openvpn client not connecting
-
In my broadband router, there is no option I can see like any source ip to any destination ip in the port forwarding section.
-
@Cleetus-Antony
I expect, that you can at least set the routrs WAN address as destination.
Any for the redirect target might not be possible. -
@Cleetus-Antony said in openvpn client not connecting:
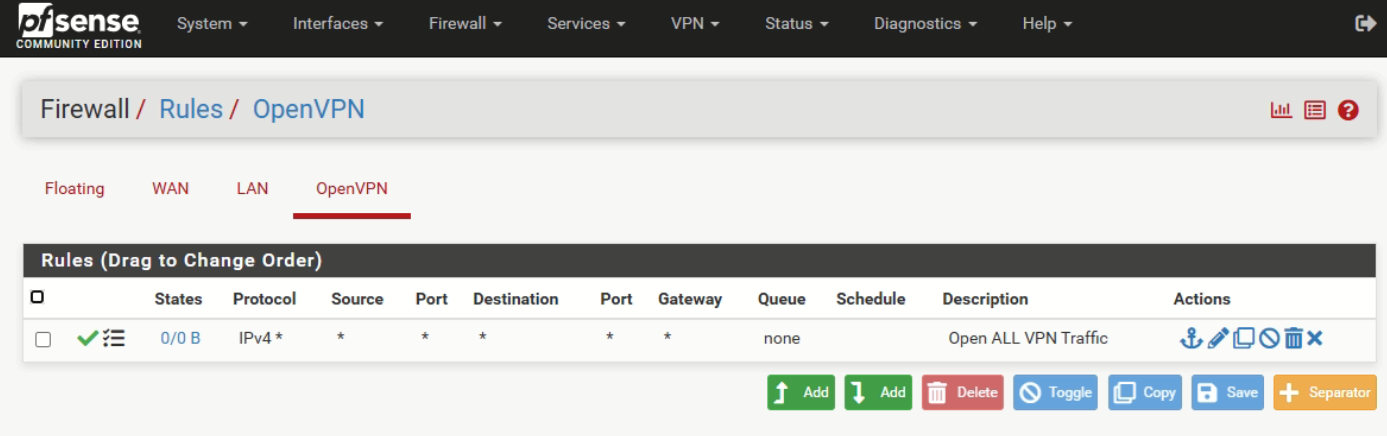
pfsense log 11.11.24.txt
That's your OpenVPN server starting, and it 'binds' to 192.168.10.10, your WAN IP, using port 1194, protocol UDP.
No trace of any incoming connection !
Which is the same info as :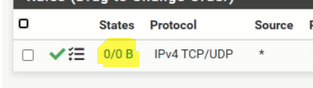
I've the same startup sequence :
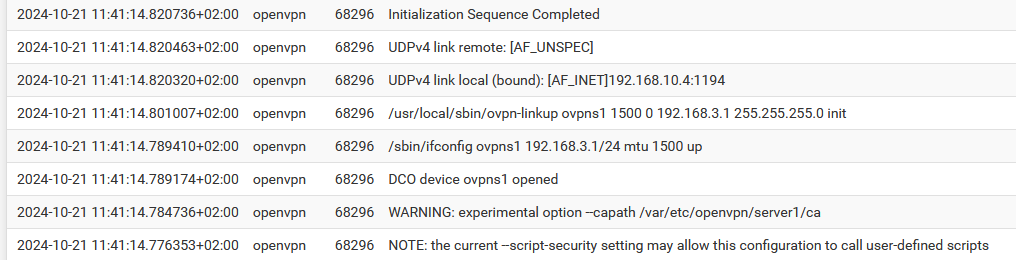
Where 192.168.10.4 is my WAN IP. I'm also using UDP and 1194, which is default.
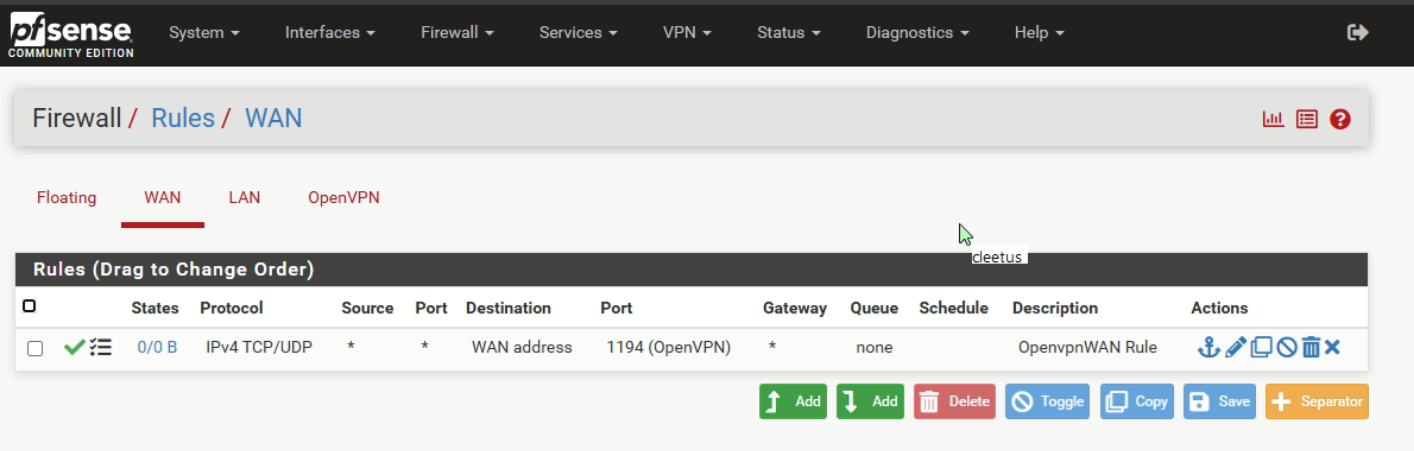
My pfSense OpenVPN server WAN interface firewall rule :
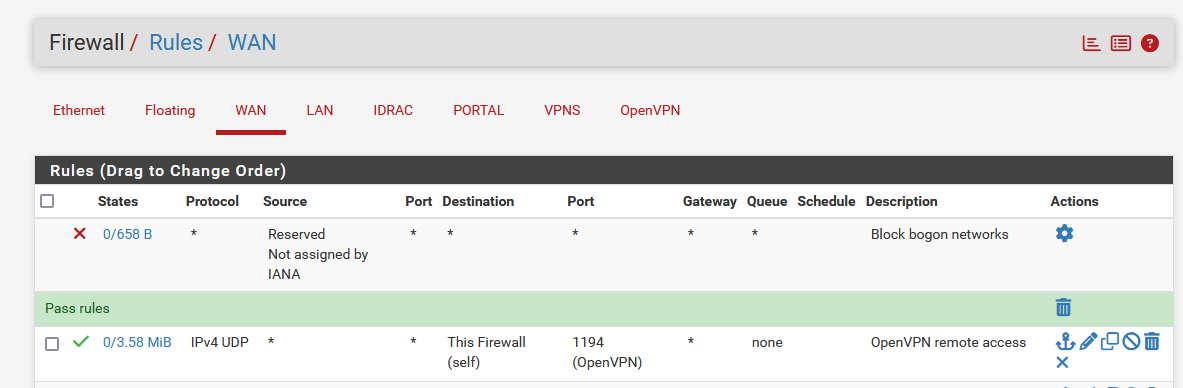
and because 192.168.10.4 is RFC1918 = I have an upstream ISP router, so I had to place a NAT rule also in this router :
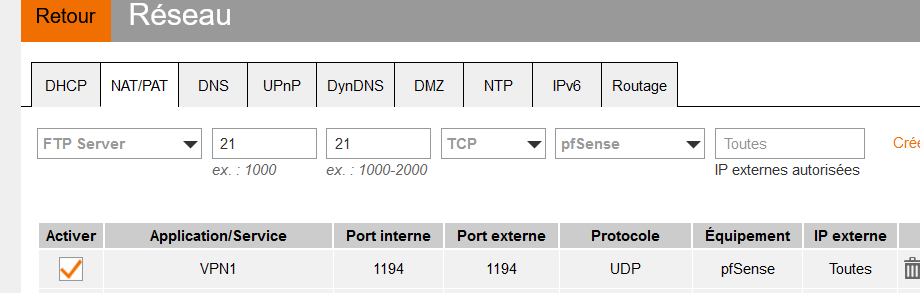
The Internal and external port number are both '1194'.
The protocol is UDP
The internal IP (= my WAN IP pfSense) is 192.168.10.4 - but my router uses his internal 'DNS' name for it, the field 'Equipement'.
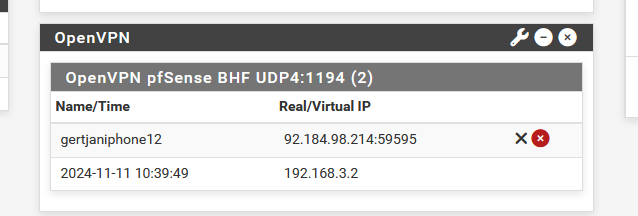
The external IP (IP Externe) is set to "All" (or "Toutes" in French).When I connect to my VPN with my phone I see this is my VPN logs (read from bottom to top) :
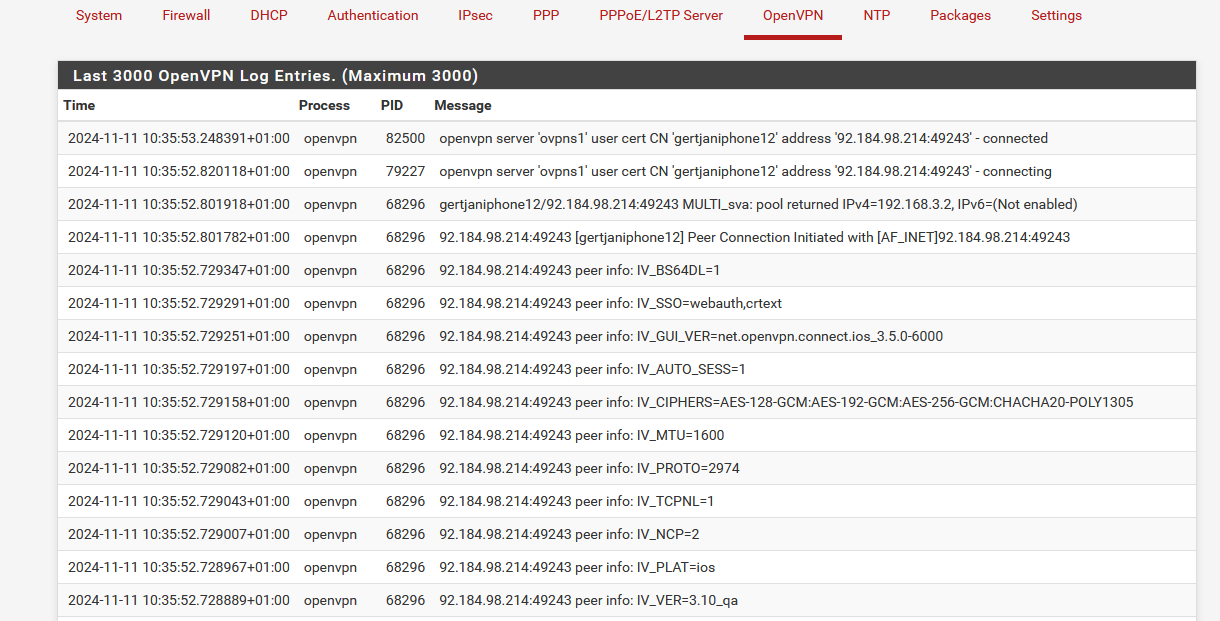
where 92.184.98.214 is the IP of my phone (5G connected, not Wifi !!! ( !!! ))
My phone got the 192.168.3.2 VPN network IP.These start going up fast now :
as traffic reaching and entering my pfSense, handled by the listing OpenVPN server.
On the pfSense dash board I see :
-
Thank you for the well explained reply. Appreciate it.
For some reason, my ISP router doesnt have the port forwarding explicitly for ports only(1194 to 1194). IP fields are mandatory so I am not getting any to any option.
@viragomann
For setting the destination as WAN IP of ISP RTR, the same is on ppoe which changes more often rt ? -
@Cleetus-Antony said in openvpn client not connecting:
doesnt have the port forwarding explicitly for ports only(1194 to 1194). IP fields are mandatory so I am not getting any to any option
"Only ports" can't exist.
After all, a 'any' IP to 'any' IP doesn't make sense.It's nearly always "from any Internet IP possible" (as you don't know what IP you will be using when your out there using some random IPv4 (so = "any")) but the redirection has to go to a known IP : the pfSense WAN IP - and not some other "random LAN IP" (where LAN IP is an IP on your ISP LAN network, pfSense is using one of them, 192.168.10.10 - redirecting to for example 192.168.10.11 doesn't make sense, it has to be 192.168.10.10)
-
@Cleetus-Antony said in openvpn client not connecting:
For setting the destination as WAN IP of ISP RTR, the same is on ppoe which changes more often rt ?
There should be an alias for the random WAN IP, I think.
I noted, that your router has a DMZ option. Maybe it also works if you state the pfSense WAN IP as DMZ.
Normally this should forward any incoming traffic then. -
@viragomann said in openvpn client not connecting:
Normally this should forward any incoming traffic then.

@Cleetus-Antony
This implies that you need a 'good' firewall after your ISP device ^^
And that's the case : you use a pfSense
I tend to see the "DMZ" often present in ISP boxes as a "no-brains super NAT rule" : Address Translate all in coming connection (ICMP, UDP, TCP, whatever) to the designated IP, which will be the pfSense WAN IP.
This will surely do the trick. -
Does all this means that my ISP router is not functioning well in terms of port forwarding to reach the openvpn traffic to pfsense. ? Do I need a replacement ? My current brand is GX Earth-4222 Router
-
@Cleetus-Antony
This rather means, that setting a pfSense as DMZ on the ISP router is the common way to configure it, when you intend to run services in your network.This forward all incoming traffic to pfSense and you can control it there, which gives you better and more options.
-
@viragomann
I configured the DMZ section of the ISP router with the destination of WAN IP of the pfsense and it didnt make any difference. -
@Cleetus-Antony
If the WAN rule on pfSense doesn't show any hit there is obviously nothing forwarded.
So most probably the problem is in front of pfSense and there is not much we can help you.Does the router provide diagnostic tools or logs to help investigating to issue?
Maybe you can sniff the traffic on its WAN to see, if there are even OpenVPN packets arriving. -
@Cleetus-Antony said in openvpn client not connecting:
I configured the DMZ section of the ISP router with the destination of WAN IP of the pfsense and it didnt make any difference.
To possible test : ping.
get and note your WAN ISP IP.
Get a phone app that can send out pings (remember to switch of Wifi !! No VPN activated neither !!). Or go to to your neighbor.
Ping your WAN ISP IP.Before you start pinging, set up a WAN ping sniffer :
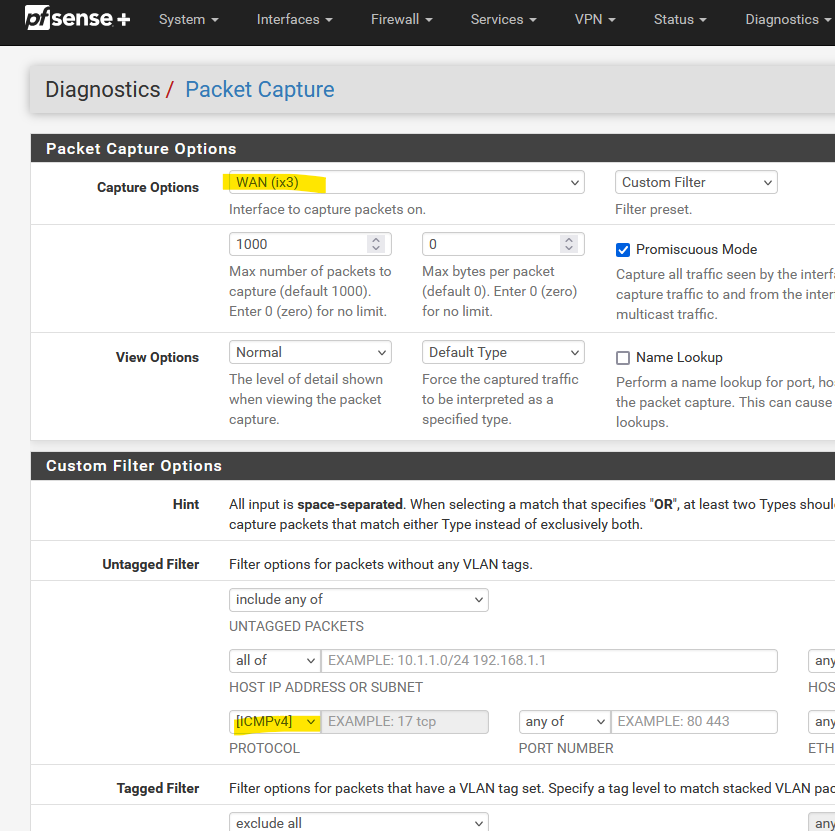
and hit Start at the bottom.
If all goes well, you'll see lines like this :
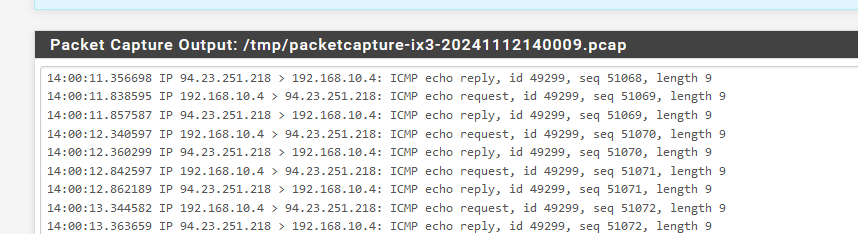
Nothing comes in ?
That means nothing reached the WAN interface.@Cleetus-Antony said in openvpn client not connecting:
Does all this means that my ISP router is not functioning well in terms of port forwarding to reach the openvpn traffic to pfsense. ? Do I need a replacement ? My current brand is GX Earth-4222 Router
Your ISP router image shows me all the needed for a port forward (NAT or/and PAT)
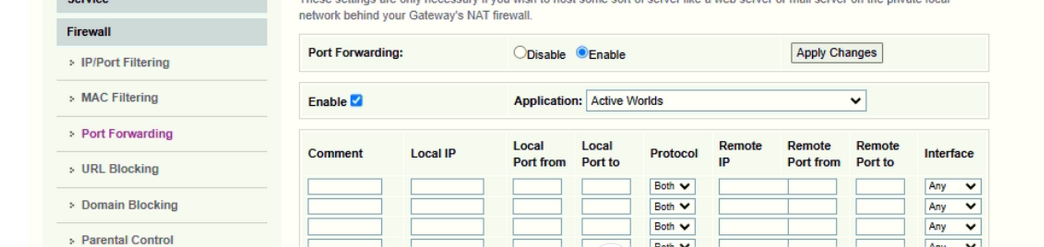
What you need : go visit the ISP FAQ and documents about your router : how to implement a NAT or port forward rule.
Putting a VPN port forward in place is since 2019 considered 'common knowledge' and I really believe your router is capable of doing that. -
@Gertjan
Will try and update -
Like : router GX Earth-4222 port forward ?!
If like the funny accent : a movie for you https://youtu.be/ZsfrGELbJbs?si=OTupRFVoPNNkrK5J
-
I can see hits now in openVPN for WAN interface. But not connecting.
Attached the logs. Please have a look.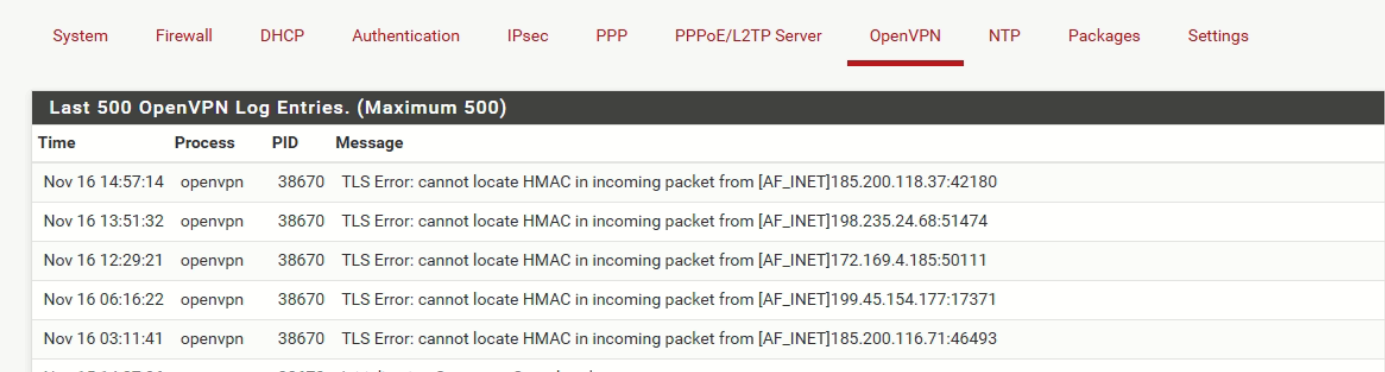
-
Ok, progress !
Connections attempts are coming in now.Question : one of these is the IP you were using with your client OpenVPN device :
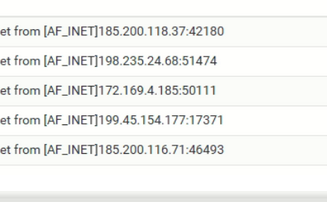
?
-
@Gertjan
infact, I do try from my office PC thru office wifi only. My IP is different than the listed ones. I wonder how this IPs r showing as origin. -
@Cleetus-Antony said in openvpn client not connecting:
I wonder how this IPs r showing as origin.
You are aware that every Internet device can access any IP ?
You can go wherever you want, so can everybody else.
What you are seeing are 'random' IP addresses that 'try' to connect to you WAN IP, protocol UDP, port 1194. They 'test' your OpenVPN.
This looks scary if you've never seen this before, but don't worry, OpenVPN was created to handle this situation. You are probably using certificates as an access control mechanism :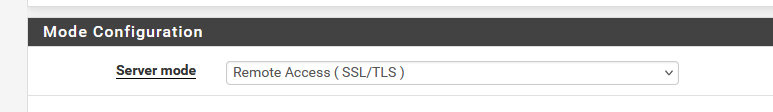
you can see these certificates - you saw them in the ovpn file you've exported to your client - and it's impossible to guess these.
You Office PC is a PC that uses the Internet to go to you OpenVPN? right ?
This Office PC should not be part of your pfSense LAN network.Normally, to test, you install this app on your phone (an iOS also exist) and you use your phone with the Wifi de activated. Use the data of your phone provider to connect to your ISP WAN IP.
You know it works, as connections are already reaching your OpenVPN server ^^ -
Ya I thought that "may" be some attack attempts. BUT:-
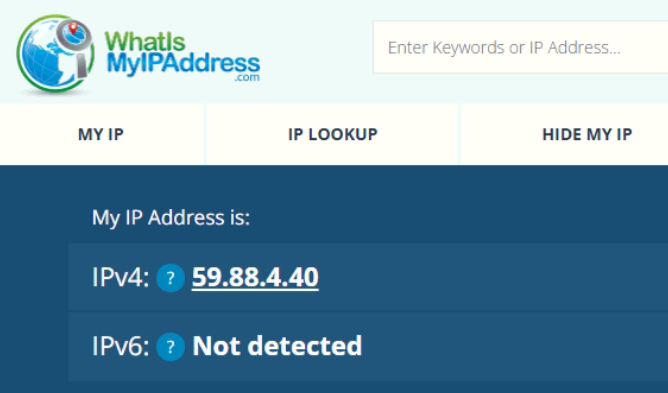
I am in UAE now and my home is in India where pfsense is located.
My home IP is 59.88.4.40
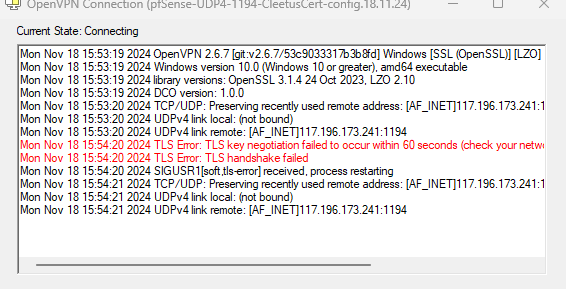
but openvpn client from my office pc is trying to connect to 117.196.173.241:1194.I am using dyndns at my pfsense end. As per my research this ip 117.196.173.241 doesnt belong to my dyndns.
This makes me kind of total confusions.
I tried both User auth as well as TLS modes.
Attached the latest openvpn log from pfsense. Plz chk if u can see anything interesting ?
-
@Cleetus-Antony said in openvpn client not connecting:
My home IP is 59.88.4.xx
but openvpn client from my office pc is trying to connect to 117.196.173.241:1194.That makes no sense.
If you know your that the IP you need to contact is is 59.88.4.xx then why would you (have it) use 117.196.a.b ?
DynDNS issues ? Who cares. Handle that one later.
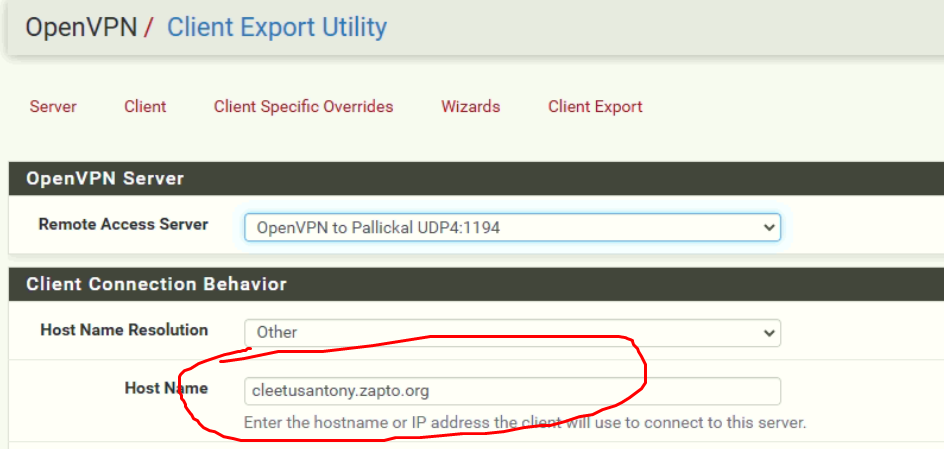
For now, set up the IP like :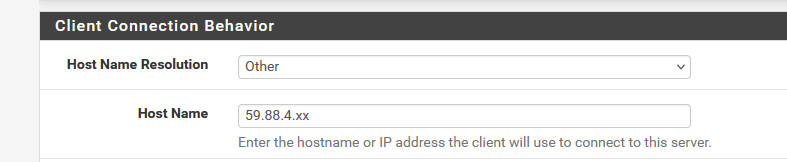
export the Client OpenVPN config.
Import the config in the client.@Cleetus-Antony said in openvpn client not connecting:
I tried both User auth as well as TLS modes.
Starting testing the user auth possibilities when you are able to reach 59.88.4.xx