Cloudflare tunnels with Docker connector security
-
@argonaut how would that be? Why would a tunnel to a docker running behind pfsense access pfsense gui?
When you resolve say something.domain.tld that is hosted on clouldflare, and then pushed down the tunnel when you access it, that would not access your pfsense wan IP and then gui port.
Now sure if something.domain.tld resolved to your pfsense wan IP, and you were running the gui on pfsense wan port, and you had that open sure they would hit your gui. But why would the gui port (443? or 80?) be open on your wan in the first place?
But none of that would have anything to do with a tunnel between a docker and clouldflare.
If your gui is exposed on your wan, they don't have to "guess" any domain, they could just hit your IP with random scan.. You understand there is going to be countless things scanning the internet, and sure on 443 and 80.. And lots of other ports - you shouldn't really ever expose pfsense gui to the public internet. If you want to access your pfsense gui while remote, it would be best to vpn to pfsense, and access the gui over the vpn.
-
I'd guess you are testing from a LAN side client and don't have split-DNS or NAT reflection enabled.
https://docs.netgate.com/pfsense/en/latest/recipes/port-forwards-from-local-networks.html
-
@stephenw10 possible - but normally when you setup some domain to be tunnel to your whatever, the fqdn would resolve to a cloudflare IP and not the actual wan IP of pfsense.
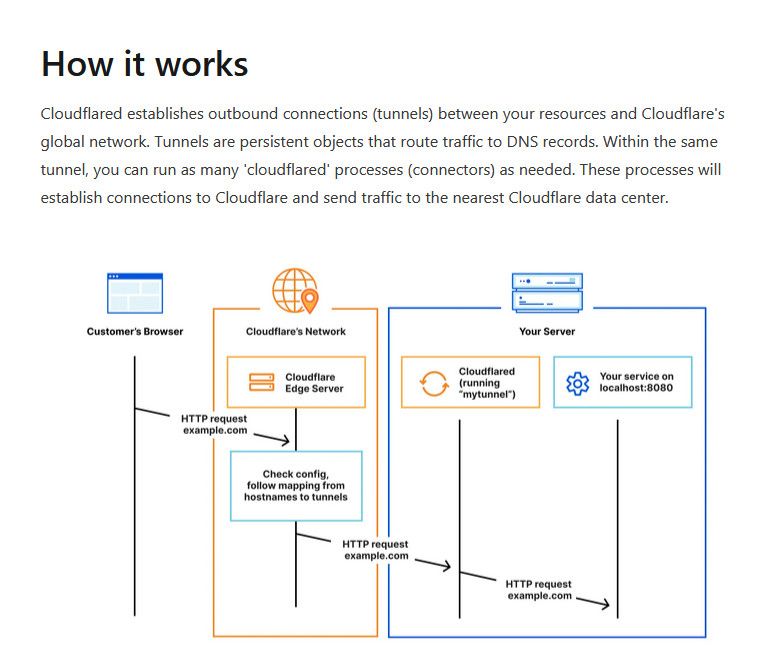
wouldn't really matter where the "client" is wanting to connect to this fqdn is, it should resolve to the cloudflare IP..
The example.com in the above pic.
cloudflare would then send it down the tunnel you setup.. your end of the tunnel will be connected by your device running the "cloudflared" app that connects to cloudflare and creates the tunnel.
Pfsense really isn't involved in this at all.. Since the tunnel is actually brought up by the docker he is running.. the fqdn you connect to should point to a cloudflare IP. All pfsense part in this would letting the device running clouldflared software outbound.
-
Hmm, good point!
Then maybe he does have split DNS configured but resolving incorrectly?
Hard to see why it would ever hit any pfSense IP, I agree.
-
@stephenw10 said in Cloudflare tunnels with Docker connector security:
split DNS configured but resolving incorrectly?
Yeah could be very probable - @argonaut can you pm the fqdn your using for this tunnel if you're not wanting it public posted.. And I can check what it resolves to on the public internet - which should be a cloudflare owned IP.
-
Thank-you for your replies. I appreciate it.
I wrote that message in haste as I had just configured Cloudflare tunnel and it worked perfectly taking me to the LAN interface on pfsense.
But then I realized anyone who guessed the domain name could also go straight into my network...
But I did some more reading and now see how you have to lock things down.
So a learning curve and an exciting new technology - for me anyways.
Any tips on locking down Cloudflare tunnels so that pfsense and the local network is not compromised?
Vlans for access vs CT?
Thanks again!
-
@argonaut anytime you allow anybody into a box on your network no matter what the method is a possible way into your network.. if they compromise that something you allow them access to. Be it a docker or a service, so yeah you are better off locking that device that service is running on from access the rest of your network..
-
Yup put that container in a different subnet/VLAN so you can segregate it from the rest of your network. If it's exposed to the internet it may be compromised at some point so it should be in a DMZ of sorts if possible.
-
containers/dockers are good starts in compartmentalization in that they normal only have the pieces needed to provide whatever service they are handling. So even if they were to get compromised in someway and the bad guy could get a prompt. What can be done could be very limited in what commands are available, etc.
But yeah it never hurts to also have it in an isolated segment that can not even talk to the rest of your network.
-
Thanks again for your replies.
I enjoy playing around with all this networking and security stuff.
Very exciting.
And pfsense is the best!
And a great support community - thank-you.