KEA DHCP missing "Register DHCP leases in DNS Resolver..."
-
@BruceX I switched to kea after the 24.11 upgrade and don't have any problems. Before I had to revert to ISC per above.
-
@4o4rh I've not used the patches package before but I interpret your statement as applying these patches also fixes this dns not registering problem.
I'll have to wait awhile before having the courage to apply these after the last 'fix' I applied lost me a few days to debugging and fixing my system.
-
@BruceX I have now enabled the KEA DHCP server. On settings I checked both "Enable DNS registration" en "Enable early DNS registration". All seems to work now. The only thing is you still need to provide an IP address of the NTP server rather than a domain name.
-
@pvk1 do you mean in the ntp server? i don't have this problem. I am using normal country level ntp pools
-
@pvk1 said in KEA DHCP missing "Register DHCP leases in DNS Resolver...":
provide an IP address of the NTP server rather than a domain name.
Which is how it should be per the rfc.. dhcp doesn't hand the client a fqdn for ntp - it hands out an IP.
-
@johnpoz I must be understanding something different from the statement.
In my NTP Server settings, I use de.pool.ntp.org and it works fine. -
@4o4rh said in KEA DHCP missing "Register DHCP leases in DNS Resolver...":
In my NTP Server settings, I use de.pool.ntp.org and it works fine.
That's the NTP server process. It uses the WAN side.
Here this :
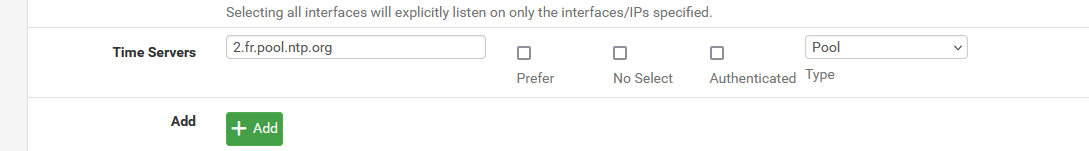
which has 'nothing' to do with the NTP DHCP server setting (the DJCP server operates on the LAN side of pfSense). The DHCP server can inform the DHCP clients of a known (local) NTP server, like pfSense, as it has a NTP server on board.
This DHCP (kea or ISC) 'NTP setting' needs to be an IP, and is typicality the pfSense LAN IP.Example :
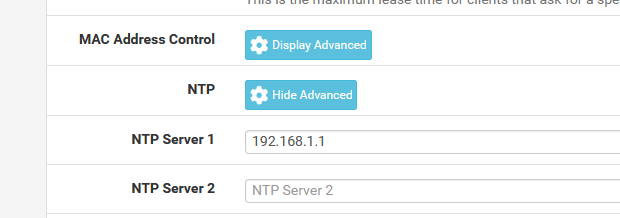
-
^exactly - pfsense allowed you to put in a fqdn for the dhcp server settings before. They would just translate that to an IP for dhcp settings. They should either modify the note below the box, or allow for fqdn (that they translate for you).. But fqdn is a bad idea because something like something.pool.ntp.org can resolve to lots of different IPs - that change, and pool members come and go so if they hand out IP X, tomorrow maybe that IP is no longer valid, etc
It really was never a good idea to allow users to put in fqdn for the dhcp server ntp it hands out.
-
@Gertjan ah ok. my clients take ntp from pfsense. that's why i don't run into this problem then.
-
@4o4rh said in KEA DHCP missing "Register DHCP leases in DNS Resolver...":
@pvk1 do you mean in the ntp server? i don't have this problem. I am using normal country level ntp pools
I mentioned it because the DHCP server did not run when I migrated it the first time. It did not give an error.
-
@pvk1 yeah I think there is/was an issue with kea if you had fqdn for ntp before, that it would just not run.
-
@johnpoz said in KEA DHCP missing "Register DHCP leases in DNS Resolver...":
that it would just not run.
Exact.
If I do this :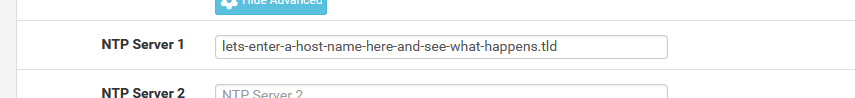
and then I save :
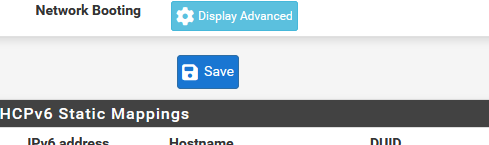
I see a big red error message :
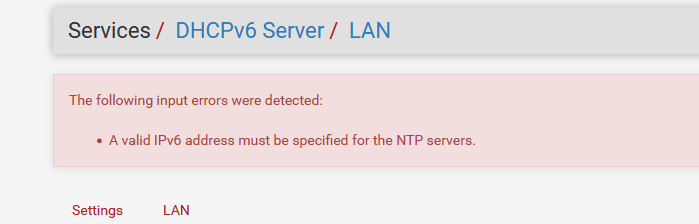
telling me that a host name is a no go.
Still, the tooltip told me :
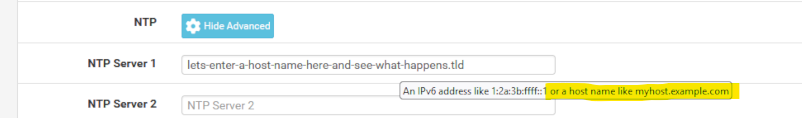

-
@Gertjan yeah this is the confusing part for some users

Maybe that should of never been an option, since dhcp can never use it - but pfsense was doing some magic in the background to convert the fqdn you put in to an IP.. Which guess is ok if the ntp server only has 1 IP, etc.. But with a pool address which is very dynamic and pool membership is very fluid - since its really just users that add their server to the pool, these change all the time..
So in hindsight (which is always 20/20) allowing for fqdn prob not the best choice.
-
@Slowmotion-0 said in KEA DHCP missing "Register DHCP leases in DNS Resolver...":
As of this moment (Feb-2024), besides the static IP mapping approach, is there any other trick we can do to inject the KEA DHCP leases into DNS Resolver?
What is the KEA trick with static IP mapping approach?
I have a machine with 2.7.2 running KEA and dns resolver does not resolve any hostnames that are acquired from dhcp or hostnames that are DHCP static reservation ip mapped.I read most the posts and appears that 24.11 PLUS has returned with this feature but my machine is CE not PLUS https://docs.netgate.com/pfsense/en/latest/releases/24-11.html "This release includes support for DNS Registration of DHCP client hostnames from the Kea DHCP daemon to the Unbound DNS Resolver"
-
@clawsonn just move back to isc, until such time that kea has all the features you want there is no reason to move to it.
Yes isc is end of life, doesn't mean it stopped working or that there are any sort of serious security risks with running it.
If your running CE version, wait til 2.8 comes out - hopefully kea will have the features you want then.
-
@clawsonn said in KEA DHCP missing "Register DHCP leases in DNS Resolver...":
I have a machine with 2.7.2 running KEA and dns resolver does not resolve any hostnames that are acquired from dhcp
Then this option would do the trick :
Under Services > DNS Resolver > General Settings, there is an option called "DHCP registration" (something like that, I don't have that anymore since I use Kea on 24.11)
If these host names are not valid ... call Houston. Some device don't even communicate a host name.
And worse : every time a lease is received, the pfSense DNS (resolver) gets restarted.@clawsonn said in KEA DHCP missing "Register DHCP leases in DNS Resolver...":
or hostnames that are DHCP static reservation ip mapped
That's the option right after.
That option always worked for me, I've been using 2.7.2 for a while.
And you can check they are included in the local DNS cache : see this file : /etc/hosts
If this doesn't work for you : call Houston again : you have a DNS problem.@clawsonn said in KEA DHCP missing "Register DHCP leases in DNS Resolver...":
I read most the posts and appears that 24.11 PLUS has returned with this feature but my machine is CE not PLUS
Correct. That's the new way of doing things.
With 24.11 I see these lines in the DHCP logs :2024-12-10 08:05:49.292692+01:00 kea2unbound 72549 Write include: /var/unbound/leases/leases4.conf (f8fa5d9f54dbf4eb328a3018566546c4e14278931f34a53625dc5d0cd16da077) 2024-12-10 08:05:49.230901+01:00 kea2unbound 72549 Add record: "iphone-xii-gertjan.bhf.tld. 2400 IN A 192.168.1.35"=> as soon as my phone connects to the LAN network, it gets a DHCPv4 lease.
The lease contains a valid host name, and the host name and IPv4 is communicated to the resolver (unbound).
I'm testing this now for a week or so. Its looking very good.
Btw : same story for the IPv6 and the reverse.Don't worry, 2.8.x show up. Netgate wanted this new system to be tested first by the ones who are paying for it (Plus users) before its releases the same functionality into the 'free' version

-
Same shit in year 2025.
Why are users forced to use such crap? -
Sorry to necrobump, but I am a long term user of pfSense. I really feel strongly that this thread has been cr*apped on. I have implemented it in different environments from gov to retail business to lab to AWS.
I took a break for a bit, and do not work for a company that uses it, and upgraded my lab. I read this entire thread:
- I cannot understand how anyone can ever think that routers do not resolve dns names of dhcp hosts - I am struggling to remember one that ever did not - we are talking d-link 2000 era 56k dial up
**You did not study your users very well here
*When I switched over to to KEA it started recording my unique identifier and broke all of my preconfigured static dhcp entries
*I don't know. I don't read release notes sometimes. When the kids are crying, and the wife is beating down my door, and I need to upgrade a lab router, I just hope it boots.
**The same goes for budget strapped IT peopleI get it, but you have this GIANT warning above the DHCP server like it is just switch and go. Possibly put release notes here?:

I interviewed with your company, and I cannot tell you how many times I have seen stuff like this, and wish I was there. There are industry leading features that could grant you a new market segment. You are breaking things in one market segment, and then being rude to your users when they jump on your forums.
This is one of the best products I have used in my life, and when I did work for other companies, we purchased your hardware, and we paid for support. You have one of the best teams I have worked with.
It is hard to balance this stuff, I get it. I can't imagine the feature requests you have on your plate. I can tell you something even stranger: After I switched to KEA, resolving DHCP requests worked until I edited Host and Domain overrides on my server. So this stuff seems super possible and even easy, but some developer or requirements gathering said "not needed" and when users post here you tell them deal with it?
I hope your sprints get this feedback information. I still love pfsense and it has been a long journey.
ps
It could have also been the fact that I added a host alias that resolves via DNS - but I will never know. - I cannot understand how anyone can ever think that routers do not resolve dns names of dhcp hosts - I am struggling to remember one that ever did not - we are talking d-link 2000 era 56k dial up
-
@webdawg yeah, the effort needed to sign up for the forum really underscores 1) how much I like pfsense's hardware and WANT this to work and 2) how messed up and annoying this is and 3) that I have some small, small sliver of hope that netgate wises up to this and is more careful in the future.
-
@webdawg said in KEA DHCP missing "Register DHCP leases in DNS Resolver...":
Sorry to necrobump, but I am a long term user of pfSense. I really feel strongly that this thread has been cr*apped on.
[ . . . ]
You are breaking things in one market segment, and then being rude to your users when they jump on your forums.Your post seems to be directed at Netgate. But I count only two official Netgate replies (from the same poster) up until this point—and both are empathetic and respectful.
As one of the 'crappers' on the thread, I feel obligated to point out that the rest of us here are merely users like you, who may simply disagree with some of the points you and others are making.