ATT Internet AIr
-
Yes exactly like that. The ports on the switch can be configured as access ports on different VLANs. The link to pfSense can carry all the VLANs. pfSense treats the VLANs as separate interfaces. And yes it can be a WAN, or any interface type.
-
@stephenw10 Perfect. thanks
-
Currently at my primary business location I have cameras on the same subnet as other devices - like the NAS, etc. My second business location as you might remember from above discussion has cameras on a seperate subnet.
Ideally I would like to keep acessing my cameras with the Synology Surveillance station which is within my network. However an alternative is to use the camera manufacturer software - but that requires a port forward., to be accessed externally.Is there a way to open several LAN IP addresses to a specific port - or even entire subnet to a particular port ? Or do a I need to change each individual camera to a non-default individual port?
Just trying to be the safest possible if I end up opening another port externally
-
Hmm, well I would avoid opening port forwards to each camera like that if at all possible. Especially if they are on the same subnet as other local resources.
To do it you would need to use a different external port for each camera and forward that to the internal camera IP. That way they can all be forwarded from the same external IP. But don't do that!
-
@stephenw10
OK. Maybe I better just keep doing the VPN connection and use of surveillance station which is part of the Symbology NAS
If that is the case and a VPN is used for external access with no open external ports is there really a strong security reason to have the cameras on a different subnet? -
Because any IoT device like that is always going to be a target for exploits. They usually only see updates for limited time (if you're lucky!). And if they are on the same subnet as other things then if a camera is compromised anything running on it will be able to directly connect. Or at least try to.
-
@stephenw10
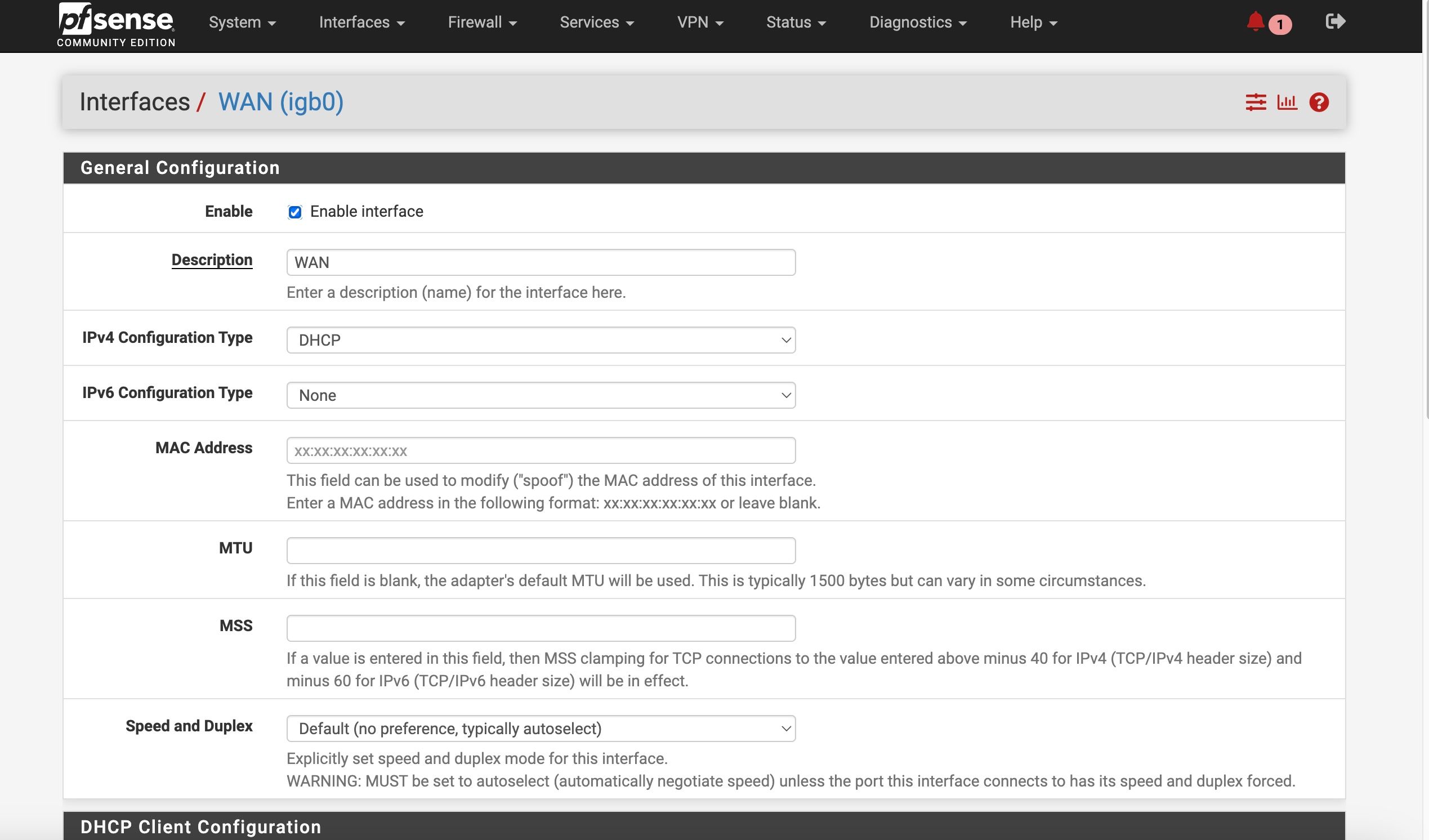
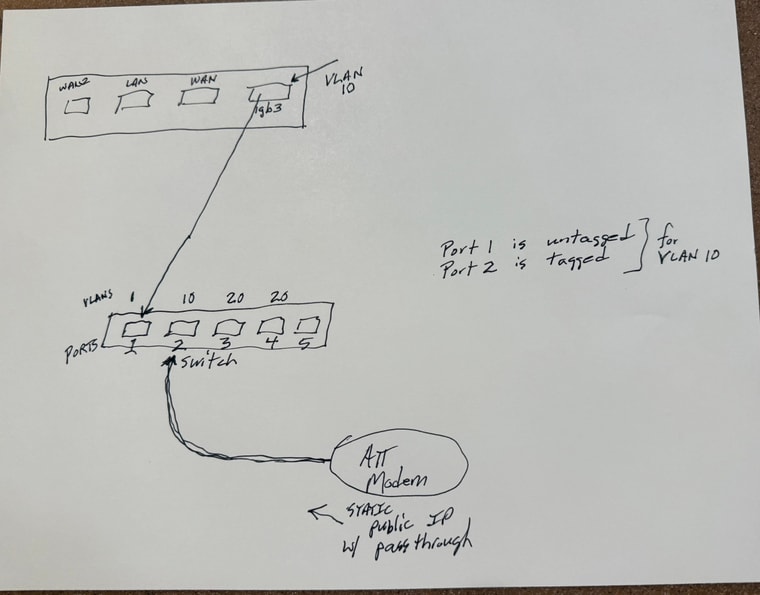
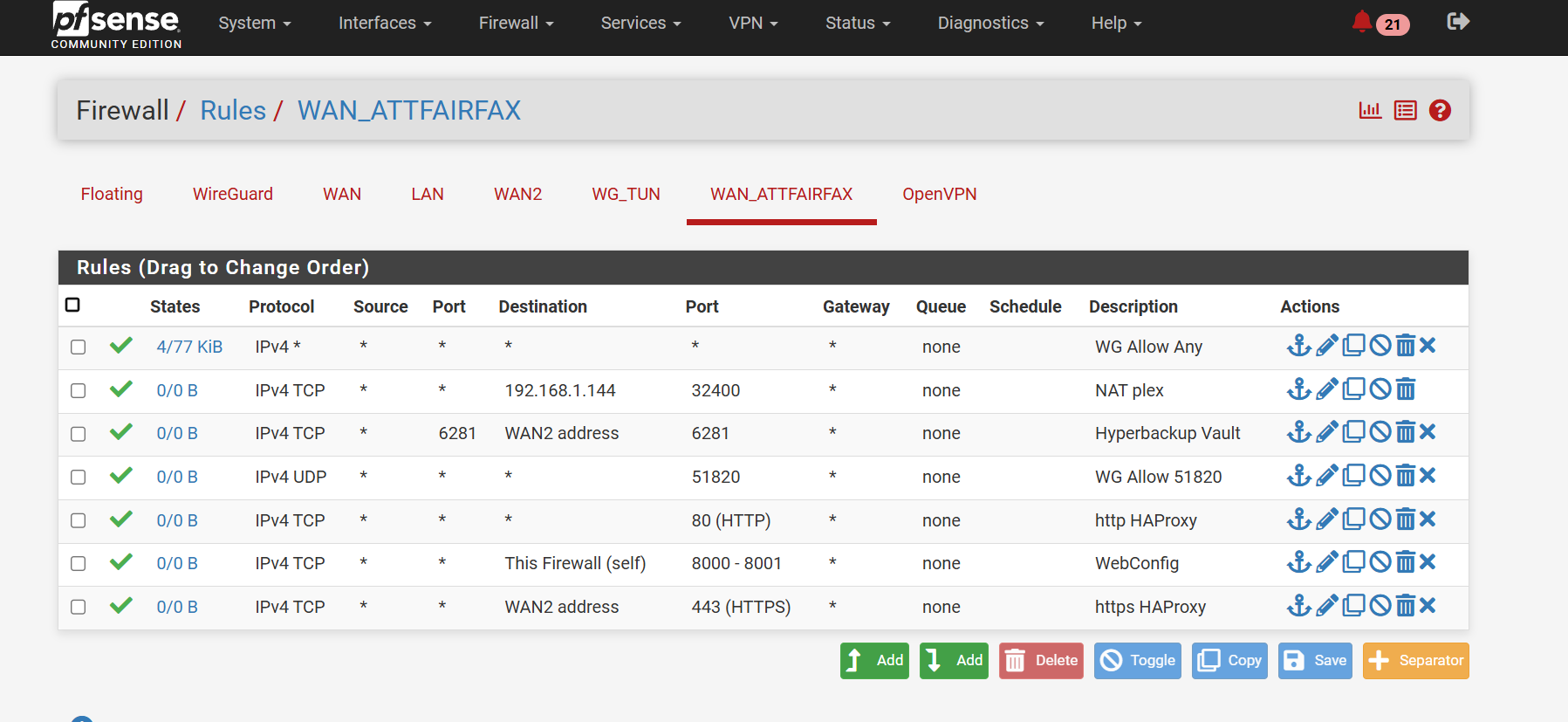
Lost again - hopefully you will have time / energy to help:As I mentioned I am trying to setup the addnl WAN ATT modem on my second store system. I mentioned that my pfsense device is a 4 port device with all 4 ports utilized. We talked about a VLAN capable switch - I purchased a TP-Link TL-SG105E
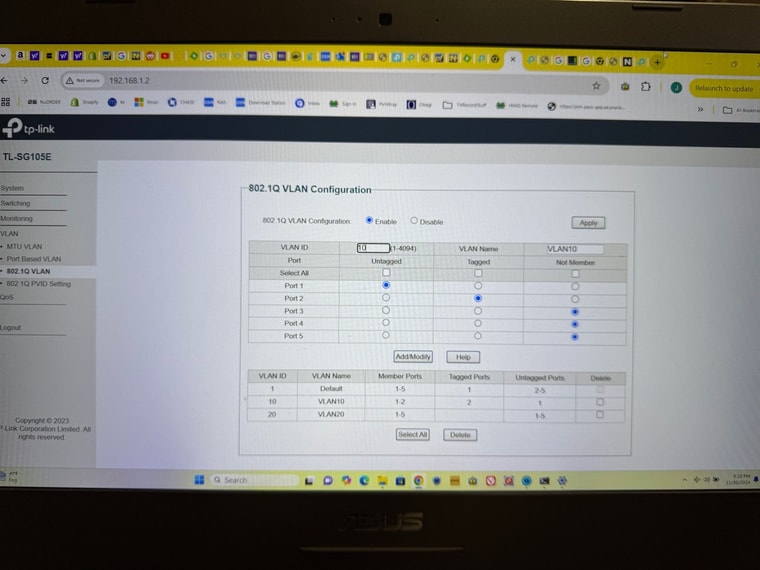
I am 5hrs off site so I am trying to get up to speed to manage remotely by trying the switch on my current system.So I have created a VLAN with a tag of 10 on interface igb3.
I have TRIED to setup my TP-Link switch (in preparation for the setup that I am currently offsite from) with port 1 being the "trunk" that a cable will be connected to igb3 (on the pfsense).
Port 1 is untagged for VLAN ID 10 and is identified as a "1" in PVID Settings
Port 2 is tagged for for VLAN ID 10 and is identified as "10" in PVID settings
(Port 3 and 4 if needed will be VLAN ID 20 for the additional LAN cable that is needed for the Camera segment of my network)The current trouble I am having is that my identical ATT device, when connected to port 2 of the switch, is not passing through the IP address when I created or setup the interface as DHCP -- the other ATT device when connected directly to one of the pfsense interfaces pushed through ATT static publc IP address. And if I try to set the IP address manually it doesn't behave correctly- says offline
I think I must be setting the VLANs and the switch incorrectly (tags vs untagged, etc). Would you expect a device (in this case the ATT modem) to behave the same way when connected via VLAN and the switch compared to connecting directly to the pfsense physical port? I thought that was the whole purpose
Do you see any glaring errors in my setup?
-
@ahole4sure said in ATT Internet AIr:
The current trouble I am having is that my identical ATT device, when connected to port 2 of the switch, is not passing through the IP address when I created or setup the interface as DHCP -- the other ATT device when connected directly to one of the pfsense interfaces pushed through ATT static publc IP address. And if I try to set the IP address manually it doesn't behave correctly- says offline
Looking at your picture, I see WAN, LAN and WAN2. So what is it that you are trying to do with the ATT modem now, connecting it to the fourth port? Are you trying to add a third WAN?
I don't understand the direction... If your VLAN is set up on pfsense, you make port 1 a TRUNK port as you said, but that means TAGGED 10. And the ports for any devices that should only belong to VLAN 10 need to be untagged and only members of VLAN 10. Currently all ports are also members of VLAN 1...
If you are trying to get an IP on port 4 on pfsense (igb3) from the ATT modem, you can simply make both ports 1 and 2 VLAN 10 UNTAGGED on the switch. Remove them from any other VLAN memberships.
This way you have created a "switch within the switch", where port 1 and 2 are connected but separate from the other ports. Pfsense doesn't need to know of any VLAN on igb3 for this to work... -
Yup that^. Port 1 should be tagged for VLAN 10 because it has to pass tragged traffic to pfSense. Port 2 should be untagged for VLAN 10 and have the PVID set as 10 (as it is).
-
Thanks for input
Yes @Gblenn my apologies for confusion -- the weird setup is because it is just for testing (and being done on the system that is currently available to me - and yes in this test, adding a third WAN)
Once I get a confirmation that I can set this up and it will function properly then the real situation is depicted in the attached.Basically the real setup needs to have proper switch setup for the current "Camera" interface to be split so that the newly added switch can accept 2 ports (one for the newly added ATT modem and the original camera network) - see diagram.
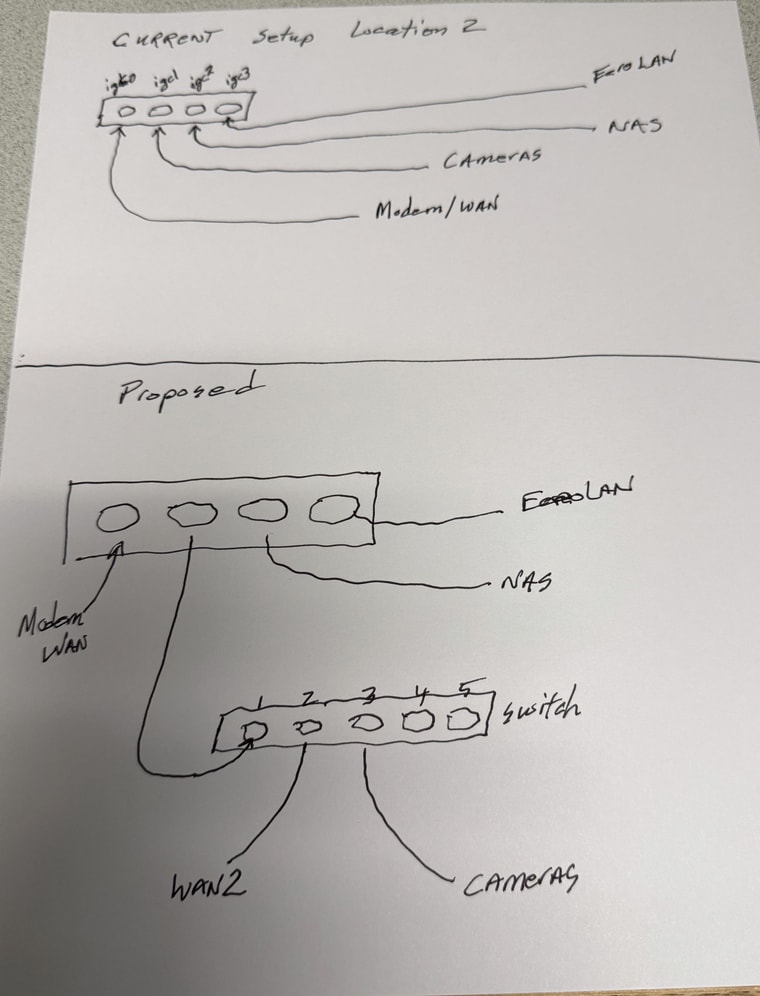
The reason for the change is to add a failover internet scource but i have no availabe addnl ports on the pfsense box.
In this real case scenario I will have the camera VLAN as ID 20So any input on how I would setup the switch (membership, tagging etc) would be appreaciated !! I have a feeling when the light goes off it is going to be easier -- but initially setting up the switch and VLANs is not as intuitive as I had thought. ugh
-
As discussed you can use just one VLAN there and have untagged traffic for the other subnet. But I would avoid that and use two VLANs instead because it avoid a bad config putting traffic onto the wrong interface.
So I would add VLANs 10 and 20. Make port 1 tagged for both those.
Make port 2 untagged for VLAN 10 with PVID 10.
Make port 3 untagged for VLAN 20 with PVID 20.
-
Another question for the situation (and in general)
So in general when you make an interface assignment and connection to VLANs (like in my case) do you need to delete the physical connection assignment - ie Camera in theis case?
And then of course make the new assignments to whatever VLANs you are connecting there?Is there an easy way to transfer or use all of the current network settings (rules, routing etc) for the Camera network - or in my case do I just leave it as it is and traffice gets passed to port 3 just like it is coming to igc3 natively currently?
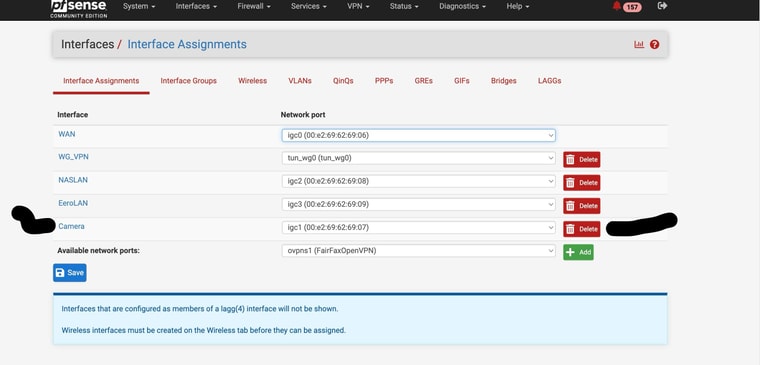
-
You don't need to remove the parent interface, you can still use the untagged interface. But I would avoid that as I said.
You can just re-assign Cameras, for example, from igc1 to the VLAN igc1.10. All the rules etc will follow it.
-
@stephenw10
Thanks
But in this case would it be better to create a seperate VLAN for the Cameras , ie VLAN ID 20 ;
Since the new failover modem is on VLAN 10 IDDon't I need to have the modem and cameras on differnt VLANs or is it not necessary?
And if that is the case - would I tag Port 1 with VLAN 10 and 20??
-
Yes use VLAN 20 for Cameras if you;re already using VLAN 10 for the second WAN.
Yes port 1 has to be a tagged member on all VLANs it's carrying.
-
Thanks again
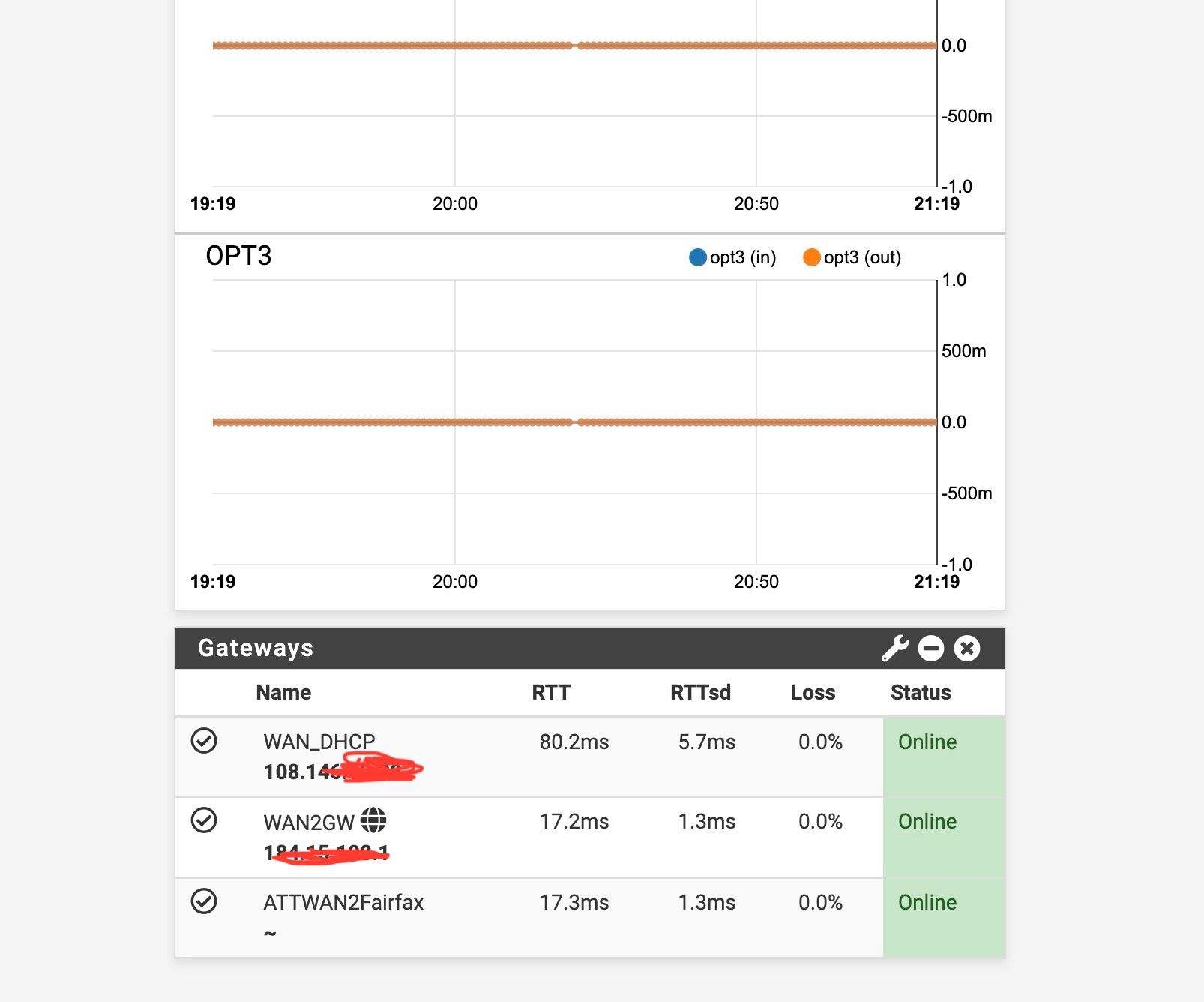
I made the changes that I thought you suggested. It appears things worked - my testing with both the ATT devices gave some squirrley results as far as consistency but I think it at least worked.What didn't happen was that with the modem connected through the switch and setting the VLAN(10) interface to DHCP it still didn't recieve the IP address (Local or public) and didn't create a gateway. However , it seemed to work when I gave the VLAN10 interface the static public IP address and created a gateway. No problem - I just wanted to make sure the slight different behavior (vs when I connected the ATT modem to a fixed port) wasn't due to me still not having the switch set up correctly??
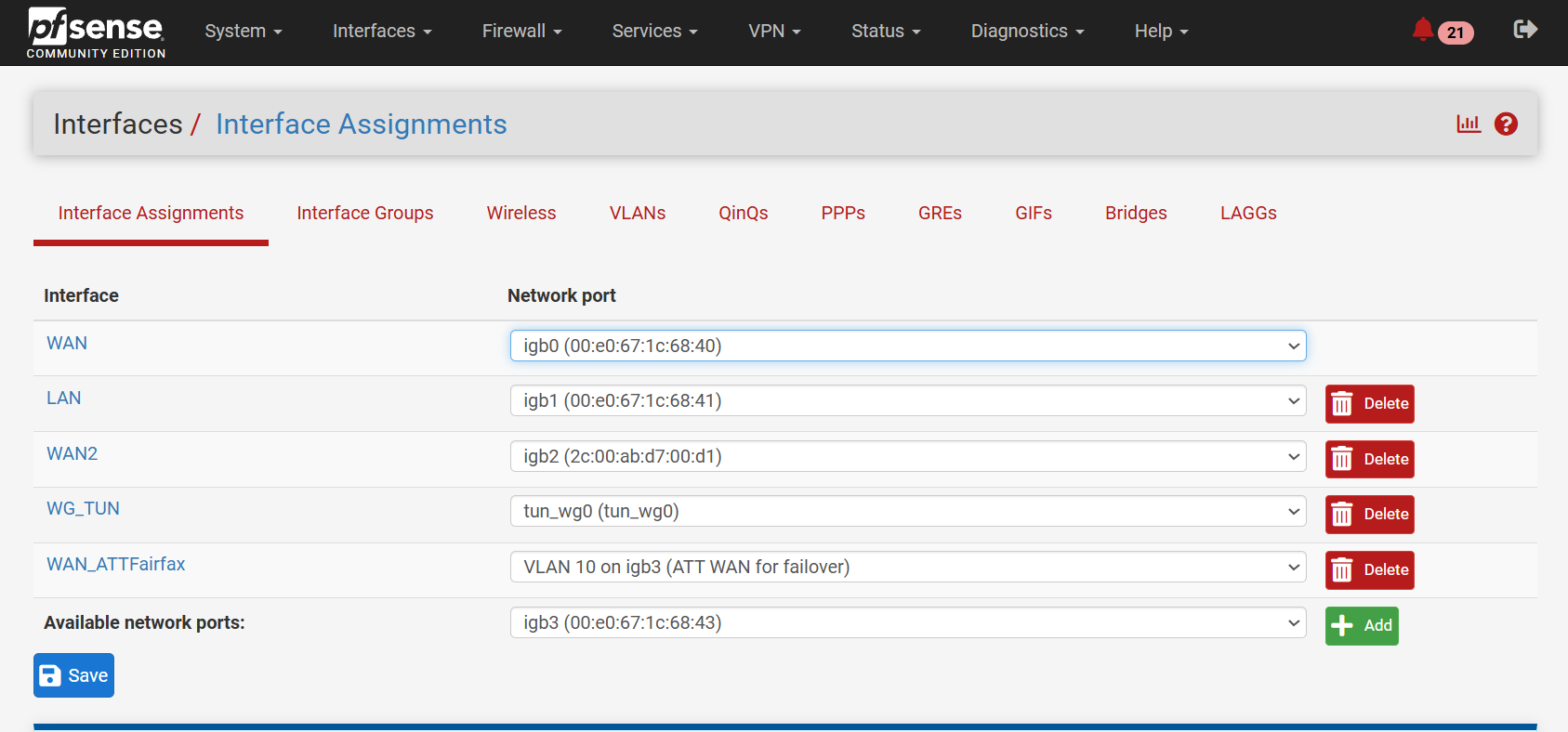
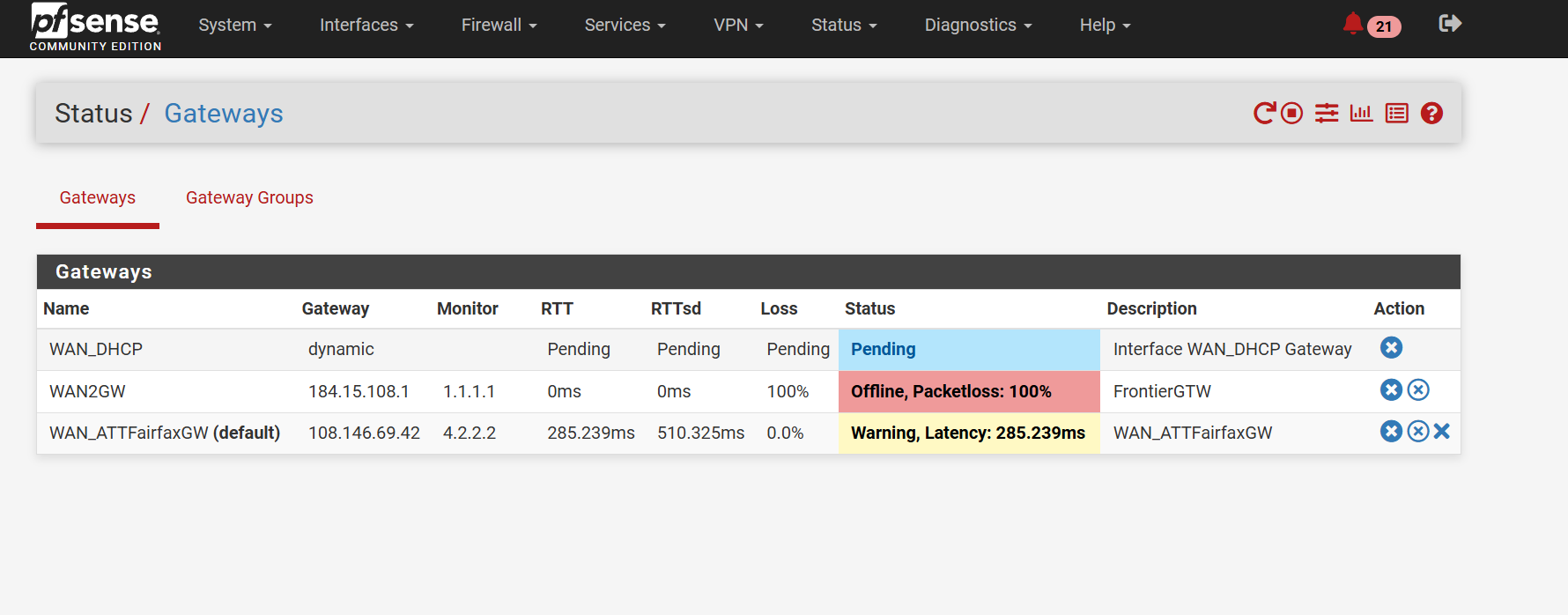
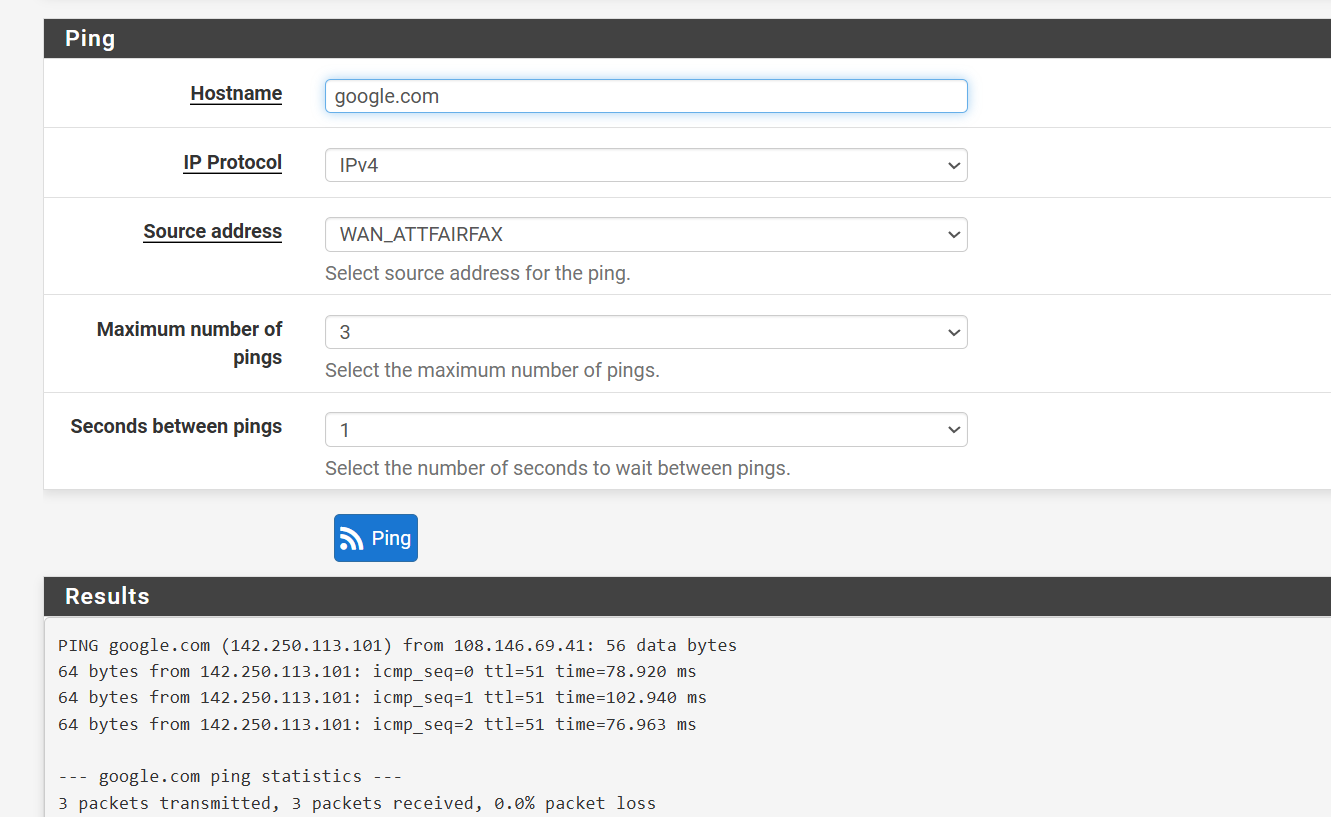
-
@ahole4sure I think you could perhaps make things a bit simpler than what you are looking at now.
I am using an LTE router as my failover WAN, and I have quite a few VLANs for Cameras, Guestwifi, VoIP and so on. However, I only have 3 ports on my pfsense, but even if I had more, I doubt I'd use more...
The way I have it set up is with two separate ports only used for the respective WAN connections, and then one single LAN port, carrying all VLANs. So what I would propose, is something like this adjusted picture, which I also suspect will help you getting your ATT connection a bit simpler to set up, is this:
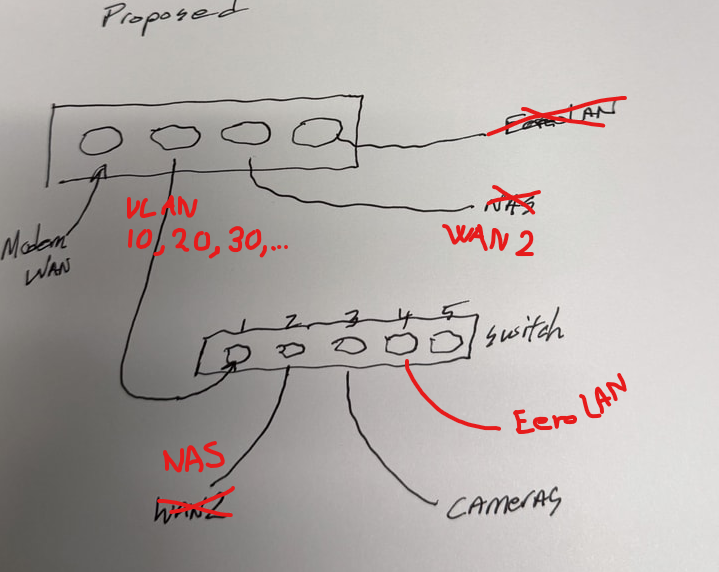
In your switch you set port 1 as TRUNK, with all VLAN ID's as TAGGED. Then you simply set each port on the switch to the VLAN you need, Port 2 could be 20 UNTAGGED, Port 3 is 10 UNTAGGED and Port 4 is perhaps default 1 (your main LAN?).
If you have more switches involved in your network you need to connect them together. And if you need VLAN's to carry over to the next swtich, that is done via TRUNK ports. Meaning that all VLAN ID's that you want to be passed along have to be TAGGED on those ports, in both switches. Since port 3 is UNTAGGED, you can connect a dumb switch to it and attach any number of cameras, and they will all be part of the Camera VLAN (without knowing it themselves...).
Since the ATT Modem is a 5G modem, you may want to place it somewhere with a really good connection, provided you have cabling for it in your home. If you don't have a cable that is unused, meaning it's already used for something else like an AP or so, you can use VLAN to "tunnel" the ATT WAN connection to the pfsense port.
If you put a VLAN capable switch also at the location where the ATT modem sits, you can create a switch only VLAN ID (say 100) and set the ATT connected port to 100 UNTAGGED. Include ID 100 in the TRUNK that connects the switches, and then set the port connecting into pfsense to 100 UNTAGGED.You don't have to do anything with VLANs on the second WAN port... VLAN ID 100 is only known and used by the switches, and becomes a switch within the switches only for "tunneling" the that extra WAN connection.
This is what I do in order to have my LTE modem on the top floor and the switch connecting the floors is not the one directly connected to pfsense.
-
If pfSense pulls a lease via DHCP when connected directly to the modem it should also do so when connected via the switch.
Since you have set ports 3, 4 and 5 to be access ports of VLAN20 the PVID needs to be 20 on all three of them.
-
Thank you both for chiming in so quickly!! Really helpful thoughts because I have a full switch up in the ceiling area for the cameras and re-designing my network with another or new VLAN capable switch up in the ceiling for the modem might be the way to go - thanks @Gblenn for the thoughts.
My real issue now is that I don't understand why my ATT modem set to passthough mode is not sending the IP address through the VLAN to the pfsense with the interface set to DHCP mode ?? (like I thought I remembered it doing for the first ATT modem I setup a couple weeks ago)
Does a modem device set to pass through "normally" send the info through to the router it's connected to?? I seem to remember that with my cable/fiber modem I had the manually set the IP address for the interface. But I swear that I remember the first ATT modem pushing through the IP.
And apologies for the weirdness of my situation partly induced by my second location being 5 hr drive away - would require drive, hotel stay, etc if I can't get this troubleshooting done remotely and by testing
-
Yes I would expect it to allow pfSense to pull a lease from AT&T directly. But I think you need to confirm that with a direct connection.
If you got any part of the VLAN or switch setup wrong it would just fail entirely. Since you are seeing ping responses to it (with high latency) it is passing traffic so the switch/vlan config is almost certainly correct.