iOS 18.1 can't establish connection anymore
-
Sice the update to iOS 18.1 my iPhone can't establish the IPsec connection to my pfSense 2.7.2 anymore.
Log:
Nov 23 17:34:30 charon 74713 01[NET] <con-mobile|98> sending packet: from 37.84.215.xxx[4500] to 80.187.66.xxx[10864] (420 bytes) Nov 23 17:34:30 charon 74713 01[NET] <con-mobile|98> sending packet: from 37.84.215.xxx[4500] to 80.187.66.xxx[10864] (1236 bytes) Nov 23 17:34:30 charon 74713 01[ENC] <con-mobile|98> generating IKE_AUTH response 1 [ EF(2/2) ] Nov 23 17:34:30 charon 74713 01[ENC] <con-mobile|98> generating IKE_AUTH response 1 [ EF(1/2) ] Nov 23 17:34:30 charon 74713 01[ENC] <con-mobile|98> splitting IKE message (1568 bytes) into 2 fragments Nov 23 17:34:30 charon 74713 01[ENC] <con-mobile|98> generating IKE_AUTH response 1 [ IDr CERT AUTH EAP/REQ/ID ] Nov 23 17:34:30 charon 74713 01[IKE] <con-mobile|98> sending end entity cert "CN=xxx.homeip.net, C=DE, ST=HE, L=xxx, O=xxx" Nov 23 17:34:30 charon 74713 01[IKE] <con-mobile|98> authentication of 'xxx.homeip.net' (myself) with RSA_EMSA_PKCS1_SHA2_256 successful Nov 23 17:34:30 charon 74713 01[IKE] <con-mobile|98> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding Nov 23 17:34:30 charon 74713 01[IKE] <con-mobile|98> peer supports MOBIKE Nov 23 17:34:30 charon 74713 01[IKE] <con-mobile|98> initiating EAP_IDENTITY method (id 0x00) Nov 23 17:34:30 charon 74713 01[CFG] <con-mobile|98> selected peer config 'con-mobile' Nov 23 17:34:30 charon 74713 01[CFG] <98> looking for peer configs matching 37.84.215.xxx[xxx.homeip.net]...80.187.66.xxx[2a01:xxx] Nov 23 17:34:30 charon 74713 01[ENC] <98> parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) IDr CPRQ(ADDR MASK DHCP DNS ADDR6 DHCP6 DNS6 DOMAIN) N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) SA TSi TSr N(MOBIKE_SUP) ] Nov 23 17:34:30 charon 74713 01[ENC] <98> unknown attribute type INTERNAL_DNS_DOMAIN Nov 23 17:34:30 charon 74713 01[NET] <98> received packet: from 80.187.66.xxx[10864] to 37.84.215.xxx[4500] (400 bytes) Nov 23 17:34:30 charon 74713 01[NET] <98> sending packet: from 37.84.215.xxx[500] to 80.187.66.xxx[500] (497 bytes) Nov 23 17:34:30 charon 74713 01[ENC] <98> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(HASH_ALG) N(CHDLESS_SUP) N(MULT_AUTH) ] Nov 23 17:34:30 charon 74713 01[IKE] <98> sending cert request for "CN=pfsense-ca, C=DE, ST=HE, L=xxx, O=xxxt" Nov 23 17:34:30 charon 74713 01[IKE] <98> remote host is behind NAT Nov 23 17:34:30 charon 74713 01[IKE] <98> local host is behind NAT, sending keep alives Nov 23 17:34:30 charon 74713 01[CFG] <98> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 Nov 23 17:34:30 charon 74713 01[IKE] <98> 80.187.66.xxx is initiating an IKE_SA Nov 23 17:34:30 charon 74713 01[ENC] <98> parsed IKE_SA_INIT request 0 [ SA KE No N(REDIR_SUP) N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) ] Nov 23 17:34:30 charon 74713 01[NET] <98> received packet: from 80.187.66.xxx[500] to 37.84.215.xxx[500] (562 bytes) Nov 23 17:34:30 charon 74713 01[NET] <97> sending packet: from 37.84.215.xxx[500] to 80.187.66.xxx[500] (38 bytes) Nov 23 17:34:30 charon 74713 01[ENC] <97> generating IKE_SA_INIT response 0 [ N(INVAL_KE) ] Nov 23 17:34:30 charon 74713 01[IKE] <97> DH group ECP_256 unacceptable, requesting MODP_2048 Nov 23 17:34:30 charon 74713 01[IKE] <97> remote host is behind NAT Nov 23 17:34:30 charon 74713 01[IKE] <97> local host is behind NAT, sending keep alives Nov 23 17:34:30 charon 74713 01[CFG] <97> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 Nov 23 17:34:30 charon 74713 01[IKE] <97> 80.187.66.xxx is initiating an IKE_SA Nov 23 17:34:30 charon 74713 01[ENC] <97> parsed IKE_SA_INIT request 0 [ SA KE No N(REDIR_SUP) N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) N(HASH_ALG) ] Nov 23 17:34:30 charon 74713 01[NET] <97> received packet: from 80.187.66.xxx[500] to 37.84.215.xxx[500] (370 bytes)Config:
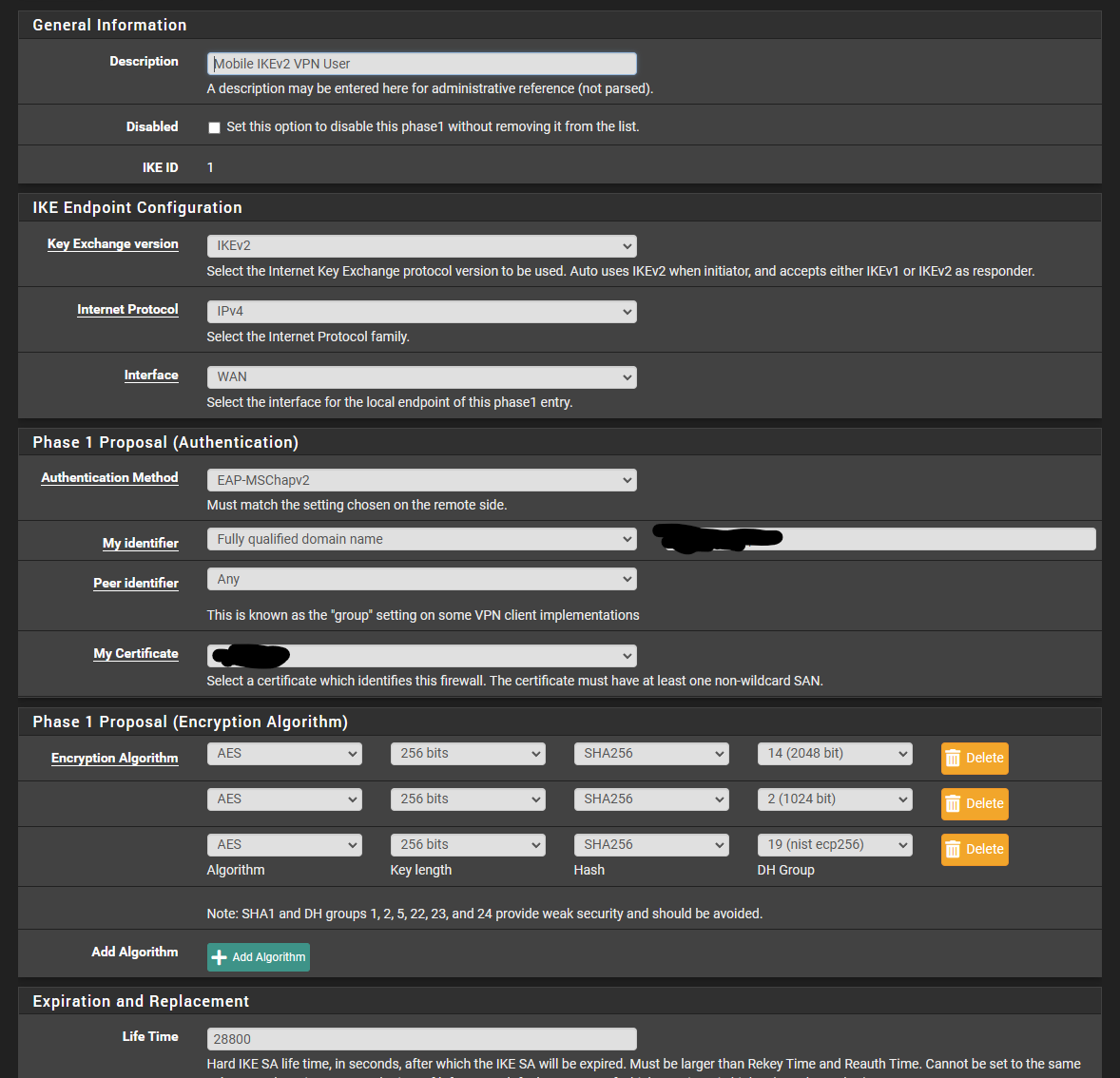
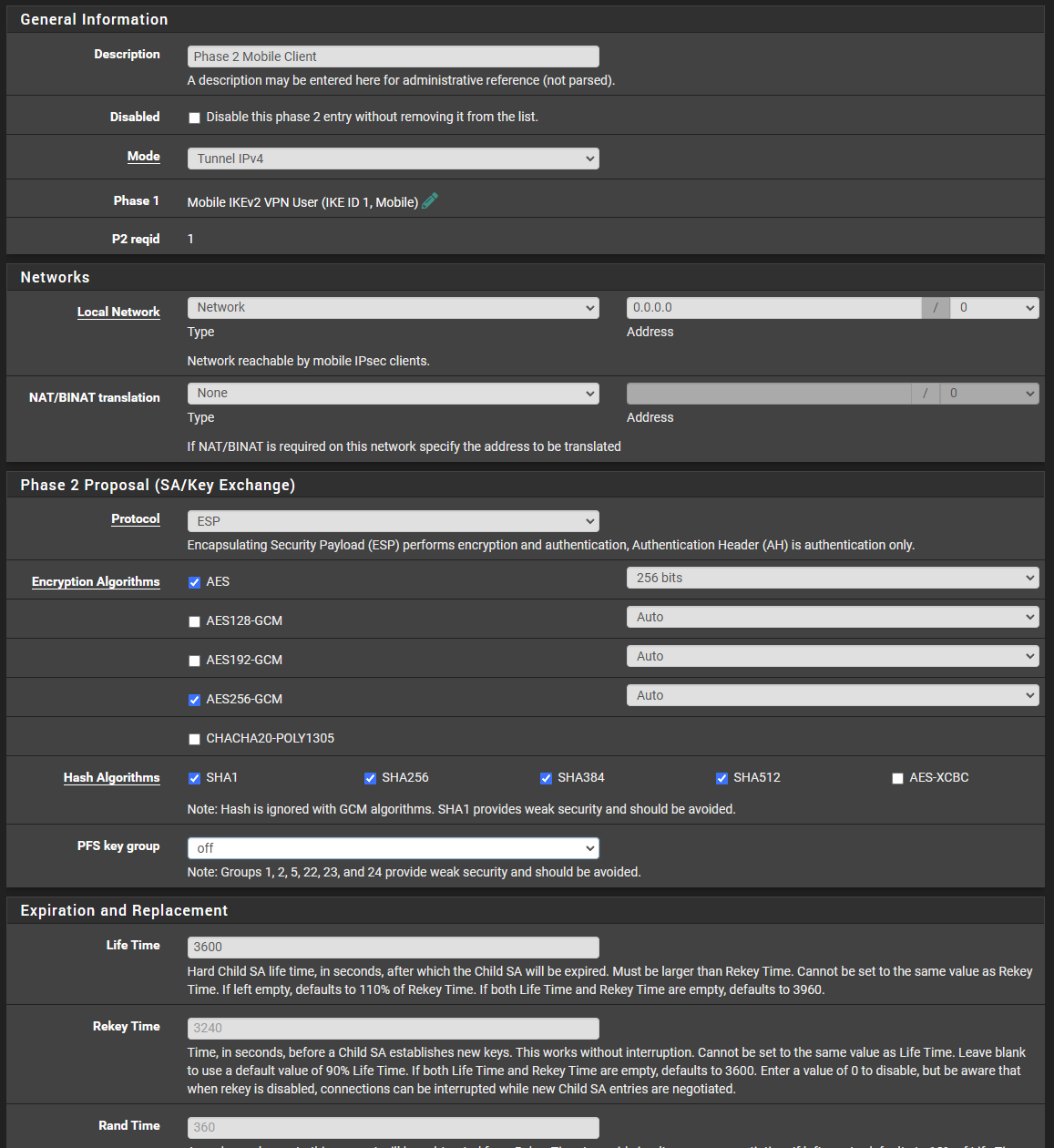
-
@mrsunfire You'll need to increase logging verbosity to drill down further (VPN / IPsec / Advanced Settings / IPsec Logging Controls).
-
One more information: on my pfSense Plus with the same settings it's still working. Also some folks here do have that issue:
https://forum.opnsense.org/index.php?topic=43766.0
-
@mrsunfire I can corroborate the OPNsense forum discussion to the extent that I have a working iOS 18.1.1 device which derives its VPN connection from a configuration profile (created via iMazing Configurator), selects IKE proposal
AES_GCM_16_256/PRF_HMAC_SHA2_512/CURVE_448(DH Group 32), and has a manually-installed CA (LE) cert.Server is on CE 2.7.2.
-
Correction to my previous post: the working iOS 18.1.1 device actually does NOT have LE's CA cert manually imported. (LE is apparently now a trusted a root authority in iOS.)
The VPN configuration profile itself is self-signed however—and it's that signer's CA cert that's manually installed on this working device.
Doubtful that any of this is relevant. Just wanting to clarify. Apologies for any confusion.