Local DNS Records on different subnet
-
-
@jhmc93 so your search suffix is a public domain? Yeah your most likely going to have weird stuff happen.
because you look, for something like pve.local.whatever its going to end up looking for pve.local.whatever.cable.otherthing.net
-
@johnpoz even though pihole is set as my dns on pfsense and on the laptop on my isp side so don't know what is going on
-
@stephenw10
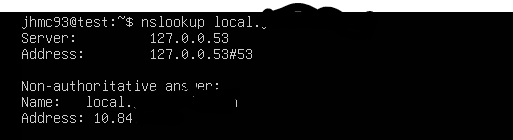 your answer
your answer -
Ok great so it does resolve to the internal IP in the pfSense LAN subnet as expected.
This it is almost certainly failing because the client has no route to reach that subnet. It would not have one by default. It would have to have been added as a static route via the pfSense WAN. And pfSense would need rules on WAN to pass it.
-
@stephenw10 how would I go about that? without exposing it to public internet because I wanna keep it in my ISP subnet and Pfsense Subnet
-
Well really what you should do is move all clients to a subnet behind pfSense to avoid this issue. It's almost certainly going to cause other problems having clients in the pfSense WAN subnet.
But I understand you might have physical restrictions for example preventing that.
So you need a firewall rule on the pfSense WAN to allow traffic from the wan subnet to whatever the target IP is on the LAN.
And you need to add a static route to the pfSense LAN subnet via the pfSense WAN IP on the client directly.
That doesn't expose anything to the public internet.
-
@stephenw10 so do I create that rule in the lan or wan firewall rule or is it a nat rule
-
It's a firewall rule on the WAN interface. The client is trying to open connections from the WAN subnet to servers in LAN.
-
@stephenw10 so what would be my source and destination ip
-
Assuming you've added the route on the client.
The firewall rule should be source: the pfSense WAN subnet and destination: the server in the LAN. Or you set the destination to the full LAN subnet as a test.
-
@stephenw10 so on pfsense add it under the WAN firewall rules? or the LAN?
-
The rule has to be on the WAN.
It needs to pass traffic from the client in the WAN subnet to the server in the LAN subnet.
But this is the wrong way to do this. You should instead move all clients to subnets behind pfSense. You will almost certainly see other issues trying to have clients in the pfSense WAN.
-
@stephenw10 so I won’t be able to access dns cname records off isp side because of security issue with routing traffic from ISP to pfsense LAN
-
I'm not sure what you're asking there.
You can set this up and it will work. It's not really a security issue because you control both subnets and are behind NAT from your ISPs router.
But it is a setup that will almost certainly cause problems in the future unless you understand exactly what is happening and allow for it.
-
@stephenw10 so I put a firewall rule under WAN , any source and destination is my traefik server should it be my pihole? because it didn't resolve to anythin
-
In the screenshot above you showed that whatever the resource is successfully resolved to a 10.84.x.x IP address. There's no need to hide those addresses they are in a private subnet and only valid locally to you.
The reason the client cannot reach it is that it needs a static route to that subnet via the pfSense WAN IP.
And pfSense needs a pass rule on WAN, at a minimum, from the client IP address in the WAN subnet to the server IP address in the LAN subnet. It probably needs only to pass TCP but I would set the protocol to any as a test so you can try pinging it.
-
@stephenw10 so under WAN firewall create a rule source “any” destination “any“?
-
@jhmc93 Your going to have nothing but problems trying to do it with devices on your pfsense wan.. For starters your going to need a route on your upstream router. And then even with a route your traffic is going to be asymetrical because you have host on your transit network.
Put your devices behind pfsense is a much simpler and elegant solution.
-
@johnpoz can’t do that unfortunately
