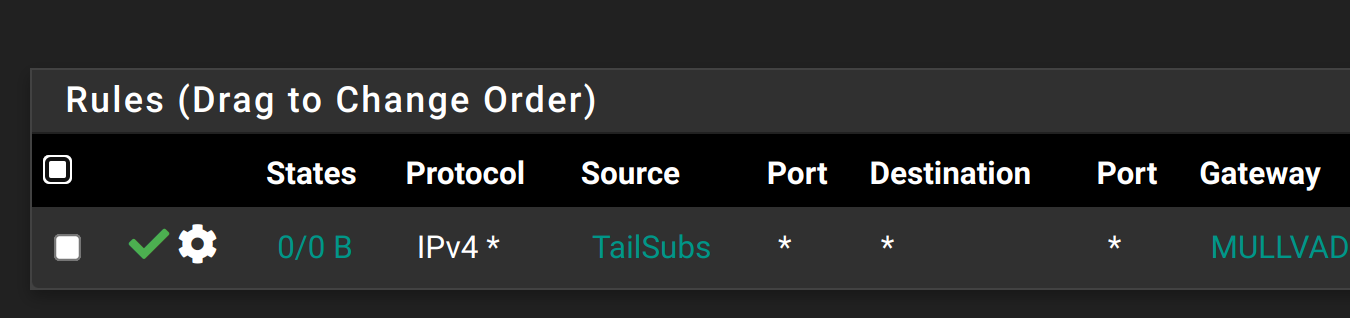
Tried reloading firewall rules and restarting tailscale service with no result. Tried using ip address of my phone instead of complete cidr block. Same thing.
The interesting part about this is that the DNS resolution is going through VPN which is what i want, but the rest of the traffic is still going through default gateway.
-
Hmm, no states shown on it so it's not matching and passing traffic for some reason.
Is it actually arriving with that source?
Is some other rule passing it?
-
@stephenw10 said in Route pfsense itself over VPN.:
Hmm, no states shown on it so it's not matching and passing traffic for some reason.
Is it actually arriving with that source?
Yes. Here is the screenshot from tailscale dashboard.
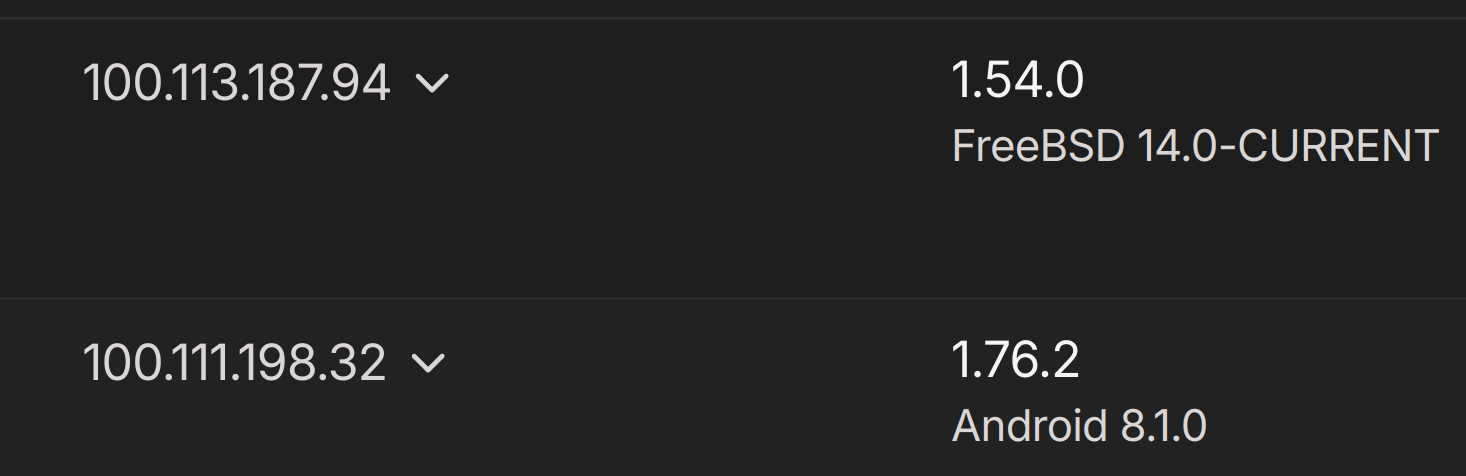
These ip addresses are also matching what the tailscale in pfsense is showing.
Is some other rule passing it?
There are no other rules anywhere, except tailscale group, where im routing 100.64.0.0/10 subnet.
-
Hmm, and the rule still shows no states or traffic on it?
Do you have a floating rule allowing that traffic perhaps?
You can check the states to see what rule opened it at the CLI:
pfctl -vvss
That will show all the states though which could a lot! -
@stephenw10 said in Route pfsense itself over VPN.:
Hmm, and the rule still shows no states or traffic on it?
Correct.
Do you have a floating rule allowing that traffic perhaps?
No.
You can check the states to see what rule opened it at the CLI:
pfctl -vvss
That will show all the states though which could a lot!pfctl -vvssis showing tons of states on all interfaces and vlans, so i refined my search withpfctl -vvss |grep 100.133and thenpfctl -vvss |grep 100.111and thenpfctl -vvss |grep 100.64None of these searches returned anything even if i execute them while the phone is connected to tailscale and receiving/sending traffic. If i use known non tailscale ip address, its shown clearly and then i can find it in the list along with the firewall id. But tailscale ips return nothing.
-
Try sending some traffic from a client to some unique IP and check the states created by that. You could be seeing it post NAT.
-
@stephenw10 said in Route pfsense itself over VPN.:
Try sending some traffic from a client to some unique IP and check the states created by that. You could be seeing it post NAT.
This is getting very strange now.
First i initiated continuous rtsp traffic from my PC to local camera and then i run
pfctl -vvssto check the states and i could clearly see this:all tcp 20.20.1.1:19791 (10.1.1.100:57738) -> 20.20.1.236:8083 ESTABLISHED:ESTABLISHED [222663977 + 2147156224] wscale 7 [2738703565 + 4293657088] wscale 7 age 00:01:20, expires in 23:59:46, 25:55 pkts, 2212:68118 bytes, rule 122, allow-opts, log id: f013346700000000 creatorid: cd852d8c origif: igb5.2510.1.1.100 - pc
20.20..1.1 - pfsense camera interface
20.20.1.236 - cameraThen i did the same from my phone via tailscale (tailscale is configured to broadcast 20.20.1.0/24 subnet) and this is what i see when i run
pfctl -vvssagain:all tcp 20.20.1.1:1996 -> 20.20.1.236 :8083 ESTABLISHED:ESTABLISHED [2330702467 + 2147156224] wscale 7 [599643748 + 65792] wscale 7 age 00:01:10, expires in 23:59:52, 26:22 pkts, 3121:14535 bytes, rule 122, allow-opts, log id: 0a14346700000000 creatorid: cd852d8c origif: igb5.25There is no tailscale or my phone ip anywhere in the logs when access to camera is initiated via tailscale.
-
Hmm, that's odd. Let me do some digging here. What pfSense version is this?
-
@stephenw10 said in Route pfsense itself over VPN.:
Hmm, that's odd. Let me do some digging here. What pfSense version is this?
Its 2.7.2 CE with all the patches applied using system patches pacakage.
-
Mmm, OK, clearly been too ling since I played with Tailscale.
 That's the expected behaviour.
That's the expected behaviour.See: https://www.youtube.com/watch?v=Fg_jIPVcioY&t=1240s
Which makes it very inconvenient as there's no way to policy route the traffic as far as I know. The only way to route that traffic would be to set the default route to the VPN. You could then policy route traffic other traffic via the WAN but pfSense itself would always use the VPN.
-
@stephenw10 said in Route pfsense itself over VPN.:
Mmm, OK, clearly been too ling since I played with Tailscale.
 That's the expected behaviour.
That's the expected behaviour.You have been helpful Stephen no matter the outcome. Much appreciated.
This makes sense now.
Which makes it very inconvenient as there's no way to policy route the traffic as far as I know. The only way to route that traffic would be to set the default route to the VPN. You could then policy route traffic other traffic via the WAN but pfSense itself would always use the VPN.
Thats how im using it currently, but the issue is that other openvpn tunnels that i use are failing to connect when pfsense is rebooted, and then i need to manually restart all openvpn services including the one selected as the default wan. Once thats done, everything is working perfectly, including the tailscale traffic.
-
You could set static routes for those VPN endpoints via the WAN gateway.
-
@stephenw10 said in Route pfsense itself over VPN.:
You could set static routes for those VPN endpoints via the WAN gateway.
Im sorry, im talking about openvpn clients in pfsense. They fail to connect to mullvad vpn server when rebooted. Can a static route help with that, and if so, how?
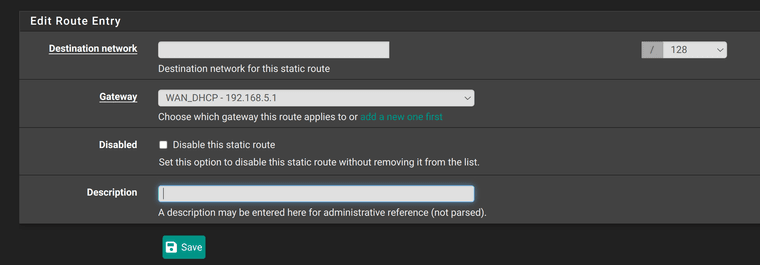
Not really sure what should i set in Destination network.
-
Put in the IP address of the VPN server the client connects to. pfSense uses the system routing table to determine how to route outgoing connections. Adding a static route to the VPN server will route it via the WAN.
-
@stephenw10 said in Route pfsense itself over VPN.:
Put in the IP address of the VPN server the client connects to. pfSense uses the system routing table to determine how to route outgoing connections. Adding a static route to the VPN server will route it via the WAN.
I have 3 openvpn clients in pfsense. Should i create 3 static routes ? One for each vpn server ?
-
Yes, add static routes to anything that needs to use the WAN gateway.