openvpn client not connecting
-
@Cleetus-Antony
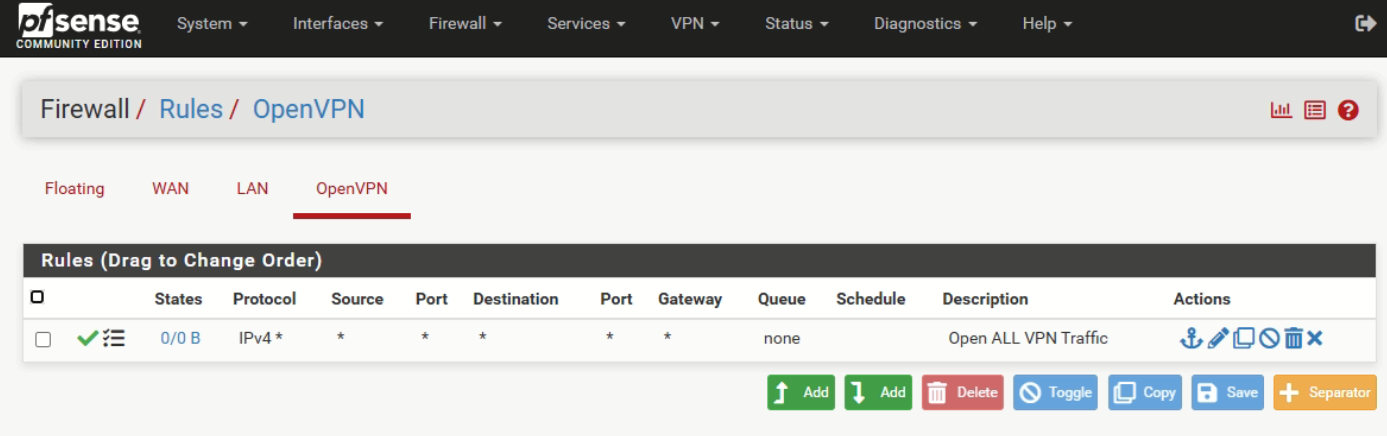
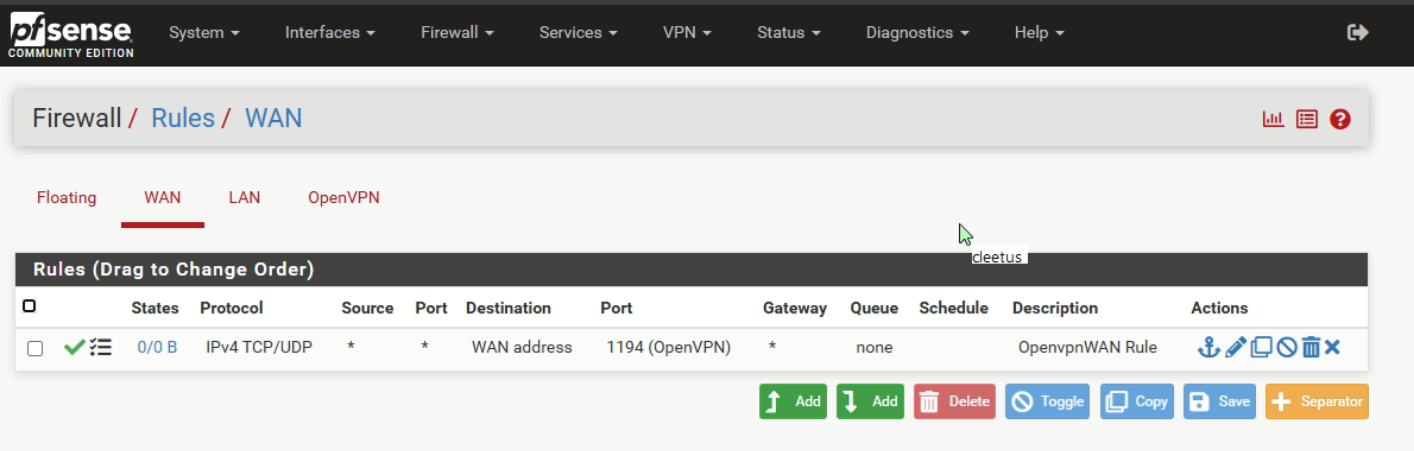
If the WAN rule on pfSense doesn't show any hit there is obviously nothing forwarded.
So most probably the problem is in front of pfSense and there is not much we can help you.Does the router provide diagnostic tools or logs to help investigating to issue?
Maybe you can sniff the traffic on its WAN to see, if there are even OpenVPN packets arriving. -
@Cleetus-Antony said in openvpn client not connecting:
I configured the DMZ section of the ISP router with the destination of WAN IP of the pfsense and it didnt make any difference.
To possible test : ping.
get and note your WAN ISP IP.
Get a phone app that can send out pings (remember to switch of Wifi !! No VPN activated neither !!). Or go to to your neighbor.
Ping your WAN ISP IP.Before you start pinging, set up a WAN ping sniffer :
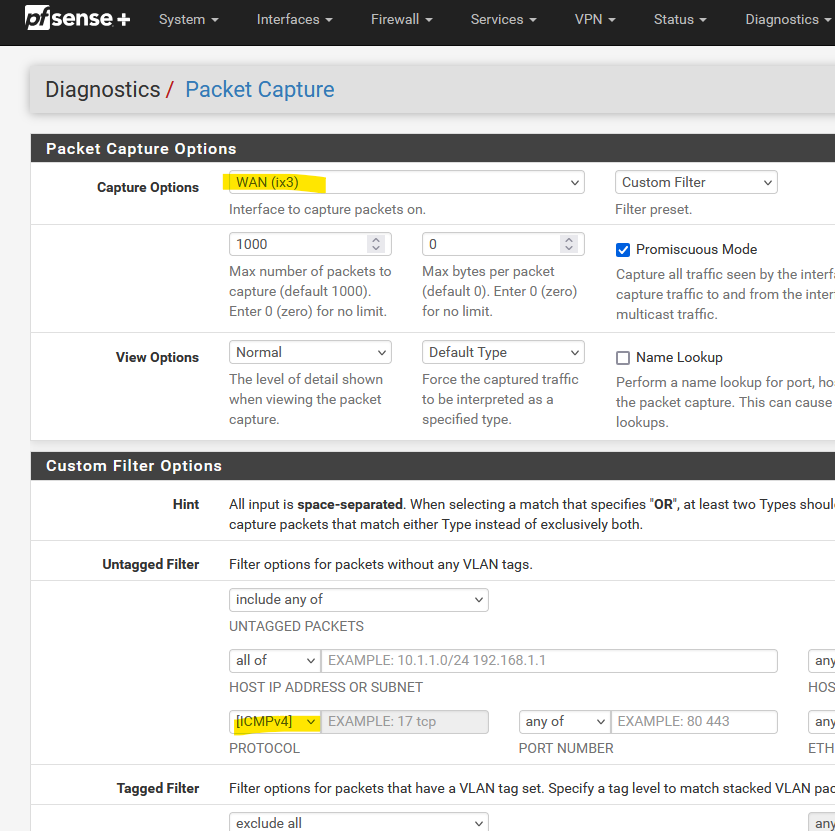
and hit Start at the bottom.
If all goes well, you'll see lines like this :
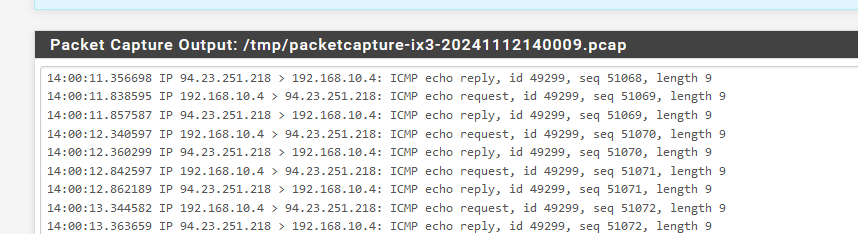
Nothing comes in ?
That means nothing reached the WAN interface.@Cleetus-Antony said in openvpn client not connecting:
Does all this means that my ISP router is not functioning well in terms of port forwarding to reach the openvpn traffic to pfsense. ? Do I need a replacement ? My current brand is GX Earth-4222 Router
Your ISP router image shows me all the needed for a port forward (NAT or/and PAT)
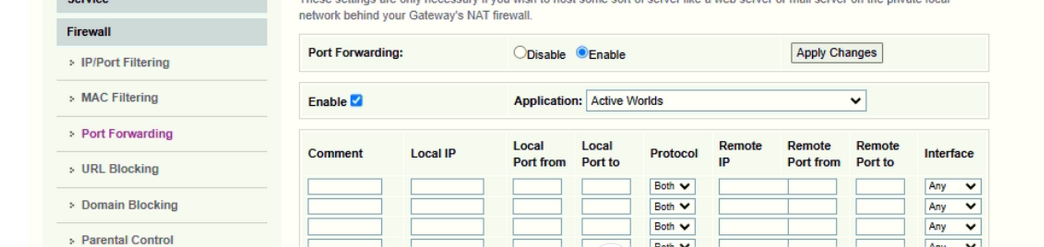
What you need : go visit the ISP FAQ and documents about your router : how to implement a NAT or port forward rule.
Putting a VPN port forward in place is since 2019 considered 'common knowledge' and I really believe your router is capable of doing that. -
@Gertjan
Will try and update -
Like : router GX Earth-4222 port forward ?!
If like the funny accent : a movie for you https://youtu.be/ZsfrGELbJbs?si=OTupRFVoPNNkrK5J
-
I can see hits now in openVPN for WAN interface. But not connecting.
Attached the logs. Please have a look.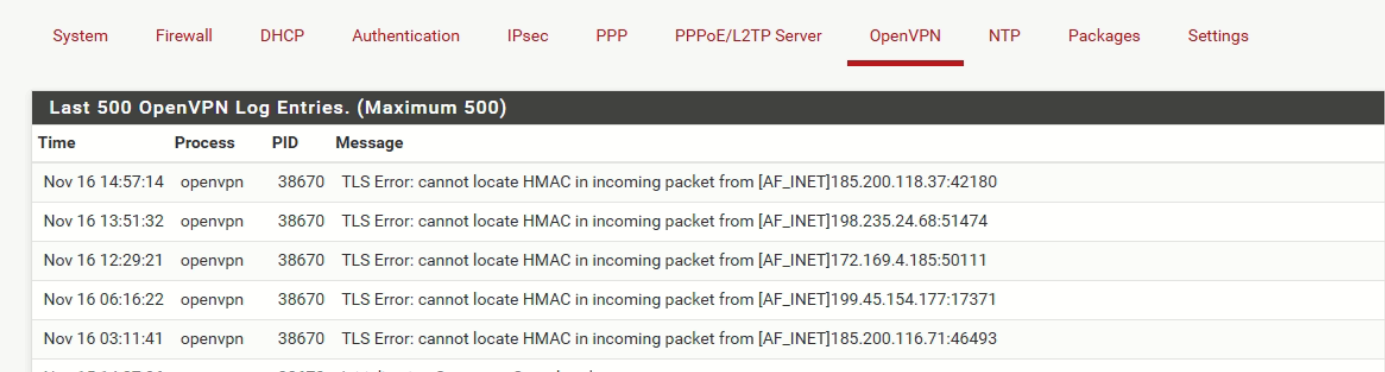
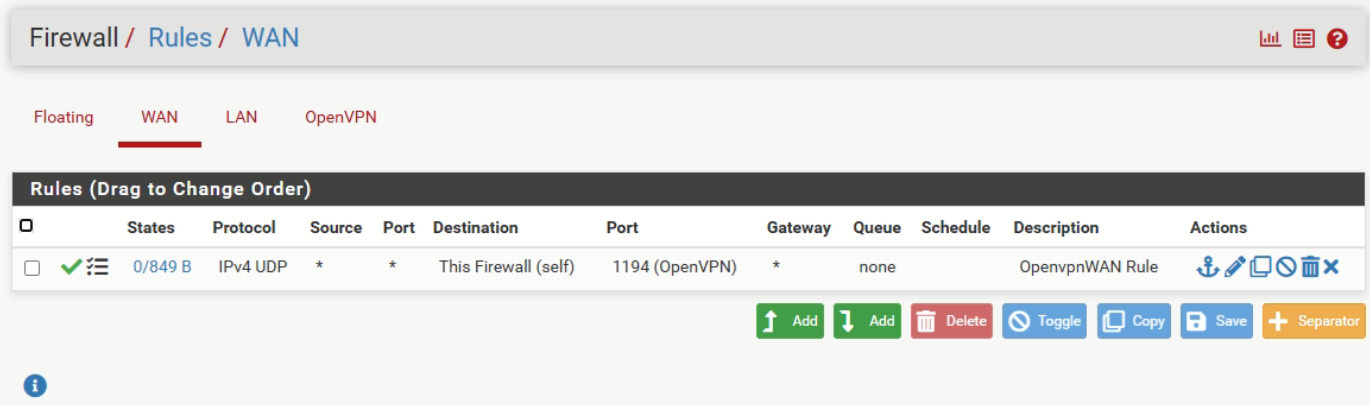
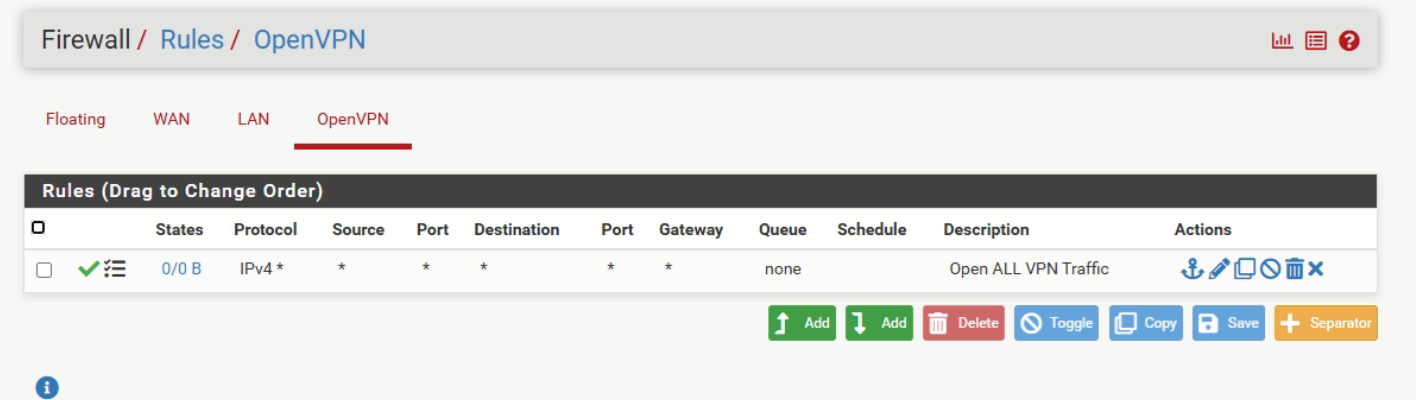
-
Ok, progress !
Connections attempts are coming in now.Question : one of these is the IP you were using with your client OpenVPN device :
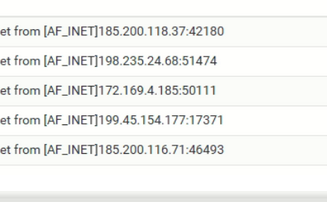
?
-
@Gertjan
infact, I do try from my office PC thru office wifi only. My IP is different than the listed ones. I wonder how this IPs r showing as origin. -
@Cleetus-Antony said in openvpn client not connecting:
I wonder how this IPs r showing as origin.
You are aware that every Internet device can access any IP ?
You can go wherever you want, so can everybody else.
What you are seeing are 'random' IP addresses that 'try' to connect to you WAN IP, protocol UDP, port 1194. They 'test' your OpenVPN.
This looks scary if you've never seen this before, but don't worry, OpenVPN was created to handle this situation. You are probably using certificates as an access control mechanism :
you can see these certificates - you saw them in the ovpn file you've exported to your client - and it's impossible to guess these.
You Office PC is a PC that uses the Internet to go to you OpenVPN? right ?
This Office PC should not be part of your pfSense LAN network.Normally, to test, you install this app on your phone (an iOS also exist) and you use your phone with the Wifi de activated. Use the data of your phone provider to connect to your ISP WAN IP.
You know it works, as connections are already reaching your OpenVPN server ^^ -
Ya I thought that "may" be some attack attempts. BUT:-
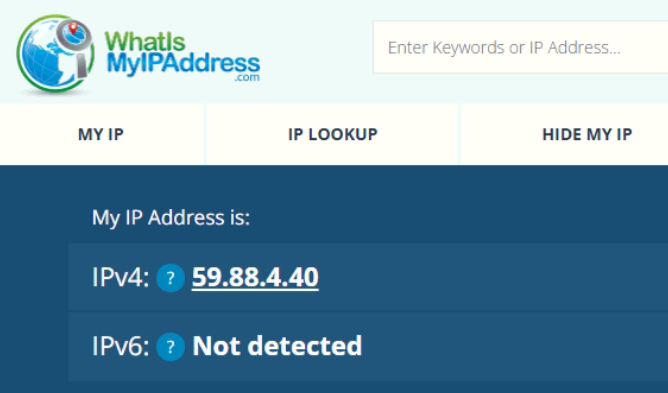
I am in UAE now and my home is in India where pfsense is located.
My home IP is 59.88.4.40
but openvpn client from my office pc is trying to connect to 117.196.173.241:1194.I am using dyndns at my pfsense end. As per my research this ip 117.196.173.241 doesnt belong to my dyndns.
This makes me kind of total confusions.
I tried both User auth as well as TLS modes.
Attached the latest openvpn log from pfsense. Plz chk if u can see anything interesting ?
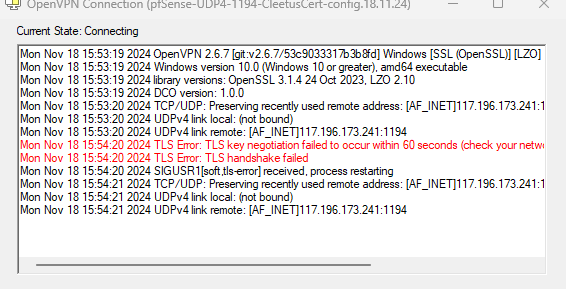
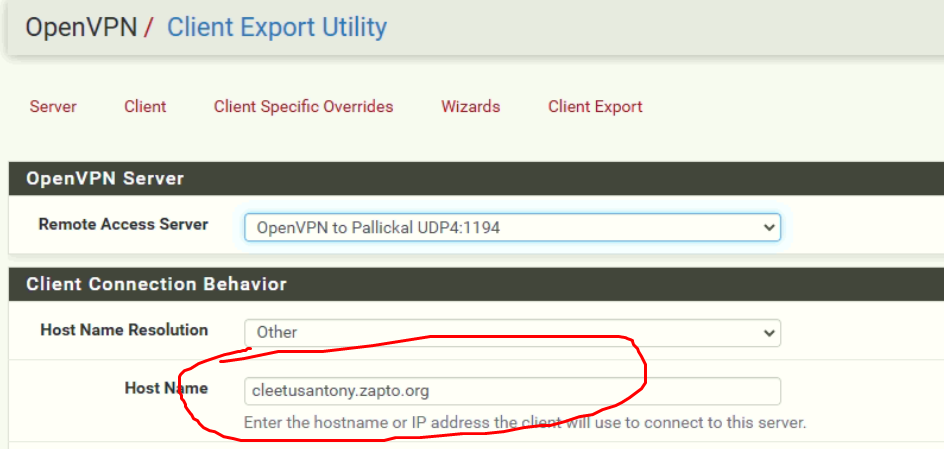
-
@Cleetus-Antony said in openvpn client not connecting:
My home IP is 59.88.4.xx
but openvpn client from my office pc is trying to connect to 117.196.173.241:1194.That makes no sense.
If you know your that the IP you need to contact is is 59.88.4.xx then why would you (have it) use 117.196.a.b ?
DynDNS issues ? Who cares. Handle that one later.
For now, set up the IP like :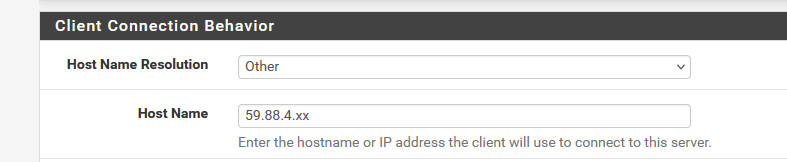
export the Client OpenVPN config.
Import the config in the client.@Cleetus-Antony said in openvpn client not connecting:
I tried both User auth as well as TLS modes.
Starting testing the user auth possibilities when you are able to reach 59.88.4.xx
-
@Gertjan
Sorry that I couldn't respond to u after the last talk.I managed connect the opnvpn from my work place to home pfsense server.
But I my open vpn adaptor is not getting gateway and dns.Please revert.
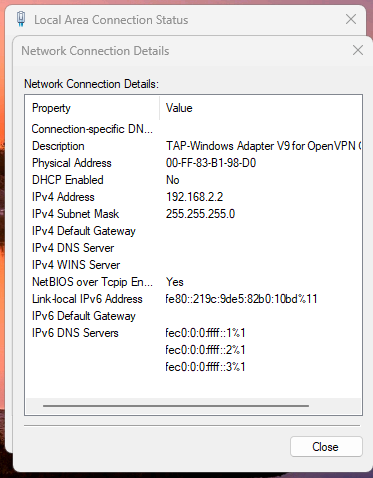
-
-
Yes sir, Thats what the adaptor is getting my tunnel network IP from 192.168.2.0 series when connected.
-
@Gertjan
I set the Device Mode in server configuration as "tun" only no "tap" . So I shudnt get TAP adaptor in my connected clients rt ?Is that matters for not getting GW and DNS in client ?
-
@Cleetus-Antony
When you set up a OpenVPN server using TUN, you have to create a corresponding (redo) your OpenVPN client side accordingly.
Actually, every time you change something on the server side, you have to redo your client config also.Normally, you export the openvon config on pfSense to an opvn file, and you import this file on your OpenVPN client.
-
@Gertjan
Thank u. But my server conf was "tun" only since starting not tap. Hav any clue why I am not getting GW and DNS ? -
@Cleetus-Antony said in openvpn client not connecting:
But my server conf was "tun" only since starting not tap
Your client side ( ? ) as showing a tap connection.
-
@Gertjan
Yes sir, Thats what bit confusing. Please let me know if u need to see any particular configuration in server, I can show the screenshot. My "Device mode" conf is tun only. -
@Cleetus-Antony
Did you even provide a DNS server in the OpenVPN server settings?A Default Gateway is not meant to be set on the VPN interface, as far as I know. There is no need for it.
What's your actual issue now?
-
@viragomann
I assigned dns in server settings and client getting the same.
But issue is client is not getting internet.
I even added redirect-gateway def1 option also.My conf file is as below:-
dev tun
persist-tun
persist-key
data-ciphers AES-256-GCM:AES-128-GCM:CHACHA20-POLY1305:AES-256-CBC
data-ciphers-fallback AES-256-CBC
auth SHA256
tls-client
client
resolv-retry infinite
remote pallickal.duckdns.org 1194 udp4
setenv opt block-outside-dns
nobind
auth-user-pass
remote-cert-tls server
explicit-exit-notify
redirect-gateway def1<ca>
-----BEGIN CERTIFICATE-----
MIIECDCCAvCgAwIBAgIIe52lR6T8wlowDQYJKoZIhvcNAQELBQAwXDETMBEGA1UE
AxQKT3BlbnZwbl9DQTELMAkGA1UEBhMCSU4xDzANBgNVBAgTBktlcmFsYTESMBAG
A1UEBxMJQWxhcHB1emhhMRMwEQYDVQQKEwpwYWxsaWNrYW5zMB4XDTI0MDYyNDA3
MTU1NFoXDTM0MDYyMjA3MTU1NFowXDETMBEGA1UEAxQKT3BlbnZwbl9DQTELMAkG
A1UEBhMCSU4xDzANBgNVBAgTBktlcmFsYTESMBAGA1UEBxMJQWxhcHB1emhhMRMw
EQYDVQQKEwpwYWxsaWNrYW5zMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKC
AQEA+LbeHSX8vVylxArGi/TI5EZaoRqznasUZxXs2OdPSGtQ8k5sNS8IoRejyt+Y
FV1ujYY4gjSmnsZhRxcSAWVG1/amGUrK5HOGkAEaUcXQB5+T6KaLp4c3RRBwrBSD
IKmO9fuuKlTLPxt4m87TF9SejbQI47uVX82e8ff8jxxh6u8EC3WzhF25Gx7MbkjL
KuHrRohehyq97Nl+rWmLafDSrCyEktoemb6rSp1+sabHwiwEuZzDC4q5Td4gA/Jr
o/08jbHqiO1MC3FdLcLxslgL2tyc5XmNmE9GfBq1dYw9QodTqND29r0EaYTnpURc
HskHBftm7Ux2iIiVTspvmTGjGQIDAQABo4HNMIHKMB0GA1UdDgQWBBTf7XNYM7C8
ip1ZRfHinjhO6Ysi3zCBjQYDVR0jBIGFMIGCgBTf7XNYM7C8ip1ZRfHinjhO6Ysi
36FgpF4wXDETMBEGA1UEAxQKT3BlbnZwbl9DQTELMAkGA1UEBhMCSU4xDzANBgNV
BAgTBktlcmFsYTESMBAGA1UEBxMJQWxhcHB1emhhMRMwEQYDVQQKEwpwYWxsaWNr
YW5zggh7naVHpPzCWjAMBgNVHRMEBTADAQH/MAsGA1UdDwQEAwIBBjANBgkqhkiG
9w0BAQsFAAOCAQEA8TRPbTAteXxGFWs3Q/Z/29mcTFwp/GHaPDmQzaBaMQEqNAcG
0tRQm9kLmn+55oJ/liCj+RUBcdLMWvQvKEi/DiL1iBeujW5PpkyWMVV+QjWCYcKh
vu5TEmkgdzyTcYaftxg9861np/mldyVJclg7FUOOgtxjlMhpYBEbzaESJoUHZMbN
tMdY1EdIRsMLNt2yqyIV/3wQ+9EQ2MvbFx3gj/OSNPXMkkF6fX8PId/iSi3MFx2L
bskELM7t/R0vpuZXRLKuvbrGZJL315mhzliRbXWJIhzezJfTZIXfTsk+s1wOHgWw
RxBR4Y9rsipH9zEhPk/fe9WK5DaMqxF6amjqgg==
-----END CERTIFICATE-----
</ca>
setenv CLIENT_CERT 0
key-direction 1
<tls-auth>2048 bit OpenVPN static key
-----BEGIN OpenVPN Static key V1-----
88af59de8bc63d86f0d59f72994afbb3
1e5ff375edc4d460ff8c145afe254e03
f4e7b72a52a747485e9216f2cb04cd43
aa5139fbd0ce8f8e77c95be0f7344fce
46b31198e56896a328e1c55e69378be0
b8bf11a080bed79983d1863572f80943
ea1e24ed83278a2348c1fd0da536ccc5
f94ed219141ad36e87ef38261f5d42f1
b9a1514390e3a00f148f83980a5072e2
553a139ad06241ba7a8378f470dc3802
8dcb4f3fad3d15161af9487d3459e2d8
a96ae3048add2843d79935eb8c7e162b
3a2fd0d8b6e403f23561a926cdc0c94c
7fd01f4abff0c83c6edf9d7c032e5d0b
c36a0982f90181980d98eeb1109bbd23
dd69c02432a400e67a6ea971f80dfe20
-----END OpenVPN Static key V1-----
</tls-auth>