after upgrade to 24.11: squid doesn´t start
-
This file is automatically generated by pfSense
Do not edit manually !
http_port 172.16.9.1:3128
http_port 172.16.4.1:3128
http_port 172.16.5.1:3128
http_port 172.16.6.1:3128
http_port 172.16.8.1:3128
tcp_outgoing_address XX.XX.XXX.XXX
icp_port 0
digest_generation off
dns_v4_first off
pid_filename /var/run/squid/squid.pid
cache_effective_user squid
cache_effective_group proxy
error_default_language fr
icon_directory /usr/local/etc/squid/icons
visible_hostname Squid Serveur
cache_mgr XXXXXXX.XXXXXXXXXX@XXXXXX.XX
access_log /var/squid/logs/access.log
cache_log /var/squid/logs/cache.log
cache_store_log none
netdb_filename /var/squid/logs/netdb.state
pinger_enable on
pinger_program /usr/local/libexec/squid/pingerlogfile_rotate 360
debug_options rotate=360
shutdown_lifetime 3 secondsAllow local network(s) on interface(s)
acl localnet src 172.16.9.0/28 172.16.4.0/28 172.16.5.0/27 172.16.6.0/28 172.16.8.0/28
forwarded_for on
uri_whitespace stripcache_mem 4000 MB
maximum_object_size_in_memory 1000 KB
memory_replacement_policy heap GDSF
cache_replacement_policy heap LFUDA
minimum_object_size 0 KB
maximum_object_size 20 MB
cache_dir ufs /var/squid/cache 2000 256 256
offline_mode on
cache_swap_low 90
cache_swap_high 95
cache allow allAdd any of your own refresh_pattern entries above these.
refresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern -i (/cgi-bin/|?) 0 0% 0
refresh_pattern . 0 20% 4320#Remote proxies
Setup some default acls
ACLs all, manager, localhost, and to_localhost are predefined.
acl allsrc src all
acl safeports port 21 70 80 210 280 443 488 563 591 631 777 901 3128 3129 1025-65535
acl sslports port 443 563acl purge method PURGE
acl connect method CONNECTDefine protocols used for redirects
acl HTTP proto HTTP
acl HTTPS proto HTTPS
acl whitelist dstdom_regex -i "/var/squid/acl/whitelist.acl"
acl sslwhitelist ssl::server_name_regex -i "/var/squid/acl/whitelist.acl"
http_access allow manager localhosthttp_access deny manager
http_access allow purge localhost
http_access deny purge
http_access deny !safeports
http_access deny CONNECT !sslportsAlways allow localhost connections
http_access allow localhost
request_body_max_size 0 KB
delay_pools 1
delay_class 1 2
delay_parameters 1 -1/-1 -1/-1
delay_initial_bucket_level 100
delay_access 1 allow allsrcReverse Proxy settings
Package Integration
url_rewrite_program /usr/local/bin/squidGuard -c /usr/local/etc/squidGuard/squidGuard.conf
url_rewrite_bypass off
url_rewrite_children 16 startup=12 idle=8 concurrency=0Custom options before auth
Always allow access to whitelist domains
http_access allow whitelist
List of domains allowed to logging in to Google services
request_header_access X-GoogApps-Allowed-Domains deny all
request_header_add X-GoogApps-Allowed-Domains microsoft.comSet YouTube safesearch restriction
acl youtubedst dstdomain -n www.youtube.com m.youtube.com youtubei.googleapis.com youtube.googleapis.com www.youtube-nocookie.com
request_header_access YouTube-Restrict deny all
request_header_add YouTube-Restrict moderate youtubedstSetup allowed ACLs
Allow local network(s) on interface(s)
http_access allow localnet
Default block all to be sure
http_access deny allsrc
icap_enable on
icap_send_client_ip on
icap_send_client_username on
icap_client_username_encode off
icap_client_username_header X-Authenticated-User
icap_preview_enable on
icap_preview_size 1024icap_service service_avi_req reqmod_precache icap://127.0.0.1:1344/squid_clamav bypass=off
adaptation_access service_avi_req allow all
icap_service service_avi_resp respmod_precache icap://127.0.0.1:1344/squid_clamav bypass=on
adaptation_access service_avi_resp allow all -
With my non-expert eyes I don't see anything that shocks me. What do you think?
-
said in after upgrade to 24.11: squid doesn´t start:
Unknown http_port option 'NO_TLSv1,'
Unknown http_port option 'NO_TLSv1,'
We had this merged as it disabled the older TLS version in the previous Squid version
2024/12/02 15:13:21| Processing: acl block_hours time 00:30-05:00 2024/12/02 15:13:21| Processing: ssl_bump terminate all block_hours 2024/12/02 15:13:21| Processing: http_access deny all block_hours 2024/12/02 15:13:21| Processing: acl getmethod method GET 2024/12/02 15:13:21| Processing: acl to_ipv6 dst ipv6 2024/12/02 15:13:21| Processing: acl from_ipv6 src ipv6 **2024/12/02 15:13:21| Processing: tls_outgoing_options options=NO_SSLv3,NO_TLSv1,NO_TLSv1_1,NO_TICKET,SINGLE_DH_USE,SINGLE_ECDH_USE** 2024/12/02 15:13:21| ERROR: Unsupported TLS option SINGLE_DH_USE 2024/12/02 15:13:21| ERROR: Unsupported TLS option SINGLE_ECDH_USE 2024/12/02 15:13:21| Processing: acl HttpAccess dstdomain "/usr/local/pkg/http.access" 2024/12/02 15:13:21| Processing: acl windowsupdate dstdomain "/usr/local/pkg/windowsupdate" 2024/12/02 15:13:21| Processing: refresh_all_ims on 2024/12/02 15:13:21| Processing: reload_into_ims on 2024/12/02 15:13:21| Processing: max_stale 20 years 2024/12/02 15:13:21| Processing: minimum_expiry_time 0See the NO_TLSv1 processes in the older boot environments that is weird I wonder if that is Squid 7 they changed that directive right when we merged it. Unreal
Merged in dc49dc3b0fa84d3e2588f31c69060f70b162e390.
https://github.com/pfsense/FreeBSD-ports/commit/bd93b039663782e42721656ed50653086e6118ba
https://github.com/pfsense/FreeBSD-ports/pull/1367
https://github.com/pfsense/FreeBSD-ports/pull/1365
That is when I added the NO_TLSv1 for security, but it is not taking scratching my head here as it was working before and on that last pfsense versions. Sorry
$sslproxy_options is used with tls_outgoing_options options and should have blocked use of TLS1 and TLS1_1 when doing packet scans without this feature flag set the proxy was allowing connections with TLS1_1 after adding this directive feature flag manually it forced TLSv1_2 and TLSv1_3 to be used as seen in pcap files. Please set this as many websites will send change cipher requests when attempting TLS1_1
Again, why does the new version block the restriction and mark it as unknown weird right it works on the older one as you can see above.
I think I got mixed up with my first attempt to improve security on this package. Sorry :(
-
@philippe34 Is that the conf file start or fails?
The error shown:
Unknown http_port option 'NO_TLSv1,'makes it seem like the conf file is being incorrectly generated such that it;s trying to use 'NO_TLSv' as a an http_port. -
Commit
dc0f0badcbf29efa73fa6d3cc5e5ab966ea3da4fcaused issues I think this directive is no longer valid as soon as we fixed it, Squid upstream must have already fixed it and disabled the directive also just NO_TLSv1 the other NO_TLSv1_1 seems to still work.
https://github.com/JonathanDLee24/FreeBSD-ports/tree/dc0f0badcbf29efa73fa6d3cc5e5ab966ea3da4f
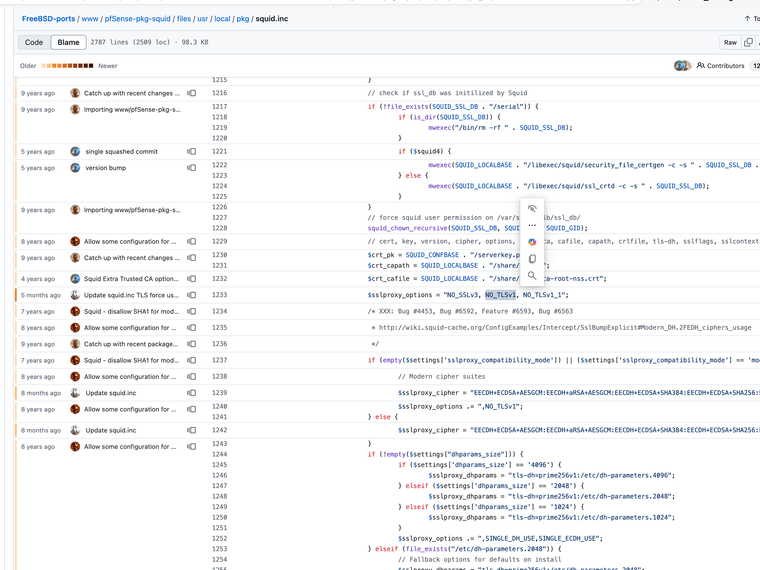
Let me change it back and see if that fixes the error but it will take 6 months to get fixed before it gets reviewed again, I tested it with my stuff and everything. Keep trying don't give up
-
Oh OK this is a fixed setting not an option. Interesting.
I expect those http_ports lines to include those options like:http_port 192.168.221.1:3128 ssl-bump generate-host-certificates=on dynamic_cert_mem_cache_size=10MB cert=/usr/local/etc/squid/serverkey.pem tls-cafile=/usr/local/share/certs/ca-root-nss.crt capath=/usr/local/share/certs/ cipher=EECDH+ECDSA+AESGCM:EECDH+aRSA+AESGCM:EECDH+ECDSA+SHA384:EECDH+ECDSA+SHA256:EECDH+aRSA+SHA384:EECDH+aRSA+SHA256:EECDH:EDH+aRSA:!RC4:!aNULL:!eNULL:!LOW:!3DES:!SHA1:!MD5:!EXP:!PSK:!SRP:!DSS tls-dh=prime256v1:/etc/dh-parameters.2048 options=NO_SSLv3, NO_TLSv1_1Which is why it throws the error there.
-
@stephenw10 said in after upgrade to 24.11: squid doesn´t start:
le=/usr/local/share/certs/ca-root-nss.crt capath=/usr/local/share/certs/ cipher=EECDH+ECDSA+AESGCM:EECDH+aRSA+AESGCM:EECDH+ECDSA+SHA384:EECDH+ECDSA+SHA256:EECDH+aRSA+SHA384:EECDH+aRSA+SHA256:EECDH:EDH+aRSA:!RC4:!aNULL:!eNULL:!LOW:!3DES:!SHA1:!MD5:!EXP:!PSK:!SRP:!DSS tls-dh=prime256v1:/etc/dh-parameters.2048 options=NO_SSLv3, NO_TLSv1_1
https://github.com/pfsense/FreeBSD-ports/commit/476a7d0e3dca704b236839970f1d215912184f73
Should fix it per maintainer
-
hello,
for the moment it works I will do more tests this evening.
I will check the logs.
thanks for your help -
nothing that helps me. I don´t use ssl or other extended options and it throws the error message i wrote before.
-
@19pegr69 said in after upgrade to 24.11: squid doesn´t start:
'ld-elf.so.1: /usr/local/sbin/squid: Undefined symbol "_ZTTNSt3__118basic_stringstreamIcNS_11char_traitsIcEENS_9allocatorIcEEEE"'
That looks more like you have the wrong squid version installed somehow.

-
I have this also. I've nothing to add to the resolution efforts unfortunately
-
@JonathanLee said in after upgrade to 24.11: squid doesn´t start:
https://github.com/pfsense/FreeBSD-ports/commit/476a7d0e3dca704b236839970f1d215912184f73
This doesn't seem enough, at least not for all archs, since it also fails on TLSv1_1:
[24.11-RELEASE][admin@2100-3.stevew.lan]/root: /usr/local/sbin/squid -f /usr/local/etc/squid/squid.conf CPU Usage: 0.064 seconds = 0.040 user + 0.024 sys Maximum Resident Size: 54384 KB Page faults with physical i/o: 0 2024/12/04 20:00:01| Processing Configuration File: /usr/local/etc/squid/squid.conf (depth 0) 2024/12/04 20:00:01| WARNING: Failed to decode EC parameters '/etc/dh-parameters.2048' OpenSSL-saved error #1: 0x1e08010c 2024/12/04 20:00:01| FATAL: Unknown http_port option 'NO_TLSv1_1'. 2024/12/04 20:00:01| Not currently OK to rewrite swap log. 2024/12/04 20:00:01| storeDirWriteCleanLogs: Operation aborted. 2024/12/04 20:00:01| FATAL: Bungled /usr/local/etc/squid/squid.conf line 4: http_port 192.168.221.1:3128 ssl-bump generate-host-certificates=on dynamic_cert_mem_cache_size=10MB cert=/usr/local/etc/squid/serverkey.pem tls-cafile=/usr/local/share/certs/ca-root-nss.crt capath=/usr/local/share/certs/ cipher=EECDH+ECDSA+AESGCM:EECDH+aRSA+AESGCM:EECDH+ECDSA+SHA384:EECDH+ECDSA+SHA256:EECDH+aRSA+SHA384:EECDH+aRSA+SHA256:EECDH:EDH+aRSA:!RC4:!aNULL:!eNULL:!LOW:!3DES:!SHA1:!MD5:!EXP:!PSK:!SRP:!DSS tls-dh=prime256v1:/etc/dh-parameters.2048 options=NO_SSLv3, NO_TLSv1_1 2024/12/04 20:00:01| Squid Cache (Version 6.10): Terminated abnormally. -
@stephenw10 I think he fixed this also it lists as a red removed line today for TLSv1_1 also. I wonder why the new Squid 7.0 that resolved all the concerns no longer lets you use this directive. Weird maybe it is just all disabled now for it and they do not need that directive. The V 7 has resolved almost all the concerns that was in that white paper
-
The issue should be fixed after applying both the previous commit and this one:
https://github.com/pfsense/FreeBSD-ports/commit/009dc5f68e0cf1d1a767d1a9119bcbaface44823 -
@marcosm thanks I love this package, I am also having that OpenSSL error for some reason.
-
Which error is that?
-
@stephenw10 2024/12/04 20:00:01| WARNING: Failed to decode EC parameters '/etc/dh-parameters.2048'
OpenSSL-saved error #1: 0x1e08010c -
Ah I see. Hmm....

-
It's nice that everyone seems to be able to solve this problem, but other than the comment that I've probably installed the wrong package, I haven't been able to get any help. I just expect the script to get the right package itself when updating. Can someone please explain to a FreeBSD layman how I can get the apparently correct package onto the system when installing via the GUI?
-
Check the pkgs you actually have installed:
pkg info -x squid