Outgoing LAN only OK to ISP GW
-
@fireix No idea if this helps anything, but here is how the results are from PING using pfSense WEB-interface:
Ping from WAN : OK
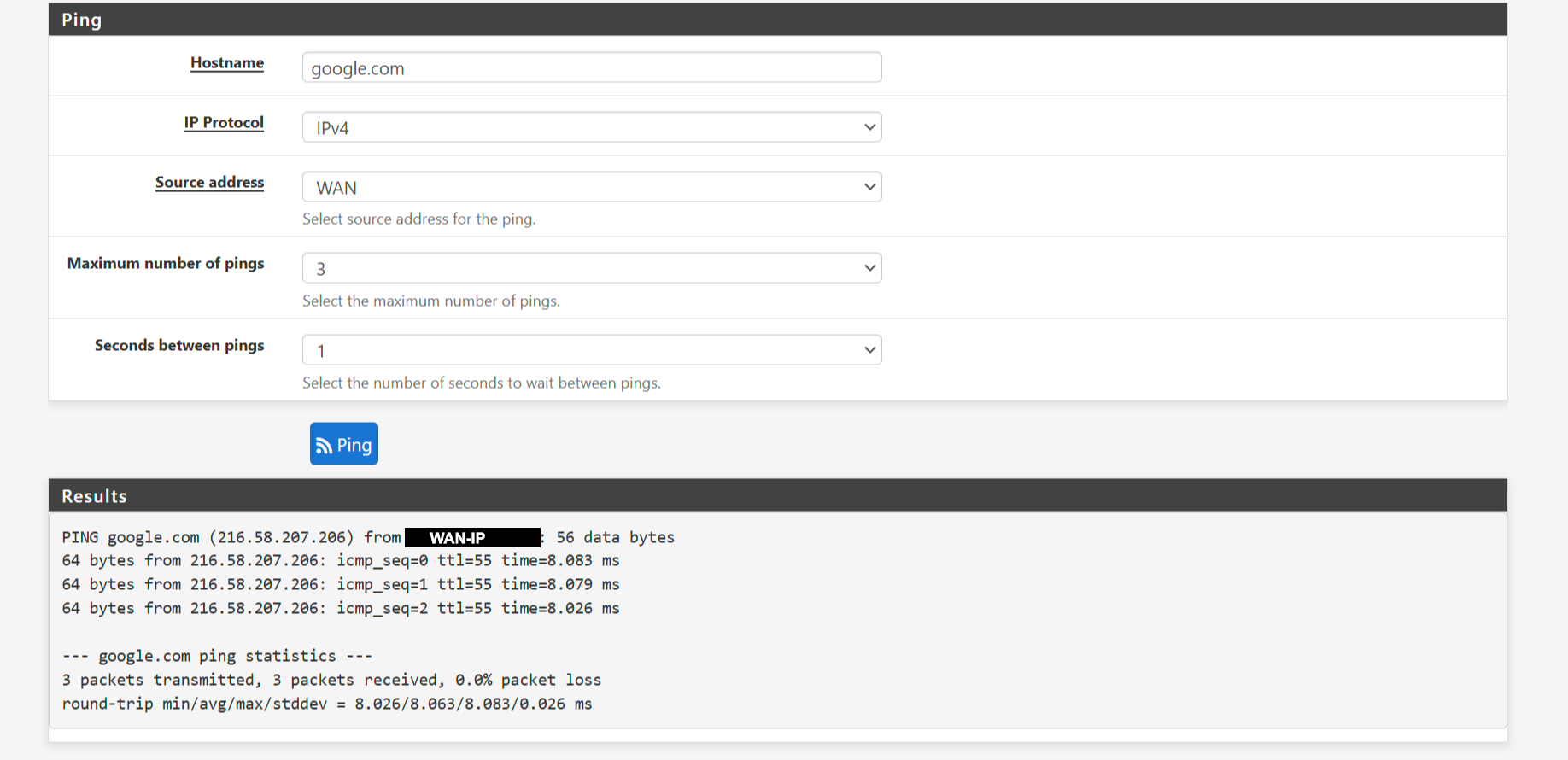
Ping from LAN : FAIL
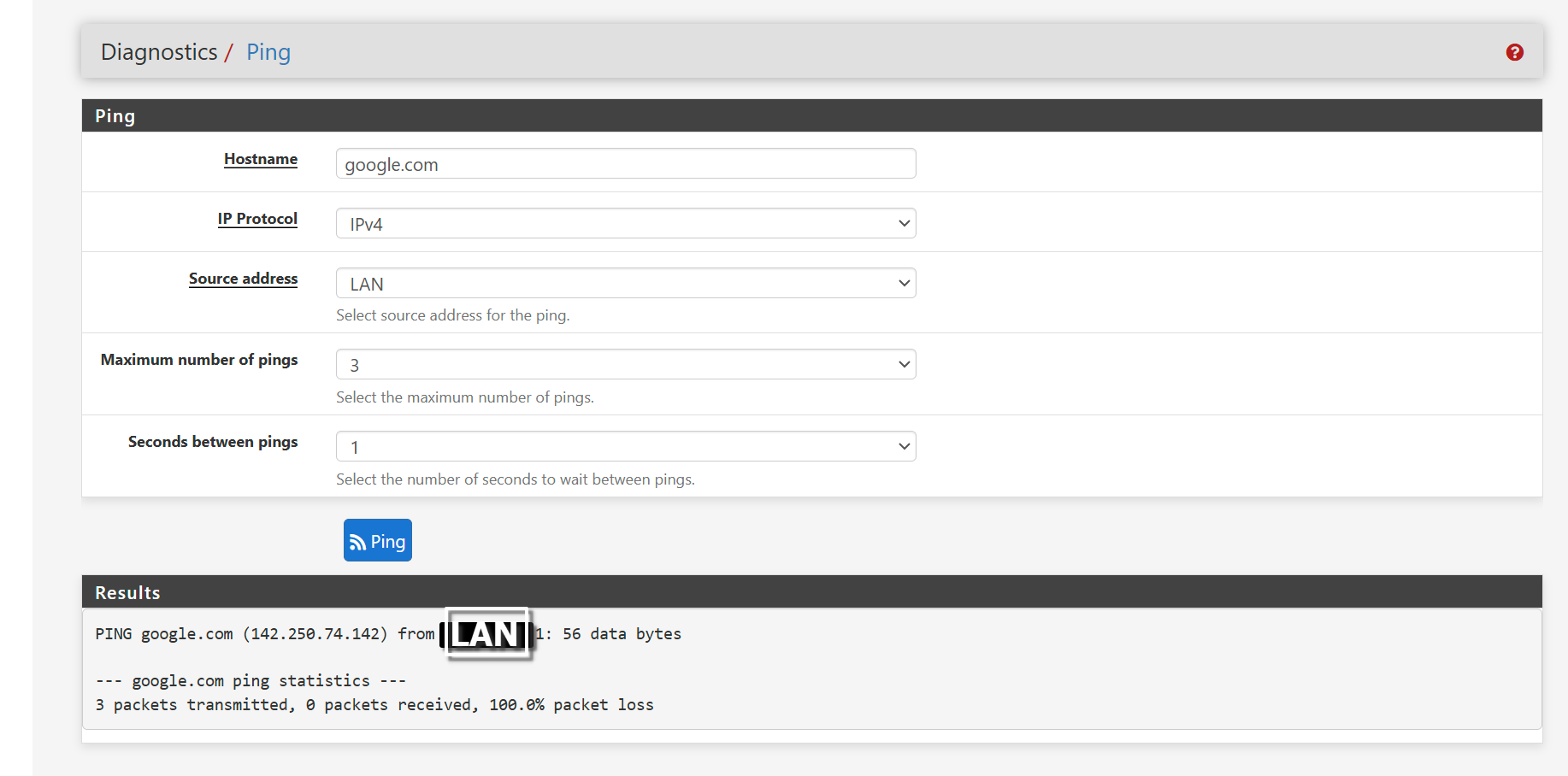
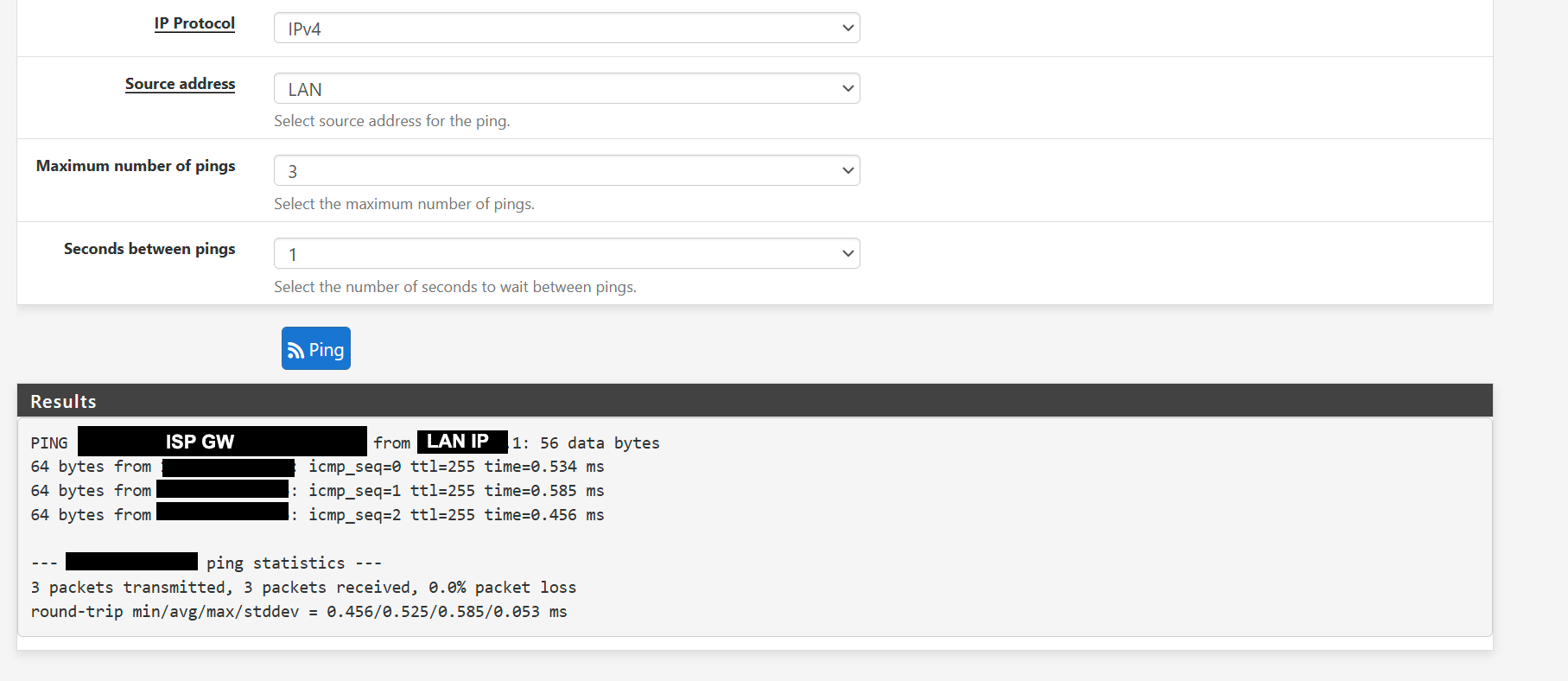
Ping from LAN to ISP GW : Success
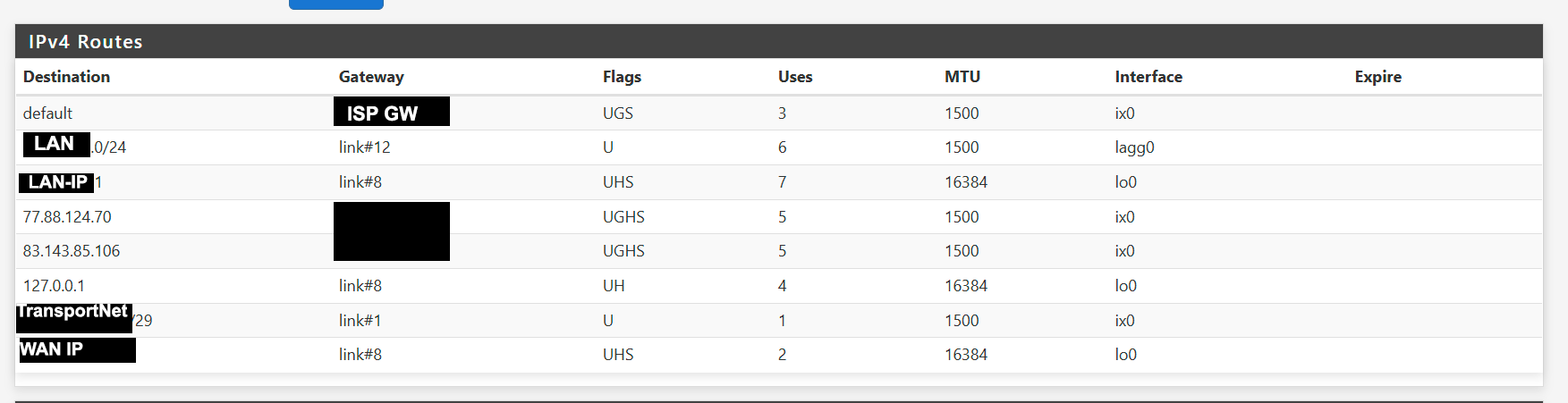
Routes
-
@fireix I am confused still... is not the gateway/WAN supposed to be the isp gateway. Or better yet the outward facing IP (WAN) is provided by the ISP. It seems you have a conflict. Unless I still don't understand? At the bottom of the routing page there is a box to choose the default gateway. How do you choose the default when it appears you have two? Actually your chart shows the default as ISP_GW. I would not expect anything to go out the WAN without it being selected as default. I also suspect the ip's of ISP_GW and WAN match.
I think I am missing something still. -
@The-Party-of-Hell-No said in Outgoing LAN only OK to ISP GW:
gateway/WAN supposed to be the isp gateway. Or better yet the outward facing IP (WAN) is provided by the IS
Gateway is supposed to be the isp gateway, yes. To be able for me to do routing native, they also have assigned a small IP range /29 that I can use on my WAN-interface. This way, I can easy create fw rules from the WAN-interface to my public big /24 range of static IPs that I have on my LAN-side.
If I disable 1:1 NAT, I notice that my entire network works, only problem is that my WAN-IP defined on pfSense is used for all outgoing connection instead of the public static IPs on the LAN-side.
On my routing page, the default gw is GW_WAN_2. That is my ISP's gw. So that should be correct. The default gw for my WAN interface is my ISP gw IP.
GW_WAN_2 Default (IPv4) WAN ISP_GW Interface wan Gateway
-
@fireix I guess my last option is to try to just install from scratch. I can't see anything directly wrong in this, settings are the same as my old one :/
-
@fireix Did a clean install, only sat up WAN with ISP default GW, LAN. All working with the WAN-IP outgoing instead of the LAN-IP. All machines on LAN had internet, but with the WAN-IP. As soon as I activated 1:1 NAT, no internet and no ping.
I tried network sniffing and it showed ping, bot no reply coming back when pined from LAN-side. I also created allow-all on both LAN and WAN during testing, doesn't seem to be anything related to fw.
I guess I have to wait for ideas from my isp.
Update: 1 ISP network switch 0.641 ms 0.381 ms 0.362 ms
2 0.756 ms 0.455 ms 0.417 ms
3 0.626 ms 0.536 ms 0.529 ms
4 0.809 ms 0.708 ms 0.703 ms
5 0.648 ms 0.512 ms 0.513 ms
6 0.792 ms 0.669 ms 0.671 ms
7
8
9
10...
So the traceroute started from LAN actually goes to my ISP. But it stops at step 7 for some reason. If I do the same from WAN, it goes all the way through. So it must be a issue with my ISP filtering? -
@fireix So if it is working, but not as you thought, is that okay?
I am still not sure why you think this is not correct - "WAN-IP outgoing instead of the LAN-IP" Pfsense resides as a firewall technically between your LAN (private) and the WAN (public) to prevent intrusion into your private LAN from the public internet and to direct traffic from your private LAN out to the public internet. You really do not want your private LAN exposed/showing on the public internet - "I want to have the LAN-IP shown at the outside" There would be no protection with your LAN IP exposed.
"they also have assigned a small IP range /29 that I can use on my WAN-interface" No what they are telling you is your modem/WAN has been assigned a single IP residing in this IP range. I would be surprised if this range and IP could be manipulated by you. They are controlled, assigned and registered by your ISP's equipment. In fact I believe all the IP's in that range are also assigned to other customers.
-
@The-Party-of-Hell-No said in Outgoing LAN only OK to ISP GW:
You really do not want your private LAN exposed/showing on the public internet -
I really want :) I know it is not usual setup for most people, because they don't need a public IP for incoming/outgoing traffic. Most businesses would hide their LAN, no reason to expose it.
Note that I'm running webserver's in a big data center - public webservers on my LAN. For instance cPanel, Directadmin and so on. If the outgoing IP is hidden, license validation will fail, firewall rules on the opposite side would put businesses at risk since they would need to open for all the customers IP and so on.
This is a setup I have been running for 10-15 years, just now I will have a different ISP. So I guess you are just not used to this type of public servers :) This setup makes it far easier to group servers and just open a fw rule for the services I want - instead of doing a lot of NAT + fw setup. The task would be to big to administer and require to much CPU.
Alternative setup to this is transparent fw, but pfSense doesn't support it that great. Special firewalls like Fortinet is perfect for it, used it for 10 first years.. just to expensive in the long run. Just open the port and the target IP and customer has access, without having to deal with a transport network. Or nat.
My ISP has assigned me a public IP-range /29 to have on my WAN side and I have my purchased a /24 public range accessible on my LAN-siden - available through normal routing. This makes the setup super simple (usually). So they should really have it assigned directly onto my pfSense. Like I always have with my old ISP.
-
I got confirmation now, that it was something wrong at my ISP and their allocation of my /24 was missing something in their end. Finally the world makes sense again.
-
@fireix Well first I apologize, you obviously know way more than I and have way more experience. This has been a humbling experience.
I was going to reply back as to your struggle. My experience is it is rarely pfsense it is almost always, always, always the ISP even at my meager consumer level.
I am sorry you went through a complete rebuild to only find it unnecessary and nothing you had control over. Which brings me to my second point I was going to encourage you about... tech staff at most ISP's, in my experience, are woefully lacking in any network structure outside their norm. I would guess you finally found a senior tech person who had previous experience with your problem and understood exactly what needed to be changed and your nightmare came to an end.
Thank you for putting up with me.
-
@The-Party-of-Hell-No It is always good to get different inputs, that's far, far better than no replies :)
-
@The-Party-of-Hell-No said in Outgoing LAN only OK to ISP GW:
Wondering about NAT outbound and whether you have rules allowing LAN subnet out other gateways/interfaces?
Reply
It’s definitely worth checking if you have NAT outbound rules set up to allow traffic from your LAN subnet to go out through the other gateways or interfaces.