Allow only certain IPs to connect to home pfSense?
-
Apologies in advance for the newbie question. I used Netgate docs and have IPsec working to connect my Mac at work to the home pfSense 2100 to then screen share my home Mac. Looking through pfSense IPsec logs I see a quite a few random connection attempts. Since I only connect from one place is there any benefit to allowing only the work router IP for IPsec connections? If so, how would I do that?
-
@terryzb It is always best to secure your connection to specific IP or limited set of IPs. No matter if a secure vpn type service with secure auth method, etc. if possible
The rule on your wan that allows access to the service your exposing can be set to only allow a specific source IP. Or a netblock, or even when you don't know the source, you could lock it down to a list of geoips.. Like only the US for example. Or the ASN of the provider they would be coming from like comcast or whatever other isp they might be using.
If you know the only place your going to connect to your vpn is from your work IP.. Then sure lock it down to that IP.
I have openvpn setup, and I am quite confident that someone is not going to just be able to auth to my vpn.. They need the cert issued by me, and they would also have to have the tls key to even start the auth process, etc. But I still lock it down to US based IPs, while I don't know what IP I would be coming from on the road, I do know its going to be a US based IP.
If nothing else it keeps noise out of your vpn log ;)
-
@johnpoz Thank you very much John. I always appreciate your experience and advice.
-
@terryzb See
https://docs.netgate.com/pfsense/en/latest/config/advanced-firewall-nat.html#disable-auto-added-vpn-rulesIf you want to, say, use a laptop, you can install a dynamic DNS client on the laptop and allow your dyndns hostname in the firewall rule. pfSense updates hostnames every 5 minutes by default.
-
I'm now blocking port 4500 from any IPs not in a range of IPs my work's ISP assigns. Should I also block port 500?
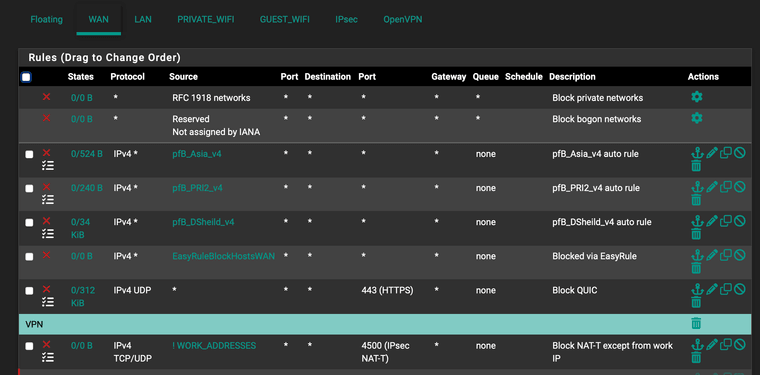
-
@terryzb If you checked “Disable Auto-added VPN rules” then you need to add allow rule(s). I do not know where the hidden, auto rules are in the list, I would guess the top.
And yes there are two ports.
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/firewall-rules.html#outer-ipsec-traffic -
@SteveITS Thanks Steve. I did not Disable Auto-added VPN rules. The block ports 500 and 4500 rules I added are being hit and the logs have been quiet, so looks like being at the bottom of the WAN list is okay.