DNS Resolver Infrastructure Cache Stats
-
@johnpoz said in DNS Resolver Infrastructure Cache Stats:
Now that you can resolve yourself - I just don't get why everyone doesn't just resolve, you couldn't get me to go back to forwarding ever.
The main reason, that my ISP filter DNS, cannot get some sites
-
@Antibiotic said in DNS Resolver Infrastructure Cache Stats:
The main reason, that my ISP filter DNS, cannot get some sites
I get it.
I'm not all against forwarding. Reasons exist, and its always better to have a choice.Public resolving will never (not in a near future) happens over TLS, your port 853, as this will make every DNS request "a thousand" time more expensive (resources needed) a creating TLS connection for small very temporary connections is a bad thing.
See my edited post above about Google in Europe.You could still resolve, but then you need to VPN out all your traffic.
Or only VPN out your DNS requests (dono if that can be done, I 'think' you could) ? -
@Gertjan said in DNS Resolver Infrastructure Cache Stats:
You could still resolve, but then you need to VPN out all your traffic.
Or only VPN out your DNS requests (dono if that can be done, I 'think' you could) ?Yes, I tried but without success, could you please get 2 firewalls examples. how to make this. For first option and for me I think preferable second option. VPN out your DNS requests , this is my dream to make,
-
@Antibiotic how would your isp stop you from going to site xyz if you were running your dns also through the vpn. Unless of course your vpn was also filtering your dns like nord.
It is unlikely your isp is filtering dns in that they prevent looking up xyz, but what they could be doing is hijacking and redirecting your dns which can break resolving.
I mean if an isp doesn't want their user base going to xyz site, its pretty lame attempt at stopping the users to just break dns, and not actually block the traffic to that sites IPs as well.
If I found out my isp was doing anything weird with my dns first thing I would be doing would be looking for a new isp. Which is not always possible sure. Next best option prob find vpn service that doesn't mess with dns either..But would prob just spin up a vpn on a vms somewhere - you can run a vps for a couple of bucks a month. I have one that is like 20 a year I can route traffic through, be more than capable of running a dns resolver for me.
I have little desire to send my dns to these dns providers - they are not providing dns out of the goodness of their hearts, there is profit in it for them, in one form or another or they wouldn't be doing it.
A simple smoking gun test to see if your isp or vpn is hijacking dns is simple directed dig to 1.2.3.4 for something.. If you get an answer then your dns is being redirected, either you are doing it yourself on pfsense or its happening up stream. But 1.2.3.4 does not answer dns, so if you got an answer its a smoking gun that you have been redirected.
dig @1.2.3.4 www.google.com
That should just time out, if you get a response your dns has been hijacked/redirected that is a fact jack ;)
-
@johnpoz said in DNS Resolver Infrastructure Cache Stats:
how would your isp stop you from going to site xyz if you were running your dns also through the vpn. Unless of course your vpn was also filtering your dns like nord.
It is unlikely your isp is filtering dns in that they prevent looking up xyz, but what they could be doing is hijacking and redirecting your dns which can break resolving.
I mean if an isp doesn't want their user base going to xyz site, its pretty lame attempt at stopping the users to just break dns, and not actually block the traffic to that sites IPs as well.
Sorry, I'm not expert in this. Try to explain, when set Unbound to resolver mode and using VPN , LAN rule here:
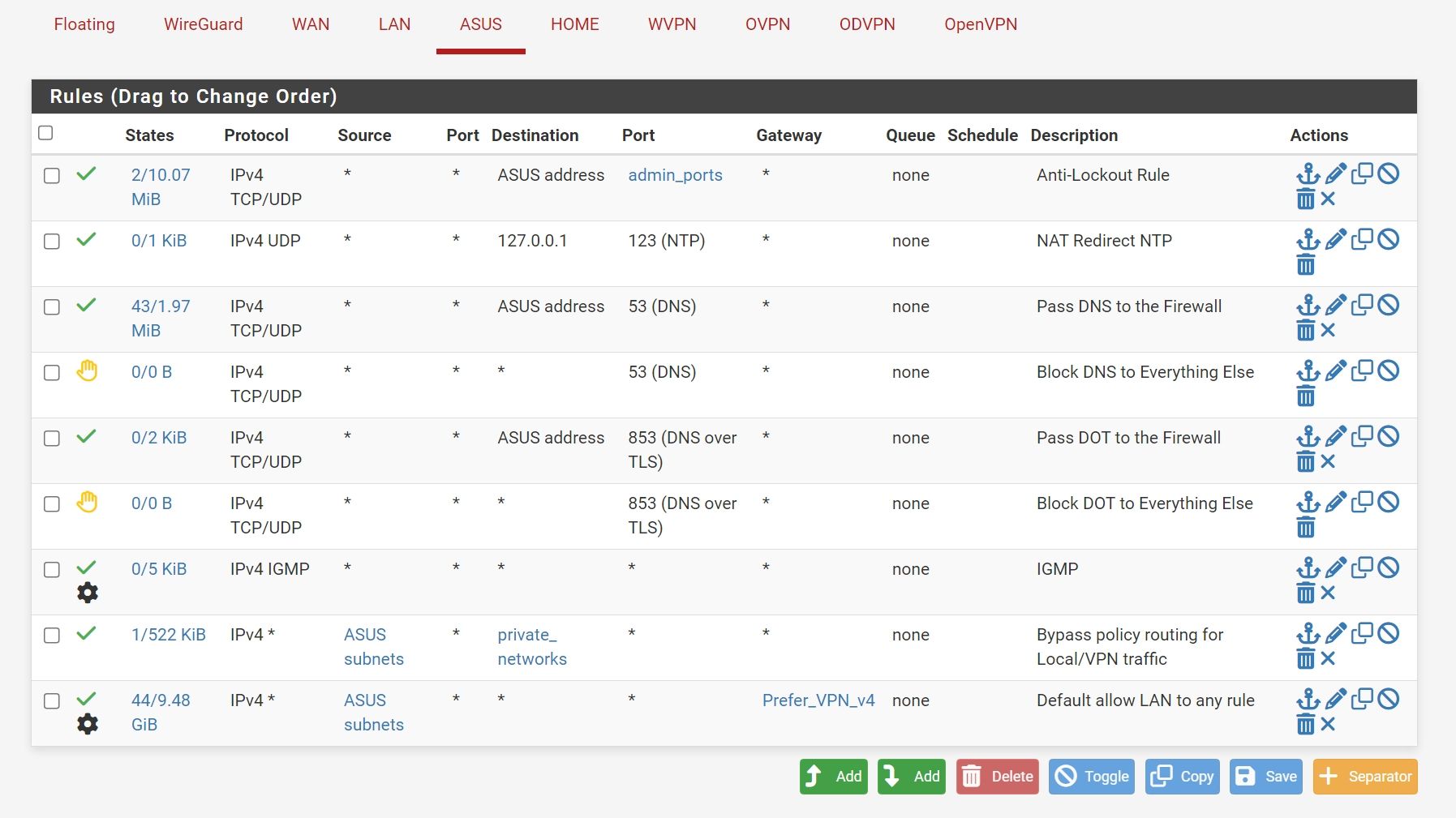
I cannot get some sites.
-
@Antibiotic where in those rules do you have pfsense dns route through your vpn? That routes your clients traffic over a vpn via policy route. What your client asks for something.domain.tld of pfsense resolver.. Does your resolver query route out the vpn? If not then no it would just be out your isp.
-
@johnpoz said in DNS Resolver Infrastructure Cache Stats:
Does your resolver query route out the vpn?
Could you please give a firewall rule example for this? If yes, regarding my settings where better to arrange this rule, I mean by rules order on this interface?
-
@Antibiotic wouldn't be a firewall rule, it would be a setting in your resolver on what outbound interface to use. Or it would be the default route in pfsense to send all traffic out the vpn.
-
@Antibiotic said in DNS Resolver Infrastructure Cache Stats:
could you please get 2 firewalls examples. how to make this. For first option and for me I think preferable second option.
Long story short : I can't.
I use a (just one now) pfSense, and that's the one used by the company I work for.
Experimenting with that setup, and my boss knows that it is me messing around (again), and I already lost all my "who broke the Internet to credit points" for this year.If I have DNS issues with my ISP, I terminate the contract with them.
I prefer by far keeping my pfSense setup as simple (for me) as possible. And we all know it, we use pfSense, so it won't be simple, that why we use pfSense.
-
@johnpoz said in DNS Resolver Infrastructure Cache Stats:
it would be a setting in your resolver on what outbound interface
Actually, I tried to do like you tell now. But anyway, cannot get some sites.
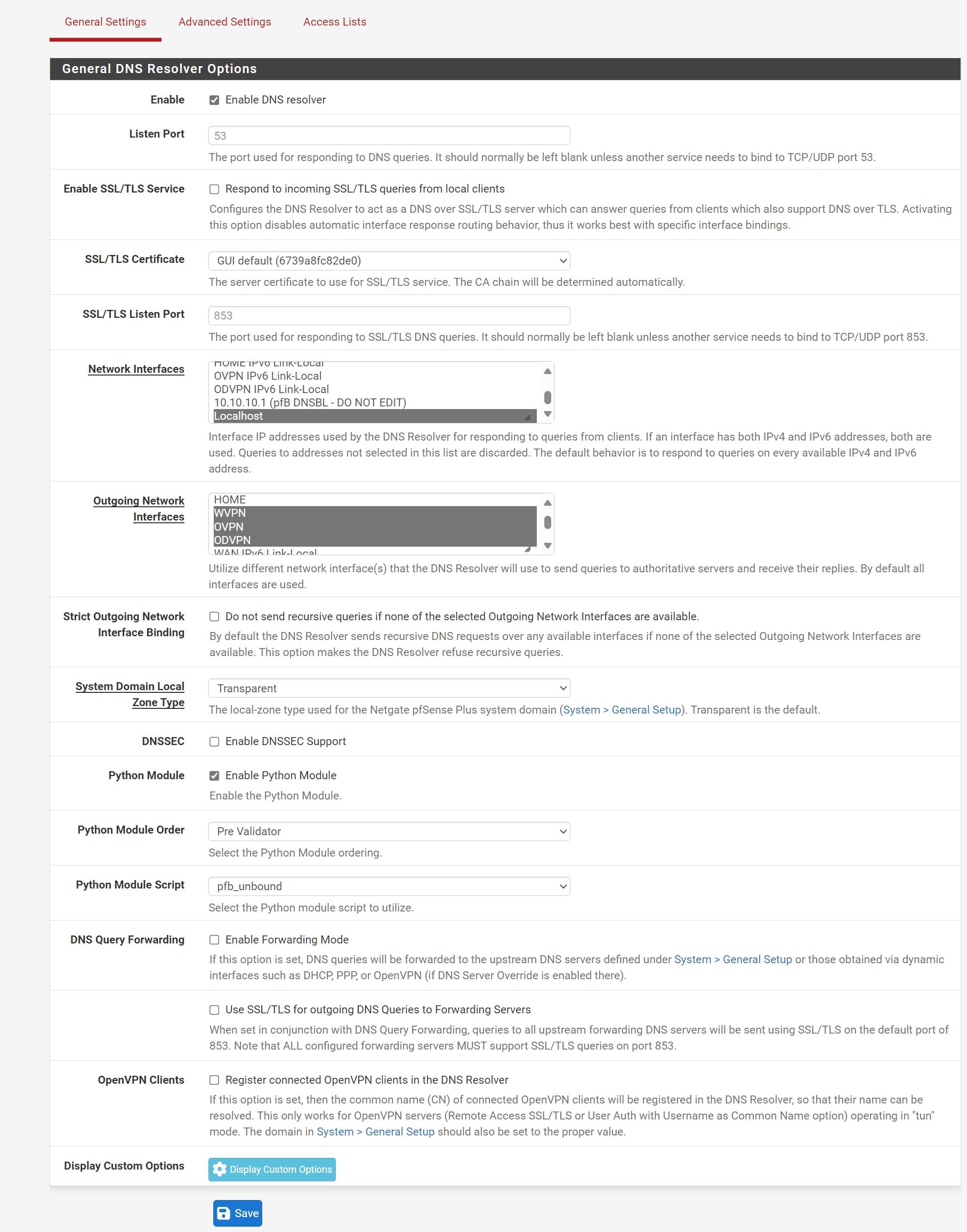
Could be make restart?
-
@Gertjan said in DNS Resolver Infrastructure Cache Stats:
Long story short : I can't.
I use a (just one now) pfSense, and that's the one used by the company I work for.
Experimenting with that setup, and my boss knows that it is me messing around (again), and I already lost all my "who broke the Internet to credit points" for this yearNo problem, buddy, anyaway thank you
-
@Antibiotic not sure how that is suppose to work at all, unless your redirecting dns.. you have unbound only listening on localhost.. which is 127.0.0.1, how would your clients actually ask pfsense for anything for dns..
unless you have it listening on interfaces your now showing?
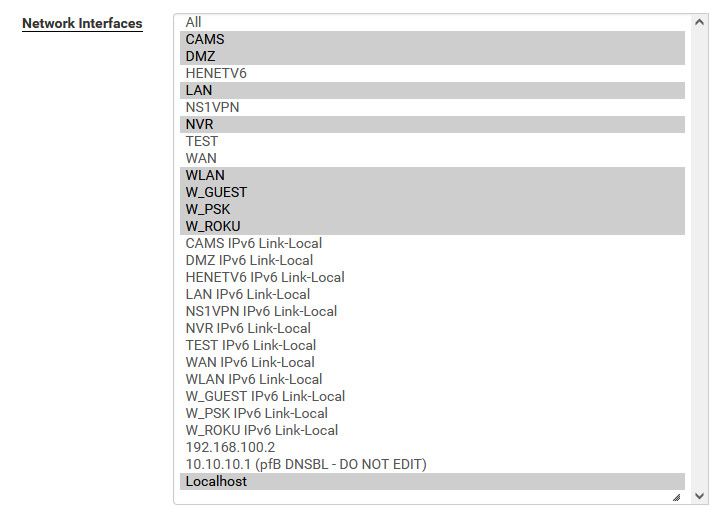
-
@Gertjan said in DNS Resolver Infrastructure Cache Stats:
If I have DNS issues with my ISP, I terminate the contract with them.
Than I have to go out of Europe))) Where freedom exist in internet)))But where exist?)))
-
@johnpoz said in DNS Resolver Infrastructure Cache Stats:
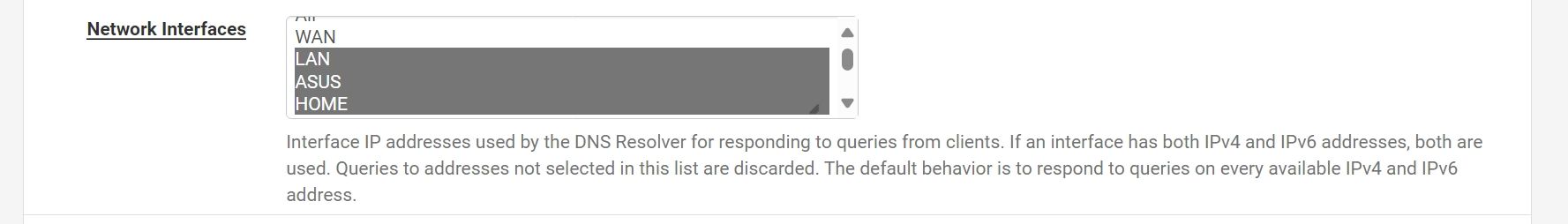
you have unbound only listening on localhost
No , its listening on pfSense interfaces as well:
-
@johnpoz said in DNS Resolver Infrastructure Cache Stats:
But would prob just spin up a vpn on a vms somewhere - you can run a vps for a couple of bucks a month. I have one that is like 20 a year I can route traffic through, be more than capable of running a dns resolver for me.
What is VPS, so cheap do you use?
-
@Antibiotic A vps (virtual private server) is just an instance you run on the internet somewhere.
Its just a vm, so a full OS that you can really pretty much do anything you want on, just like some vm or server you would setup locally but its hosted somewhere on the internet.
If your looking for a lowcost vps, check out https://lowendbox.com they have all sorts of links to deals.
I show one on there currently at racknerd for like $10 a year.
check out for a few different $1 a month deals
https://lowendbox.com/blog/1-vps-1-usd-vps-per-month/
I use to have bunch of different ones in different locations, west cost, east cost, Chicago, EU (NL) - but I trimmed back and currently only one I have active is with https://buyvm.net/ which is 2$ a month currently.. Price has gone up over the years ;) I do have another server currently in NL.. But its not really a lowend box, and is more like $10 month vs a year.
The one I have currently still have, I first got back in 2016, it was $15 a year then. Now its 24.. not really bad price increases, since over the years they have increased what you got for the money.. I might have to spin up one of these 10 a year guys to just kick the ties on it. Might switch over and save myself $15 a year ;) hehehe
If I needed one in a specific location for something I was testing, the great things about these is you can have them spun up and active normally in a few minutes.
-
@johnpoz said in DNS Resolver Infrastructure Cache Stats:
Its just a vm, so a full OS that you can really pretty much do anything you want on, just like some vm or server you would setup locally but its hosted somewhere on the internet.
But in case of planning to use this VPS as private DNS server and VPN for my home net. Is it important to choose server as close to my real location or this not so important regarding my purposes. Second, this VPS have a more less easy setup of DNS server and VPN. I mean these procedures well instructed usually? or have some auto scripts to do on VPS side?
-
@johnpoz said in DNS Resolver Infrastructure Cache Stats:
If your looking for a lowcost vps, check out https://lowendbox.com they have all sorts of links to deals.
Also, if planning use as DNS server and VPN server, how much need RAM and CPU to be not overpay and do not have slow connections?
-
@Antibiotic dns would require pretty much nothing.. you could run that on a pi zero.. vpn on the other hand would depend on how fast of connection want/have and how much traffic your actually going to push through it.
-
@johnpoz said in DNS Resolver Infrastructure Cache Stats:
Now that you can resolve yourself - I just don't get why everyone doesn't just resolve, you couldn't get me to go back to forwarding ever..
Simple: because the root name servers don't accept encyrpted queries. If you're resolving, every query leaving your LAN does so via sniffable cleartext to at least your ISP and whoever/whatever else they allow, knowingly or unknowingly, to sniff their LAN.
ISPs are massive corporate overlords—even more so in so-called 'developed countries' (e.g. AT&T, Charter, Comcast, Cox Communications, Frontier, Time Warner, Verizon, etc.) than lesser developed ones—and I'm not convinced they aren't all in bed with one another when it comes to sharing private customer data.
@Gertjan said in DNS Resolver Infrastructure Cache Stats:
You could still resolve, but then you need to VPN out all your traffic.
My opinion from a privacy perspective is that this would be the only acceptable alternative to DoT. (In fact, if you were really paranoid, you could encapsulate DoT queries within the tunnel to keep them hidden from even your VPN provider.)